How Spy App Without Target Phone Works? What are the best ones?
Numerous individuals can’t help thinking about how a Spy App without Target Phone works. On the off chance that you feel dubious about your mate or accomplice or are a parent and notice the withdrawal disorder regularly of teenagers and young people in your kids, you should check their online exercises. As much as it is conceivable to keep an eye on a telephone nowadays, it very well may be trying to locate a productive Spy App without Target Phone. Note that perhaps the primary contemplation to make while searching for the best government agent on the web is security. Getting to the objective telephone remotely with a Spy App without Target Phone for Android without the valid telephone is for having power over children, workers, and others to screen their exercises and keep them in mind. With the Spy App without Target Phone for Android without the objective telephone, one can get to the total highlights of the valid telephone like SMS messages, versatile calls, GPS area, and online media exercises like Facebook, WhatsApp, WeChat, Skype, Viber, Instagram, different destinations and applications.
This spying is done exclusively to have command over the exercises of the concerned individuals. The approach of cell phones has changed how individuals are living. Their ways of life, propensities, kinships, activities, culture and social tendencies are changing in the present innovative world. It has gotten basic for one to have a registration for one’s life. Consequently, the requirement for spying without the other individual realizing it is being finished.
Individuals have a duty regarding this general public to be unblemished from these changing patterns the world over. In the current day lives, the more significant part of individuals has occupied in the family setup, so the working guardians can’t keep a tab on the children. Subsequently, the Spy App without Target iPhone has become a requirement for monitoring their children. Most managers and corporate Chiefs utilize the Spy App without Target Phone for keeping a tab on their most significant heads as the world is seeing merciless rivalry in the field of corporate business. All said and done, do you think keeping an eye on somebody is exploitative?
Not the least, if one is accomplishing to benefit the ones they are keeping an eye on, it tends to be kids or the high school kids who are developing and are interested to know the world.
Highlights of a Spy App without Target Phone
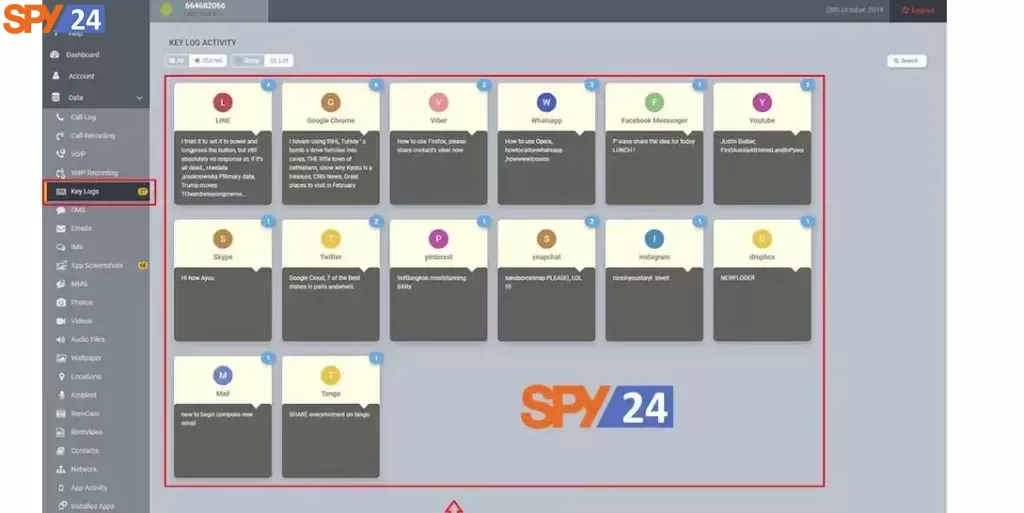
The Spy App without Target Phone can break the start-to-finish encryption innovation of most informing applications by bypassing their encryption to have a peep into the goings-on in those web-based media applications. There is some best-shrouded Spy App without Target Phone for iPhone to access all the objective telephones’ highlights. A portion of the exercises the Spy App without Target Phone can approach is:

- Instant messages
- Live Calls
- Online Media Apps and Websites
- GPS Location
- Messages
- Reports
- Call Log History
- Call length
- Telephone directory
- Change of SIM card Messages
- Pictures Gallery
Recall that these exercises may vary in a Spy App with Target Phone.
How Does the Spy App Without Target Phone Work?
There are two strategies for the establishment of a Spy App without a Target Phone. The first is to get to the objective telephone and download the concealed Spy App without Target Phone. The subsequent one introduces the Spy App without Target Phone by bringing to sites that offer admittance to the objective telephone without introducing the product. Some best specialist co-ops provide to do this work for you. These specialist organizations have their terms and conditions for providing this assistance to you, wherein you need to consent to their terms and states of understanding approach.
From that point forward, you need to give the subtleties and data on the objective telephone. At that point, the specialist co-op interfaces you to the valid telephone with the connection pinging code. The primary goal is to call or send an instant message to the objective phone. When the individual with the aim phone reacts, a code is created naturally. It finishes the third-party referencing measure, hence giving you indispensable admittance to the valid phone. Presently you can approach the objective telephone.

Besides, you can see yourself what’s going on the opposite side, and what they are doing, their calls, message messages, photographs, posting on Social Media like Facebook, Instagram, texts in Facebook Messenger, WhatsApp, WeChat, Skype, Viber, and their perusing history on the web, without the other individual realizing that you are viewing.
One can utilize these government agent applications without the objective telephone for some reason. Out of which you can use as a type of proof for nailing the other individual with the aim of telephone, number 1 is Call streaming: you can approach and tune in to the calls of the individual who is settling on the decisions or accepting the calls.
Number 2 is Call recording: this gives you admittance to the discussions, which you can record for some time later. There are numerous advantages and disadvantages to utilizing this framework. Having a falcon eye on the messes, you are attempting to control various outcomes. Juvenile children and youngsters respond uniquely in contrast to more youthful children. In general, the more youthful children will hear you out while young people and youngsters have more protection from your arrangement of control, which is severity.
While this can have a helpful result when a Corporate Chief screens his high-flying heads and significant workers, bridling the high-flyers in a corporate world has become perhaps the central element in the advancement of corporate organizations.
Will individuals notice the Spy Apps?
You need to accomplish the objective’s telephone; you need to keep an eye on Android phones correctly on the off chance. Really at that time, the government operative application can be downloaded on the telephone. You would then be able to download the application to the phones of your children or staff. There is anyway a scope of approaches to distantly download them.

You need to introduce the government agent application on the pointed Android telephone for only a few minutes, and you’re finished. Note that the program symbol should be covered up on the objective versatile, so they don’t know about establishing a covert operative application. You can sign in to your online dashboard and track all exercises on your Android target telephone straightforwardly when the Spy application is empowered. Person-to-person communication applications like Facebook, Twitter, WhatsApp, Skype, and so on incorporate. For all Android gadgets, the methodology stays as before.
Now let’s take a look at some of the best Spy Apps.
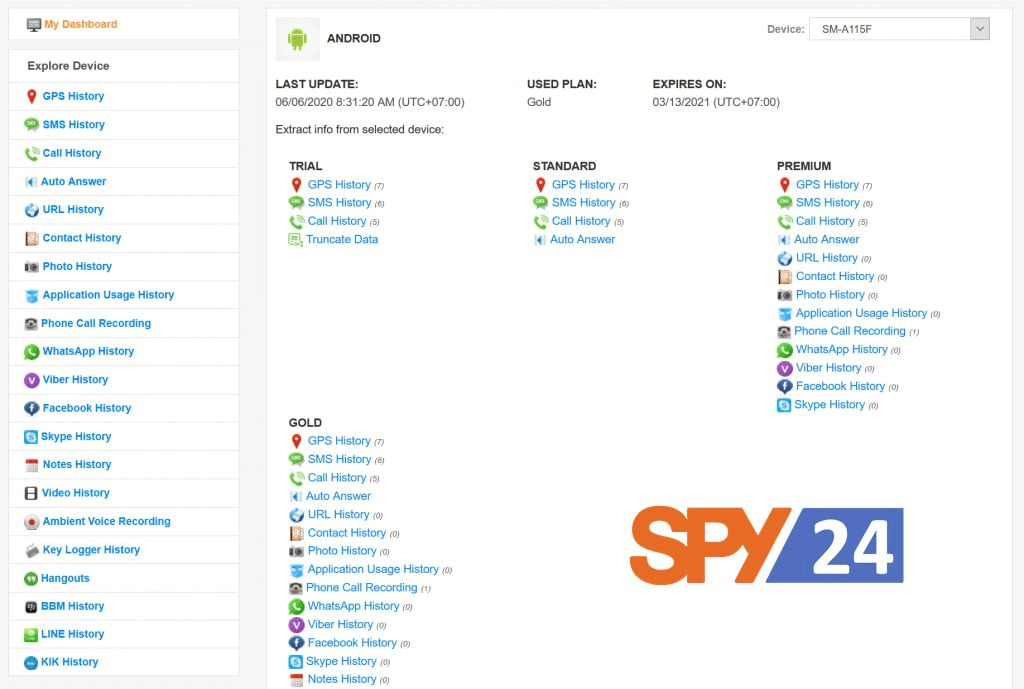
SPY24
Like each other application on this rundown, it is a fantastic alternative for a telephone checking application on your Android and iOS gadgets. SPY24 has shown up all through a small bunch of significant driving tech stages; Huff Post, and Life Wire, since initiating the application into the commercial center for accepting a substantial remainder as a brilliant Spy App Without Target Phone. Setting up SPY24 takes not over 10 minutes! You should make a free record. Your email address will be your username and to be utilized to check your record enrollment.
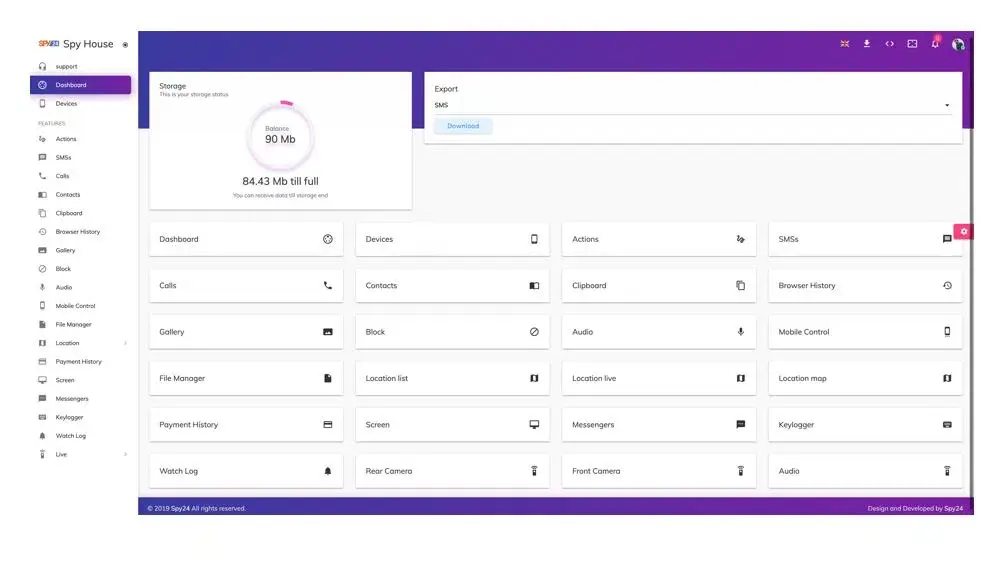
Some of SPY24’s features include:
- Remotely controlling a cellphone
- KEYLOGGER for monitoring keystrokes in messaging apps
- 24/7 instant alerts for certain keywords and social media activity
- SPY24 analytics for summarizing repetitive activities in a specific period
- Email and online activity monitoring, including bookmarks
- Recording phone calls and surroundings
- Multimedia file and appointment tracking
- SMS/MMS monitoring
- Call tracking with details on incoming, outgoing, and missed calls
- GPS location tracking
- Remote control of the targeted phone for actions like data deletion and picture taking
- Live viewing of the phone’s screen and surroundings without detection
- File manager browsing of the targeted device
- Schedule restrictions to block access to applications
- Calendar and contact monitoring
- Analysis tools for generating reports on targeted person’s activities
Overall, SPY24 is a highly comprehensive and advanced monitoring software that is suitable for parental and employee monitoring needs.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
Spyier
If you have been perusing this post so far, you should be pondering, shouldn’t something be said about parent-youngsters spy applications? Spyier has you covered. It was planned in light of the typical parent. We know about the inherent risks on the web. While we can’t altogether keep the children off the web, we can screen their online exercises. There are a ton of search inquiries on the web, asking something very similar – “Would someone be able to keep an eye on my telephone without contacting it”? How about we quit wasting time? Indeed, that is a chance. With Spyier, you unquestionably can. If you have your gadget synchronized across various devices, all you require is to input the iCloud qualifications on the connected gadget, and Voila! Spyier is fully operational.
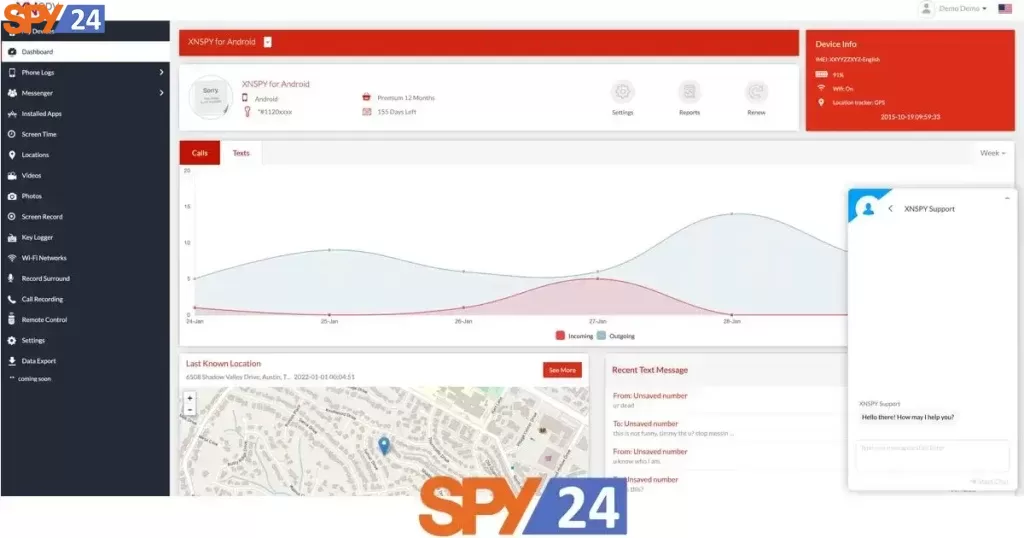
XNSPY
Xnspy gives you admittance to screen an objective Android gadget, yet regarding the clients’ security. Notwithstanding, a similar isn’t correct with the cost as it doesn’t fall set up with different contenders. Xnspy gives a wide cluster of highlights and parental control applications, essentially centered on controlling and setting time cutoff points for kids’ utilization of their gadgets while likewise impeding their admittance to grimy sites.
Spyera
Spyra used to be a significant part of the applications spying world. It packs a ton of highlights offering many strategies to get information from an objective Android telephone. Spyera lost its place as its estimate got tremendous, genuinely gigantic. With the inundation of new contenders, spyera couldn’t keep up and lost severally to the newcomers.
TheTruthSpy
TheTruthSpy is an instrument with the best highlights and is simple to utilize. This device is for most guardians as a result of its observing capacities. One can follow their children with this covert operative tool. GPS area capacity is excellent for this government agent apparatus. You can approach call logs, perusing history, web-based media exercises, and text, media messages on WhatsApp. Indeed, even an individual lacking technical information can deal with this application without any problem.