Instasheep – Tool Hack Instagram Accounts Download For PC – Apk – IOS Free

Are you looking for a way to take control of your Instagram account? Look no further than Instasheep! The newest tool to hit the market is taking the social media world by storm with its unique and powerful ability to hack into Instagram accounts. Download Instasheep now and take back control of your Instagram account today!
Instasheep: Don’t Fall Prey to Instagram Account Hacking
Instagram is one of the most popular social media networks in the world, with over 1 billion active users. But with its growing popularity, it’s also become a target for cybercriminals. Recently, a new tool was released called Instasheep that can be used to gain access to someone’s Instagram account without their knowledge or consent. In this blog post, we will explain what Instasheep is and why it’s important to protect yourself from this type of attack.
What Is Instasheep?
Instasheep is an automated tool that was released on GitHub recently and is used by hackers to gain access to someone’s Instagram account. It works by exploiting a vulnerability in the Instagram API (application programming interface). The vulnerability allows hackers to gain access to someone’s account without their knowledge or consent. Once inside a user’s account, hackers can take control of their personal data and potentially even steal money from them.
How Can You Protect Yourself From Instasheep?
The best way to protect yourself from these types of attacks is by using strong passwords and two-factor authentication. Strong passwords are those that are at least 12 characters long and contain numbers, symbols, and uppercase and lowercase letters. Two-factor authentication (2FA) adds an extra layer of security by requiring users to verify their identity by entering a code sent via text message or email when logging into their accounts. Additionally, you should always make sure you are running the latest version of your operating system so any security patches are applied as soon as possible.
It’s also important to be aware of phishing scams and other malicious activities online as they can lead to your accounts being hacked if you accidentally click on a malicious link or download an unsafe file attachment. Finally, if you think your account has been compromised in any way, contact Instagram immediately so they can help you recover your information before any harm is done.
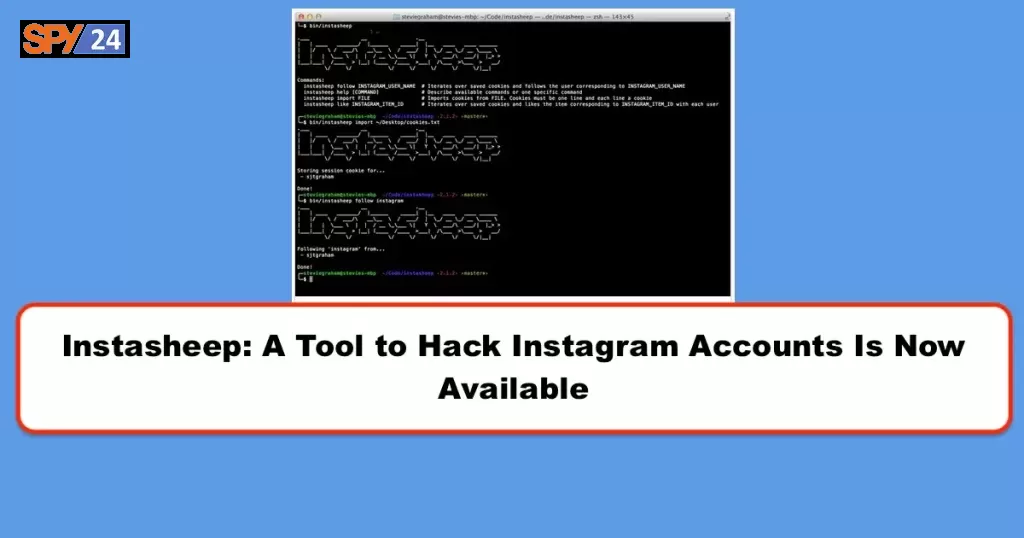
Instasheep: A Tool to Hack Instagram Accounts Is Now Available
Instasheep is an Instagram account hacking/session hijacking tool that takes advantage of a weakness in the Instagram mobile app.
With the instasheep hacking tool hacks Instagram accounts with a key hack a very important vulnerability in the Instagram mobile app has been notified. With this high Instagram vulnerability, you can completely take control of an account.
Hacker wrote two days ago about a serious problem with the Instagram app for mobiles, which is the most popular way to share photos and videos. The problem lets an attacker take over a user’s account and access private photos, delete the victim’s photos, edit comments, and also post new photos.
Yesterday, a London developer named Stevie Graham released a tool called “Instasheep.” The name is a play on the 2010 Facebook stealer Firesheep, which is a Firefox extension that can be used to automatically hack online accounts with a click of the mouse.
Instagram makes API calls to non-HTTPS endpoints with session cookies in the request headers allowing full session hijack by a malicious actor.
How to hack Instagram with instasheep
Stevie Graham, a London-based developer, recently submitted a security bug report to Facebook in which he sees it as a very high-security vulnerability on Instagram that allows anyone to share a user meeting based on data taken through Hijack a public Wi-Fi network. Stevie Graham had discovered this very important Instagram vulnerability but found that Facebook hadn’t yet modified that security bug and shared it with Facebook executives, and when he wasn’t awarded any prizes from Facebook Inc., which owns Instagram, Stevie Graham began to build a proof-of-concept tool to exploit Instagram by an extension that was used for the browser.
Firefox can trouble Instagram online accounts with just one click and provide Instasheep. He posted a message saying, “Refusing to pay the reward. The next step is to create an automated tool for the massive hacking of user accounts. Very important vulnerability. Please correct it quickly.”Using this vulnerability can cause Instagram users to have interception attacks because Instagram sends data with an unencrypted and unencrypted cookie. A hacker can reuse these session cookies intercepted on a system or browser to hack victims’ Instagram accounts. With the Instasheep tool, Stevie Graham wants to force Facebook to correct the vulnerability it has discovered.
Hacking Instagram simply and how to prevent it
Instagram is the kind of popular social network that can contain important information from its users. This important information and a large number of users have led many hackers to look at people’s Instagram accounts, especially those with a large number of flavors, as a target and seek to hack into their accounts.
But as you know, Instagram is one of the social networks that have more than a billion users and has been able to keep its users safe so far. So what causes us to sometimes hear the news that different people’s accounts have been hacked and even among our friends to know people whose Instagram accounts have been hacked?
Follow along with us to talk more about this and explore the hacking methods of Instagram and the apps and software that exist for this action.
How to hack Instagram
A hacker has several strategies to access private information and control a person’s Instagram, which is mentioned below on a case-by-case basis:
Access to the device that the person used to log in to their accounts, such as a phone or tablet
- Obtaining the desired person’s account password in various ways
- Penetration of users’ information on Instagram’s main servers
- Installing a spy app on the desired person’s device and obtaining information
Training Instasheep
In general, these methods are the most famous ways to hack Instagram or any other app or service like Instagram. Of course, there are some innovative solutions that may also be used depending on the hacker’s creativity. But in general, the methods mentioned above express the generalities of Instagram’s hacking methods. In the first method, we actually see a type of unauthorized access that someone takes over our device without permission and connects to our Instagram account. At the same time that our device is in his possession, he can gain control of our Instagram and access all our account information on Instagram and all our messages.
In this method, there is no need to perform complex operations. In the second method, the hacker uses the tool at his disposal or uses the user’s lack of knowledge to obtain the password of the person’s account and uses that password connects to his Instagram account. This Instagram hacking method itself can include using a variety of methods such as social engineering, making phishing pages and emails, or using password-breaking apps. In the third method, the hacker must have a lot of expertise in the field of hacking and security, and so far a successful person has not done it yet.
In this method, you have to go through different layers of security and access Instagram’s main servers, which is very complicated and time-a-time. The fourth method is also a common method in the field of Instagram hacking in which the hacker succeeds by installing an app on an individual device. Get information from other apps like Instagram. In this method, the hacker can use only other people’s programs that are built for this purpose and can design such a program himself. Instagram servers have a lot of security.
We will only examine the second and fourth methods here and we will not do anything with other methods.
Get Instagram password
The method that is very common and is currently very common is obtaining the password to other people’s accounts. If someone succeeds to get the password to our Instagram account, it can easily access our private information on this social network and even send messages to others instead of us or post different pictures and videos.
This is very vital for all Instagram users and is also much more important for those users who have a lot of flavors on Instagram. But in what ways are hackers succeed are able to get the password of other people’s Instagram accounts and even succeed hack Instagram celebrities as well? We have introduced some of the most popular methods.
Hacking Instagram with social engineering Instasheep training
In this way, the hacker succeeds by building trust between himself and the person in question and using psychological tricks. It is allowed to obtain the password to the account of the person in question from his or her own language.
In addition, the hacker may not directly disclose the password to the hacker, but the hacker obtains the password to the Instagram account from his/her conversations and the information that is exchanged between them, such as the date of birth, the child’s name, or otherwise. Also, in some cases, the hacker uses the same method to persuade his victim to install a malicious program on his device, which can be a killer capable of stealing passwords. Hacking with social engineering has a very high success rate and many hackers use it. In the way of social engineering, the hacker convinces you to do whatever he or she wants.

Hacking Instagram with a Password Cracker
Password Cracker is a program or process during which a successful hacker obtains the user’s password. In this way, there is no need to install the app on the target device or the connection between the hacker and the victim, and can only be through password fragile tool, successfully carried out the attack.
The success rate of this attack is directly related to the simplicity and guessability of the target user’s password, and the more the user uses the safer and stronger passwords for their Instagram account, the more difficult the hacker will have to break the password. Read also | Instagram Farsi: The best alternative to Instagram after filtering, including these methods, can be mentioned the use of Termux, a Linux terminal emulator on Android.
Using Kali Linux operating system and various modules to break passwords on this operating system is also another way to hack people’s Instagram. Also, using packages designed solely to break Instagram passwords can also be very fruitful.

Instagram hack with instasheep:
The more complex the password you use for your account, the lower the chance of it being cracked.
Hacking Instagram with a phishing attack
In the phishing and counterfeiting method, the hacker attempts to forge a valid account or a valid page and asks the user to enter their information on that fake page to log in to his Instagram account or to confirm a series of changes to his account.
In this situation, the user is usually duped because he feels that there is a problem with his Instagram account, according to the hacker’s commands, and enters his account information, including the password to his account on the fake page. For example, the hacker will send you an email with an Instagram username and the email text will tell you that your Instagram page has been blocked due to an invalid login attempt.
If you own this account, click on the link listed below the email and follow the other steps. After clicking on the specified link, the user will log in to a page that is designed exactly like the Instagram login page and enter their account information to log in to Instagram. By entering this information on the fake page, you have actually provided your account information to the hacker, and the hacker can simply log in to your page using the password you provided yourself and access your private information.
Phishing attacks play a key role in the theft of information, including people’s bank card information
Instagram hacking app
As mentioned in the Instagram hacking method using the spy app, it is easy to use existing products made for this or another purpose. In this way, you need to install the app on the device of the person you plan to hack into Instagram, and then enter a series of settings manually in it.
After successful installation, the program secretly starts collecting information and sending it to another destination. Many internal and external applications are designed for this, each of which has its own features.
For example, the Android Hamyar Market app is a program to monitor and control the behaviors of family members in cyberspace that can be installed on the mobile phones of people under the age of 18 and then send complete information about their user’s activities in cyberspace to parents.
It is merely a monitoring program for children and family members and is very useful given that the cyberspace platform can be very risky for adolescents.
Are you curious about what your children are doing on Instagram? Do you want to know what kind of conversations they are having or what kind of pictures they are sharing? Are you worried about their online activities and want to keep track of their activities?
If these are your concerns, then a spy app like SPY24 is the perfect solution for you. SPY24 is an easy-to-use and reliable spy app that can provide you with detailed insights into your children’s Instagram activities. With SPY24, you can easily monitor your children’s messages, photos, stories, and more. It is also a great tool for employers who want to keep track of their employees’ online activities.
SPY24 is a powerful Instagram spy app that offers a wide range of features. You can monitor all of your target’s activities on Instagram, including what posts they like, comment on, or share. You can also see the conversations they are having with other users and even view their direct messages. Moreover, you can also track their Instagram followers and even block suspicious accounts.
SPY24 is the perfect spy app for keeping an eye on your children’s online activities. It is a reliable and user-friendly app that is compatible with both Android and iOS devices. It also comes with a range of features that make it easy to monitor your children’s online activities.
SPY24 lets you read Instagram messages
We’ve already found that there isn’t a specific app that says you can hack someone else’s Instagram account by installing it on your device. But if you install the SPY24 app on the target device, you can spy on the Instagram account of that device and see Instagram messages, Instagram Direct, and other parts of the account.
- Spy Instagram Messages
- SPY24 is a tool for spying.
- You can also keep an eye on social network apps like Instagram with the SPY24 monitoring tool.
- Keep an eye on direct messages
- Look at shared pictures and videos
- Keep an eye on all the Likes and Comments.
- Use your Control Panel to get direct access to all the information.
- Applications to hack Instagram
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
If you are looking for a more powerful and feature-rich Instagram spy app, then mSpy and Xnspy are two great options. Both apps offer a wide range of features such as geolocation tracking, call, and SMS monitoring, access to social media accounts, and more. Both apps also come with a range of plans and pricing options to suit your needs and budget.
No matter which spy app you choose, SPY24, mSpy, or Xnspy, you can be sure that it will give you detailed insights into your children’s Instagram activities. With SPY24, you can easily keep an eye on your children’s online activities and ensure that they are safe from any potential harm. So what are you waiting for? Get started with SPY24 today and keep your children safe and secure.
The download hacking Instagram with instasheep
The Instasheep app is widely known on the Internet as the Instagram hacking app. It is interesting that this app is not for downloading Instasheep or you can hardly find the download link of the Instaship app. From downloading the Instasheep app the more interesting tutorial talk is the use of this app, which seems stranger.
Different websites in training to use the Instagram app mention that after rooting the phone and installing the busybox app you should run the Instasheep program and by giving the user name of the Instagram account the target of the program automatically hacks the target Instagram account.
It is quite clear that there is no such program that you can only infiltrate the Instagram account of the person in question by installing it on your phone and giving you the username or Yuzrinim Instagram account of others. Because even assuming there is such a method, Instagram spreaders will definitely be quickly looking for a way to prevent it.
How to hack Instagram with Instasheep training keylogger
Another way to discuss it online is to teach Instagram hacking with keyloggers. Perhaps we should first explain what a keylogger is and what helps in hacking Instagram. keylogger is a software program that aims to use this program to receive and record any characters entered by the user by input tools such as keyboards. keylogger is also referred to as a spy and hacking tool, which is why a hacker can be informed of all the words typed by that person by installing the keylogger program in someone else’s system.
How to hack Instagram with Keylogger 2023
But in training Instagram hacking with a keylogger, the method used to hack everything else is mentioned. In this way, you need to install the Kilger app in the target person’s system, and then if you enter the target person and the password of your Instagram account, you will be aware of it and you can access other people’s Instagram accounts.
Instagram hacking tutorial and prevent hacking so we’ll find out here that hacking other people’s Instagram or hacking, in general, is not that easy and you definitely can’t hack other people’s accounts by installing an app on your device under the title of Instagram Hacking App.
The widespread publicity on this issue is completely untrue. But considering that the most common method of hacking Instagram is engineered with a keylogger or hacking. Engineering hacking means having direct access to the target device to access the login information. So here’s how we’ll make recommendations about preventing your Instagram account from being hacked.
To prevent Instagram from being hacked, make sure that unknown and strangers don’t have access to the device on which you use the Instagram app.
This way you will avoid the most common hacking method. In the next step, prevent any miscellaneous, anonymous, and suspicious apps on your device and remove them immediately from your device if you see any apps you don’t know about. Installing antivirus programs to detect malicious programs and preventing the installation of hacking programs is the best method.
Instasheep Instagram performance report
Instasheep – Instagram account hacking tool released. Two days ago, we reported on hackers’ news about a major issue in the most popular photo and video sharing service, the Instagram app for mobile phones, which allows an attacker to hijack users’ accounts and successfully access private photos, delete victim photos, edit comments as well as post new images.
Yesterday, London developer Steve Graham released a tool called “Instasheep” to play in the 2010 Firesheep Facebook heist, a Firefox extension that can be used to compromise online accounts in certain situations using mouse clicks. Graham discovered the Instagram issue years ago and was shocked when he learned that it hadn’t been fixed by Facebook yet.
He used the tool after Facebook claimed it refused to pay for the bug because of its reported vulnerabilities affecting the iOS Instagram mobile app. Graham tweeted about it: “Vow rejected the bug. The next step is to write an automated tool that allows for the extensive hijacking of accounts.”Very serious, violent FB.
FB Responsible Disclosure · GitHub:
Please correct.”Facebook’s biggest social networking giant was reportedly aware of the issue related to its iOS Instagram app and was working on a fix with HTTPS deployment in its portfolio, but it remains unclear how long it will take. Correct use of vulnerabilities can expose iOS app users to personal attacks (middle). As we said earlier, Instagram sends unencrypted data with session cookies. An attacker can then use these HTTP session cookies intercepted on another system/browser to hijack the victim’s Instagram account session.
Graham wrote on YCombinator: “I do not accept that the barrier to abuse is too much. All it takes is for a skilled person to release a tool so that even a code script can use it. At that time, Pandora’s box has been separated.”Mike Krieger, founder of Instagram, through the same YCombinator website, has responded to the issue, saying, “We have steadily increased our HTTPS coverage – for example, Instagram Direct, which we launched in late 2013, is 100% HTTPS.
From the program, especially delayed sensitive reading endpoints such as the main feed and other browsing experiences, we are seriously trying to run HTTPS while making sure we don’t lag behind in our performance, stability, and user experience. Hopefully, it will be completed soon, and we will share our experiences on the eng blog so that other companies can learn from it as well. To force Facebook’s hand, Graham applied an “Instasheep” tool to automate the process, although the company needs to speed up its efforts to deploy HTTPS.
Steps to reproduce (on Mac OS X):
Jump on an open or WEP-encrypted wifi access point
Put your network interface into promiscuous mode filtering on i.instagram.com
- sudo tcpdump -In -i en0 -s 2048 -A DST i.instagram.com
- Wait for someone to use the Instagram iOS app on the same network
- Extract the cookie request header from the resulting output
- Use sessionid cookie parameter to make any API call as that user Even HTTPS endpoints like direct messages.
- curl -H ‘User-Agent: Instagram 6.0.4 (iPhone6,2; iPhone OS 7_1_1; en_GB; en-GB) AppleWebKit/420+’ \
- -H ‘Cookie: sessionid=REDACTED’ \
- https://i.instagram.com/api/v1/direct_share/inbox/`
This Returns The User’s Direct Message Inbox As JSON
I was able to perform a session hijack on my own account on my laptop while someone else browsed Instagram on my iPhone.
I was also able to:
- take the cookie sniffed from the iOS app
- go to instagram.com as an unlogged-in user.
- set document.cookie = $COOKIE
- navigate to a profile
- see I’m logged in as that user
There is some screwy behavior where ‘instagram.com/’ gets into a redirect loop, I will see if I can fix that. However, going to ‘instagram.com/someones_profile’ works and shows me as logged in.
I think this attack is extremely severe because it allows full session hijack and is easily automated. I could go to the Apple Store tomorrow and reap thousands of accounts in one day, and then use them to post spam.
Recommendations:
Use SSL everywhere
Graham Put Up The Steps Needed To Repeat His Findings:
Connect to a Wi-Fi access point that is open or has WEP encryption.
Put your network interface’s filtering on i.instagram.com into promiscuous mode: Sudo tcpdump -In -I en0 -s 2048 -A DST i.instagram.com
Wait until someone else on the same network uses the Instagram iOS app.
From the output, get the cookie request header.
- Use the sessionid parameter of a cookie to make any API call as that user. Even HTTPS endpoints like direct messages:
- curl -H ‘User-Agent: Instagram 6.0.4 (iPhone6,2; iPhone OS 7_1_1; en GB; en-GB) AppleWebKit/420+’ \ -H ‘Cookie: sessionid=REDACTED’ \ https://i.instagram.com/api/v1/direct share/inbox/`
This gives back the user’s direct message inbox in JSON format (JavaScript Object Notation).
This kind of attack is similar to the “Firesheep” attack that happened in 2010 and caused Facebook to switch to HTTPS for user sessions on its pages. Graham called it “Instasheep” in a Twitter chat about it.
Ars has tried to get Facebook to say something about the bug but has not heard back. We’ll add new information to this story as it comes in.
If you want to keep hackers from getting into your account and make it safer, you should do things like:
- Choosing a password for your account that is hard to guess. (Use more than 8 characters, capital letters, small letters, symbols, etc.)
- Set your Instagram account up for two-step verification.
- Etc.
You can also read the article How to secure your Instagram account to learn more about how to keep your account safe.
- Conclusion
Instasheep is an app that lets you get into other people’s Instagram accounts. Once you learn how to use it, it’s easy to do. In this article on SPY24, we talked about the different ways to hack Instagram and showed you how to do it with Instasheep. By reading this article, you can use this tutorial, and we hope you find it helpful.
Q1: What is Instasheep?
A1: Instasheep is a tool that allows users to hack Instagram accounts.
Q2: How does Instasheep work?
A2: Instasheep uses advanced technology and algorithms to access Instagram accounts. Once it has gained entry, it can make changes to the account, such as changing passwords, posting content, and accessing private messages.
Q3: Does Instasheep work on all devices?
A3: Instasheep is compatible with all major operating systems, including Windows, Mac OS, iOS, and Android.
Conclusion: Cybercriminals are always looking for new ways to exploit vulnerabilities in computer systems and social media networks like Instagram are no exception. Instasheep is one such tool that has been released recently and it can be used to gain access to someone’s account without their knowledge or consent. Fortunately, there are steps everyone can take—like using strong passwords and two-factor authentication—to protect themselves from this type of attack. If you think your account has been compromised in any way, contact Instagram immediately so they can help you recover your information before any harm is done!




