How to Secure My Phone from Hackers?

Phone hacking can put your identity and privacy at risk without you even understanding it. Fraudsters are constantly developing and enhancing their hacking techniques, making them harder to detect. This indicates that the intermediate user could be overwhelmed by any number of cyberattacks. However, you can save yourself by remaining up-to-date on the latest hacks.
Phones have carried all our accounts and private information into one suitable place, making our phones an ideal goal for a hacker. Everything from account banking to email and social media is connected to your phone. This indicates that when a criminal gains access to your phone, all of your data are available to cyber theft.
What is phone hacking?

Phone hacking contains any strategy in which an individual gains access to a phone or its contacts. This can vary from state-of-the-art security breaches to eavesdropping on unsafe internet links. It can also contain physically stealing your phone and forcibly hacking it through techniques such as brute force. Phone hacking can occur on all types of phones, including Android and iPhone systems. Since anyone can be at risk of phone hacking, we suggest that all users know how to recognize a compromised gadget.
How do Protected phones from hacking?
If you desire to be proactive, there are many steps you can take to save yourself from phone hacking, most of which contain typical sense. Additionally, there are developed techniques to guarantee your phone is as secure as feasible.
Basic Phone Security Tips
For everyday phone users, sticking to the basics to stop simple hacking attempts is an excellent place to begin:

- Never leave your phone unattended: Always keeping your cell phone in a public area is the first and most useful practice to track.
- Modify your phone’s default passcode: Your phone probably has an easy and predictable default password that those in the know can utilize to their benefit. Alter your code to something more complicated and defy common code that is typically used.
- Manage your Bluetooth Security: Do not employ unsafe Bluetooth networks and turn off your Bluetooth service when not in use.
- Protect your PIN and Credit Card data: Utilize a secure app to keep PINs and credit cards, or sufficiently yet, don’t keep them on your phone at all.
Advanced Ways to Prevent Phone Hacking
If you’re still concerned about being hacked, there are more steps you can take to safeguard yourself. Nevertheless, overdoing everything defeats the goal of having a smartphone.
- Avoid unsecured public WiFi: Hackers usually target significant locations such as bank accounts over public Wi-Fi, which is usually not secure due to lax or even non-secure security criteria.
- Turn off you’re autocompleted feature: By doing so, you can stop access to stored critical personal information.
- Regularly delete your browsing history, cookies, and cache: Eliminating your virtual footprint is critical in minimizing the quantity of data that can be collected by prying eyes.
- Have an iPhone? Enable Find My iPhone: By turning on this attribute in the settings, you can discover your phone if you put it before hackers get their feet on it.
- Use a security app that increases protection: For Android users, Webroot suggests an integrated Mobile Security app for Android that offers antivirus protection and lets you remotely find, lock, and unlock your phone if you lose track of it. For iOS users, Webroot also suggests a free safe web browser to enhance mobile security on the iPhone and iPad.
How to Know If Someone is Hacking Your Phone
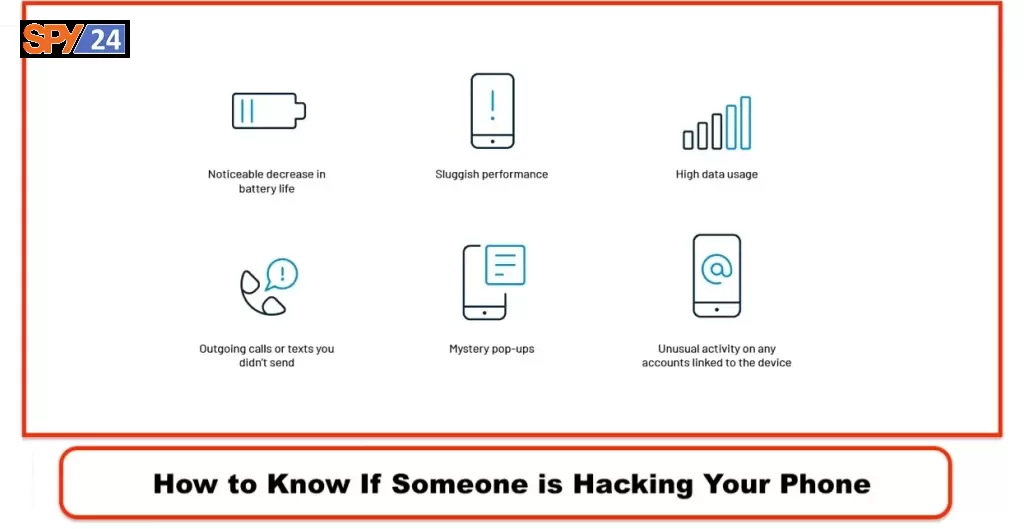
- Your phone loses charge fast: Malware and rogue apps occasionally use malicious code that manages to exhaust a lot of energy.
- Your phone operates abnormally slowly: A breached phone may give all its processing power to stealthy hacker programs. This can slow your phone. Unpredictable crashes and unanticipated reboots can occasionally be signs.
- You detect abnormal activity on your other online accounts: When a hacker accesses your phone, he attempts to steal access to your invaluable accounts. Scan your social media and email for password reset requests, uncommon login places, or new account registration confirmations.
- You notice strange calls or messages in your logs: Hackers may hit your phone with an SMS Trojan. On the other hand, they can impersonate you to steal the personal data of your valued ones. Be careful, because any of these techniques leave breadcrumb-like output messages.
What to Do If You’re Smartphone Has Been Hacked
You have understood how to tell if someone is hacking your phone. Currently, you are ready to deal with it. Here’s how to remove these cyber criminals from your Phone.

First, you need to remove any malware that has entered your gadget. Once you root out an information breach, you can save your accounts and keep hackers away from your gadget.
What To Do if Your Phone Has Been Hacked
- Use antivirus software: Antivirus software quarantines malware in a sandbox so it can’t influence the remains of your device. It removes it for you. No more calls from inside the house. Hold your antivirus software turned on to keep it operating in the background.
- Contact businesses: Contact any monetary services or e-commerce companies that have your credit card or bank account data, which is very susceptible to data. Find out which transactions you should discuss with your bank and, in some circumstances, report fake.
- Delete apps: If you notice applications on your device that you haven’t downloaded, remove them.
- Factory-reset your phone: However, it is better to do a full factory reset on your device to fix it to the settings it had when you received it.
- Modify your passwords: Eventually, alter the passwords of any breached accounts, a reasonable approach whenever your login credentials are applied in a data breach.
How Do Phones Get Hacked?
The reason we take so considerable precautions with our phones is that hacks can occur in many forms. Here are some instances:

- Phishing: Phishing messages involve social engineering – for example, requesting individuals instantly for their login credentials to achieve access to PC systems. Phishing is possible not only via email and SMS but also via fraudulent phone calls. If you receive a weird message or email from somebody you don’t know, don’t click on it. The same applies to social media messages.
- Brute-force attacks: Brute-force attacks are possibly the most basic way of hacking, as hackers only guess passwords until they log inaccurately.
- Man-in-the-middle attacks: Using this technique, hackers track information packets as they travel between the sender and the receiver and listen for login information.
- Physical access: Whether the phone is lost or robbed, it’s much more effortless to hack if it doesn’t have a password.
- Programming-based hacking: Hacking based on programming needs the most specialized ability. Hackers discover exposures in systems and give themselves full administrative rights.
Conclusion:
Today, data is widely available on the Internet. Enthusiastic people can learn and adjust instantly. The motive behind hacking is what puts hackers apart. This ability is utilized to harm people or governments or for personal profit, which makes hackers scary. The kinds of hacker attacks differ from organization to organization. The severity and type of attack rely on the capability of hackers to find loopholes and infiltrate the security system. So this has put a lot of stress on all organizations to constantly be up-to-date with their cyber security protection.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.




