How to Bypass Two-Factor Authentication Instagram
(This article covers how to bypass two-factor authentication on Instagram. Learn how to use methods like SMS, email, biometric authentication, and third-party apps to gain access to your account. Discover the security risks associated with bypassing two-factor authentication and how to protect yourself.)
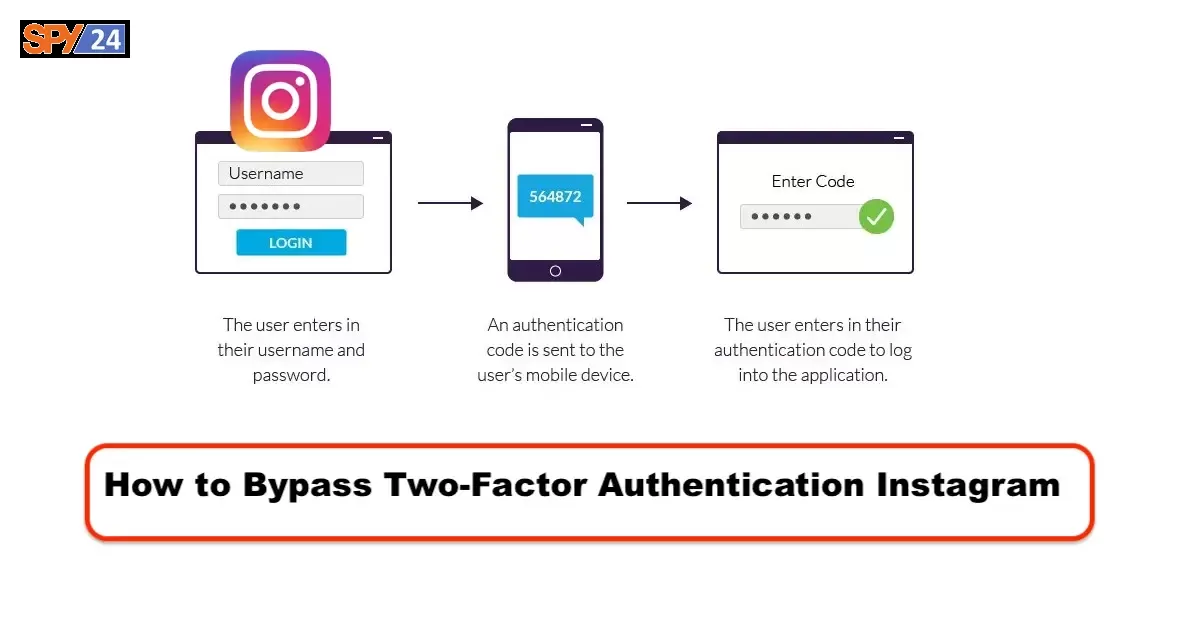
Two-Factor Authentication is a security feature offered on many websites and apps that require users to provide an additional layer of authentication when signing into their account. This extra layer of security helps protect user data from unauthorized access, making it more difficult for hackers and other malicious actors to gain access to someone’s account. However, if you’re trying to bypass two-factor authentication on Instagram and don’t feel like waiting the usual amount of time required to go through the process, then you might be wondering how you can do so quickly and easily. In this blog post, we’ll be looking at ways to bypass two-factor authentication on Instagram so you can get back into your account faster.
What is Two-Factor Authentication?
Two-factor authentication is an extra layer of security that can be used to protect your account. When you enable two-factor authentication, you’ll need to enter a code that is sent to your mobile device every time you try to log in. This code can help prevent someone from accessing your account, even if they have your password.
How does two-factor authentication work?
Two-factor authentication is an extra layer of security that can be added to your account to make it more difficult for someone to hack into your account. When you enable two-factor authentication, you will be required to enter a code that is sent to your phone or email each time you try to log in. This code is generated by an app on your phone or by a service such as Google Authenticator.
- Google Authenticator
- Microsoft Authenticator
- Salesforce Authenticator
- SecureAuth
- Duo Security
- Symantec VIP
- Transakt
- LastPass Authenticator
So Why Do You Need Two-Factor Authentication?
In a world where data breaches are becoming more and more common, two-factor authentication helps protect your accounts from being hacked. Without two-factor authentication, hackers can easily guess your password and access your account. With two-factor authentication, even if a hacker guesses your password, they will still need access to your smartphone to gain access to your account.
Now that you understand why two-factor authentication is important, you may be wondering how to enable it for your accounts.

How to Enable Two-Factor Authentication on Instagram
To enable two-factor authentication on Instagram, first, open the Instagram app. Tap on the profile icon in the bottom right corner. Next, tap on the settings gear icon in the top right corner. Scroll down to “Account” and tap on “Two-Factor Authentication”. Then, tap “Require Security Code” and enter a security code that you would like to use.
Once you’ve set up a security code, you will need to enter it each time you want to log in to Instagram. This security code will be sent to your smartphone and you’ll be asked to enter it each time you want to access your account.
To activate two-factor authentication:
Click the More menu at the bottom left, then click Settings settings.
Click Privacy and security in the menu on the left.
Scroll down to Two-Factor Authentication, then click Edit Two-Factor Authentication Settings.
Choose the security method you want to add and follow the instructions on the screen.
When you set up two-factor authentication on Instagram, you’ll be asked to choose one of three security methods:
Authenticator app: (recommended): Download an authenticator app, such as Duo Mobile or Google Authenticator to get login codes.
This security method is recommended because you can add multiple connected devices to one account so they can all get login codes.
Note: Two-factor authentication via an authenticator app can only be activated through the Instagram app for Android and iPhone.
Text Message: We’ll send a login code to your mobile phone number.
WhatsApp: Activate the text message security method first.
Then you can activate the WhatsApp security method to get WhatsApp login codes.
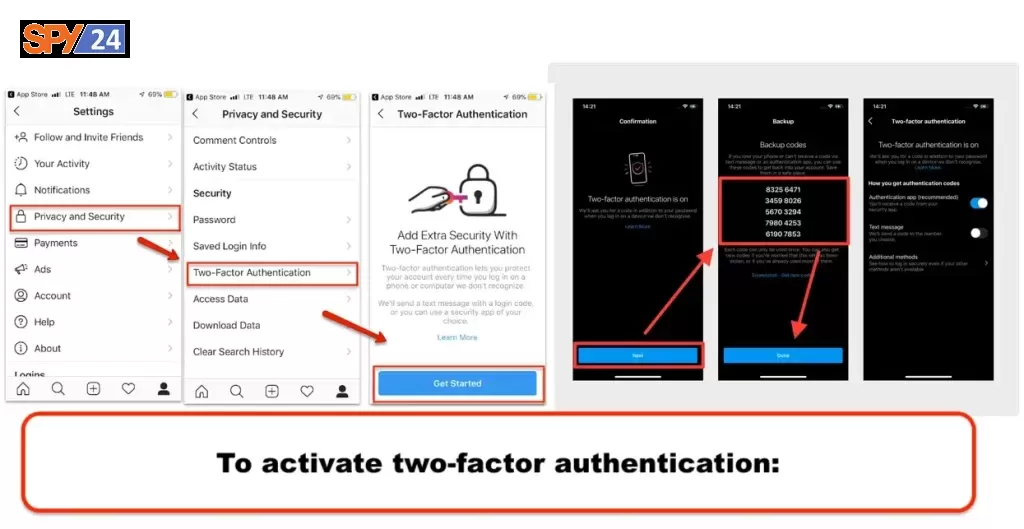
You will need to have at least one of these configured to use two-factor authentication.
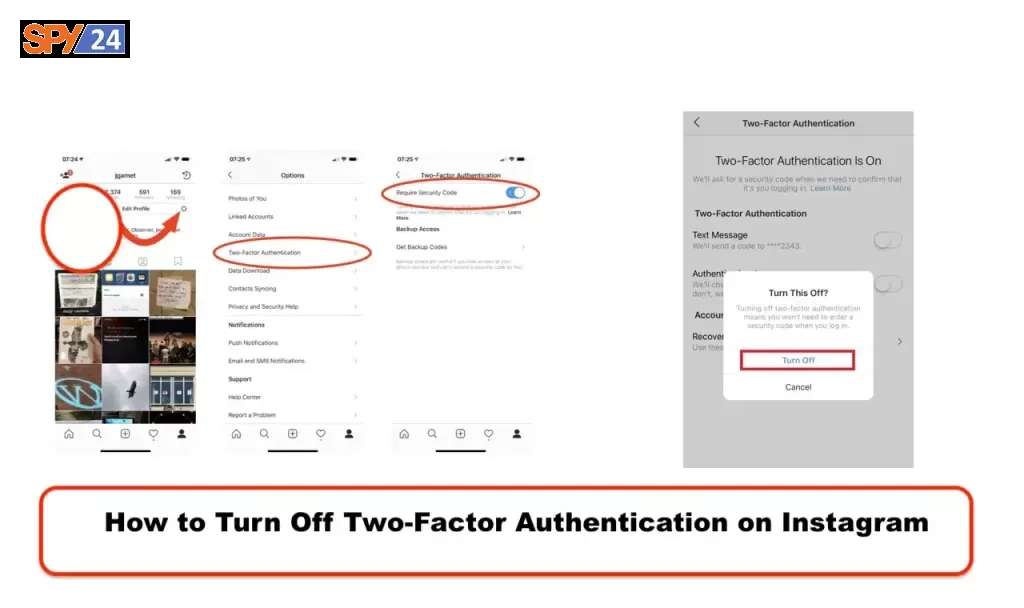
How to Turn Off Two-Factor Authentication on Instagram
Although 2FA is a great way to keep your account safe, it can be a hassle when you need to log in quickly. Thankfully, there is a way to remove 2FA from your Instagram account without having to log in.
To deactivate two-factor authentication on a connected device:
To access your profile, tap your profile or your profile picture in the bottom-right corner.
Tap More Options in the upper-right corner, then tap Settings.
Select Security, followed by Two-Factor Authentication.
To remove a device, tap More options to the right of the desired device.
Tap Delete. Note that removing a device from two-factor authentication does not log the device out of your account.
Note: Your Instagram key can be used if multiple authentication apps are installed on the same device. Follow the steps outlined above on the same device.
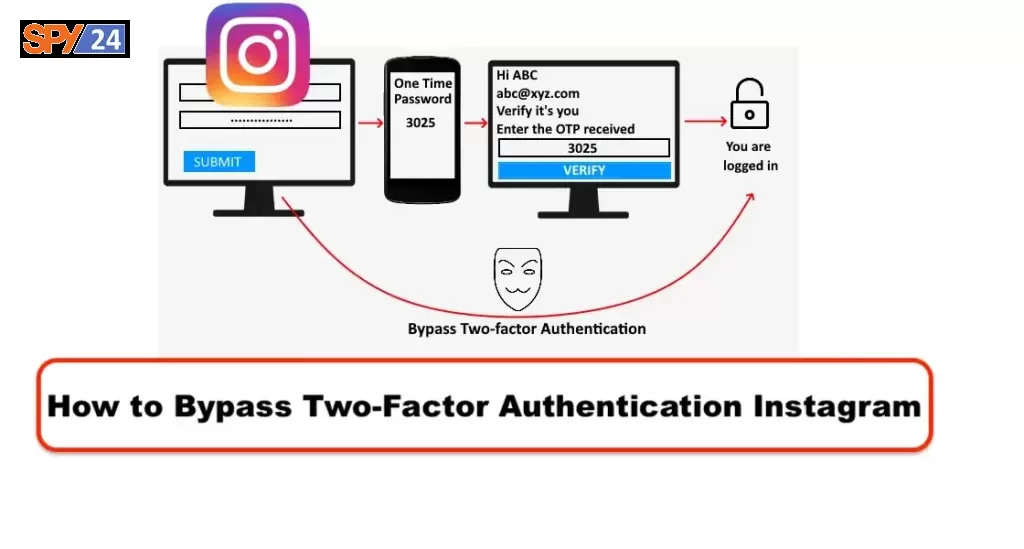
How to Bypass Two-Factor Authentication Instagram
Yes, you can bypass Instagram’s two-factor authentication. However, it’s not recommended, as it’s a very insecure way to access your account. If you already logged in to your Instagram then all you need to do is go to the settings of the account after that just disable the two-step verification. When you enter the Instagram application and are on a page that asks you for two-step verification, take a screenshot of the same page and copy it to a secure location. If you have the option to bypass the two-factor authentication system on Instagram, you can do so by using the phone number associated with the account or by using a third-party authentication app. Additionally, you can also try brute force methods to bypass the two-factor authentication system, but it is a highly insecure method and should be avoided.
1. Bypassing 2FA with conventional session management
Bypassing two-factor authentication (2FA) with conventional session management involves using existing login credentials to gain access to an account without the need for a verification code. To do this, you would need to have already established a session with the account and then use the existing credentials to log in again without having to enter the verification code. This can be done by using a different device or browser, or by using a private browsing window or incognito mode.
- The attacker clicks on the ‘change password’ link.
- The attacker requests the password reset token.
- The attacker uses the password reset token.
- The attacker logs into the web application.
- Using this method, attackers can bypass the two-factor
authentication in certain platforms where the architecture of the site or platform makes it possible.
However, this is not recommended as it is an insecure way to access your account and is not recommended for use.
2. Bypassing 2FA using Open Authorization (OAuth)
Bypassing two-factor authentication (2FA) using Open Authorization (OAuth) is a process by which a user can log in to a platform or website with a third-party account such as Instagram or Google. To do this, the site requests an authentication token from the third-party site and verifies the user account. Once the user is verified, the site logs the user in. This is a convenient way to bypass 2FA, but it is important to note that it is not very secure and can be easily compromised.
- The website requests a token of authentication from a third-party website (e.g., Instagram).
- The user account is verified by Instagram (or another third-party site).
- Instagram (or a third-party website) transmits a callback code.
- The site authenticates the user.
Here, the attackers don’t even need to use 2FA if they, for example, have the user’s Facebook or Gmail username and password.
3. Bypassing 2FA using brute force
Bypassing two-factor authentication (2FA) using brute force is a trial-and-error process used to guess credentials in order to gain unauthorized access to an account. It is highly insecure and should be avoided as it can be easily detected and can cause significant damage.
When the length of the two-factor authentication code is between four and six characters (often just numbers), brute-force attacks against the account can circumvent 2FA.
This method involves trying various combinations of usernames and passwords until the correct one is found. It is not recommended and is considered illegal in many countries.
4. Bypassing 2FA using earlier-generated tokens
Bypassing two-factor authentication (2FA) using earlier-generated tokens is a method of bypassing 2FA by using a document or file with a certain number of verification codes that have been generated in advance. This method can be used by attackers if they get access to the document, as they can use it to bypass 2FA. It is important to note that this method is not very secure as the attacker would also need to have the user’s password in order to access the document.
Some platforms allow users to generate tokens, such as a document containing a certain number of codes, that can be used later to bypass 2FA. If an attacker gains access to the document, they can easily circumvent 2FA if they also possess the user’s password.
5. Bypassing 2FA using social engineering
Bypassing two-factor authentication (2FA) using social engineering is a technique used by attackers in which they use deception, manipulation, and psychological tactics to get the user to give away their 2FA code or other sensitive information. This can be done through phishing emails, telephone calls, or other forms of social engineering. It is important to be aware of these tactics and to ensure that your employees are trained to recognize and avoid them.
6. Bypassing 2FA with Session Cookie or Man-in-the-middle
Bypassing two-factor authentication (2FA) with a session cookie or man-in-the-middle is a type of attack in which an attacker uses a session cookie or a man-in-the-middle attack to bypass the two-factor authentication process. In this type of attack, an attacker can gain access to a user’s account by intercepting the session cookie or by using a man-in-the-middle attack. This type of attack can be prevented by using secure protocols such as TLS or SSL and by implementing measures such as IP whitelisting.
Cookie stealing, otherwise known as session hijacking, is stealing the user’s session cookie. When users log into a site, they do not need their password every time.
A cookie contains the user’s information, keeps the user authenticated, and tracks their session activity. The session cookie stays in the browser until the user logs out, and closing the window doesn’t log the user out.
So, an attacker can use the cookie to his advantage. Once the hacker acquires the session cookie, he can bypass the two-factor authentication. Attackers know many hijacking methods, like session sniffing, session fixation, cross-site scripting, and malware attacks.
Also, Evilginx is a popular framework that hackers use for man-in-the-middle attacks. With Evilginx, the attacker sends a phishing link to the user, which takes the user to a proxy login page. When the user logs into his account using 2FA, Evilginx captures his login credentials and the authentication code.
Because the OTP expires after using it and is only valid for a short time, there’s no need to capture the authentication code. Instead, the hacker has the user’s session cookies, which he uses to log in and bypass the two-factor authentication.
7. Bypassing 2FA with SIM-Jacking
SIM-jacking is a type of identity theft that targets your phone number. It involves taking control of your mobile number and is used to bypass two-factor authentication. Hackers will send a piece of spyware-like code to a target device using an SMS message. If the user opens the message the hacker will be able to take control of their phone number, allowing them to bypass the Multi-Factor Authentication (MFA) and gain access to any account connected to the phone number. This attack works by first doing a SIM swap on the victim’s phone number. A SIM swap is when an attacker transfers the phone number of a victim to a SIM card owned by them. This allows them to then use the new SIM card for authentication and gain access to the user’s accounts.
8. Bypassing 2FA with Spyware
Spyware is another method that attackers can use to bypass two-factor authentication (2FA). Attackers can use spyware to gain access to the user’s device and steal the authentication codes used for 2FA. Spyware can be installed on a user’s device by exploiting vulnerabilities in the operating system or by sending malicious links or attachments through emails, chat messages or other communication channels. Once the spyware is installed, the attacker can gain access to the user’s device and use the authentication codes to bypass 2FA. This type of attack can be prevented by using anti-spyware software, keeping all software up to date, and being aware of malicious emails, messages, or other communication channels.

Why Can’t You Log Back into Your Instagram?
If you’ve enabled two-factor authentication on your account, then you must enter a unique code sent to your phone or email address in order to access your account. If you don’t enter the code, then you won’t be able to log back in. This is done to protect your account from unauthorized access and make sure that only you have access to it.
Is It Possible to Bypass OTP?
If you’ve enabled two-factor authentication (2FA) on your account, then you’ll need to enter a one-time password (OTP) in order to access your account. You can bypass this code by entering the correct username and password that you used to set up your account. This is not recommended, however, as it could leave your account vulnerable to unauthorized access.
Can 2 Factor Authentication be Bypassed?
Yes, two-factor authentication can be bypassed. However, this is not recommended as it could leave your account vulnerable to unauthorized access.
Can You Bypass Instagram 2-Step Verification?
Yes, you can bypass two-step verification on Instagram. This requires you to enter a one-time password (OTP) in order to access your account. This code is sent to your phone or email address, and you will have to enter it in order to log back into your account.
What If You Lose Your Phone with Two-Factor Authentication?
If you lose your phone with two-factor authentication enabled, then you won’t be able to log back into your account. You will have to contact Instagram and provide them with additional information to prove that you are the rightful owner of the account. If they are satisfied with your proof, then they will reset your account and allow you to log back in.

Can Multi-Factor Authentication be Hacked?
Multi-factor authentication is a very secure form of authentication, and it is very difficult to hack. However, it is still possible for hackers to bypass it if they have access to your phone or email address. The best way to protect yourself is to enable two-factor authentication on all of your accounts and use strong passwords that are difficult to guess.
In conclusion, bypassing two-factor authentication on Instagram can be done in several ways. You can use a third-party authentication app, create an account without two-factor authentication, or use a virtual private network. No matter which method you choose, always make sure to keep your account and personal information secure.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.