Pathfinder Rat Tool Remote Access Software Download Github
Having access to a secure and dependable remote access tool is essential in today’s digital world. While there are plenty of great options out there, choosing the best RAT software for your needs can be difficult. In this blog post, we cover the top-rated tools for remotely accessing computers and networks. You’ll learn about the features each provider offers as well finding out what detection and prevention methods should be used to protect yourself from malicious attacks. By understanding these tools, you’ll be able to make informed decisions on which product or service suits your requirements best. So let’s dive into exploring some of the best RAT software & detection techniques available on the market!
Exploring Remote Access Trojans (RATs) and their Tools
Have you ever heard of a Remote Access Trojan (RAT)? They are malicious software tools used to gain access to remote computer networks. RATs allow an attacker to control the targeted system remotely, making it easy for them to steal data or even take control of the entire system. If you’ve ever wondered how RATs work and what kind of tools they use, keep reading!
How RATs Work
RATs are typically spread through email attachments or file-sharing programs. Once installed on a system, it can be used to collect sensitive information such as passwords, credit card numbers, and other confidential data. Additionally, RATs can give attackers full control over the targeted system, allowing them to install additional malware or delete files.
Types of RAT Tools
There are several different types of RAT tools available for download on the internet. One popular example is Pathfinder RAT, which is a free open-source tool that allows users to remotely access computers and perform various tasks such as creating/deleting files, changing user settings, and executing programs. It also supports file transfers between two computers connected via a network connection. Another type of RAT tool is Blackshades RAT which is a commercial software package developed for use in cybercrime activities such as identity theft and fraud. It provides attackers with the ability to monitor keystrokes, capture screenshots, and even disable security programs on the target machine.
Security Measures Against RATS
The best way to protect against RATS is by using strong passwords and keeping your operating system up-to-date with the latest security patches. Additionally, you should only download software from trusted sources and avoid clicking on suspicious links or opening email attachments from unknown senders. You should also install anti-virus software on your computer and scan your system regularly for potential threats. Finally, be sure to keep backups of your important data so that if your computer does fall victim to a RAT attack you can restore it quickly without losing any data in the process.
Pathfinder RAT Tools Free
Powerful HTTP RAT FUD Backdoor Binder and web-based Application System Surveillance Monitor Locate. Track. Manipulate.

You have a remote-controlled tracking device in your pocket
Pathfinder RAT is a web-based surveillance monitor and app binder malware program developed by SPY24 Group. Pathfinder is one of the most effective and well-engineered Remote Administration tools (RAT) programs. It is the ultimate tool for mobile surveillance, to take over remote devices easily and undetected; the software creates an automated 100% FUD (Fully Undetectable) persistent backdoor designed to take full control of the devices through adding code to the legitimate apps. The backdoor, acting as masked malicious software, gives attackers full access to perform different actions on the target device.
Pathfinder-RAT_2.16.2 (.exe, .dmg, .AppImage)Pathfinder-RAT_1.42.9_latest_stable (.apk x86_64)
Screenshots Pathfinder RAT
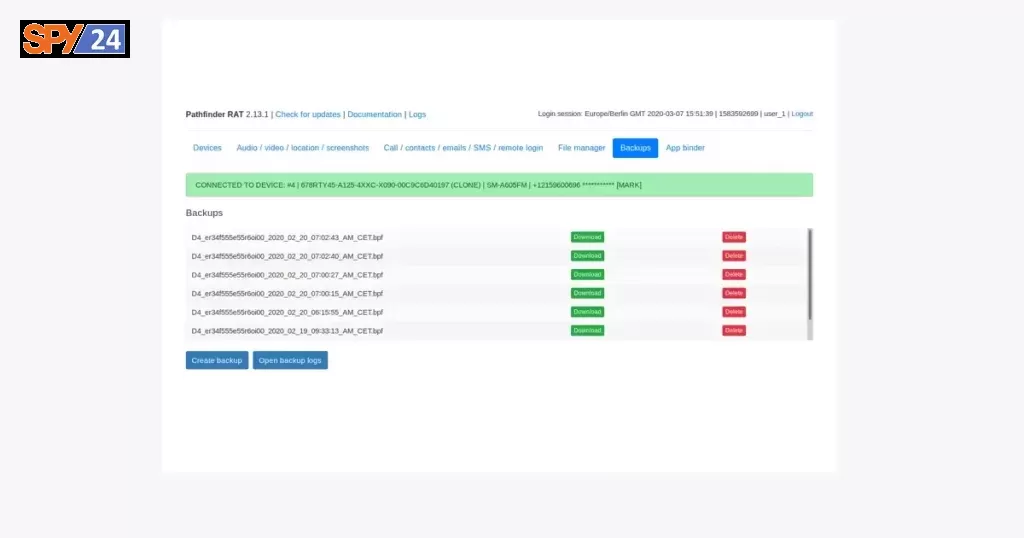
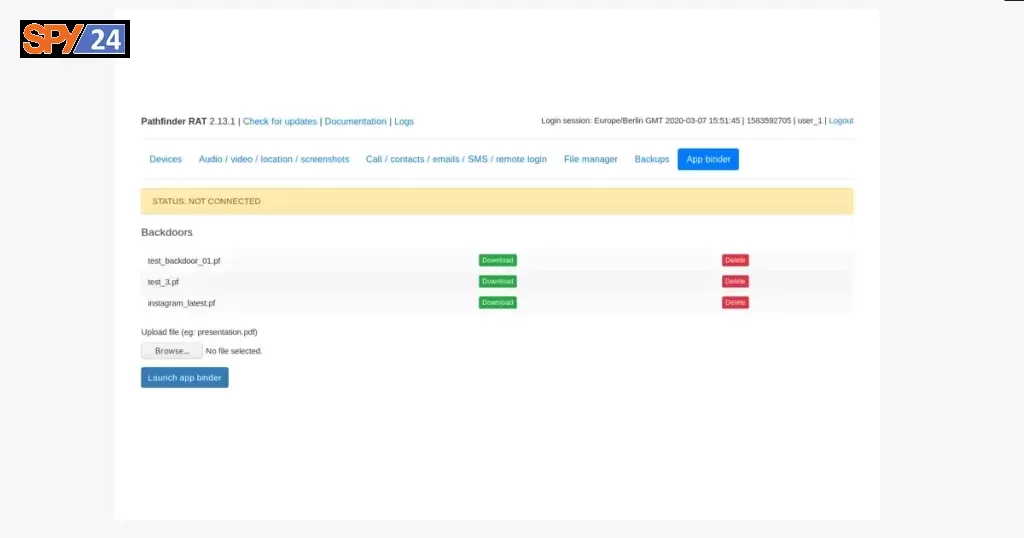
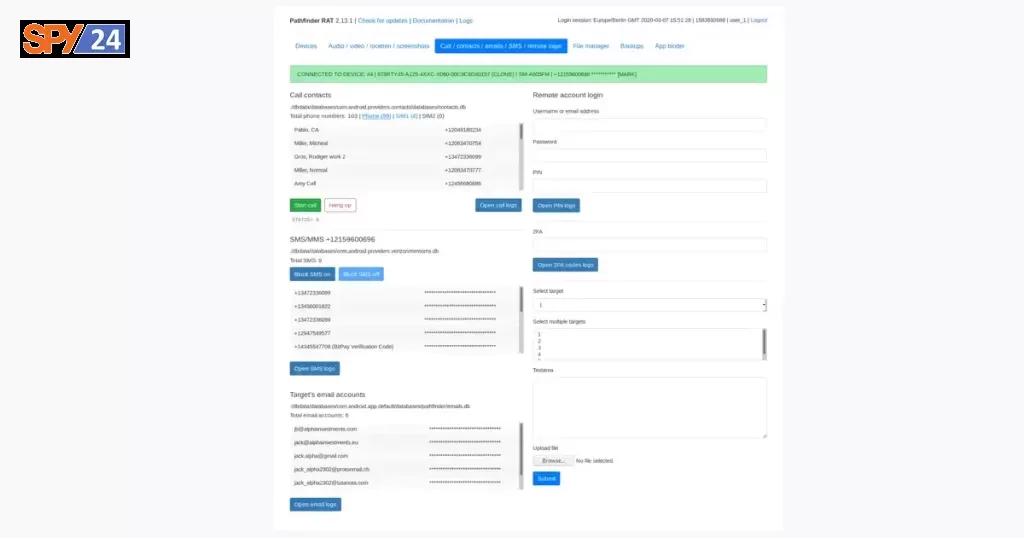
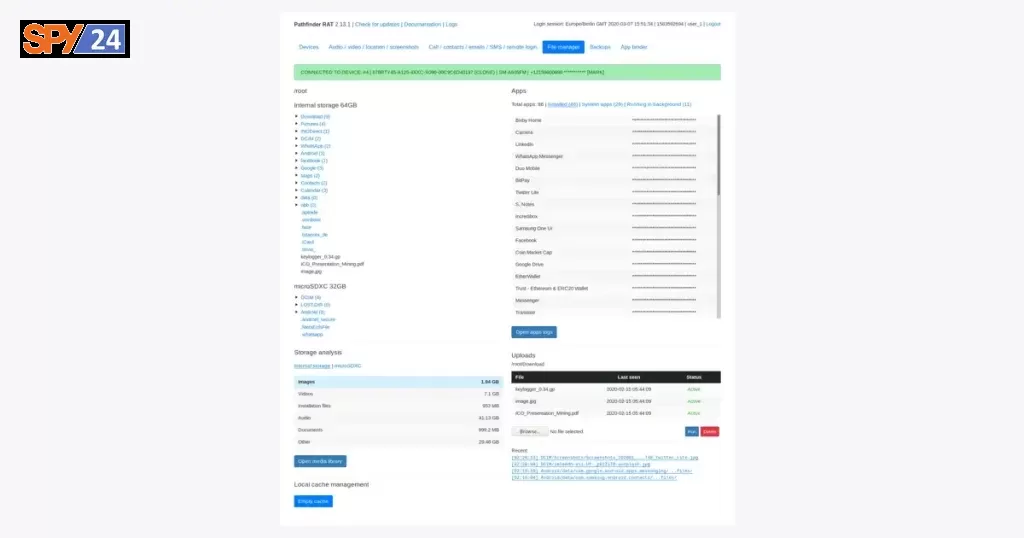
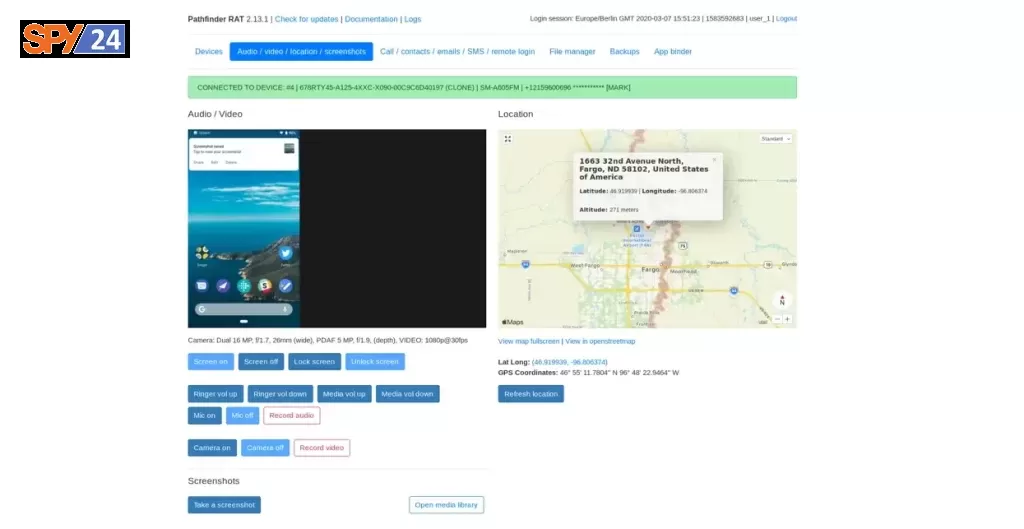
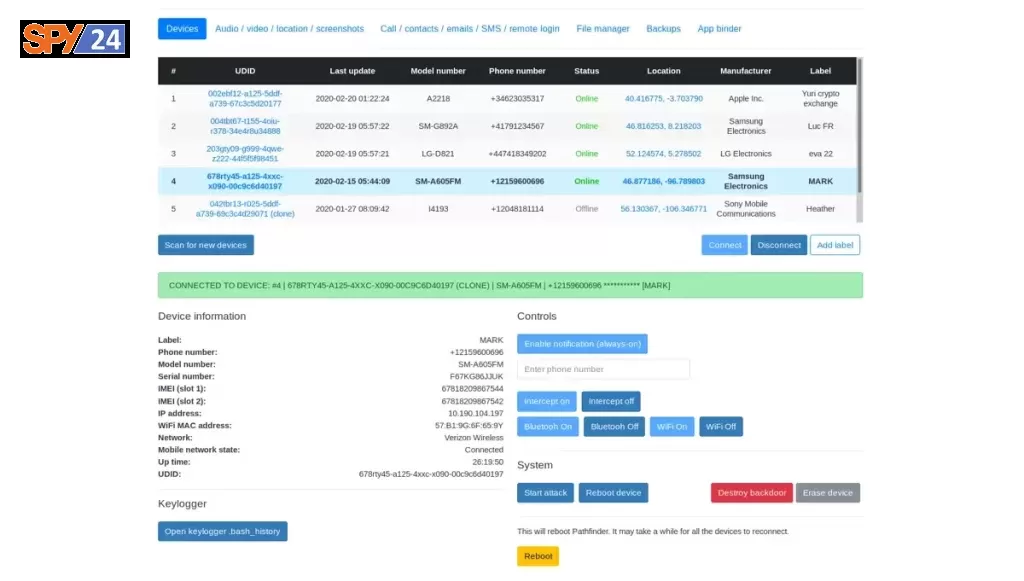
Architecture
Pathfinder RAT grants a user to control the Graphical User Interface (GUI) of any other person’s device system. Pathfinder can be used for performing malicious or surveillance tasks, or to harm one’s computer system, but it can be also used as an administrative remote helping tool. The primary use of Pathfinder is to spy, and surveillance, to keep an eye on your targets by password stealing, real-time tracking, screen captures and key-logging, perform post-exploitation tasks, call, and video recording, read messages, and more…
Pathfinder comes with a pre-installed App Binder, designed to easily develop a trojan and perform various post-exploitation tasks, like browser hijacking, DDL hacking, windows/Linux/android privileges escalation, etc, the payload is 100% fully undetectable (FUD). The payload will bypass all anti-virus software protection, easily creating a session between the attacker and the target; doing so will take full control of the device.
The software consists of two parts:
1. Server side: web-based desktop application (control panel)
2. Client side: device application (backdoor)
Infiltrator Real-Time Tracking System
The Infiltrator Real-Time Tracking System is an innovative tool for governmental and security organizations that require real-time data about the suspect’s location and movement. The combination of the Infiltrator Real-Time Tracking System as a strategic location solution and the Intelligence Interceptor, a tactical interception and location system, provides accurate, real-time data on target suspects and people of interest by tracking their mobile phones. The Infiltrator Real-Time Tracking System will provide the location (GPS coordination) at a Cell-ID level. The input will be the target mobile number or the IMSI and the result will show the BTS coordinator, where the target is registered on any map.
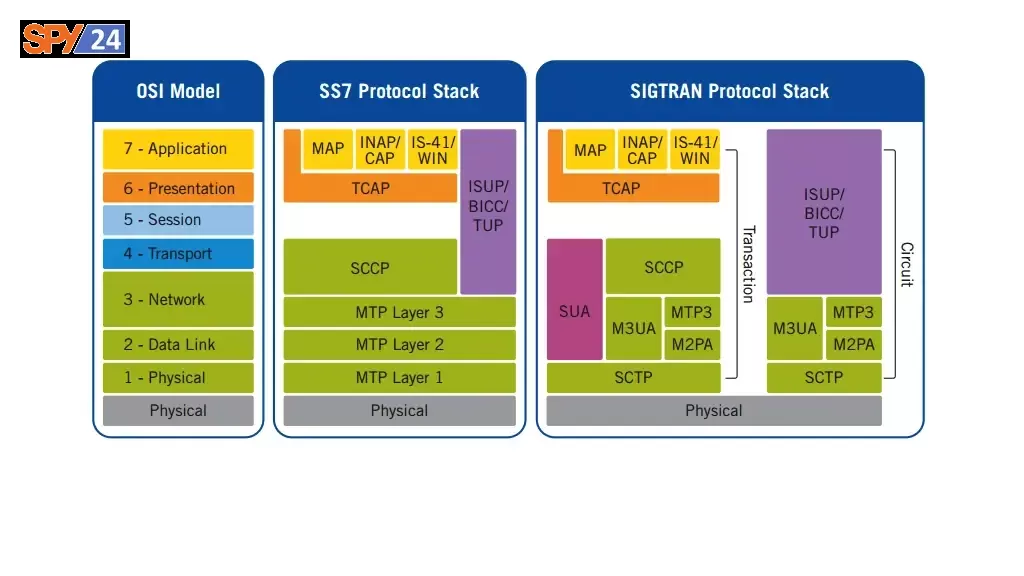
SS7 and SIGTRAN Protocol Stacks
The SS7 and SIGTRAN protocol implementations are available with their relationship to the Open Systems Interconnection Basic Reference Model (OSI Model). Protocol suite used by most telecommunications network operators throughout the world to talk to each other.
Some of the most powerful features of Pathfinder
- Full device access
- Database access AES 256 encrypted
- Make calls to phone numbers
- Reading call logs
- Opening web pages and browsing history
- Recording calls
- Recording audio through a microphone remotely
- Remote camera to capture photos and videos
- Get real-time geo-location
- Pre-installed keylogger
- Opening apps
- Watch via the camera in real-time
- Upload and download data
- Full device backup
- Infiltrator Real-Time Tracking System
- Real-time notifications
- Remotely DDoS attacks for a period of time
specified by the attacker - Intercepting MMS/SMS, WhatsApp, messenger, telegram, chats, and more…
- Fully integrated app binder
- Browsing files
- Unlimited devices
- 100% FUD (Fully Undetectable)
- Run on USB
- SS7 exploitation
FAQ Pathfinder RAT Tools:
Q1: What is Pathfinder RAT?
A1: Pathfinder RAT is a Remote Administration Tool (RAT) designed to provide users with remote access to their system, allowing them to take control of their computer from a remote location.
Q2: What features does Pathfinder RAT provide?
A2: Pathfinder RAT provides a variety of features, including remote desktop access, file transfer, remote command execution, application management, and more.
Q3: Is Pathfinder RAT secure?
A3: Yes. Pathfinder RAT is built with the latest security technologies and protocols to protect users from malicious activity.
Q4: Does Pathfinder RAT work on Windows, Mac, or Linux?
A4: Pathfinder RAT is compatible with Windows, Mac, and Linux operating systems.
Q5: Does Pathfinder RAT cost anything?
A5: Pathfinder RAT is free to use.
Conclusion:
Remote Access Trojans (RATS) are malicious tools used by attackers to gain access to remote computer networks and steal confidential information or take control of systems for their own nefarious purposes. Although there are several different types of tools available for download online—such as Pathfinder Rat or Blackshades Rat—it’s important that everyone takes necessary security measures in order to protect themselves against these threats. By using strong passwords, keeping your OS up-to-date with the latest security patches, avoiding suspicious links/attachments from unknown sources, and installing anti-virus software on your computer; you will be able to stay safe online while still enjoying all the benefits that come with using technology today!
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.




