AndroRat Phone Android Hack Software With Training And Download Github Apk
What Is A RAT? A RAT (Remote Access Trojan) is malware that an attacker uses to gain full administrative privileges and remotely control the target computer. Rats are often downloaded along with seemingly legitimate user-demanded programs -such as video games – or sent to their target as an email attachment through a phishing email. Once the host system is compromised, intruders use a backdoor to gain control of the host, or they may distribute RATs to other vulnerable computers and create a botnet. RATs, which belong to the Trojan horse virus family, are specifically designed to disguise themselves as legitimate content.
How does a remote access Trojan work?
A RAT is usually deployed as a malicious payload using exploit kits, such as Metasploit. Once installed, the RAT connects to a command-and-control server that hackers control. Hackers achieve this connection by compromising an open TCP port on the target device. RAT can also be installed through phishing emails, download packages, web links, or torrent files. Users are tricked into downloading malicious files through social engineering tactics, or RATs are installed by threat actors after physical access to the victim’s machine, such as in a malicious servant attack.
Because a RAT provides a backdoor and enables administrative control, it allows an intruder to do almost anything on a target computer, including:
- Monitor user behavior, such as keystrokes, through keyloggers and spyware.
- Access confidential information, such as credit card and Social Security numbers.
- Activate a system’s webcam and record video.
- Take screenshots.
- Distribute viruses and malware, as well as launch ransomware
- Format drives.
- Delete, download, or alter files and file systems.
Why are remote-access Trojans a threat?
RATs can be difficult to spot because they usually don’t show up in the list of running programs or tasks. The actions they take can be similar to the actions of legitimate applications. In addition, an intruder often manages the level of resource usage so that performance drops do not alert the user that something is wrong.
Unlike other cyber security threat vectors, RATs are dangerous even after they are removed from a system. They can modify files and hard drives, alter data, and capture passwords and user codes through keylogging and screen capture, all of which can have long-lasting effects.
The following are some of the ways RATs can compromise users, systems, and organizations:
- Spying and blackmail attempts: By deploying a RAT, threat actors can access a victim’s smartphone camera and microphone and compromise their privacy. They can take pictures of users and their surroundings to launch further attacks or blackmail users into some sort of agreement, such as providing ransom money or top-secret data.
- Crypto mining: It is common for threat actors to use RATs to mine Bitcoin and other cryptocurrencies on victims’ computers. Attackers can make a significant profit by spreading RATs across multiple devices.
- Distributed denial-of-service (DDoS) attacks: RATs deployed on a large number of devices can be used to perform a DDoS attack by flooding a target server with fake traffic. Although a DDoS attack may cause performance degradation, users are usually not aware that their devices are being used for such attacks.
- Remote file storage: To ensure that their accounts and operations are not shut down by the authorities, cybercriminals may use RATs to store illicit content on the victim’s device instead of their storage servers.
- Industrial system compromise: Threat actors often use a RAT to control large-scale industrial systems, such as water and electricity. The purpose of these cyber-attacks is to cause extensive damage to industrial machinery and disrupt critical services in certain geographic areas.
How to protect against RATs
Similar measures for threat protection against malware and viruses can also be effective against RATs. The following preventative measures can help reduce remote access to Trojans.
Disconnect devices
The first step to take after detecting suspicious activity or the presence of a RAT is to disconnect the devices from the network. This prevents additional malicious activity by remotely disconnecting the installed RAT from the attacker.
Update antivirus and firewalls
Keep antivirus software and firewalls up to date and avoid downloading programs or opening attachments that are not from trusted sources. At the administrative level, block unused ports shut down idle services, and monitor outgoing traffic.

Deploy multifactor authentication
Multi-factor authentication (MFA) provides an additional layer of security, as two or more authenticators are required before access to a service is granted. Since most hackers attempt to steal usernames and passwords, setting up and implementing MFA throughout your organization is an important defense mechanism.
Avoid suspicious links and attachments
Phishing emails trick unsuspecting users into opening them. Once a malicious link or attachment is opened, it can secretly distribute malware and RATs to the compromised system. Security awareness training should be provided to all users within an organization so that they can easily identify phishing emails and avoid downloading malicious files and attachments.
Install the latest upgrades
An operating system (OS) should always be patched with the latest updates because they contain fixes for vulnerabilities, exploits, bugs, and malware, including RATs.
Use an intrusion detection system
An intrusion detection system (IDS) is used to monitor network traffic and detect anomalies or suspicious activities on the network. Although many RATs have evolved to avoid detection, specific IDSs and advanced persistent threat tools (APTs) can be useful because they can detect unusual behavior patterns such as strange keyboard and mouse behavior or spontaneous commands.
Employ the principle of least privilege
The Principle of Least Privilege (POLP) is a computer security concept that promotes minimal access to systems and resources. The lowest score required for a job is awarded initially and increased as needed. Restricted access can act as an obstacle for threat actors to gain full control of a system.
How to detect remote access Trojans
RATs are good at evading detection, and even strong antivirus software can miss them. While only specific scans may detect the presence of a RAT, the following five signs should be observed when searching for a remote access Trojan:
- Failure of antivirus program: An antivirus program that constantly crashes or responds slowly may be a sign of infection.
- Slow system performance: RATs run in the background and consume a lot of processing power. A computer that runs much slower for no apparent reason may be infected by a remote Trojan.
- Website redirects: If the browser requests are constantly redirected or webpages aren’t loading, then it can be a sign of a RAT infection.
- Unidentifiable files: Any file or program that appears unrecognizable or that has not been downloaded or installed by the user should be carefully observed, as it may be related to a Trojan virus.
- Operational webcam: The indicator light on the webcam usually turns on when an application accesses the webcam, such as video conferencing applications. However, if the webcam indicator light turns on for no apparent reason, it could be a sign of a RAT infection.
AndroRAT
AndroRAT is a tool designed to remotely control the Android system and recover data from it. AndroRAT is a client/server application that is developed in Android Java for the client side and the server is in Python.
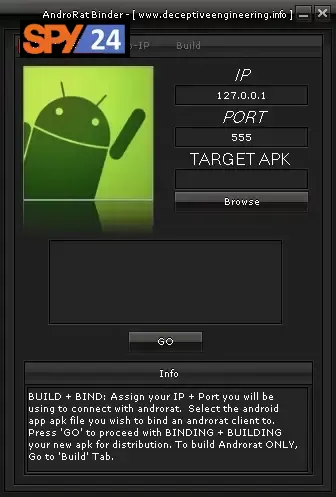
AndroRAT will work on devices from Android 4.1 (Jelly Bean) to Android 9.0 (Oreo) (API 16 to API 28). AndroRAT also works on Android 10 (Q), but some interpreter commands will be unstable.
Features of AndroRAT
- Features of AndroRAT
- Complete permanent back door
- Invisible icon installing
- A lightweight apk that runs 24/7 in the background
- The program starts automatically at the startup
- It can record audio, and video, and take photos from both cameras
- Browse your call list and SMS logs
- Get the device’s current location, SIM details, IP, MAC address
Prerequisites
- Access to a computer or laptop
- Install the latest version of Java (direct download of Java)
- A wireless router (WIFI router with Port Forwarding enabled)
- High-speed Internet (for a fast Internet connection)
- An Android phone (for testing the program)
Fully undetectable by any antivirus scanner VirusTotal- (download from here)
Installation AndroRAT
Step 1: To make the AndroRAT phone hacking software, we need a place on the Internet to send the information obtained from the AndroRAT phone hacking application. So, for this purpose, enter the noip.com site and create a host with the name you want.

Step 2: We need to perform a port forwarding operation. The port transfer operation is performed in a special way for each modem. So, to perform port forwarding, it is better to search your modem type on Google and then get the port forwarding method.
Step 3: You need to download the AndroRAT Blinder software and then in the Hostname section, enter the hostname you created in the Port section, enter the port name.
Step 4: You should choose a name for the file and click Go. (If you want to render and combine the file you created in another app format, go to the Build Blind tab and import the apk file from there.)
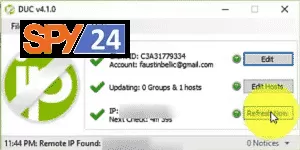
Step 5: You need to download and install the DUC software used to automatically update DNS in Windows (you can visit noip to download DUC). After installing the DUC program, open DUC and enter the details of the host you created in the corresponding section.
Step 6: You need to download and run the AndroRAT Project software and then open the Server tab and enter the port number you created earlier.
Step 7: You need to run the apk file that you created in the previous sections by the AndroRAT Blinder program on the target phone.
Step 8: After the above steps, you are almost successful in creating a hacked Android phone app. Of course, you should know that most antiviruses recognize this program as a virus and do not allow access to it due to the popularity of AndroRAT software in the process of spying and hacking.
Step 9: This is the most important stage of building and running your RAT program and it should be according to the following steps:
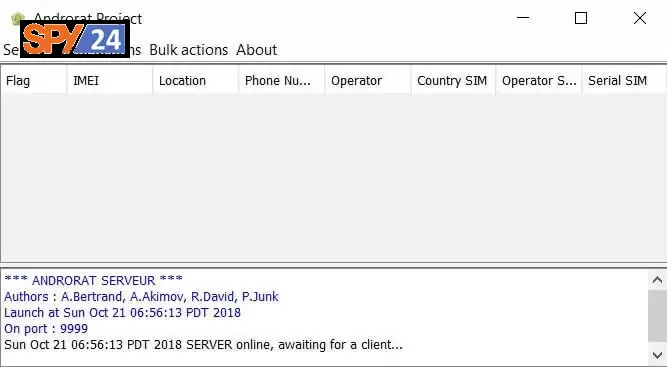
- After downloading AndroRAT apk
- Open AndroRAT folder.
- Look up. Select “Noip” from the tab.
- Now save the information from the NOIP website and click on “Update”.
- Select the Build tab from the top.
- In the IP field: enter the hostname and enter the port you forwarded.
- Now press the GO option.
- You will find a file called “framework.apk” in the AndroRAT folder.
- Open the “AndroRAT.jar” file in the AndroRAT folder.
- Click on Server >> Port [Enter Forwarded Port].
- Restart the Jar file and you are all set to use your tool
AndroRAT VS SPY24
SPY24 is a much more powerful program than AndroRAT. With SPY24, users can monitor all their devices, including phones and tablets, and Windows and macOS. In addition, SPY24 can access all incoming and outgoing text messages, emails, and even multimedia files. SPY24 also allows users to track device locations, view saved contacts, and even monitor calls. AndroRAT, on the other hand, is limited to Android devices only. It can only track incoming and outgoing text messages, calls, and emails. It also does not allow users to track the location of the device or access saved contacts.
In addition, SPY24 has a user-friendly interface that makes it easy for everyone to use the program. AndroRAT, on the other hand, requires users to have the moderate technical knowledge to use and understand the program.
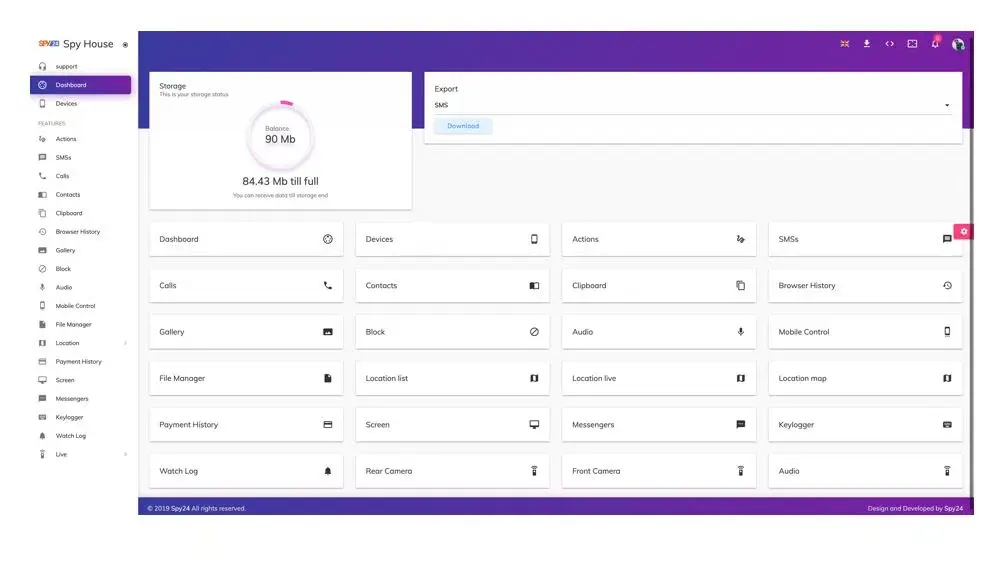
Finally, SPY24 is much more reliable than AndroRAT. SPY24 is regularly updated with the latest security patches and features, ensuring that users have the best possible experience. On the other hand, AndroRAT is not updated regularly and can be prone to technical issues.
When it comes to cell phone spying, there’s no comparison to SPY24; it’s the most reliable and powerful spy app on the market. SPY24 offers users a comprehensive set of features, a user-friendly interface, and the reliability of regular updates. Therefore, if you are looking for a reliable, powerful, and easy-to-use spy app, SPY24 is a great choice.
SPY24 App Features
let’s look at some of the vital things that you can do using the SPY24 tool. While SPY24 gives you access to tones of details from any device, these features are some of the major offerings:
- Location-based features: The most noted feature of SPY24 is that it supports real-time location tracking of the device. You can just do a SPY24 login to monitor their live locations and places also you will have access to the location history.
- Calls and contacts: SPY24 app gives you access to their entire contact list. Also, you have access to incoming and outgoing call logs including contacts and timestamps.
- Messages Tracking: You have access to their sent or receive messages in your SPY24 dashboard. You can read their messages with conversational threads including their contact and timestamp details.
- Social Media Monitoring: SPY24 also gives you access to track all major social media platforms. You can find this option in your account dashboard and give you access to monitor details from apps like Facebook, Instagram, Snapchat, WhatsApp, Viber, etc.
- Access Saved Media: You can also go to the SPY24 dashboard to access the saved photos and videos from your device. Besides viewing their photos, you can also download them to your system.
- Inbuilt keylogger: If you want, you can enable an inbuilt keylogger on the SPY24 app. This will let you access their account passwords, deleted messages, and every other keystroke typed on the device.
- Browsing History: SPY24 will give you access to the detailed browsing history and the websites they have visited with timestamps. You can also check what they look for on the web and how much time they spent browsing it.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
FAQs
Is it lawful to hack?
Yes, if your IT company, government agency, or group has given you permission to use the app for hacking. Alternatively, you may use it for educational and ethical hacking purposes.
Is AndroRAT secure?
Yes, is completely safe and secure unless you are using it for ethical and educational objectives and are an expert in IT.
Are AndroRAT and SPY24 Detectable?
One of the best things about the SPY24 app is that it isn’t detectable. After installing the application, you can simply enable the “stealth mode” features of SPY24. This will let you track the targeted device without letting the user know about it. But if you want to use the AndroRAT you need to do some changes on your target device.
Conclusion
Staying safe online can be difficult, but having an understanding of potential threats like rats like AndroRAT can help you stay ahead of any potential attacks. Knowing the different types of malware out there helps us make sure our devices stay safe from malicious actors trying to steal our valuable data.
By following the above guide on removal techniques used to deal with AndroRAT remote access trojan infections, you can rest assured that your personal information will remain safe and secure.




