How To Hack Telegram Account With Two-Step Verification?

Are you looking for ways to safeguard yourself from the dangers of cybercrime? You’ll be happy to learn that there’s something even more secure than a simple password- Telegram, with its two-step verification process. Yes, it may sound like an elaborate measure, however, setting up this added security is easy and doesn’t require any fancy technology! Hacking Telegram has become a full-time job in recent years and having two-step verification adds an extra layer of protection against intruders. So why not give it a try? Read on as we show you how to hack telegram using two-step verification!
How to Hack Telegram with Two-Step Verification
Have you ever heard of the popular messaging app, Telegram? If so, then you’re probably familiar with its two-step verification feature. This feature is designed to protect users from hackers and other cyber threats. In this blog post, we’ll explore how two-step verification works, how to enable it in Telegram, and how to disable it if necessary.
What is Telegram Two Step Verification?
Two-step verification (also known as two-factor authentication) is an extra layer of security that requires both a code sent via SMS or email as well as your password to log into your account. This helps keep your account secure by making sure that only you can access it.
How to Enable Two-Step Verification on Telegram?
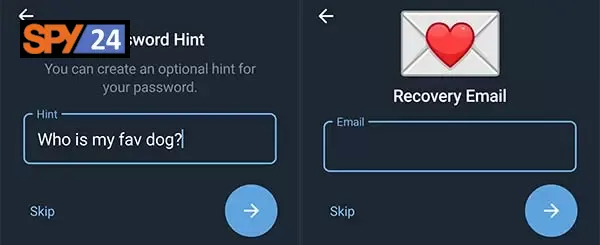
To enable two-step verification on Telegram, open the app and go to “Settings” > “Security & Privacy.” From there, select “Two-Step Verification” and follow the instructions provided. You will be asked to provide an email address for recovery purposes and will be required to create a backup code that can be used if you forget your password or lose access to your email address. Once this is done, you will be all set!
1. Settings
2. Tap “Privacy & Security.”
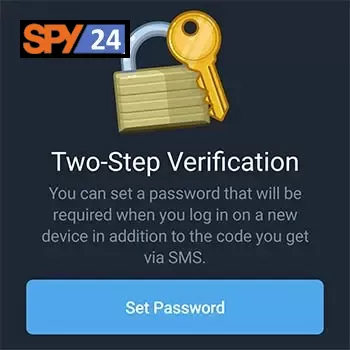
5. Type your password and press “Continue.”
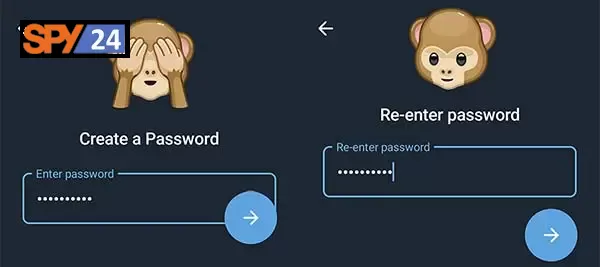
7. Set a password hint in the following window.
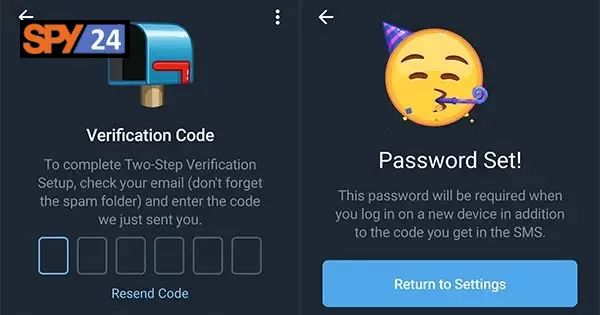
Disable Two-Step Verification in Telegram:
If for some reason you need to disable two-step verification on Telegram, simply go back into the “Settings” > “Security & Privacy” menu and select “Disable” under the Two-Step Verification option. Then enter your current password or recovery code (if necessary) and confirm that you wish to disable the feature. That’s it! Your account should now be protected without two-factor authentication enabled.
- Run telegram application
- Tap on the three-line icon to see the menu
- Choose “settings”
- Tap on “privacy & security”
- Select the “two-step verification” option
- Enter your password and tap on the tick icon
- Choose ” Turn Password Off “
- Click on “OK” in the pop-up window that appears.
How do I enable a fingerprint lock on Telegram?
If You Are Using an Official Telegram Client Follow This Steps :
- Open Telegram ( Obviously ).
- Open Drop Down Menu and Tap On “ Settings ”.
- Tap on the “ Privacy and Security ” Tab.
- Tan on Passcode ( Under Security Tab ).
- Enable “ Passcode Lock ” and Add Pin First.
- Now Enable “ Unlock With Password ”.
That’s it. But maybe Different For Different Clients.
Bypassing Two-Factor Telegram
Below are six common ways cybercriminals can bypass Two-Step Verification. Hackers can also use these methods to bypass two-factor authentication.
- Social Engineering
- Phishing
- Exploiting Generated Tokens
- SIM Hacking
- Email spoofing
- Spyware Software
Conclusion: Hacking into someone else’s Telegram account can be difficult if they have enabled two-step verification. However, understanding how this security feature works can help keep your own accounts safe by adding an extra layer of protection against malicious actors online. By following these simple steps, anyone can enable two-step authentication on their account and rest easy knowing their data is secure from prying eyes! SPY24 also provides additional layers of protection such as encrypted storage of data on our servers, so make sure to check out our website for more information about our services today!
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.