Can Someone Hack My Gallery?
In our modern world, phones, and galleries have become the digital containers of our memories, holding precious photos and videos that capture our most cherished moments. However, with the ever-increasing threat of hacking, these devices have become vulnerable to invasion, leaving us exposed to potential breaches of privacy and security. Whether it’s a celebrity’s personal photos being leaked or a regular person’s private moments being stolen, the consequences of phone and gallery hacking can be devastating. In this digital age, it’s more important than ever to protect our memories and keep our devices secure.
Can someone hack my phone’s gallery?
Yes, unfortunately, it is possible for someone to hack into your phone’s gallery. If your phone is connected to the internet, it becomes vulnerable to potential cyber-attacks, including hacking attempts. There are several ways that someone could gain unauthorized access to your phone’s gallery, including phishing scams, malware infections, or by exploiting vulnerabilities in your device’s software.
To protect your phone’s gallery from hacking attempts, it’s important to take certain precautions, such as keeping your device’s software up-to-date, avoiding suspicious emails or messages, and using strong passwords to secure your phone. Additionally, you can consider using encryption or two-factor authentication to add an extra layer of security to your device.
How to protect your phone?
There are several ways you can protect your phone from potential security threats, such as hacking attempts. Here are some tips to help you keep your phone secure:
- Keep your software up-to-date: Make sure that your phone’s operating system, apps, and antivirus software are all updated regularly. Software updates often contain security patches and bug fixes that can help protect your phone from potential threats.
- Use strong passwords: Set a strong password or PIN to lock your phone, and avoid using easily guessable passwords such as “1234” or “password”. You can also consider using biometric authentication, such as a fingerprint or face recognition, for an extra layer of security.
- Be cautious of suspicious messages or emails: Don’t click on links or download attachments from unknown or suspicious sources, as they may contain malware or other security threats.
- Use trusted apps and services: Only download apps from official app stores such as the Google Play Store or Apple App Store, and avoid downloading apps from third-party sources. Be sure to read app reviews and check the app’s permissions before downloading.
- Use two-factor authentication: Consider using two-factor authentication for your accounts, which requires a second form of verification in addition to your passwords, such as a code sent to your phone or email.
- Enable encryption: Enable encryption on your phone to help protect your data in case your phone is lost or stolen. This will scramble your data so that it can only be accessed with a password or PIN.
By following these tips, you can help protect your phone from potential security threats and keep your personal information secure.
Who can hack my phone gallery?
In general, anyone with the necessary technical knowledge and resources can potentially hack into your phone’s gallery, including cybercriminals, hackers, and even individuals with malicious intent. Here are some possible scenarios of who might be able to hack your gallery phone:
- Cybercriminals: These are individuals or groups that use malicious software or phishing tactics to steal personal information, such as photos, videos, and passwords, for financial gain.
- Hackers: These are individuals who seek to exploit vulnerabilities in your phone’s software or security systems for various purposes, such as to gain access to your personal information, spread viruses or malware, or disrupt services.
- Insiders: This refers to individuals who have access to your phone, such as friends, family members, or co-workers, who may use your phone to gain access to your personal information, including your gallery.
- Government agencies: Government agencies, such as law enforcement or intelligence agencies, may have the ability to hack into your phone’s gallery for legal reasons, such as in the case of an investigation or surveillance.
It’s important to take steps to protect your phone from potential security threats and keep your personal information secure.
How to prevent my phone from hacking?
Here are some steps you can take to prevent your phone from being hacked:
Keep your phone and apps up-to-date: Regularly update your phone’s operating system and apps to ensure that they have the latest security patches and bug fixes.
Use strong passwords and two-factor authentication: Use a strong, unique password or PIN to lock your phone, and consider using two-factor authentication for an extra layer of security.
Use trusted apps and services: Only download apps from official app stores such as the Google Play Store or Apple App Store, and be sure to read app reviews and check app permissions before downloading.
Avoid suspicious messages or emails: Don’t click on links or download attachments from unknown or suspicious sources, as they may contain malware or other security threats.
Use a VPN: Consider using a virtual private network (VPN) when using public Wi-Fi to encrypt your data and protect your privacy.
Enable encryption: Enable encryption on your phone to scramble your data so that it can only be accessed with a password or PIN.
Be cautious with public Wi-Fi: Avoid using public Wi-Fi for sensitive activities such as online banking or shopping, as these networks may be insecure and prone to hacking attempts.
By following these steps, you can help protect your phone from potential security threats and keep your personal information secure.
Is hacking easy?
Hacking is not easy, as it requires a high level of technical knowledge, expertise, and experience. Hacking involves finding and exploiting vulnerabilities in computer systems, networks, or applications, which can be a complex and time-consuming process. It also requires a deep understanding of programming languages, operating systems, and networking protocols.
However, with the increasing availability of hacking tools and resources online, it has become easier for some individuals to launch basic hacking attacks without extensive technical knowledge. These attacks are often aimed at exploiting known vulnerabilities in common software or systems, such as weak passwords or unpatched software.
It’s important to note that hacking without authorization is illegal and can have serious consequences. Hacking can lead to data breaches, theft of personal information, and financial loss, among other things. It’s important to take steps to protect your devices and data from potential hacking attempts.
Is being hacked easy?
Being hacked is not always easy to detect, as some hacking attempts can be very sophisticated and difficult to identify. Hackers can use a variety of methods to gain unauthorized access to your device or accounts, such as malware, phishing emails, or social engineering tactics.
While some attacks may be easier to detect, such as a ransomware attack that locks your device and demands payment, others may be more subtle and may go unnoticed for a long time. For example, a hacker could gain access to your email account or social media profile and use it to send malicious messages or posts without your knowledge.
It’s important to take steps to protect yourself from potential hacking attempts, such as using strong passwords, keeping your software up-to-date, being cautious with suspicious messages or emails, and using two-factor authentication. If you suspect that your device or accounts have been hacked, it’s important to take immediate action to limit the damage and prevent further attacks.
How to tell if your phone has been hacked?
It can be difficult to tell if your phone has been hacked, but here are some signs that may indicate that your phone has been compromised:
- Unusual activity: If you notice unusual activity on your phone, such as strange pop-ups, notifications, or unfamiliar apps that you did not install, it could be a sign that your phone has been hacked.
- Battery drain: If your phone’s battery life is significantly shorter than usual, it could be a sign that malware or spyware is running in the background and consuming battery resources.
- Slow performance: If your phone is running slower than usual or apps are taking longer to load, it could be a sign of malware or spyware running in the background.
- Increased data usage: If your phone is using more data than usual, it could be a sign that malware is sending data from your phone to a remote server.
- Suspicious texts or calls: If you receive suspicious text messages or phone calls, it could be a sign that your phone has been compromised.
If you suspect that your phone has been hacked, it’s important to take immediate action. S
start by running a malware scan on your phone using antivirus software and consider resetting your phone to its factory settings. You may also want to contact your mobile provider or a security professional for additional help and advice.
A phone camera that has been hacked
If your phone camera has been hacked, it can be a serious violation of your privacy. Here are some signs that your phone camera may have been hacked:
- Camera app behavior: If the camera app on your phone behaves erratically, such as taking photos or videos without your knowledge or showing unusual error messages, it could be a sign that someone has gained unauthorized access to your camera.
- Unusual activity: If you notice unusual activity on your phone, such as lights turning on or off when you’re not using your phone, it could be a sign that someone is remotely accessing your phone’s camera.
- Battery drain: If your phone’s battery life is significantly shorter than usual, it could be a sign that malware or spyware is running in the background and using your camera.
If you suspect that your phone’s camera has been hacked, here are some steps you can take to protect your privacy:
- Cover your camera lens: Covering your camera lens with a piece of tape or a camera cover can prevent unauthorized access to your camera.
- Check your app permissions: Review the app permissions for your camera app and make sure that only trusted apps have access to your camera.
- Use antivirus software: Install antivirus software on your phone and run regular scans to detect and remove any malware or spyware that may be running on your phone.
- Reset your phone: If you suspect that your phone has been hacked, consider resetting your phone to its factory settings to remove any malicious software.
Apps that request permissions too frequently
Some apps may request more permissions than they need to function properly, which can potentially put your privacy and security at risk. Here are some common examples of over-requested app permissions to watch out for:
- Contacts: An app that does not need to access your contacts should not request permission to do so. This permission can give the app access to your entire contact list, which could be used for malicious purposes.
- Camera and microphone: An app that does not require access to your camera or microphone should not request permission to use them. These permissions can allow the app to record audio and video without your knowledge or consent.
- Location: An app that does not require access to your location should not request permission to use it. This permission can allow the app to track your movements and share your location with third-party advertisers or other entities.
- SMS and call logs: An app that does not require access to your SMS or call logs should not request permission to use them. These permissions can allow the app to read your text messages and call logs, potentially compromising your privacy.
It’s important to be mindful of the permissions that apps request and to only grant permissions to apps that truly need them to function properly. You can also review the permissions for each app in your phone’s settings and revoke any unnecessary permissions. Additionally, using a mobile security app can help you identify and protect against over-requested app permissions.
Open WiFi networks can be snooped on
Snooping via open Wi-Fi networks can be a serious security risk, as it allows potential attackers to intercept and view your internet traffic. Here are some steps you can take to protect yourself when using open Wi-Fi networks:
Use a VPN: A virtual private network (VPN) encrypts your internet traffic and routes it through a secure server, making it difficult for potential attackers to intercept your data. Consider using a reputable VPN service when accessing open Wi-Fi networks.
Avoid sensitive transactions: Avoid conducting sensitive transactions, such as online banking or shopping, when using open Wi-Fi networks. These transactions should only be conducted on secure, password-protected networks.

Use secure websites: Make sure to only use secure websites that have HTTPS encryption when accessing sensitive information or logging into accounts. This helps to protect your data from being intercepted by attackers.
Keep your device updated: Keeping your device’s operating system and apps up to date helps to ensure that any known security vulnerabilities are patched and addressed.
Disable automatic Wi-Fi connections: Disable automatic Wi-Fi connections on your device, as this can prevent your device from connecting to potentially insecure networks without your knowledge.
By following these tips, you can help to protect your privacy and security when using open Wi-Fi networks.
Can your phone be hacked remotely?
Yes, it is possible for a phone to be hacked remotely. Remote hacking typically involves the use of malware, which is a type of malicious software that can be installed on a device without the user’s knowledge or consent. Once installed, the malware can give the attacker remote access to the phone’s data and functions.
There are several ways that a phone can be infected with malware, including through malicious apps, phishing emails, and text messages containing links to malicious websites. Once the malware is installed on the phone, the attacker can use it to remotely access the phone’s camera, microphone, and other features, as well as to steal sensitive information such as passwords and personal data.
To protect your phone from remote hacking, it’s important to follow basic security best practices such as:

Installing security software: Install reputable antivirus and anti-malware software on your phone and keep it updated.
Keeping your software up to date: Keep your phone’s operating system and apps up to date with the latest security patches and updates.
Avoiding suspicious links: Don’t click on links in emails or text messages from unknown senders, and avoid downloading apps or files from untrusted sources.
Using strong passwords: Use strong, unique passwords for your phone and all your online accounts, and enable two-factor authentication when possible.
Avoiding public Wi-Fi: Be cautious when using public Wi-Fi networks, as they can be insecure and vulnerable to hacking.
By taking these steps, you can help to protect your phone from remote hacking and keep your personal data and information secure.
Is spyware real?
Yes, spyware is a real type of malicious software that is designed to secretly monitor and gather information from a device, including personal data, browsing history, and passwords. Spyware can be installed on a device through various means, such as downloading a malicious app, clicking on a link in an email or message, or visiting a compromised website.
Once installed, spyware can run in the background of a device without the user’s knowledge or consent and can be difficult to detect or remove. Some common signs of spyware infection include a slower device performance, excessive pop-ups, and unexpected changes to the device’s settings.

Spyware can be used for various purposes, including stealing personal information, monitoring online activity, and tracking a user’s location. It can also be used by cybercriminals to conduct espionage, such as stealing business secrets or government intelligence.
To protect against spyware, it’s important to follow basic security best practices such as installing reputable security software, avoiding suspicious links and downloads, and keeping your device and apps up to date with the latest security patches and updates. If you suspect that your device may be infected with spyware, it’s important to seek help from a cybersecurity professional.
Final Thoughts
In today’s digital age, it’s important to be aware of the risks and threats posed by cybercriminals and to take steps to protect yourself and your devices from hacking, malware, and other forms of cyberattacks.
By following basic security best practices such as using strong passwords, keeping your software up to date, and being cautious when using public Wi-Fi, you can help to safeguard your personal data and information.
It’s also important to be vigilant and to stay informed about the latest threats and vulnerabilities, as cybercriminals are constantly evolving their tactics and techniques.
By staying informed and taking proactive steps to protect yourself and your devices, you can help to ensure that you stay safe and secure in an increasingly connected world. If you liked this post please let us know in the comment section and tell us your thoughts on this topic. We hope you find this article in SPY24 useful! You can also read our other articles such as How to Hack a Webcam Without Them Knowing It?
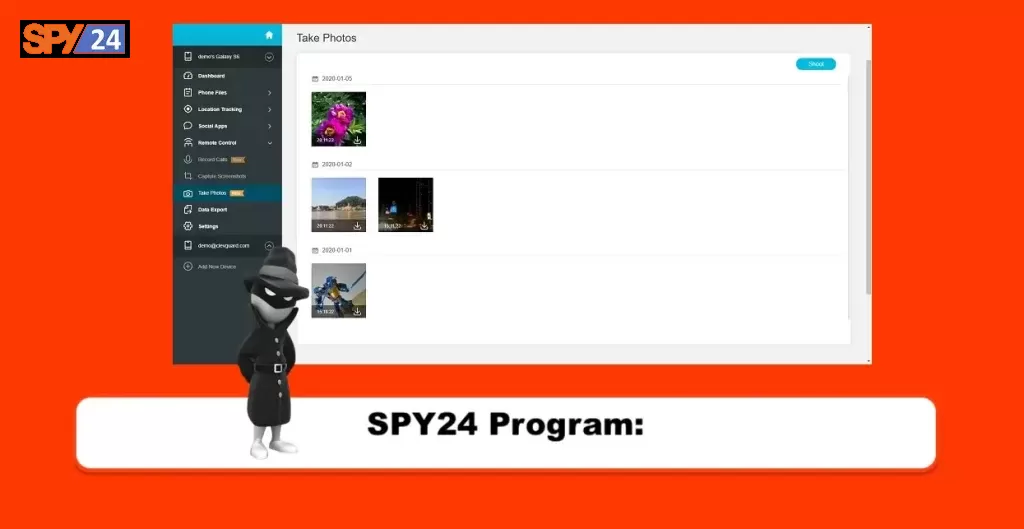
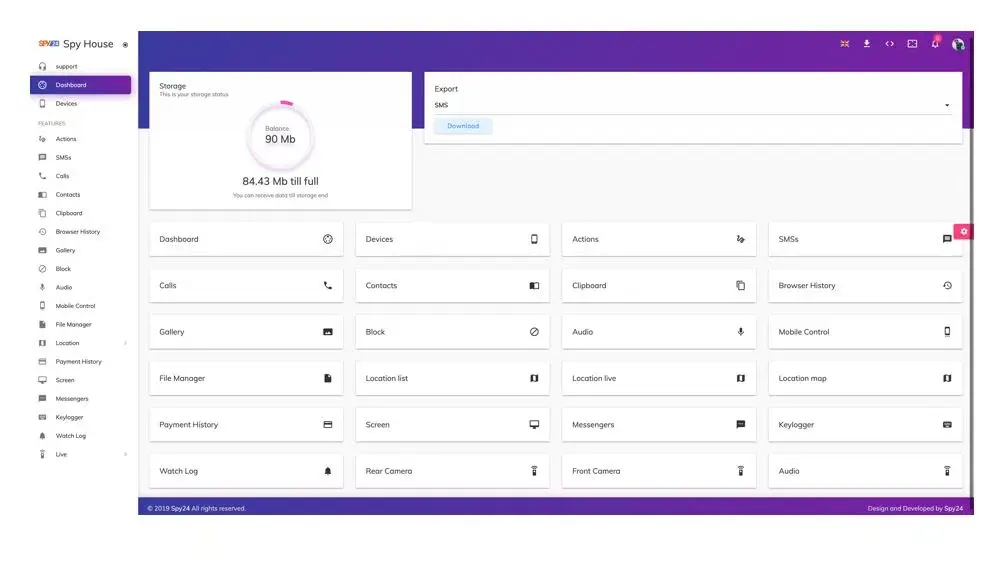
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.