Instashell Download Github for Pc – kali Linux – APK
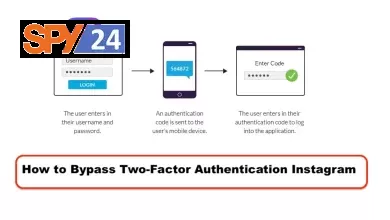
INSTASHELL: FREE INSTAGRAM HACKING TOOL: Hackers target social media profiles because thousands of people use them for employment and income. This time, cybersecurity specialists from the International Institute of Cyber Security (IICS) will demonstrate a brute force attack technique that bypasses Instagram’s login limits.
Instashell allows users to try an infinite amount of passwords by evading Instagram’s brute-force attack restrictions. This script leverages Android ApkSignature to authenticate and the TOR network to swap IP addresses after blockage to continue a persistent attack.
As usual, IICS cybersecurity specialists are not liable for any malicious use of this content, which was written for informational purposes only.
Today, I’ll discuss Kali Linux’s chosen instashell utility. Instagram brute force tool. Instagram password cracker. First, we know Instashell Tool (brute force attack). in Kali Linux?
How to Brute Force Instagram Password Instashell
Instashell, a multi-threaded brute force attack tool for Instagram, can bypass login limiting and test limitless passwords at +400 passwords/min utilizing 20 threads.
Instagram Password: Linux InstaShell Brute Force Instagram Password.
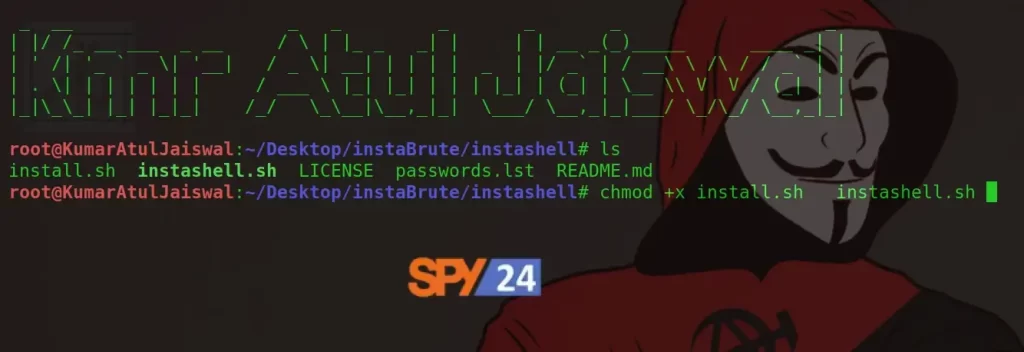
Install
git clone https://github.com/g0r60n/InstaShell: This link is not working ( Temporary unavailable )
Try this link: git clone https://github.com/maxrooted/instashell
sudo apt install gitgit clone https://github.com/g0r60n/InstaShellcd instashellchmod +x instashell.shls
This command changes file permissions.
Change permission to run.
chmod +x install.sh instashell.sh( alter the mode with executable permission ) ( change the mode with executable permission )
TOOL LAUNCHING
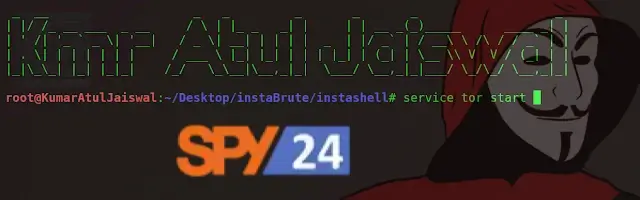
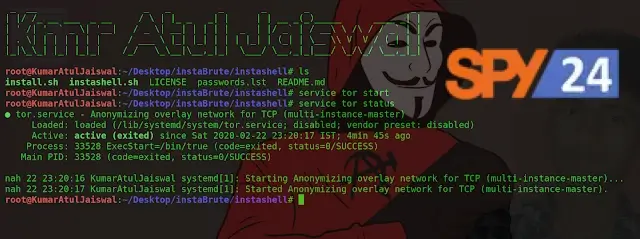
Cybersecurity experts say that Tor and curl must be installed in order for the script to work. If they are not, configure:
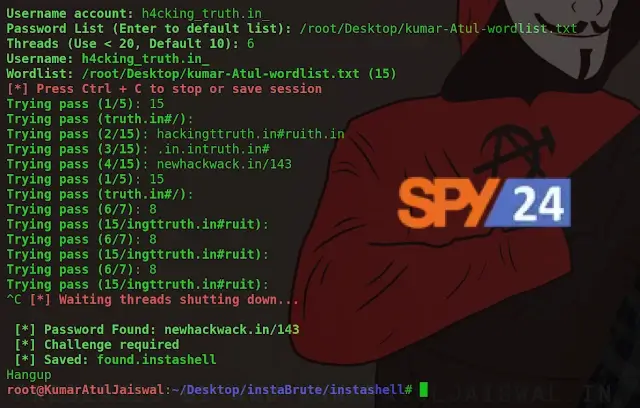
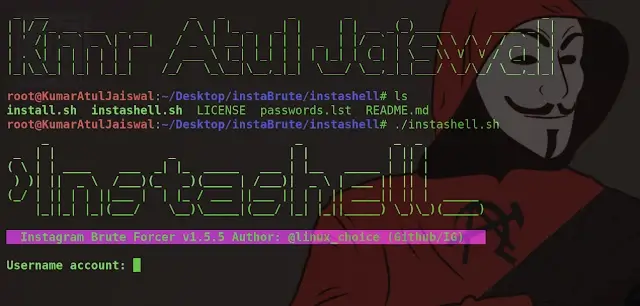
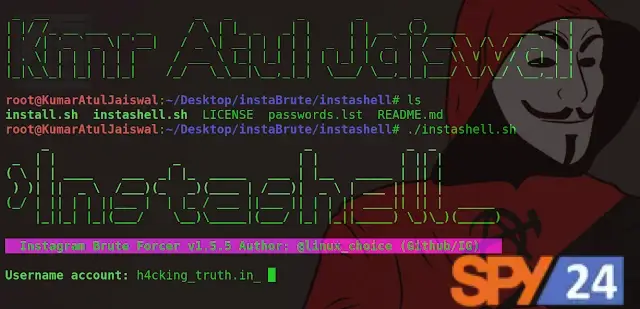
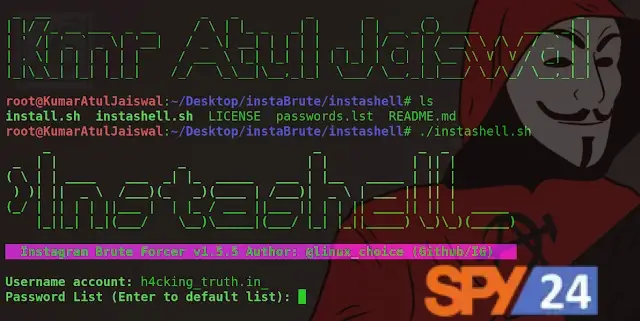
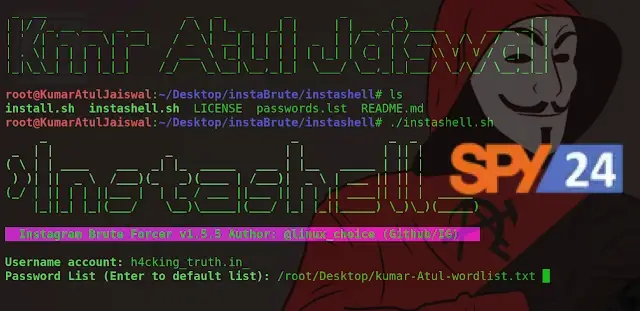
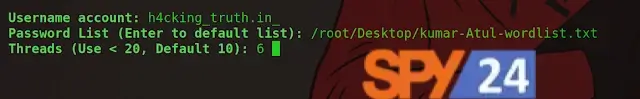
sudo apt install torsudo apt install curl./instashell.shservice tor startNow enter the victim’s Username, the list of words, and the value for Threads.
Account name: spy24.app
Password List: /root/Desktop/Password-wordlist.txtThreads: 6
After the wordlist is done (like 15 words), press Ctrl+C to stop the session or save it.
Password Found: SPY24app
Challenge required
Saved: Found. instashell

Video Tutorial: Don’t forget to subscribe
How to Hack Instagram Accounts with InstaShell
SPY24 offers a powerful tool for hacking Instagram accounts called InstaShell. This tool makes it easy to hack any Instagram account, and in this blog post, we’ll show you how to use it.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
How to Use InstaShell
Using InstaShell is simple. Just enter the username of the Instagram account you want to hack into the “Username” field and click “Start Hacking.” Once you do that, InstaShell will do its magic and give you the password for the account within seconds. It’s really that easy!
Once you have the password for an account, you can do whatever you want with it. You can log in and view private photos, post on behalf of the user, or even change the password and lock out the real owner of the account. So, if you’re looking for a way to hack into someone’s Instagram account, be sure to give InstaShell a try.
Find out how to make the most of Instagram
Follow these steps to learn how to hack Instagram: As you may know, Instagram is one of the most popular online networks in the world. Many people today have their own pages on Instagram, where they not only promote their businesses but also themselves. They start out and make money through the Internet.
Instagram is one of the most popular mobile apps and, in general, one of the most important social networks in the world. It has a lot of followers. Also, a lot of people use it. Every network in cyberspace can be hacked, and security is important to many of us.
Understanding how to hack Instagram can help us make our page more secure and make it harder for other people to hack. This article on SPY24 will talk about some of the best ways and tools to hack Instagram, as well as give you a step-by-step guide to hacking Instagram.
1: Encrypt Instagram password
Most Instagram hacking guides use this strategy. Passwords are the easiest way to hijack an Instagram page. Password cracking is one of the most common ways to get hacked and lose money. Instagram cracking tools:
InstaShell InstaInsane
- InstaCheck
- InstaHack
InstaInsane and InstaShell are computer apps you can download and use. These two apps require a password list before use.
For instance, hacking a 1999-born person is difficult. His birth date can be used to create a password and stored in a “password” file if it suits either the solar or Gregorian calendars. This file can also contain personal information like a loved one’s first and surname names, pet’s name, email address, and other favorites.
After creating the possible password file, open the software and start hacking. These hacking tools can test 1000 passwords in a minute and give you a person’s account password in seconds.
In contrast, the Instax tool is easier to use. Insta Hack is web-based, thus no password file or other specific steps are needed. You can hack someone quickly and easily by opening this hack and entering their username.
Make your Instagram password strong enough that software and tools can’t guess it. On encryption sites like LastPass, random passwords are also the best.
2: Social engineering
Social engineering, which we’ve covered on SPY24, may be used to hack computers. Social engineering is deception. Your relationship with them can provide you access to their phone or hacking information.
Social engineering allows for several computer hacking tactics. More specifically, social engineering can be used to hack others to improve your job performance without others knowing. If you’re hacking a friend, you need to get close to them for social engineering.
After establishing enough intimacy, you can request information or persuade the person. Social engineering has two fascinating points: if your request is denied, you are probably not close enough to the individual yet, and if you ask too many questions, you may create concerns about the person. Thus, approach the person cautiously.
Social engineering is also utilized for phishing assaults, and many consider it the most dangerous hacking tactic. First, learn about social engineering hacking, then don’t share important information with anyone. “What is Social Engineering?” provides a more detailed explanation. Look.
Twitter and Instagram. Hack a system.
3: Hack Instagram’s security weaknesses
Exploits are commands or codes that allow you to access your operating system or account. Websites advertise Instagram hacking exploits, but their accuracy and efficacy are unknown.
4: Hacking Instagram with many applications
Hackers or script hackers use other people’s programs or scripts to hack their targets. Hacking a personal Instagram account does not require expert hacking skills. Hacking into computers and stealing data is possible with many viruses and applications.
Keyloggers are among the best Instagram hacking tools. Keylogger software like IKeyMonitor lets you see all the information individuals enter into their phones, including their usernames and password. Remote access Trojan (RAT) is another option. Remote Access Trojan (RAT) lets you access another person’s data remotely. This trojan virus effortlessly infiltrates the target’s phone and texts you all the information.

5: Thermax Instagram hacking
One of the most popular tools for hacking social networks is Thermax. It runs on Linux and Android. Linux-based Termux hacks and cracks passwords. Watch the video below to hack Instagram with Thermox.
Who hacked Instagram?
People hack Instagram for various purposes. Hacking Instagram is widespread for these reasons:
To access and restore your account,
password Online activities As we know, hackers hack several accounts daily to generate money. Black hat hackers breach Instagram accounts to demonstrate dominance, steal followers to sell, or extort money from victims.
Why hack Instagram?
Learning how to hack accounts can help secure your website. For instance, if you can crack your Instagram password, it’s a bad one. You must change your password immediately. SPY24 offers Instagram hacking tutorials. Follow these procedures to assess your Instagram account’s cybersecurity and avoid getting hacked.
We recommend two-step verification on all major social media platforms if your account is stolen. If your account is compromised, the hacker will have trouble logging in. Two-step verification protects social media accounts from hackers.
We tried to teach you several Instagram hacking strategies in this SPY24 article to help you secure or penetrate your page.

Below are the FAQs.
Hack Instagram?
Instagram, like any social media site, can be hacked.
Instagram security issues?
Instagram, one of the safest social media networks, has security issues.
Can brute-force decrypt this password?
Hacking or regaining an Instagram account involves cracking the password.
Instagram hacking training has ambiguous goals. Hacking Instagram lets you verify and improve account security.
How is hacking a private Instagram account?
Security and data security have become increasingly crucial to people. Personal Instagram accounts can be hacked. It looks that virtual or real doesn’t matter!!! Insecurity worries people. As technology and digital life evolve, everyone’s biggest concern is virtual life security. For several years, in addition to our many identities, we have had a virtual identity, which we appreciate and are committed to.
Instagram, one of the most popular social networks, affects many people’s lives nowadays. Social media creates our virtual selves. A popular virtual network attracts hackers, which worries many individuals. Currently, hundreds of websites sell Instagram hacking tools or offer techniques to hack Instagram.
Are these claims credible? Is the size correct?
Hackers try to breach Instagram accounts to generate money or achieve other goals, however, it’s practically hard to break into an Instagram server. We will build on this SPY24 Social article by explaining five safe ways to hack personal Instagram accounts.
Password hacking Instagram
Passwords are the best way to keep Instagram hackers out. If these passwords are basic patterns like 1234, hackers can easily hack them. Thus, we recommend a password with more than 8 digits and a mix of letters, numbers, and characters.
aH, # 942d & 7 $ 9kl @ is a superb, unbreakable password. Cracker passwords are obtained by hackers using crack software.
Many passwords are not in this format, therefore cracker passwords can be used to breach private accounts. One issue exists. The program’s technique and method of cracking the password may take several days if the password is secure.
This method rarely requires a hacker-victim link or program installation on the target device. This attack requires a weak password tool. This attack is less likely if the target user’s password is easy to guess. The target user’s Instagram password is harder to crack if it’s strong.

Phishing attacks on Instagram are used to compromise the social media site.
Hackers create Instagram accounts. They ask the user to enter his Instagram account, confirm a series of modifications that have been made to it, or log out of his Instagram account. Fake a website. Users are often deceived into thinking there is a problem with their Instagram account, and as a result, they follow the hacker’s instructions and enter their account details, including their account login password, on the false page. The hacker can access their Instagram. If nothing happens, you may receive a suspension email with your Instagram username in the subject line.
If you own this Instagram account, follow the link to unblock it. Click the email link below and follow the steps. You enter your Instagram login details after clicking the link from anywhere. You gave an abuser your confidential information. Phishing assaults, which steal bank card information, are also frequent.
This phishing attack takes several forms. A phony account and social engineering can steal your information or, at worst, construct a fake Instagram login page to deceive you. However, typing your details quickly is risky.
One crucial step is needed to hack someone this way. You must be imaginative and precise in your work. Deception is only limited by your imagination. “Different hacking methods” covers phishing.
Hacking Instagram for followers:
You’ve probably seen words like “increase followers in a few minutes” or “increase free followers.” We’ve all been tempted to adopt this strategy to grow our Instagram audience, ignorant that none of these stories are genuine and that it’s actually hurt us.
There are legal and ethical ways to gain Instagram followers. However, profiteers sell systems that claim to increase Instagram followers, likes, and comments ethically. They can also hack many accounts by widely advertising these applications. Users must log in to these programs using their Instagram username and password (found by searching “Instagram user panel”) to access their user panel.
Prevent having phony followers and believing that more followers mean more success to avoid such scenarios. In the next phase, you must utilize genuine and secure software for all your needs and be sure you intend to access the information. No obligation.
If you want to hack into people’s private Instagram accounts, you can use mobile programming to create a fake app that appears to boost the user’s followers or likes but actually gives you their password. However, hiring an experienced Android coder may take time.
Instagram hacking or spying software
Use a tool that hacks other people’s Instagram accounts to become a pink hat hacker. Visit “What is a hack and who is a hacker?” to learn more about network hackers. Tools and programs can also access a website.
These tools allow instant account hacking. Programs can hack Instagram. After downloading and installing this app on your phone or computer, enter the username of the person you want to contact to access their private account in minutes. Latest Instahack Instaleak Arro App hacking tools:
Mobile app Instahack
Monitoring programs are the second technique you can employ to access personal page data. Surveillance applications are disguised on a phone to avoid complications. Install this app to control the other person on the phone. One crucial element requires your attention.
Some surveillance programs, especially Universal ones, monitor your job. If you hack other people, like your spouse, the software won’t work and restricts your internet connection. Some of these security tools cost money.
Phone-hack any Instagram account! Keyloggers can hack Instagram.
Hackers may use you to test key loggers to breach Instagram. Keyloggers, unlike other viruses, are installed on the victim’s phone or computer and record all keystrokes in a log file that the hacker receives.
Keyloggers can steal a personal Instagram account if the user logs in via a web browser and logs out after each session. The hacker can install a keylogger on a victim’s phone and wait for the victim to log into Instagram only once, following which the keylogger will record the password and give it to the hacker.
Why would a hacker desire a regular user’s account?
For instance, if someone is upset at you and hires a hacker to steal your personal information, he may get revenge on you because you didn’t protect it. Someone can log into your account without justification. Instagram hacking is widespread, so you should protect your account. They may hack your account to extort money.
According to the law, hackers can only hack Instagram accounts for a specified cause. Hackers generally leave celebrities’ accounts to gain fame. They accomplished their mission after that. Hackers have made a lot of money selling celebrity Instagram accounts because of their big followings. Due to severe hacking and privacy laws in different countries, most hackers leave users’ accounts after a while to show their strength and popularity to their followers.

Why learn this hack?
We know how immunizations work. Our bodies learn to oppose vaccines because they’re not very precise. Learning how to hack Instagram can also help you secure your account and avoid getting hacked.
In this SPY24 article, we showed you five secure and effective techniques to hack your personal Instagram account so you can handle it or hack it if necessary.
Below are the FAQs.
Are there Instagram private page hacks?
Phishing, password cracking, and other means can breach these pages.
Phishing?
Pheasants employ “social engineering,” or “the art of deceit,” to induce people to log into a bogus website and reveal personal information.
Why would hackers hack our systems?
In recent years, 50% of hacks have been done to watch others. Hackers attack you for several reasons.
Why hack Instagram?
so you can protect your page from these tactics and hack someone if necessary.
The team of professionals and specialists educates and informs individuals about how to secure their social media accounts and prevent third-party websites from accessing them. Hackers can steal your data. Hack, responsibility, and repercussions requests are never accepted by this collection. Studying and following our instructional themes is also a secure and dependable approach to strengthening security, reducing the number of persons who enter your private regions, and keeping yourself safe.
You want to feel safe on social media and help protect your data.
This service does not accept services for hacks, responsibility, or consequences under any title or condition. The team of professionals and specialists only educates and informs social network users about preventive steps to raise their awareness and security and prevent unwanted access to their data in the system (hacking). We think that studying and following our instructional subjects is a secure and trustworthy way to strengthen security and avoid intrusion into your private regions.
You want to feel safe on social media and help protect your data.
Conclusion:
InstaShell is a powerful tool that makes it easy to hack any Instagram account. In this blog post, we’ve shown you how to use it. So, if you’re looking for a way to view someone’s private photos or post on their behalf, be sure to give InstaShell a try.