How Do Hackers Spy on You?

Hacking is usually technical. But hackers can also use psychology to trick a user into clicking on a malicious attachment or providing personal data. These tactics are called “social engineering”.
It is accurate to describe hacking as an umbrella term for the activity behind most malware and destructive cyberattacks on computing people, businesses, and governments. In addition to social engineering and bad advertising, common hacking techniques include:
- Botnets
- Browser hijacks
- Denial of service (DDoS) attacks
- Ransomware
- Rootkits
- Trojans
- Viruses
- Worms
hacking has gone from teenage mischief to a billion-dollar growth business, whose proponents have created a criminal infrastructure that develops and sells turnkey hacking tools and targets would-be fraudsters with less sophisticated technical skills (known as “kiddies”).
In another example, Windows users are reported to be the target of a massive cybercriminal effort offering remote access to IT systems for as little as $10 through a dark web hack shop – potentially enabling attackers to steal files, disrupt systems, deploy ransomware, and more. Systems advertised for sale on the forum range from Windows XP to Windows 10. Store owners even offer tips on how people using illegal logins can go undetected.
How Do Hackers Spy on You?
Hackers always try to stay one step ahead of anti-virus and anti-malware software in order to access secure data. As technology advances and changes, so do the tactics of cybercriminals. Hacking, online fraud, and social engineering are significant threats to your devices and network security. Studies have shown that cyberattacks happen more often to small businesses than to large businesses. Here are five common cybersecurity threats used by cybercriminals to bypass the security of your data and inside your network.
Email Threats
Emails can contain viruses and malware that allow unauthorized access and, if chosen, can leave your device or network vulnerable to cyberattacks. Virus-infected software is commonly known as malware, and there are many different types of malware, all of which work slightly differently.
The easiest way for malware to gain access to your device is via email to unsuspecting users. The email is usually difficult to identify, but often contains a link that downloads malware (gives the hacker sensitive information on your computer) that is clicked. The real problem is that if you don’t have anti-malware installed on your device, you may not even know about a cyber security breach.
Spyware
This is a type of spyware malware that collects information from a computer (such as user activity) without the user even knowing it exists. Spyware records every activity you do on your device, including the passwords you type to log into your email or bank accounts, the links you click, and the websites you visit. Spyware does exactly what you think. It will spy on you when you are on your computer trying to steal sensitive information. All this behavior and related data are then transmitted to the cybercriminal.
Keylogger
Keylogger is a type of spyware and one of the most common and dangerous malware that steals sensitive information. Software companies legitimately use keylogger software to get feedback to improve development, but hackers also use it to steal data. Keylogger software is powerful because it tracks everything you type on your device, including your email address and passwords. Cybercriminals use keylogger malware to steal data by recording information as you type. Then it transfers the data to unauthorized users.
Malicious Websites
Make sure you know what you’re clicking on. A malicious website can look like a trustworthy website, but its sole purpose is to cause damage to your computer systems, information systems, or network infrastructure. Links to this website may appear in an email or even on a legitimate website. If you know what to look for, you can spot a malicious website. Here are some things to keep in mind:
- Requests for personal information: Are you being asked to provide personal or sensitive information? This is the number one red flag for suspicious activity. No reputable organization will ask you to provide sensitive information or personal data through email.
- Unknown or suspicious links: It is good practice to be suspicious of links provided in emails. Additionally, it’s important to make sure the link takes you where you expected. If you’re not sure, right-click the link and select Properties to check the link.
- Poor grammar or sloppy formatting: Look for misspellings in the URL or email copy, which is often a sign of a scam.
Social Media Cyber Security Threats
People have the misconception that if they log out of their social media accounts, hackers can’t access them. That is not true. Hackers gain access to social media accounts through social engineering techniques and social media pages. These pages often look legitimate, and therefore, when a user receives an invitation to join, they usually do so. When a user clicks on a link, malware is downloaded to their device and tries to access sensitive information. Common threats that hackers use social media to work on cyber security tools include:
- Phishing
- Malicious links in group posts
- Celebrity spoofing
- Links on websites
- Fake accounts from “friends”
- Link in a message from a friend who’s infected
Ways to help ensure the security of your data is to delete your browsing history. Cybersecurity experts also recommend having unique passwords for each login and avoiding connecting to the Internet through public Wi-Fi.
Online Hijacking
Whether you’re shopping online, watching a YouTube video, or playing a game, ads are commonplace no matter where you go online. Most ads are legitimate, but ads can be deceptive.
- Browser Hijacking: Often, users download apps and extensions to their browsers, but these improvements in performance can come at a cost. These free apps and extensions can be bundled with ads. When the user downloads them, the deceptive ads are installed in the user’s web browsers and change the way they are viewed from the business’s website. These ads can direct users to a competitor’s website or a website with a similar product. For small businesses, this can mean a loss of revenue and trust.
- Pre-Hijack Online Accounts: A relatively new data breach technique involves prediction, where an attacker predicts which online service a target user will sign up for and then manipulates the sign-up process before creating an account. This usually results in the attacker gaining access to the account. These types of attacks can also involve users with single sign-on (SSO) services.
Trojan Horse Software
Using the Trojan technique is one of the easiest ways for hackers to gain access to your network and sensitive information. Like other techniques, Trojan horse software looks legitimate and can be used to gain legitimate access.
Trojans can:
- Create backdoors for hackers that make it easy for them to manipulate your personal information. They can edit, create and delete files on your system through a Trojan.
- be very harmful because there is no warning activity. They can extract banking information and transaction activity.
- can use your device to influence other users and get their personal information and money by misusing the data.
- It can encrypt files, folders, and mobile devices, and hackers can demand any amount from users to decrypt devices and data.
Trojans can also be used in the form of a computer worm. A computer worm is a type of Trojan horse malware that spreads through your computer and network like wildfire. A computer worm can gain access to your device through phishing, file sharing, social platforms, and even infected USB drives. Worms can appear as legitimate software and after downloading the files, once the device is infected, it accesses your email and sends links to your contacts. Anyone who opens the link will be infected with the worm.
How Hackers Use Spyware to Collect Data
Hackers are becoming more and more sophisticated. This idea about how spyware is distributed does not go away. The most common way spyware is distributed is through online downloads, which are usually harmless. Another common method is free or easy-to-hack unsecured (no password required) WIFI connections. For most hackers, this is all they need to gain full access to not only your computer or network but every connected device in your office or home. And then it goes back to your downloads, files, etc., and collects unknown information about you, your customers, and your system until it is discovered and destroyed.

Spyware is almost always downloaded unknowingly or disguised as something legitimate. This means that it is rarely intentional. And more often than not, spyware is introduced into your system by an employee who thought they were doing the right thing, but inadvertently infects a computer or a workstation, and then ends up spreading throughout the system.
What Is Spyware?
Spyware is a type of malicious software — or malware — that is installed on a computing device without the end user’s knowledge. It attacks the device, steals sensitive information and internet usage data, and sends it to advertisers, data companies, or external users. Any software that is downloaded without the user’s permission can be classified as spyware. Spyware is controversial because, even when installed for relatively innocuous reasons, it can violate end-user privacy and has the potential for abuse.
Spyware is one of the most common threats to Internet users. Once installed, it monitors internet activity, tracks logins, and spies sensitive information. Basic spyware is usually used to obtain credit card numbers, banking information, and passwords. But spyware can also be used to track people’s location, which is also the case with stalker ware. This type of spyware, secretly installed on cell phones by jealous spouses, ex-partners, and even concerned parents, can snoop on the victim, hack their emails and messages, and make calls. eavesdrop on their phone and record conversations, and gain personal data access such as photos, and videos.
Spyware can be difficult to detect. Often, the first indication a user has that a computing device is infected with spyware is a noticeable drop in processor or network connection speed and – in the case of mobile devices – data consumption and battery life. Anti-spyware tools can be used to prevent or remove spyware. They can provide real-time protection by scanning network data and blocking malicious data, or they can run scans to detect and remove spyware already on a system.
How Does Spyware Work?
Spyware can make its way onto a device without the end user’s knowledge through a program installation package, file attachment, or malicious website. At its worst, spyware exists as a program that starts as soon as the device is turned on and continues to run in the background. Its presence steals random access memory and CPU power and can generate endless pop-up ads, effectively slowing down the web browser until it becomes unusable. Spyware may also reset the browser’s home page to open an ad every time or redirect web searches to control the results presented and render the search engine useless.
In addition, spyware can modify the computer’s dynamic link libraries used to connect to the Internet, resulting in connection disruptions that are difficult to diagnose. At its worst, spyware tracks web browsing history, passwords, and other private information such as email addresses, credit card numbers, personal identification numbers, or banking records. All of this information can be collected and used for identity theft or sold to third parties. Information can be collected using keyloggers and screenshots. Spyware can also secretly make changes to a device’s firewall settings and reconfigure security settings to allow more malware to enter. Some forms of spyware can even detect that a device is trying to remove it from the Windows registry and stop all attempts to do so.
How Can I Protect Myself?
Maintaining strict cybersecurity practices is the best way to prevent spyware. Some of the best practices include the following:
- only downloading software from trusted sources;
- reading all disclosures when installing software;
- avoiding interactions with pop-up ads;
- staying current with updates and patches for browser, operating system (OS), and application software;
- not opening email attachments or clicking on links from unknown senders;
- using only trusted antivirus software and reputable spyware tools; and
- enabling two-factor authentication (2FA) whenever possible.
To further reduce the possibility of contamination, network administrators should adhere to the principle of least privilege and require remote workers to access network resources through a virtual private network that runs a security scan before granting access. Using a pop-up blocker or ad blocker will also help prevent spyware. Mozilla Firefox and Google Chrome have built-in pop-up blockers, and ad blockers can be added as browser extensions. Mobile phone users should avoid downloading apps from outside their respective app stores and avoid jailbreaking their phones if possible. As both make it easy for spyware to infect mobile devices.
iPhone users can enable 2FA at no cost to protect all data on their smartphones and prevent mobile spyware attacks. 2FA can also be used on a variety of other popular services including PayPal, Google, Dropbox, and Microsoft 365, as well as on social networking sites such as Instagram, Snapchat, Facebook, and Twitter. Most major banks have also started implementing 2FA on their websites and mobile apps. Even some services have increased their authentication process to three-step and four-step authentication.
Understanding How Hackers may Hack Your Phone by a Spy app

Easy ways to break into a phone
These are the ways a hacker would use to gain access to a phone and you can use them too.
- Social engineering
The easiest way for any hacker to break into any device is for the user to open the door themselves. Of course, this is easier said than done, but this is the goal of most forms of social engineering attacks.
- Malvertising
One important vector for this type of deceptive dialog box is so-called “malvertisements”, which refers to the infrastructure developed for the mobile advertising ecosystem, either in a browser or in an app.
- Smishing
Another way for attackers to get the all-important, tangible link in front of their victims is SMS text messaging, with a whole different set of social engineering tricks in play. This practice is known as SMS phishing or smishing and it traps the gullible and the powerful alike.
- Malware
If a hacker can’t trick you into clicking a button and inadvertently lowering your phone’s security barriers, they might be looking for someone who has already done it on purpose by jailbreaking their phone. Jailbreaking is seen by many as allowing users to better customize their device and install the apps of their choice from unofficial sources, but by its nature, it relaxes the strict security sandboxing that keeps smartphones locked down.
- Pretexting
Finally, if the user does not voluntarily relinquish control of their device, the attacker can go to their mobile provider. You may recall the UK media scandal in the mid-00s where newspapers used what they called “snooping” techniques to access the mobile voicemails of celebrities and crime victims. This process, also known as spoofing, involves an attacker gathering enough personal information about their victim to plausibly impersonate them in communications with their phone provider, thereby gaining access to the victim’s account.
- Breaking in through Bluetooth
There are a pair of wireless attack vectors that hackers can use to break into phones without tricking anyone into giving up permissions. Both require physical proximity to the target, but can sometimes be pulled out in public spaces. Aleksandr Maklakov, technology and security expert and chief technology officer of MacKeeper, said: “Bluetooth connectivity is one of the weak points of smartphones, and hackers often use special methods to connect to devices that work on Bluetooth and hack them. “This is a common method of hacking because many people keep their Bluetooth connection turned on. If the Bluetooth connection is not set, hackers can approach your smartphone unannounced and hack their way in.”
- Man-in-the-middle Wi-Fi attacks
Another potential wireless attack vector is the Wi-Fi man-in-the-middle attack. “Many people tend to connect their smartphones to free public Wi-Fi whenever they get the chance,” explains Peter Balthazar, cybersecurity expert and technical writer at MalwareFox.com. This habit can lead to big problems because smart hackers can intercept the connection and break into the phone. By intercepting communications, hackers can obtain a wealth of information without controlling the user’s phone. (A connection using TLS 1.3 is much more difficult to intercept this way, but the protocol is not yet universally available.)
Getting Software for Hacking
- Acunetix
Acunetix is a fully automated ethical hacking tool that detects and reports over 4500 web application vulnerabilities including all types of SQL Injection and XSS. The Acunetix crawler fully supports HTML5 and JavaScript and single-page applications, enabling the auditing of complex and authenticated applications.
Advanced features put vulnerability management right at its core, prioritizing risks based on data through a single, integrated view, and integrating scanner results into other tools and platforms.
- Invicti (formerly Netsparker)
Invicti (formerly Netsparker) is a dead-end ethical hacking tool that mimics hackers’ moves to identify vulnerabilities such as SQL Injection and Cross-site Scripting in web applications and web APIs. Invicti uniquely verifies detected vulnerabilities and proves they are real and not false positives, so you don’t have to waste hours manually verifying detected vulnerabilities after the scan is complete. It is available as Windows software and online service.
- Intruder
The intruder is a fully automated scanner that finds cybersecurity weaknesses in your digital assets, explains the risks, and helps you remediate them. It’s a great addition to your arsenal of ethical hacking tools. With more than 9,000 available security checks, Intruder makes enterprise-grade vulnerability scanning available to companies of all sizes. Its security checks include the detection of misconfigurations, missing patches, and common web application problems such as SQL injection and cross-site scripting. Built by experienced security professionals, Intruder takes much of the hassle out of vulnerability management, so you can focus on what’s important. It saves you time by prioritizing results based on their context, as well as proactively scanning your systems for the latest vulnerabilities, so you don’t have to stress about it.
The Intruder also integrates with major cloud providers as well as Slack & Jira.
- Nmap
Price: Free
Nmap is a security scanner, port scanner, and also network exploration tool. This software is open source and available for free.
It supports cross-platform. It can be used for network inventory, managing service upgrade plans, and monitoring host and service update times. It can work for a single host as well as large networks. It provides binary packages for Linux, Windows, and Mac OS X.
- Metasploit
Price: Metasploit Framework is an open-source tool and can be downloaded for free. Metasploit Pro is a commercial product. A free trial is available for 14 days.
This software is for penetration testing. Using the Metasploit Framework, you can develop and execute exploit code on a remote machine. It supports cross-platform.
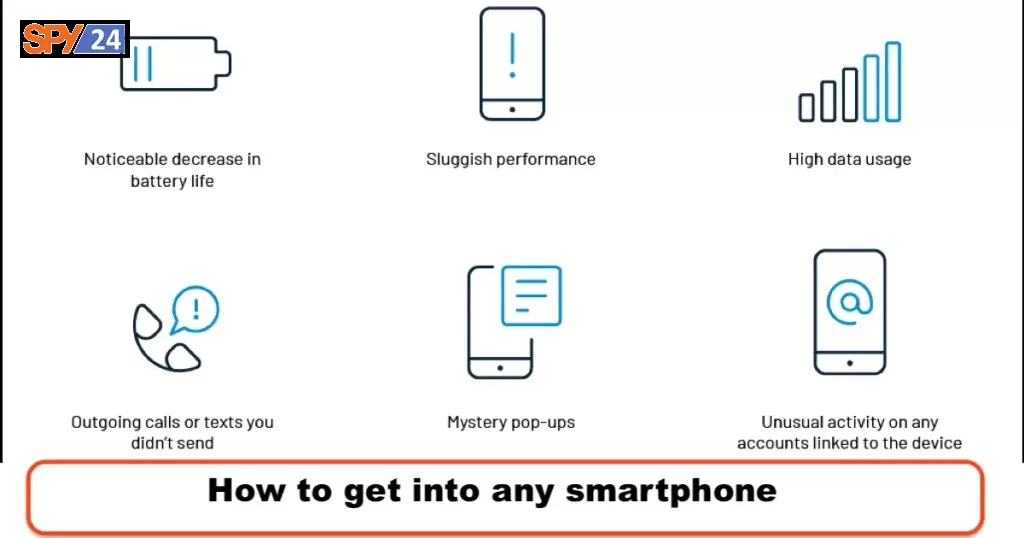
Ways to Tell If Your Phone Has Been Hacked
- Noticeable decrease in battery life
While phone battery life inevitably decreases over time, a smartphone that has been compromised by malware may begin to show a significant decrease in battery life. This is because malware – or spyware – may use your phone’s resources to scan your device and transmit information to the hacker’s server.
- Sluggish performance
Do you notice that your phone often freezes or that certain apps crash? This could be a sign that malware is overloading your phone’s resources or interfering with other apps. You may also experience apps continuing to run despite attempts to close them, or your phone may even crash and/or restart repeatedly.
- The phone feels hot when not using or charging it
According to Vavra, malware or apps like Bitcoin miners running in the background can cause your phone to heat up or even overheat. If your phone is hot to the touch when you’re not using it or it’s not on your charger, it could be a sign of malware. Try turning your phone off and on again to see if the problem goes away. If not, there may be a reason to worry.
- High data usage
Another sign of a compromised phone is an unusually high data bill or running out of data before the end of the month. Excess data usage can be caused by malware or spyware running in the background and sending data to their server.
For iPhones, go to Settings > Cellular and scroll down to see a list of apps that use cellular data. You can check the current and past billing periods.
For plain Android phones (Google Pixels phones), go to Settings > Network & Internet > SIM card > App data usage. For Samsung phones, go to Settings > Connections > Data usage > Mobile data usage. Or search for “data usage” in the search bar of the Settings app.
- Outgoing calls or texts you didn’t send
Be careful if you see a list of calls or texts to numbers you don’t recognize. These can be premium-rate numbers that the malware forces your phone to call, and the proceeds end up in the cybercriminal’s wallet. If so, check your phone bill for any charges you don’t recognize.
- Mystery pop-ups and apps
While not all pop-ups mean your phone has been hacked, constant pop-up alerts can indicate that your phone is infected with adware, a type of malware that forces devices to view certain pages that earn money through clicks. Even if a pop-up isn’t the result of a compromised phone, pop-ups that come from external sources can contain phishing links that try to get you to type in sensitive information or download malware.
You may also find apps on your phone that you haven’t downloaded and may have signed malware installed on your device. If you don’t remember downloading the app, you can press and hold the app icon (Android) and click on the app info option. Scroll down and the app details section will tell you where the app is installed (should be the Google Play Store). Click on the app details to go to the Google Play Store, where you can check if the app is a legitimate app from a trusted developer. For Apple owners, go to the App Store and tap your profile icon, select Purchased > My Purchases, and search for the app name.
- Unusual activity on any accounts linked to the device
If a hacker has access to your phone, they also have access to your accounts-from social media to email to various lifestyle or productivity apps This can include activities on your accounts, such as resetting your password, sending emails, signing up for new accounts whose verification emails land in your inbox or moving emails to trash that you don’t remember seeing (especially those verification emails).
In this case, you may be at risk of identity fraud, where criminals open new accounts or lines of credit in your name using information taken from your compromised accounts. It’s a good idea to change your passwords – without updating them on your phone – before running a security scan on your phone. SPY24 provides extra layers of protection against malicious software like spyware so make sure you check out our services today!
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.