How to Install Keylogger Remotely on Android Phone
Have you ever heard of keyloggers? these tools can intercept and record anything typed on a smartphone or computer keyboard (including passwords) without anyone noticing. There is no way to detect the presence of Keyloggers “with the naked eye” since they are completely invisible.
Nowadays you can find the android keylogger application conveniently but the question is which is the most effective android keylogger application? Another important question is how can we install a keylogger remotely on a phone.
In this article from SPY24, we will explain what keyloggers are and how they work. The information that we give you in the next paragraphs is for illustrative purposes only, so we do not accept any responsibility for the consequences of improper use of the same.
What is a keylogger?
A keylogger is a tool responsible for registering every single key pressed on the monitored device. It can be considered the equivalent of digital surveillance as it reveals all pulsations, downloads, and conversations. The keylogger allows you to discreetly track all touches on the screen of the phone in question so that the user does not know that their actions are being monitored.
Keylogger: How it works
You must know that there are two types of keyloggers: hardware and software. The former are devices that look like USB sticks and are usually used to spy on computers. They are simply connected to the keyboard cable in order to be able to intercept all data that is transmitted on the PC at lightning speed.
The latter are programs that have to be installed directly on the device to be monitored and can record all the words and phrases typed on the keyboard. This type of key logger is more suitable for cell phone monitoring: what reason would there be to plug a USB stick into a phone? None, except to make the rightful owner suspicious.
Some keyloggers even work remotely: they store the data on the internal memory and then send them as reports to the email account specified during installation.
Detecting the presence of keyloggers is difficult, and the bad guys know that very well. These devices are completely independent of the operating system of the PC or phone they are installed on and are therefore not recognized. The software keyloggers always remain active in the background and are therefore able to intercept:
- All keystrokes.
- The movements of the mouse or the sounds picked up by the microphone.
Getting a keylogger is very easy, just a quick search on the net is enough to find cheap programs and gadgets. Because of this, defending against these types of attacks is difficult, although not entirely impossible.
How does the keylogger work?
Knowing how to use a keylogger is easy. Once you install the keylogger on the phone you want to monitor, it works invisibly in the background and detects all activities that take place on the device. The keylogger software records all the keys pressed and also records the conversations made in the chat.
The keylogger has the disadvantage that it could be used by hackers for illegal purposes, but it also has a positive side. An invisible keylogger is a perfect tool for parents tracking conversations and wanting to know what they are doing online. This could help parents to protect their children from destructive phenomena online such as cyberbullying, sexting, cheating, or sex crimes. Therefore, knowing how to use a keylogger is fundamental.
How to remotely install a keylogger app on Android
Keyloggers are widely available, and you may even have one installed on the very device you’re holding or sitting in front of. Such software cannot necessarily be considered troublesome, especially if you were aware of its existence before and agreed to use a device equipped with it. What makes Keylogger so dangerous is the malicious actors and the naivety of the victims.
Whether you’re using it legally or illegally, all keylogging mechanisms work in essentially the same way: they record all user interactions with the keyboard and allow a third party a complete log of all emails, messages, searches, passwords, accounts, etc. Retrieves the user and any other text typed by the user. You can remotely install a keylogger app in These ways:
Phishing emails: By clicking on a link or downloading a file attached to a phishing email, text message, or social media post, you may accidentally download malware designed to track keystrokes.
Trojan viruses: Trojans are a type of malware named after the wooden horse used by the Greeks to invade Troy. Hackers may deceive users and force them to download by displaying a Trojan virus in the form of a valid application or file.
Zero-Day Exploit: Zero-Day Exploit occurs when hackers find the latest software security flaws and use them to distribute malware such as malicious web scripts or Trojans. In this case, software developers discover vulnerabilities too late to be able to protect users. This is a very dangerous situation because once the system is infected, the vulnerability to further attacks increases.
Infected systems: Keyloggers can exploit already infected systems and install more and more malware on them.
Best Keyloggers for Android no-Root Remote Free
In this part of the article, we mention some of the best available keyloggers and list their features.
| Name | Android Versions Supported | Require Root | Free Trial | Link |
|---|---|---|---|---|
| 🕵️ SPY24 🏅 | All Android Versions 4.4.4 for 13 | No | Yes | Learn More |
| uMobix | Android 4.0 and above | Yes | No | Learn More |
| Auto Forward | Android 4.0 and above | Yes | No | Learn More |
| mSpy | Android 3.0 to 7.2 | Yes | No | Learn More |
| iKeyMonitor | Android 4.0 to 12 | Yes | No | Learn More |
| Hoverwatch | Android 4.0 and above | Yes | No | Learn More |
SPY24 – Keylogger app for Android and iPhone phones – MAC & Windows
SPY24 is one of the most popular choices for a keylogger on almost any platform. This app also works well on WhatsApp, Facebook, Snapchat, and Twitter accounts.
This app has a very simple installation and activation that allows parents to control and manage their children’s activity in virtual mobile networks.
After installing the SPY24 application on the device, you can delete any traces of it and hide it from the user of the device. The app continues to run in the background and sends you the requested data. To access the premium features of the app, you need to purchase the premium package and also root your iOS or Android phone.
Below you can see some features of the SPY24 program:
- Monitor calls and SMS along with date and time
- Telegram, Instagram, WhatsApp, etc. messages report
- Continuous current position and traveled routes
- Websites visited and programs run
- With the ability to hide 100% of the program and remote management
- Ability to block websites, apps, and contacts remotely
SPY24 is perhaps the most successful spy tool available online. To access most of the features that allow you to hack an Instagram account, you need to pay a subscription fee, but the free trial version allows you to:
- View general information in the profile
- Check activity on any mobile phone.
- See the last known location and top ten contacts.
When you pay for your subscription, this service gives you access to the following features.
- Ability to view all media files and direct links sent from the desired account.
- Ability to view all DMs from the desired account.
- The possibility of hacking the password and username of Instagram.
- Full control over the target Instagram account.
How to Install Keylogger Remotely on Android Phone
Wondering if it’s possible to find an app that includes all points described above? We’ve created one just like this, called SPY24. Actually, it’s not a keylogger, it’s a complete monitoring app that does so much more than record keystrokes. More on this later. Now let’s see how to remotely install our keylogger.
If you still think that cell phone keylogger remote installation is a hard process, it’ll change once you download SPY24. Here’s how to send a keylogger to someone’s phone:
- Go to SPY24.PRO and choose the subscription plan.
- Select what device you want to monitor (Android, iPhone, macOS, and Windows).
- Install Eyezy on your loved one’s phone by following the instruction sent to your email.
- Log in to your Control panel.
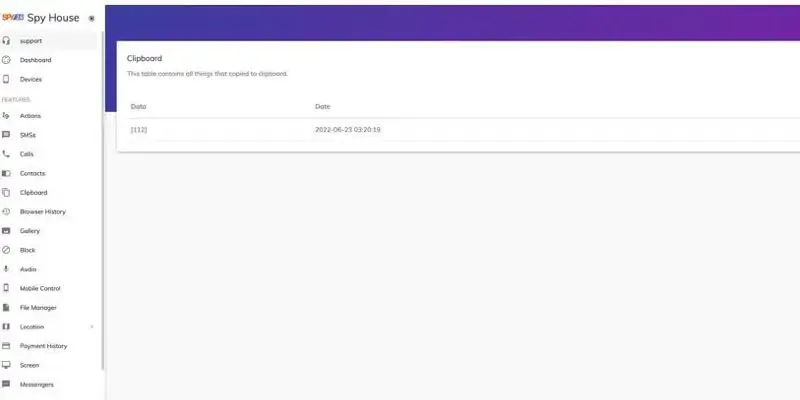
- Go to the Keylogger tab to view every keystroke made in texts or searches.
- As you see, our remote installing keylogger guide is so easy that even a non-tech person can handle it.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
mSpy: keylogger
there are various features of the mSpy. mSpy application can retrieve all the outgoing as well as incoming text messages so that you can get all the details about the text message logs on the Android phone.
mSpy will surely not only remove the set Android keystrokes for you but will also reveal to you the complete web content of the received and also sent SMS message.
One of the most important functions of the Android keylogger is to get the keystrokes placed on social media.
The last and also very helpful attribute that basic Android keyloggers don’t offer is Android GPS location tracking
You will surely be able to see where someone is at the current time. There is no activity that you will certainly not recognize. If a person exists to you and what individual tasks are tracked throughout the day, you will surely be able to find out.
uMobix: keylogger
uMobix is an application that is almost flawless as a spy tool in every way. It was one of the first remote spying apps on the market and offered monitoring services without having to install it on the device it was monitoring.
The price of this program is $29.99 per month.
iKeyMonitor: keylogger
ikeymonitor is a software that can control the phone of family members, or in other words, its work is to hack the child’s phone, which is designed to monitor and control children in the virtual and social space. ikeymonitor is a system program whose main function is a software package to hack a child’s phone and receive family members’ phone information such as calls, SMS, social networks such as Telegram and Instagram, location, and other features.
ikeymonitor is software for Android and iPhone phones that can be easily used by parents who are not familiar with phone software by installing it very easily.
Features of ikeymonitor app
- Working in secret
- Record keystrokes and passwords in the American keyboard and nbsp typing;
- Logging of all incoming and outgoing SMS and WhatsApp messages;
- Logging of response history with contacts, date and time, and duration;
- tracking websites visited in Chrome and stock web browsers;
- Look at the images at the time interval set by the users;
- Sending login report to the e-mail address defined by the user;
- remote on/off status monitoring;
- Support for smartphones running Android OS 2.3 and above.
- No need for the carrier, phone models, or regions of the users.
Hoverwatch: keylogger
It is another useful keylogger for Android users. This is also a complete spy app that comes with many amazing features. With this app, you can track all activities of your target person. For example, it is equipped with an accurate GPS tracking system. You can check call logs, read messages from all instant messaging apps and check everything in the gallery.
Auto Forward keylogger
There are hundreds of other spy apps, but Auto Forward py has a place among them and a large number of devoted users. It has been on the market for more than five years at this point and has established a reputation for being a trustworthy and consistently improving spying force. The list of available options and features in Auto Forward Spy is both comprehensive and adaptable. Because of this, the app is an excellent choice for a wide variety of users in all parts of the world.
You can monitor incoming and outgoing calls and texts, as well as the history of websites you’ve visited, all while taking advantage of the software’s blazing-fast performance. In addition to this, the app is designed to work with a wide range of mobile gadgets and is compatible with the vast majority of operating systems that are currently in use. And all of this can be yours for the low, low price of $29.99 (one-time payment). You can find a comprehensive review here.
Can I install a keylogger remotely on Android phones for free?
Some people might think that they can send the keylogger directly through any of the social media apps or email. Most of these platforms have a virus scanner that will first scan your file and then allow you to send it.
Let’s assume that you sent the file without being recognized. Chances are the person will see an error message stating “this app may damage your device”. You have to convince the person that it is a safe application and that nothing will happen if they install this application.
Even if you somehow send the file, a big problem is waiting for you. None of these apps are apps to use directly. In simpler terms, you cannot just install the app on their phone and you will start getting the keywords. There is a little configuration needed to make it work. The main question remains the same: Who will do the configuration?
You cannot persuade them to enter your details. Hence, this becomes a very confusing, hard, and risky method. So, you need to go with a bit simple method that every person uses.
the simplest way would be to get physical access. You can always have physical access to the cell phone and then you can start installing the keylogger. This is the easiest way to send the keylogger.
When you have physical access, there are very fewer chances that people will come to know. You can easily borrow their device for a wide if they give you the phone. This way you will end up with no loss and very little risk. This is the preferred way to install keyloggers.
Why may you need a keylogger?
Apart from being widely used in cyber attacks and stealing digital currencies, keylogger software also has useful uses, and all software that can record keyboard activity is not necessarily malware.
For example, parents use this software to monitor their children’s behavior online. Apart from this, some employers also use Keylogger software to monitor the activities of their employees during working hours, which must be known to the employees from a legal and ethical point of view.
Another use of keyboard activity recording software is to record and protect passwords and other data in case of system failure. Of course, there are better ways to do this, and using Key Logger is not very smart.
Which free Android keylogger is best?
Keylogger’s Android free app is now one of the most searched things on the internet. People are looking for the best keylogger Android APK to use. As you will know e Google Play store does not allow such apps in their market. Hence, you need to look for a third-party tool that can help you save the keystrokes on any Android device easily.
The totally free keyloggers will certainly be really minimal in most situations. The real application will surely set you back some money, but it will surely get the job done flawlessly. You can experiment with free applications, but if you avoid mistakes, we certainly wouldn’t suggest it.
Why do you need to install Keylogger for Mobile Monitor?
The internet is a fantastic tool for young people to gain knowledge, but without adult supervision, it can become a dangerous and destructive place.
The more connected your kids are, the greater the risk that they will be exposed to the dangers of the internet and encounter inappropriate and violent content. Therefore, parental control is vital for the safety of the children.
The software can’t do everything, but it can make life much easier for parents, especially when the children grow up and want more and more independence. Therefore, it is important to choose the right software, paying attention to the remote keylogger service, which is a fundamental part of sophisticated surveillance. Below we explain what a keylogger is and why you need one.
How to identify and remove a keylogger
In general, it should be said that the keylogger malware can get into your computer in the same ways as other common viruses, but at the same time, it is also possible to buy or download it on your own. To summarize, keyloggers are both a valuable tool and a dangerous weapon, and everything depends on the intentions of the person who installs it and obtains the final information. In the following we have listed the ways of identifying a keylogger:
Look for suspicious or unknown programs.
If you see something you don’t know, look it up online. If it is unnecessary or dangerous, right-click and delete it.
Delete temporary files
Temporary files are a common place to hide keyloggers. The Temp folder quickly fills up with scrambled files, making it easy for keyloggers to disguise themselves as legitimate files. Clearing temporary files can lead to successful keylogger virus removal.
For example, here’s how to clear temporary files in Windows 10:
1. Click on the gear icon in the start menu to open Windows settings
2. Click on the System option.
3. Click Storage in the left navigation menu, then select Temporary files on the drive where Windows is installed.
4. Select all temporary files using the checkboxes, then click Delete files.
Does my phone have a Keylogger?
If you are worried about cyber attacks and your personal information or for any reason you feel that a keylogger has been installed on your system; You can deal with this malware by using one of the following methods:
- Remove all the software that is automatically installed on your system. (This means the software that was not installed at your request)
- Do not download from untrusted and unknown websites.
- Use the virtual keyboard when entering your critical information (such as bank card information when making a purchase).
- Use a password manager (this program will enter your passwords automatically)
- Use a strong antivirus to protect your system from cyber attacks.
If keyloggers fall into the hands of hackers, they can be dangerous. Information such as usernames and passwords is often entered on the keyboard, which is misused by fraudsters. Depending on the type of login method, there are different types of keyloggers. Keylogger involves tracking and recording every keystroke on the keyboard.
How to identify Android keylogger
Android mobile phones are also not safe from keyloggers and may face the risk of malware attacks at any moment. But don’t worry; we will continue to introduce methods that will help you detect keyloggers on your mobile phone.
Strange text messages
Fraudsters and cyber thieves often use strange text messages to break into mobile phones. If you’re getting strange texts that don’t make sense (like texts made up of random characters), you may have a keylogger installed on your cell phone.
If you receive these messages from unknown contacts (on Telegram, WhatsApp, Instagram, etc.), do not open them under any circumstances. The best way in this situation is to delete these messages immediately.
Battery drains quickly
Keyloggers and malicious programs in general usually operate in the background of your mobile phone and therefore require more energy. If your phone’s battery drains abnormally, you may be under the control of one of this malware.
Mobile phone heating
When your device is processing multiple applications at the same time, it can heat up considerably! It’s normal for your phone to get hot when watching movies, chatting with friends, and browsing the web at the same time. But if all these apps are closed and your mobile phone is still hot, there might be a keylogger running.
Constant turning off and on of the device
Constant turning on and off of your Android mobile phone can be another sign of a keylogger. If you face the problem of turning off and on the phone without any reason while running different programs, you should be worried about this thief malware!
Don’t forget that keyloggers make your mobile phone do some things (such as turn it off and on) without your permission.
Slow performance
Slowing down the performance of the mobile phone itself is a painful and uncomfortable event! But the story becomes more worrying when we know that a key logger has caused this problem. Unfortunately, sometimes the presence of malware and its continuous activity in the background can slow down your mobile phone to such an extent that you cannot actually use it.
Are Keyloggers illegal?
The legality of keyloggers depends on consent – and if the content is not provided, keyloggers are illegal. If you work for a company that uses employee monitoring or tracking software, you must agree in your contract to agree to this type of keylogging. Parents are legally allowed to supervise their children if they are under 18 years old. Malicious keylogging by hackers against victims is illegal. The victim did not consent to be monitored, and keylogging is against several data theft, eavesdropping, cybercrime, and hacking laws.
Conclusion
A keylogger is a type of hardware or software tool that is used to record user activities with a computer keyboard. Keyloggers, apart from their useful applications, are also used in hacking sensitive user information such as the private key of digital wallets.
Most keylogger attacks are carried out using software keyloggers to steal user information. These Key Loggers are carried out through various types of cyber attacks such as social engineering attacks and phishing attacks, or very easily through user mistakes and negligence.
When keylogger software is installed on a user’s system, it can record information entered with the keyboard on the computer (such as sensitive passwords) and send it to the hacker. In simple terms, a hacker can steal the private key of a digital wallet and steal users’ digital assets.
To protect your sensitive data from keylogger attacks, you must follow all the principles of cyber security and information protection.
FAQs
What is a key logger tool?
A keylogger is a type of software or hardware that is specifically designed to monitor and record user interactions with keyboards and other similar peripherals.
What does Keylogger do?
A key logger monitors what you type on your keyboard, as well as your interactions with browsers, word processors, web forms, and other text media.
Is a keylogger an illegal tool?
Although keylogging tools are not illegal per se, they are commonly used in illegal ways, mainly by cybercriminals, identity thieves, and other malicious users who seek to steal information or monitor activity.
What is the history of Key Lager?
The first cases of keyloggers date back to the 1970s when the US government was monitoring electronic typewriters. These days, button-tracking software is widely used for personal and organizational purposes.
Are smartphones also infected with keyloggers?
Contrary to what the general public thinks, it is possible to monitor smartphones with the help of keylogging applications. Some of these programs can track your page interactions, downloads, location information, and even conversations.
How to detect contamination with a keylogger?
If your device is infected with keylogger malware, you may experience things like system slowdowns, overheating, or unknown software, processes, or browser extensions.



