Bluetooth Spy App
An Introduction to Bluetooth Spy Apps: Wireless technology assumes to exist everywhere nowadays. For example, walking through a busy region– like the shopping area of a big town. Perhaps you’re just doing casual window shopping, and you’ve got your phone and Bluetooth on “exploration”. This lets other Bluetooth phones find your place.
While you’re in front of a clothes store, considering a new style, your phone alarms: someone texted you. It reads: “We know where you are. Have fun shopping?” It Sounds like something out of a horror movie, correct?
This event is possible and has already happened. The feature of Bluetooth – the technology that can seek and locate other Bluetooth -enabled machines– has some people anxious. Security has long been a topic of technology.
For instance, bluejacking, while easily a sinless joke, allows Bluetooth users to send unwanted messages to nearby devices. Since Bluetooth machines are somewhat detectable, the concept of Bluetooth monitoring has been offered to the tech world.
What is a Bluetooth Spy App?
I try to express the simple meaning of A Bluetooth spy app, a kind of software that utilizes the vigor of Bluetooth to follow activity on other connected systems.
This involves recording talking, tracking location information, accessing text messages and emails, taking photos or videos from the device’s camera, and so on.
This app is usually installed on the device you desire to monitor, but free Bluetooth spy apps are available for download that doesn’t need installation.
How Does It Work?
Bluetooth spy apps work with wireless technology to link to nearby devices – such as smartphones and tablets – making it simple for users to access information remotely. Once the app is installed on the aiming device, it commences recording all the actions done on it – including calls, messages, emails, and photos taken with the device’s camera. The information can then be accessed remotely through an online dashboard or smartphone app.
For those who don’t wish to install an app on their system– such as parents who desire to pursue their children’s phone actions– there are also free Bluetooth spy microphone apps available that let users listen in on conversations without installing any software on the device.
People can listen to their cell phones through SMS and Bluetooth!!
It’s less likely nowadays, but it’s still possible. If someone is listening to your calls, here are some signs to look out for:
Background noise: When your mobile device has background noise while on a call is a sign that somebody else could be listening. Listen out carefully for static, buzzing, or clicks on the line.
Interference around other electronic devices: If you have understood to interfere with other electronic devices, such as your phone or even your TV – then that could be a strong point that there is a tapping device in the structure. These devices often work signals that can change the regular operation of some electronic machines.
Exotic noises from the phone when not on a call.: When you pick up the phone to make a call before you dial any contact, hear the receiver and see if you can listen to any uncommon noises on the line other than the dial tone.
Features of a Bluetooth spy app are:
- You can view their text messages
- Access to the contact index
- You are able to listen to the objective phone’s music without them noticing
- You can turn off/on the phone.
- Access to the phone data
Bluetooth can stop phone hacking:
A great way to avoid using Bluetooth to hack your phone is to utilize the latest version of the operating device. This attack can happen on both Android and iOS operating systems. You can avoid using Bluetooth to hack your phone by getting the latest update for them. Therefore, to stop hackers from entering your phone through Bluetooth, you should only use your phone’s Bluetooth and always turn it off.
Generally, it seems that the more safety options are accessed, the more intrusion manner is used. To avoid these kinds of attacks and similar ones, you should always retain your devices up-to-date and use the latest updates for them. Bluetooth phone hacking can be less anxious if you have a strong antivirus program and an excellent anti-hacking program.
How to handle a Bluetooth spy app for Android:
The first task of installing Super Bluetooth Hack on your Android is to root your system.
Step 1: Discover a site that proposes Super Bluetooth Hack APK files that are appropriate for your operating system and Android version.
Step 2: After you have found the APK file for download, open it in Chrome or any other internet browser on your device.
Step 3: Click “Install” and opt “OK” when prompted; then click “Install App” again.
How can you keep yourself safe?
Hackers are professionals who work with particular tools, such as software or tools that find Bluetooth devices around them. With these specific tools, hackers ambush crowded zones and try to find Bluetooth networks.
When they discover an open Bluetooth network, they struggle to achieve it. If hackers have access to a Bluetooth system, it is easier for them to hack it again. This is because the phone handles the already connected machine as a trusted source and easily attaches to them without your permission.
7 of the most popular App for hacking mobile phones with Bluetooth

1. Super Bluetooth Hack 1.08
This software organizes and reads data from a distance phone via Bluetooth or infrared. Phone lists and SMS can be saved in HTML format. In addition to it, it will show information about charges, networks, and sim cards.
2. Blue Scanner
Blue Scanner seeks Bluetooth-enabled machines and struggles to extract as much data as possible for each newly detected device; in other words, one can utilize this one to spy on others who are near.
3. Blue Sniff
BlueSniff is an easy utility for detecting discoverable and secret Bluetooth-enabled devices. It works on Linux.
4. BlueBugger
This exploits the BlueBug (name of a set of Bluetooth security holes) vulnerability of Bluetooth-enabled devices. By using these vulnerabilities, one can access phone-book, call lists, and other data about that device.
5. BTBrowser
BT Browser is a J2ME application that can browse and explore the technical features of surrounding Bluetooth-enabled devices. One can browse device data and all supported profiles and service records of each device.
6. BTCrawler
BT Crawler is a scanner for Windows Mobile Based devices. It scans for other devices in range and performs service queries. It implements Bluejacking and BlueSnarfing attacks.
7. BlueSnarfing
Bluesnarfing is a manner of hacking into Bluetooth-enabled mobile phones; with this, you can copy all its information like contact book, etc. With this software, you give complete freedom to hackers to send a “corruption code” to you, which will completely shut down the phone and make it unusable for you.
Part 1 of Bluetooth Hacking: How to Start with Bluetooth
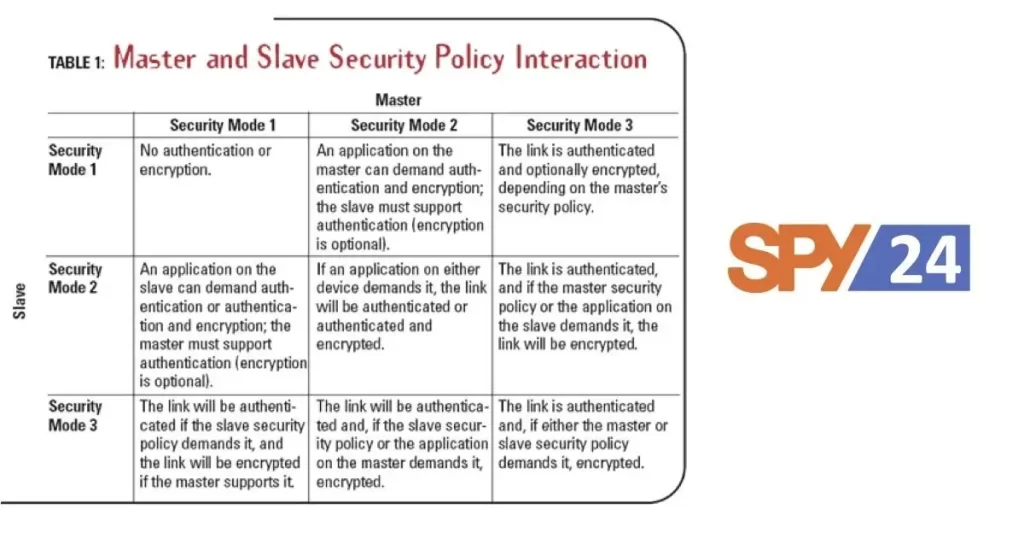
Today, Bluetooth is made into nearly all our systems and gadgets. These involve our computers, smartphones, iPods, tablets, speakers, game controllers, keyboards, and many other machines.
In this article, we will be concentrated on hacking mobile devices, tablets, and phones as they are the most prolific ground for hackers. The ability to hack Bluetooth can cause the compromise of any data on the system (pictures, emails, text, etc.), control of the device, and the ability to send unwanted info to the device.
Before we begin hacking Bluetooth, though, we require to figure out the technology, the terms, and the safety that is built into Bluetooth, if we desire to hack it successfully. In a short article like this, I can’t transmit an in-depth understanding of Bluetooth, but I do think I can give you primary wisdom that you can use in further tutorials/hacks.
Bluetooth is a universal protocol for low-power, near-field connection operating at 2.4 – 2.485 GHz using extension spectrum, frequency hopping at 1,600 hops per second (this frequency hopping is a safety size). It was expanded in 1994 by Ericsson Corp. of Sweden and named after the 10th-century Danish (Sweden and Denmark were a single country in the 10th century) King Harald Bluetooth.
The minimum feature for Bluetooth range is 10 meters, but there is no limit to the range that manufacturers might perform in their devices. Many systems have ranges as long as 100 meters. With particular antennas, we can extend the range even further.
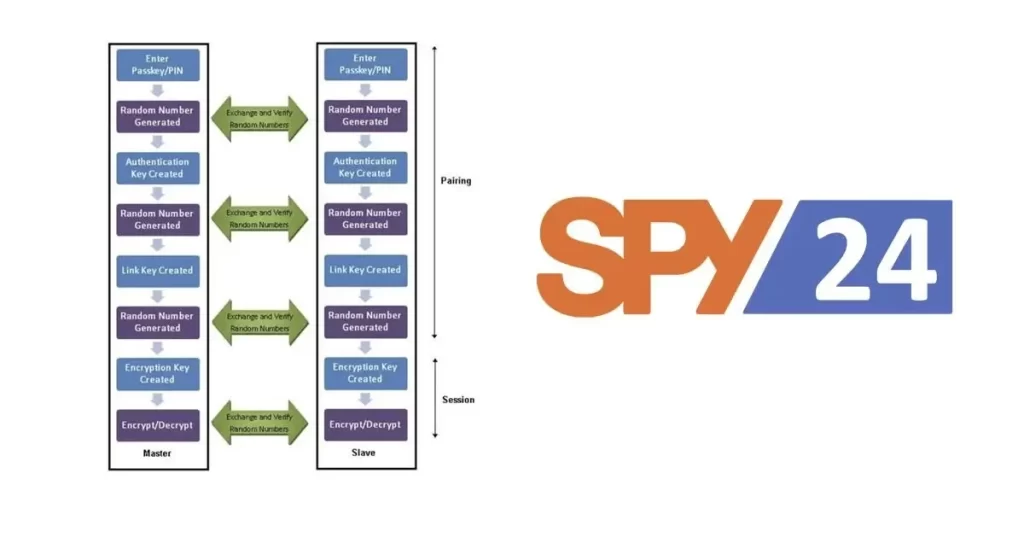
When two Bluetooth devices link, this is referred to as pairing. Somewhat any two Bluetooth systems can link to each other. Any discoverable Bluetooth device conveys the following data:
- Name
- Class
- List of services
- Technical data
When the two devices couple, they exchange a pre-shared code or link key. Each device has this link key to identify the other in subsequent pairings.
Every system has a single 48-bit signal (a MAC-like address) and usually a manufacturer-assigned name.
Basic Bluetooth Tools for Linux
With the increasing spread of Bluetooth peripherals such as keyboards and headsets, it can be hard to fancy using the wired versions of these machines sometimes.

On some Linux repartitions, Bluetooth is organized perfectly for you straight out of the box. Distributions like Ubuntu and Elementary make it simple for you to get Bluetooth set up and working on your system.
However, other distributions like Fedora and Arch Linux need you to do some setup before you can fully pleasure the profits of Bluetooth on your device.
Hciconfig
This Hciconfig is the primary Linux command line utility used for interacting with Bluetooth machines (Bluetooth dongle).
If you know Linux, you might already see the reference to other tools like ifconfig or iwconfig.
In other words, Hciconfig uses configured Bluetooth systems. Hciconfig publishes names and primary data about all the Bluetooth devices installed in the system.

The data you achieve to read from the Hciconfig are:
- The name of the joint is: “hci0“.
- How it is linked to a PC (either via a USB or built-in) here is the USB dongle.
- MAC address of the Bluetooth dongle
- It is currently running (UP flag) and you can look at received (RX) and transmitted (TX) packets.
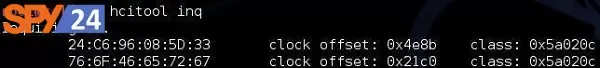
Hcitool
Host Controller Interface (HCI) The HCI provides a command interface to the baseband controller and link directory and access to hardware conditions and govern registers. Actually, this joint provides the same manner of accessing the Bluetooth baseband capabilities.
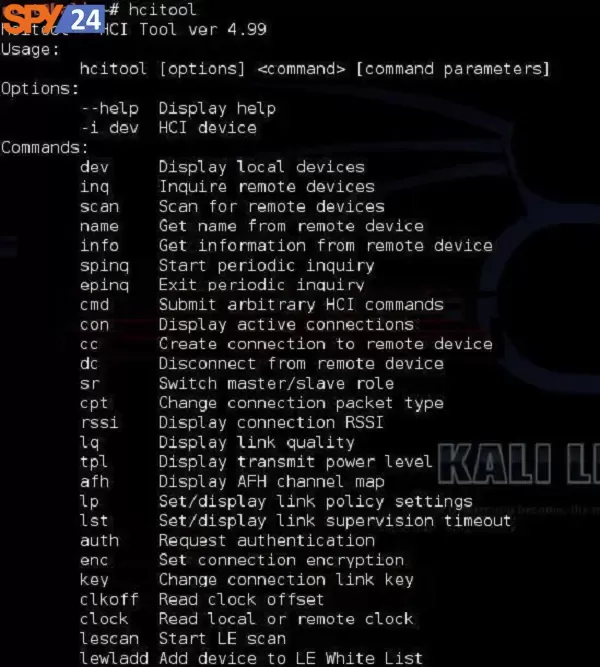

Sdptool
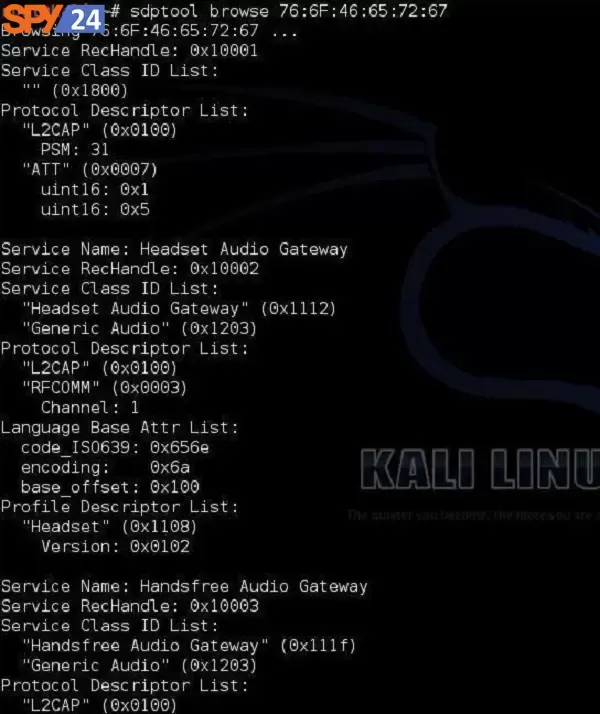
The program Sdptool can use to check which services are made available by a special system.
Tools to Hack Bluetooth in Kali
Kali also has a made-in tool for making Service Discovery (SDP). It lets you enumerate all the systems running on the Bluetooth system.
l2ping
We all recognize the ping utility from the IP world that is used to check the connectivity between IP nodes using the ICMP protocol. The Bluetooth world has its equivalent called l2ping.
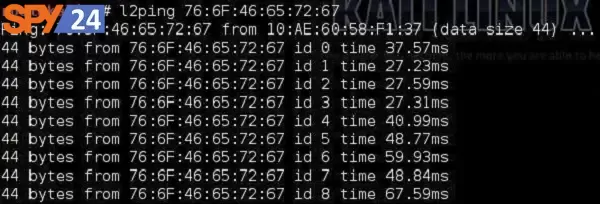
This detection tool lets the user check whether a particular device is within the range and is reachable for Bluetooth communication.
Conclusion
Bluetooth spy apps allow users a comfortable manner to follow the actions of other linked devices without needing physical attendance. With these kinds of apps, you can quickly track the location information of your family members or overhear their talks from anywhere in the world, giving you the health of mind that they are always safe. We hope you find this article in SPY24 useful! You can also read our other articles such as Best Phone Tracker Apps without Permission.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.



