Instagram hacking tool
While Instagram is a great way to share photos and connect with friends, it can also be a breeding ground for online predators. A new Instagram hacking tool has been developed that allows users to see the private posts of any user, regardless of whether they are following them or not. This tool could be used by stalkers or other malicious individuals to gain access to sensitive information. So, how does this tool work, and what can you do to protect yourself from being hacked? Read on to find out.
All You Need to Know About Instagram Hacking
Instagram hacking is a huge topic of conversation, and for good reason. With the rise of social media comes the risk of data breaches and security vulnerabilities. It’s important to be aware of the different types of Instagram hacking, as well as how to protect yourself from it. In this blog post, we’ll dive into what you need to know about Instagram hacking so that you can stay safe online.
Types of Instagram Hacking
The most common type of Instagram hacking is through malicious apps or websites that claim they can hack an account and provide access to private information. This type of hack typically requires that someone enters their login credentials into a website or application in order to gain access to the account. Unfortunately, these websites and applications are often set up by hackers who may be looking to steal personal information, credit card numbers, or other valuable data.
Another type of Instagram hack involves gaining access to other accounts through phishing scams. In this case, hackers will send messages with malicious links in them, asking people to click on them in order for them to “verify” their account or gain access to a special offer. These links often lead people directly to a scammer’s page where they are asked for personal information like passwords and credit card numbers in order for the hacker to gain access.
Lastly, there have been reports of hackers using bitcoin wallets as part of their strategy when it comes to gaining access to an account on Instagram. The idea here is that hackers will create fake accounts with profile pictures that look similar enough so as not to appear suspicious and then send out messages offering users money if they enter their bitcoin wallet address into a field on the page. Once entered, the hacker has full control over the wallet and can use it however they please – including sending all funds in it directly back out into their own wallet address without permission from the user themselves!
Conclusion:
As you can see, there are many different types of hacks that target Instagram users every day. It’s important for everyone using social media platforms such as Instagram to stay aware of these threats and take the steps necessary in order to protect themselves from becoming victims of any type of hack. By following best practices such as avoiding clicking on suspicious links sent via direct message, not entering login credentials into unfamiliar websites or applications, and being mindful when dealing with cryptocurrency transactions online – SPY24 users can keep their accounts safe from potential threats posed by hackers!
1. How to hack an Instagram account?
2. How to get someone’s Instagram password?
3. How to hack Instagram without the software?
4. Is it possible to hack an Instagram account?
5. How to hack Instagram with CMD?
6. How to hack Instagram using Kali Linux?
7. What is the easiest way to hack an Instagram account?
8. How to hack an Instagram account without downloading anything?
-

How Can I Hack My Husband’s Phone for Free?
Are you considering hacking your husband’s phone for free? It can be a daunting and potentially dangerous task, especially for…
Read More » -

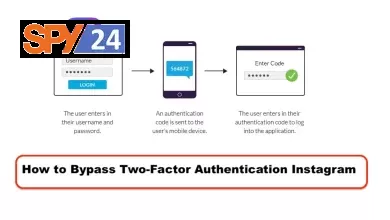
How to Bypass Two-Factor Authentication Instagram
(This article covers how to bypass two-factor authentication on Instagram. Learn how to use methods like SMS, email, biometric authentication,…
Read More » -

Instasheep – Tool Hack Instagram Accounts Download For PC – Apk – IOS Free
Are you looking for a way to take control of your Instagram account? Look no further than Instasheep! The newest…
Read More » -

How To Hack Instagram Accounts Using Termux?
Do you want to know how to get inside the world of Instagram and take control of its functions? Have…
Read More » -

How to Hack Someone’s Instagram Without a Password
If you’ve ever wanted to know how the pros hack someone’s Instagram without even knowing their password, the answer is…
Read More » -

How to Hack Private Instagram Accounts?
Are you a spy looking to gain access to private Instagram accounts? If so, then you’re in luck! We’ve put…
Read More » -

Instashell Download Github for Pc – kali Linux – APK
INSTASHELL: FREE INSTAGRAM HACKING TOOL: Hackers target social media profiles because thousands of people use them for employment and income.…
Read More » -

Best 11 Instagram Hacking Apps for iPhone and Android
Instagram is a great way to share photos, information, and other things with your friends and family. It gives you…
Read More »