The World’s Only Way To Spy App on an iPhone 13 Pro Max Tracking
In this article from SPY24, we will do a full review of the iPhone 13 Pro Max and we will check how this phone works. In addition, we introduce you to how to hack conversations and social networks in IOS phones through the SPY24 application.
Spy app for iPhone 13 Pro Max makes it easy to spy on iPhone 13 Pro Max
The iPhone 13 has many features that are not currently available in other iPhone models. One of these features is the possibility of using a spy application to track the location and behavior of another person. This can be especially useful for parents who want to keep track of their children or for business owners who need to keep an eye on their employees. There are many different spyware programs available, so it is important to choose one that is reliable and has a good track record.
Introducing the iPhone 13 spy program and its features
iPhone 13 is the latest version from Apple and it has new features. Among these new features is the possibility of spying on other iPhone users. There are a number of reasons you might want to do this, including looking after your children or employees. Whatever your reason, there are a few things you need to know before you start using the iPhone 13 spy app.
The iPhone 13 Pro is one of the most complete phones on the market with a 120 Hz screen, excellent charging, and a more efficient camera.
Appearance changes aside, Apple has focused on improving the iPhone’s screen, chip, and camera more than anything else in recent years. the battery has also been added to the list of important items, and the role of the camera is more prominent than ever; So bold that Apple claims to “bring Hollywood to your pocket” with the iPhone 13 Pro. Last year’s iPhone 12 Pro and iPhone 12 Pro Max were underpowered phones and challenged by expensive Android flagships, now it remains to be seen how the new iPhones will perform.
On paper, the iPhone 13 Pro experiences interesting changes compared to the previous generation; 1.5 to 2.5 hours of increased charging time, 50% more processing power compared to competitors, 2.2 times better camera performance in the dark, macro photography, and 120 Hz screen are among these features and changes.
Design and build quality of iPhone 13 Pro Max
The new iPhones are slightly different from the iPhone 12 family; Apple, abandoning the convex frame of previous generations, introduced iPhones with a flat and angular design to harmonize the design language of its smartphones and tablets. The iPhone 13 family also follows the same flat design language, with the difference that the new iPhones are now slightly thicker and heavier with increased battery capacity and improved cameras.
iPhone 13 Pro and iPhone 13 Pro Max are now 15 and 12 grams heavier and 0.3 mm thicker than their previous generation. You will feel the weight of 204 and 240 grams of the two phones and their 7.7 mm thickness. The iPhone 13 Pro Max is now about 13 grams heavier than the Galaxy S21 Ultra despite using a 0.1-inch, smaller display.
iPhone 13 Pro has a very high quality and manufacturing accuracy, all the parts are well mounted together; So by touching the border between the glass panel and the frame of the device, you can hardly notice the gap between them. In the front view, there is no plastic strip between the frame and the screen cover, and these two elements are mounted directly on top of each other. The display of the new iPhones is also protected by a cover composed of glass and ceramic, known as Ceramic Shield; A cover that is more resistant than all the glass used in smartphones.

The iPhone 13 Pro and iPhone 13 Pro Max screens are 6.1 and 6.7 inches, respectively, like the previous generation, and use the 19.5:9 aspect ratio. The most important difference between the front of the new iPhones and the previous generations is the dimensions of the screen cutout; For the first time since the introduction of the iPhone 10, Apple engineers have reduced the dimensions of the cutout by 20% by moving the conversation speaker opening to a gap between the screen protector and the device frame; Although the space freed from the screen is not used to display more information, such as battery charging!
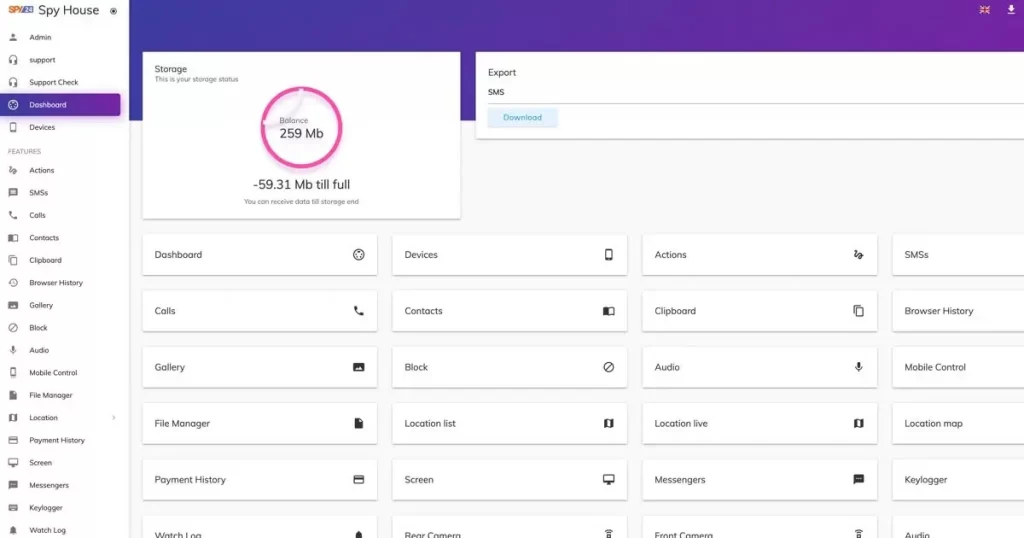
SPY24 program: hacking all types of iPhone and Android phones as well as the Promax13 model
Family Monitoring System SPY24 is a mobile software with very simple installation and activation that allows parents to control and manage their children’s activities on mobile networks such as iPhone and IOS phones.
Below you can see some features of the SPY24 program:
- Monitor calls and SMS along with date and time
- Report Telegram, Instagram, WhatsApp messages, etc.
- Continuous current position and traveled routes
- Websites visited and programs run
- With the ability to hide 100% of the program and remote management
- Ability to block websites, applications, and contacts remotely
Who can Install spy apps and software on your iPhone?
A professional hacker can be anyone around you, from a spouse, an employer, or even a complete stranger the guise of a professional hacker is truly impossible to spot – especially since spy apps are so readily available and the use of They are easy.
For most people, you are much more likely to get hacked by someone you know than a complete stranger.
Why would someone hack your iPhone Pro Max 13?
There are many reasons why someone might decide to hack you. The main reasons are either financial gain or collecting information about an aspect of your personal life.
Here are some examples of why someone might install a spy app on your iPhone and how it can abuse your private data:
- Access to private messages for use in divorce
- GPS location monitoring by wife hacking iPhone
- Full monitoring of unauthorized devices by employers
- identity theft: Once they have access to your personal information, a hacker can completely steal your identity. They may use your information to open new bank accounts, take out loans, or worse. It has the ability to completely destroy your life and leave you with a mountain of debt that you didn’t create – or at the very least cause enormous stress and waste of time.
- stealing money: If a hacker manages to steal your financial information, it’s common for them to use your information to purchase items online, ask for money from your contacts, or simply withdraw money from your bank accounts.
- Sell your data: Many hackers make a quick buck by collecting data from large numbers of victims and then just selling the information to others who use it however they want. Complete ID packages can sell for up to $100 each, given that hackers typically sell this data in large batches. If this happens to you, other hackers may target you in the future.
- blackout: Hackers can use the data they have stolen to blackmail you. This is usually something like: Pay me this amount of money otherwise, I will send these images and videos to all your contacts.
Is it possible to hack Apple and iPhone? And how do we understand this?
Yes. As Apple does not allow spy app scanning programs in its Apple Store, at SPY24, we have developed an innovative solution to the growing problem of spyware.
SPY24 is a program for your computer that you can use to scan your iPhone and determine if someone has installed spyware. Here’s why it’s perfect for keeping your iPhone safe:
- Easy to install on your PC – just connect your iPhone and follow the easy on-screen instructions.
- It only takes a few clicks and 2 minutes to scan your device.
- Nothing is installed on your iPhone, so a hacker won’t know you’ve scanned with software.
So, with the SPY24 family care application, you will be able to scan your iPhone and identify all existing malware and ransomware.
Types of iPhone spy software:
1. Hidden Spy apps
Hidden spy apps are the most common type of iPhone spying. These fees can easily be purchased for $30.
They have the ability to hide on your iPhone and gain access to a large amount of your personal information, including instant messages, emails, real-time location, photos, and more.
This type of spyware requires the hacker to have physical access to the victim’s device for a few minutes to install. Once installed, the hacker can remotely monitor all the activities of the infected device and in some cases even turn on the microphone and cameras and watch remotely.
2. iCloud backup attack
An alternative method available to hackers who want to steal iPhone data is the iCloud Backup Attack. This is when a hacker, as opposed to going after your physical device, will target your device backups stored in your iCloud account.
This is dangerous because if a hacker gets access to your backup, they can download all the data you have backed up or even clone your entire iPhone.
This type of attack does not require access to the device but requires the hacker to have the victim’s Apple ID login credentials. And since it is 100% done over the internet, it is almost impossible to detect.
Fortunately, it’s quite easy to protect it by enabling two-factor authentication with your Apple ID.
3. Defiant organizational plans
This type of hack relies on bypassing the App Store’s strict security measures by installing apps in a different way. It uses a method that is usually reserved for app developers and larger companies that need their own “custom” apps.
This method allows hackers to install apps on your phone that are not approved by Apple, such as Spywares. It is also not as powerful and intrusive as a hidden spy app, but it is compatible with a wide range of devices.
4. Misuse of legal programs
Pre-installed apps like “Find Me” and “Google Maps” can be used to share a victim’s location with a hacker. For this, it is necessary for the hacker to gain access to the victim’s device for a short period of time. A hacker can also log into the device’s web browser to collect browser history and online account login details.
Since no malicious program or code is installed, it is very easy for this type of attack to go unnoticed for months or even years, by which time the hacker has acquired a lot of information.
5.ZeroDay exploits
ZeroDay exploits are somewhat rare but can be devastating to those affected.
They are called Zero-day because these exploits have not yet been discovered by security researchers and thus no fixes have yet been released for the affected apps/devices.
Zero-day exploits are usually created when hackers discover weaknesses in operating systems or third-party applications.
When this weakness is revealed, it is immediately exploited, and developers are trying to fix the problem as quickly as possible to minimize the risk to their user information.
If a zero-day is found in a popular app or device, it can affect millions of users. In some cases, more advanced exploits can even infect a device with spyware without the hacker ever having to touch the victim’s device.
Introducing some applications and tools to learn about iOS hacking methods
xSellize Game Hack app
Anyone who is a computer game player knows that they have to work hard for paid games. xSellize Game Hack has solved this problem and allows hackers to download paid games for free. Thousands of games such as Game Boy, Nintendo, SEGA, and many other games are hacked by this game hacker which is specially designed for IOS and can be played for free. In addition, this game hack program provides functions such as anti-method swizzling, hack program data, real-time tracking, and automatic detection of vulnerable function calls. To be able to use this program, you must install jailbreak on your IOS phone.
iSpy hacking program
iSpy is one of the must-have hacking tools to learn reverse engineering and dynamically analyze iOS apps. The iOS hacking program easily uses web GUI and can perform various programming functions including Cycript integration, class dumps, automatic jailbreak detection bypasses, automatic bypasses SSL certificate, objc_msgSend pass-through used for logging, and real-time call tracking. In order to use this tool, the jailbreak operation must be done on the phone.
Myriam iOS Security App
The Myriam iOS security app was developed by a GitHub security researcher known as GeoSn0w, who wanted to create a learning platform for techies to become great iOS hackers in the future. As a result, this iOS hacking tool is the best place for any novice iOS hacker to start to develop their skills. Among the things that novice hackers can do with this tool include authentication, changing and converting in-program data, program activation bypass, identifying jailbreaks, in-program resources, and variable changes.
What is the best spy application for monitoring Apple and iPhone in the world?
Above, we have given you a complete list of attacks, software, and ransomware. But we should add that SPY24 is the best option for monitoring iPhones. the SPY24 application gives you great access to both the protection and safety of your personal information and allows you to easily install the SPY24 software by having your children’s phone for one to two minutes. With this app, you can Spy on their geographic location, messages, activities, and sites they follow.
So, before downloading or trusting free sites and apps, be sure to read the required materials for this work.
Is it possible to hack and eavesdrop on an iPhone without jailbreaking? How does SPY24’s iPhone listening application work?
Yes, you can control the iPhone and iPad without jailbreaking, among the features of the SPY24 application for iPhone are as follows:
- No need to jailbreak the iPhone
- No need to install
- Full access to iCloud
- Compatible with iOS 14.4
- iPhone control program without jailbreak
- iPhone and iPad control software with jailbreak
- Enjoy unlimited features
- The WhatsApp message control program
- Hassle-free location tracking
- Compatible up to 14.4
Conclusion:
In this article from SPY24, we discussed whether it is possible to hack an iPhone. Also, we went to the full review of the iPhone Pro Max 13 phone and ways to hack this popular product of Apple and we checked different ways to hack.
Then we went on to discuss why you should use SPY24, the best iPhone hacking software.
Frequently Asked Questions
Can the Apple iPhone Pro Max 13 be hacked?
iPhone Pro Max 13 is one of the latest models released in the market, and we at SPY24 have discussed its security, as well as the possibility of hacking and its various features.
Do the software or sites that claim to hack the iPhone really work?
Yes, there are many different ways to hack iPhones, you can hack iPhone phones using these ways.
How can I find out if malware or spyware is installed on my iPhone?
You can do this with the SPY24 software under Windows or Mac by just connecting the phone to the system.
How to hack iPhone without jailbreaking? Is this possible?
Using the SPY24 iPhone application, you can hack iPhone without jailbreaking.
Does SPY24 also work on iPhone phones?
Yes, SPY24 for iPhone also has many features, including full scanning and checking of the phone, or real-time tracking and tracking of the iPhone by installing the SPY24 application.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.




