How to Remote Hacking Software Mobile Download
Hackers are often portrayed as nefarious computer criminals. Still, in reality, the term “hacker” refers to anyone who uses their technical skills to solve problems, improve systems, or create innovative solutions. There are actually different types of hackers, including “white hat” hackers who use their skills for ethical purposes, such as improving cybersecurity or exposing vulnerabilities in systems, and “black hat” hackers who use their skills for malicious purposes, such as stealing information or disrupting systems.
Many hackers are curious, creative, and passionate about technology, and they enjoy exploring and pushing the boundaries of what’s possible. They often collaborate with other hackers and share their knowledge and skills with others in the community. Some hackers even participate in “hackathons” or other events where they work together to develop new ideas and solutions.
Overall, hackers are an important part of the technology ecosystem, and their skills and creativity can be used for both good and bad purposes. It’s important to understand the different types of hackers and to promote ethical and responsible hacking practices.
What is remote hacking?
Remote hacking, also known as remote code execution, is a type of cyber attack where an attacker gains unauthorized access to a computer or network from a remote location. This means that the attacker does not have physical access to the system or device that they are trying to compromise.
Remote hacking can be done using a variety of techniques, such as exploiting vulnerabilities in software, social engineering attacks, or phishing scams. Once the attacker gains access to the system, they can then use it to steal sensitive data, install malware, or take control of the system.

Remote hacking can be very dangerous, as it allows attackers to compromise systems and networks without ever physically being present. It is important for individuals and organizations to take steps to protect themselves against remote hacking, such as keeping their software up to date, using strong passwords, and implementing security measures such as firewalls and intrusion detection systems.
How does remote hacking work?
Remote hacking involves gaining unauthorized access to a computer or network from a remote location. There are several methods that attackers can use to achieve remote access, including:
- Exploiting vulnerabilities: Attackers can look for vulnerabilities in software or systems, and then use them to gain access. For example, an attacker may find a vulnerability in a web application and then use it to execute code on the server.
- Social engineering: Social engineering involves tricking users into giving up sensitive information or access to their systems. For example, an attacker may send a phishing email that appears to be from a trusted source, and then trick the user into clicking a link or downloading a malicious attachment.
- Brute force attacks: Brute force attacks involve guessing passwords or other authentication credentials. Attackers can use software to automate the process of guessing passwords, which can allow them to gain access to a system over time.
Once the attacker has gained remote access, they can then use the compromised system to steal sensitive data, install malware, or take control of the system. This can be very dangerous, as it can allow attackers to do significant damage without ever physically being present.
To protect against remote hacking, it’s important to keep software up to date, use strong passwords and two-factor authentication, and implement security measures such as firewalls and intrusion detection systems. It’s also important to educate users about the dangers of social engineering and phishing attacks.
The benefits of Remove hacking
Ethical hacking can provide several benefits, such as:
Identifying vulnerabilities: Ethical hackers can identify security weaknesses in systems that may not have been discovered otherwise. By addressing these vulnerabilities, organizations can improve their overall security posture and protect against potential threats.
Testing security measures: Ethical hacking can be used to test the effectiveness of security measures such as firewalls, intrusion detection systems, and access controls. By identifying weaknesses in these measures, organizations can improve their defenses and better protect against attacks.
Compliance: Many organizations are required by regulations or industry standards to conduct regular security assessments. Ethical hacking can help organizations meet these requirements and demonstrate compliance.
It’s important to note that ethical hacking should always be done with proper authorization and under controlled conditions to ensure that it does not cause harm to systems or individuals.
Remote hacking a sim card
Remote hacking of a SIM card involves gaining unauthorized access to the SIM card from a remote location. This can allow attackers to intercept communications, steal sensitive data, or use SIM cards to conduct fraudulent activities.
There are several methods that attackers can use to remotely hack a SIM card, including:
- SIM swapping: Attackers can convince a mobile phone carrier to transfer a victim’s phone number to a new SIM card in their possession. Once they have control of the phone number, they can intercept communications and gain access to sensitive data.
- SMS spoofing: Attackers can use software to send SMS messages that appear to be from a trusted source, such as a bank or other financial institution. If the victim responds to the message, the attacker can gain access to sensitive information.
- Vulnerabilities in SIM card software: Like any other software, the software running on a SIM card can have vulnerabilities that attackers can exploit. For example, an attacker could send a specially crafted SMS message that exploits a vulnerability in the SIM card software.
To protect against remote hacking of a SIM card, it’s important to take steps such as:
- Using two-factor authentication: Using two-factor authentication can help prevent SIM swapping attacks by requiring additional verification before allowing access to sensitive data or accounts.
- Avoid phishing scams: Be cautious of SMS messages or phone calls from unknown sources and avoid clicking on links or downloading attachments from suspicious messages.
- Keeping software up to date: Like any other software, the software on a SIM card can have vulnerabilities that are fixed with updates. It’s important to keep software up to date to protect against known vulnerabilities.
Remote hacking over the internet
Remote hacking over the internet involves gaining unauthorized access to a computer or network from a remote location using the internet. This type of hacking can be done from anywhere in the world and does not require the attacker to have physical access to the target system.
Remote hacking over the internet can be done using a variety of techniques, including:
- Exploiting vulnerabilities in software: Attackers can look for vulnerabilities in software or systems and then use them to gain access. This can include exploiting known vulnerabilities in operating systems, applications, or web servers.
- Social engineering attacks: Social engineering attacks involve tricking users into giving up sensitive information or access to their systems. This can include phishing scams or other types of social engineering attacks.
- Brute force attacks: Brute force attacks involve guessing passwords or other authentication credentials. Attackers can use software to automate the process of guessing passwords, which can allow them to gain access to a system over time.
Once the attacker has gained remote access, they can then use the compromised system to steal sensitive data, install malware, or take control of the system. Remote hacking over the internet can be very dangerous, as it can allow attackers to do significant damage without ever physically being present.
To protect against remote hacking over the internet, it’s important to take steps such as:
- Keeping software up to date: Software vulnerabilities are often patched in updates, so it’s important to keep software up to date to protect against known vulnerabilities.
- Using strong passwords and two-factor authentication: Using strong passwords and two-factor authentication can help prevent brute force attacks by requiring additional verification before allowing access to sensitive data or accounts.
Implementing security measures: Implementing security measures such as firewalls and intrusion detection systems can help detect and prevent unauthorized access to systems and networks.
Remote hacking wi-fi and Bluetooth
Remote hacking of Wi-Fi and Bluetooth involves gaining unauthorized access to a wireless network or device from a remote location using the internet. This type of hacking can be done from anywhere in the world and can give attackers access to sensitive data and systems.
Remote hacking of Wi-Fi and Bluetooth can be done using a variety of techniques, including:
- Wi-Fi cracking: Attackers can use software to crack the Wi-Fi password or gain access to the network through vulnerabilities in the Wi-Fi router.
- Bluetooth hacking: Attackers can use software to exploit vulnerabilities in the Bluetooth protocol to gain access to devices or intercept data transmitted over Bluetooth.
- Man-in-the-middle attacks: In this type of attack, attackers intercept communications between devices and act as a middleman, allowing them to intercept sensitive data or inject malware.
Once the attacker has gained remote access to the wireless network or device, they can then use the compromised system to steal sensitive data, install malware, or take control of the system. Remote hacking of Wi-Fi and Bluetooth can be very dangerous, as it can allow attackers to do significant damage without ever physically being present.
To protect against remote hacking of Wi-Fi and Bluetooth, it’s important to take steps such as:
- Using strong passwords and encryption: Using strong passwords for Wi-Fi networks and encryption for Bluetooth connections can help prevent attackers from gaining access to the network or device.
- Disabling unnecessary services: Disabling unnecessary Wi-Fi or Bluetooth services can help reduce the attack surface and prevent attackers from exploiting vulnerabilities in these services.
- Keeping software up to date: Software vulnerabilities in Wi-Fi routers and Bluetooth devices are often patched in updates, so it’s important to keep software up to date to protect against known vulnerabilities.
Implementing security measures: Security measures such as firewalls and intrusion detection systems can help detect and prevent unauthorized access to wireless networks and devices.
Is remote hacking easy?
Remote hacking is not easy and requires a high level of technical knowledge and skill. It can take a lot of time, effort, and resources to successfully carry out a remote hack. However, as technology continues to advance, it has become easier for attackers to automate some of the processes involved in remote hacking, making it more accessible to a wider range of attackers.
Additionally, attackers are constantly developing new tactics and techniques to bypass security measures and exploit vulnerabilities in systems and networks. This means that defenders need to be constantly vigilant and stay up to date on the latest security threats and best practices to protect against remote hacking.
While remote hacking may not be easy, it is still a significant threat that can result in serious damage and financial losses for individuals and organizations. It is important to take steps to protect against remote hacking, such as using strong passwords, keeping software up to date, and implementing security measures such as firewalls and intrusion detection systems.
How to spy on someone without having to know how to hack?
There are spy tools such as spy24 or other spy apps that you can use to spy on someone and monitor their activities through various social media platforms.
- Install monitoring software: There are many monitoring software programs available that allow you to track a person’s online activities, including their web browsing history, social media activity, and instant messaging conversations. These programs can be installed on the person’s computer or mobile device with their consent.
- Use parental control features: Most modern operating systems and web browsers come with parental control features that allow you to restrict access to certain websites and monitor online activity. These features can be used to keep track of your child’s online activities and ensure they are using the internet safely.
- Hire a private investigator: If you have concerns about a person’s activities and want to investigate further, you can hire a licensed private investigator to gather evidence legally and ethically.
It’s important to remember that any form of monitoring should be done for legitimate reasons and with the person’s consent whenever possible. It’s also important to follow applicable laws and regulations regarding privacy and data protection.
How to tell if your phone has been hacked?

If you suspect that your phone has been hacked, there are several signs that you can look out for:
- Battery drain: If your phone’s battery is draining much faster than usual, it could be a sign that there is a rogue app or process running in the background that is draining your battery.
- Unusual activity: If you notice unusual activity on your phone, such as text messages or phone calls that you didn’t make, or apps that you didn’t install, it could be a sign that someone else is using your phone.
- Slow performance: If your phone is running slower than usual, it could be a sign that there is malware or other malicious software running on your device.
- Unfamiliar pop-ups and ads: If you start seeing unfamiliar pop-ups and ads on your phone, it could be a sign that your phone has been infected with malware.
- High data usage: If your phone’s data usage is much higher than usual, it could be a sign that there is malware or other malicious software running on your device that is using up your data.
If you suspect that your phone has been hacked, there are several steps you can take to protect yourself:
- Update your phone’s software: Make sure your phone’s operating system and apps are up to date, as updates often include security patches that can help protect against hacking.
- Install anti-virus software: Install an anti-virus app on your phone to help detect and remove any malware that may be present.
- Change your passwords: Change your passwords for all your accounts, including email, social media, and financial accounts, as these could be compromised if your phone has been hacked.
- Reset your phone: If you are unable to remove the malware from your phone, you may need to reset your phone to its factory settings. This will erase all data on your phone, so be sure to back up any important data before doing so.
If you are still unsure whether your phone has been hacked, it is best to seek the assistance of a professional, such as a cybersecurity expert or a mobile phone technician.
Poisoning of the domain name services
DNS poisoning, also known as DNS spoofing or DNS cache poisoning, is a type of cyber attack that involves changing the IP address associated with a domain name in the DNS cache of a DNS server. This can cause legitimate users who try to access the website to be redirected to a fake website, which can be used to steal sensitive information such as login credentials or credit card information.
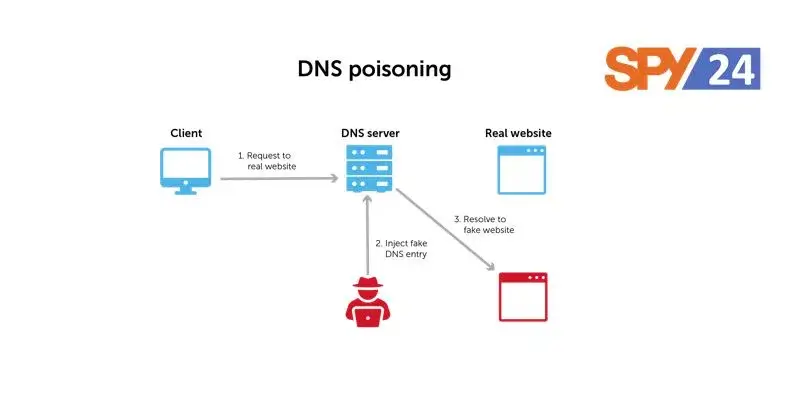
DNS poisoning can be carried out in several ways, including:
- Man-in-the-middle attack: An attacker intercepts the communication between the user and the DNS server and injects fake DNS responses into the communication.
- Pharming: An attacker infects a user’s computer with malware that modifies the DNS settings and redirects the user to a fake website.
- DNS cache poisoning: An attacker exploits vulnerabilities in the DNS software to inject fake DNS records into the cache of the DNS server.
To protect against DNS poisoning, it is important to take the following steps:
- Use a reputable DNS server: Use a DNS server that is known to be secure and reliable, such as those provided by your internet service provider (ISP) or by well-known companies such as Google or Cloudflare.
- Implement DNSSEC: DNSSEC (Domain Name System Security Extensions) is a security protocol that provides authentication and integrity verification for DNS responses, making it more difficult for attackers to carry out DNS poisoning attacks.
- Use HTTPS: Use websites that have HTTPS (Hypertext Transfer Protocol Secure) enabled, which encrypts the data transmitted between the user and the website and helps protect against man-in-the-middle attacks.
- Keep software up to date: Keep your computer and other devices up to date with the latest security patches and software updates to reduce the risk of malware infections and other security vulnerabilities that could be exploited in DNS poisoning attacks.
By taking these steps, you can help protect yourself and your organization against DNS poisoning attacks.
Spraying passwords
Password spraying is a type of cyber attack that involves trying a small number of commonly used passwords against a large number of user accounts in order to gain unauthorized access. Unlike brute-force attacks, which involve trying every possible password combination, password spraying is more targeted and aims to bypass security measures by using a list of known weak passwords.

The basic steps of a password spraying attack are:
The attacker selects a list of commonly used passwords, such as “password”, “123456”, or “qwerty”.
The attacker targets a large number of user accounts, such as those on a company’s network or a popular web service.
The attacker uses an automated tool to try each password against each account until they find one that works.
Once the attacker gains access to an account, they can use it to steal sensitive data, install malware, or carry out other malicious activities.
To protect against password spraying attacks, it is important to:
Use strong passwords: Avoid using common passwords that are easy to guess, and instead use complex passwords that are difficult to crack. A strong password should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols.
Implement multi-factor authentication (MFA): MFA adds an extra layer of security to the authentication process by requiring a second factor, such as a fingerprint or a one-time code sent to your phone, in addition to your password.
Monitor for suspicious activity: Regularly monitor your accounts for suspicious activity, such as failed login attempts or unusual access patterns.
Limit login attempts: Limit the number of failed login attempts before locking an account or imposing a temporary lockout period to prevent password-spraying attacks.
By taking these steps, you can help protect yourself and your organization against password-spraying attacks.
Remote hacking Spyware
SPY24: SPY24 solution is another high-quality and popular spyware. It provides access to most info on the target phone without the need to root or jailbreak (except for some apps). Just like SPY24, on an Android system, it must first be installed. For iOS, it doesn’t even need that.
Flexispy: This spyware has many essential features, including access to live information
Flexispy: This spyware has many essential features, including access to live information (calling and recording) and a camera. It does, however, need rooting in some cases. calling and recording) and camera. It does, however, need rooting in some cases.
Shadow Spy: This spyware works only on android phones. However, it does its job great. It also has a 3-day free trial for you to test the app and decide if you want to continue using it. It provides the user with information such as live location, camera and calls, and keystroke log, among others. It must be downloaded on the target phone once.
- Remote hacking Malware
Malware refers to any kind of malicious software (as the name implies), including worms, viruses, adware, etc. One type of malware that can be used to hack a mobile device is Trojan (-horse). Trojans are malware disguised as harmless messages, advertisements, links to free music or software, and other similar forms. When a Trojan is “let in”, it creates a backdoor in the system for the attacker to access the phone and take control. The Trojan will work in complete stealth, gathering data such as usernames and passwords and delivering them to the hacker.
What is Phishing?
Phishing is a type of cyber attack that involves tricking users into divulging sensitive information, such as passwords, credit card numbers, or personal information. Phishing attacks typically involve sending fraudulent emails or messages that appear to come from a legitimate source, such as a bank or a popular website, and asking the user to click on a link or enter their login credentials or other sensitive information.

The goal of a phishing attack is to steal sensitive information that can be used to commit identity theft, fraud, or other malicious activities. Phishing attacks can also be used to distribute malware, such as ransomware or keyloggers, that can be used to gain access to sensitive data or hold it for ransom.
To protect against phishing attacks, it is important to:
- Be vigilant: Be wary of emails or messages that ask you to click on a link or provide sensitive information, especially if they are unexpected or come from an unknown source.
- Check the sender’s email address: Check the sender’s email address to ensure that it matches the expected sender. Attackers often use spoofed email addresses that appear to come from a legitimate source but are actually fraudulent.
- Look for signs of fraud: Look for signs of fraud in the message, such as poor grammar or spelling mistakes, unusual formatting, or urgent requests for sensitive information.
- Don’t click on links or download attachments: Avoid clicking on links or downloading attachments in suspicious messages, as they may contain malware or lead to fraudulent websites.
- Use anti-phishing software: Use anti-phishing software or browser extensions that can help detect and block phishing attacks.
By taking these steps, you can help protect yourself and your organization against phishing attacks. Remember that attackers are always coming up with new and more sophisticated methods of carrying out phishing attacks, so it is important to remain vigilant and stay up to date on the latest threats and countermeasures.
Final thoughts on hacking software mobile
In conclusion, cybersecurity threats such as remote hacking, phishing, and password spraying are very real and can have serious consequences for individuals and organizations. It is important to stay informed about these threats and take steps to protect yourself and your sensitive information.
Some best practices for staying safe online include using strong and unique passwords, enabling multi-factor authentication, being cautious of suspicious emails and messages, keeping software and systems up to date with the latest security patches, and using reputable security software and tools.
Remember that cybersecurity is an ongoing process, and staying safe online requires constant vigilance and awareness. By following best practices and taking proactive steps to protect yourself and your organization, you can help reduce the risk of cyber-attacks and minimize the potential impact of any incidents that do occur.
We would appreciate it if you could let us know in the comment section what you thought about this post and tell us what you think about it in general.
Warning! Android phone remote control // Hackers can hack your phone
In this video, I’m going to show you how I can remotely control an Android phone. If you install software or I use a special cable, an O.M.G. cable, to get that phone to download and install software, I can. Remotely control the phone. I can read your SMS and send SMS from the phone to another phone which I’ll demonstrate. May this video be a warning to both you and your family why you should not download untrusted software? In a previous video, I showed you how I could log keystrokes when the software was downloaded and run on a Windows 11 laptop. Use the link below to see that video. Now you can do many things here. As an example, if I type Sysinfo, you can see that this phone is running Android 12. If I go to settings on the phone, you can see that the version being used here is Android. 12. I can read SMS remotely. O.M.G. cables are essentially the same. They act like normal cables but have an AP inside them that you can connect to using WiFi. They can send keystrokes to a device such as a phone. What we are doing is getting the device to download a malicious APK file from a server. The server is running on Linode who I want to thank for sponsoring this video.
Metasploit is running on the cable modem. It opens up a web browser and connects to the server. It downloads the apk file. Installs the file. Then allows that app to access everything on the phone, basically. We can also send SMS from the phone once again. Android phones should not accept applications such as this. The default behavior should be to block all these types of applications. Do not download software from the internet that you do not trust. I have attached a pdf document below this video that shows you how to set this up.