How to Protect Telegram from Hacking?
Has someone hacked my Telegram account? If this question happened to you, something must be false. You may not be able to access your account because your password has been altered without your license. You may have found questionable activity on your account. Someone else may have informed you of their story about a hacked account. Whatever the case, if you suspect that someone may have hacked your account, you should do everything you can to save it. We will try to show how you can secure your Telegram account and make sure that it is not hacked.
What is Telegram?
Telegram is a prevalent instant messaging app provided by Telegram Messenger Inc. It can be used in Android, iOS, Windows, Mac, and Linux operating systems, and also its website is telegram.org. At the start of the year, 200 million monthly active users were using the service, and that number has certainly increased in the rest of the year. Obviously, these numbers are amazing, but what is even more remarkable is that these numbers were documented only 16 months after Telegram’s initial launch. No wonder this name always appears in the list of the most famous instant messaging apps and services along with Facebook Messenger, WhatsApp, WeChat, Snapchat, Skype, etc. However, popularity constantly draws cybercriminals. Sure, large corporations have better resources to guarantee the security and satisfaction of their customers, but Telegram security isn’t always effortless.

Can Your Telegram Account Be Hacked?
Telegram is a widespread instant messaging app. This platform has been around for years, so it’s not unknown to internet users. In addition to numerous features that make contact easy, the app asserts to present users with maximum safety and privacy features. This may explain why so considerable individuals choose it. Nevertheless, Telegram is not as perfect as you might believe. It can be hacked by people who are looking to use people’s personal data. Thus, users ask a typical question: “Is it possible to hack a Telegram account?”
The answer is yes. Your Telegram account can be hacked in different forms. When a Telegram company is hacked, your account password is compromised. This is named public hacking. This type of hack often impacts numerous users, so you don’t need to do much. There is a high probability that it will be resolved shortly. The security and privacy group of the company will notify you of the required measures.

Another method that can put your Telegram account at risk is spyware. Spyware traces and records all your movements on your mobile device. These activities include chats, calls, and video calls in Telegram, other apps, and general activities on your phone. You might wonder how that is feasible. Well, spyware is usually a deliberate way to hack someone’s Telegram account. If you doubt that this is your case, the spyware must have been installed on your phone by the hacker without you guessing it. It is required to access your device. Most of the time, the hacker is probably someone close to you.
The condition with spyware is that everything on your phone is compromised. Thus, not only your Telegram data but also others are susceptible to disclosure. A fast fix is to check your phone for the odd app.
What are the symptoms that your Telegram has been hacked?
Now that you understand that your Telegram can be hacked in various forms, you need to know how to tell if your account has been compromised. In this way, you can take the essential actions as soon as possible.

Unknown activities on your Telegram
One of the first detectable signs that someone is manipulating your Telegram account is that you see new changes that you didn’t make. For instance, new contacts appearing on your phone or changing your name and profile photo are symptoms of hacking. If this is your case, start by checking your Telegram security information.
Messages are being sent or received without your understanding
Another indication that you should pay attention to is the messages from the contacts or the messages that you have received. If your contacts draw your attention to a message they receive and you didn’t send them, this is an indication of a hack. These spam messages often contain corrupted photos, videos, and file content.
You will receive a message from the Telegram
As one of the methods Telegram promises to protect its users’ accounts, it usually sends a message to users when they see weird activity. For example, you may receive a message that your account has been logged in from a different location. If it’s not you, somebody will hack your account. Also, consider your account is logged in from another device. In this case, you will receive an email from Telegram requesting you to verify if it is you or not. Make sure you verify that the message you receive is clearly from Telegram. This is because hackers may act like Telegram to deceive you into providing personal information about your account.
You can’t access your account
Eventually, another symptom that someone has hacked or is attempting to hack your account is that you can’t set up your Telegram account on your phone or PC. Again, if you are demanded to enter your login details every time you attempt to access your account, your account may be tampered with.
How someone can hack a Telegram account
Telegram employs very powerful industry-standard encryption for all messages between the customer and their servers for regular conversations. For confidential conversations, they use end-to-end encryption between two devices. Encryption is so powerful that hacking an account with today’s resources is nearly unbelievable, even for government law enforcement agents. So how is it possible for hackers and rogue governments to hack Telegram accounts?
The difficulty is not in the encryption system but in the login protocols. Telegram accounts are bound to their phone numbers at the time of initial creation. You can modify this phone number. Every time a person logs into his Telegram account with a new phone, the server sends a short message with the login code to the registered phone number.
Today, this is the real drawback of Telegram or any other secure messaging app that depends on SMS to get into the phone. This SMS is not encrypted and can be seen by the phone operator. Thus, for instance, if you’re in Iran and the government knows your phone number, all they have to accomplish is log into Telegram with a new phone utilizing your phone number. When the server sends the login SMS to your number, they can intercept it at the operator. Utilizing this number, they can log into your Telegram account on another phone.

The SMS protocol is very unsafe. If you have the essential expertise and resources, any hacker can intercept Telegram login SMS and log into your user account with your phone. Then they can read old texts and scan your contacts. The only messages they can’t read are the ones hidden in the conversation, encrypted between the two devices.
Another method to hack your account is to have someone (think your girlfriend!) access your phone for a short period of time. During this time, they can log into your account through their phone and utilize the text message sent to them to log into your account.
What to do if your Telegram account is hacked:
Knowing whether your Telegram account has been hacked or not relies on how it was hacked. It goes without saying that if you have not secured your Telegram account, the chance of someone hacking it is much higher. Typically, when an individual hacks a user account, the login is compromised. Hackers can’t do anything unless they get access to your unsecured Telegram account. Thus, how can hackers breach clearly protected accounts? They usually use brute-force attacks to guess input data.
If you believe cybercriminals spend hours typing in accidental passwords and username mixtures to make a good guess, you’re wrong. Today’s hacking strategies are much more developed and can employ hardware and software to achieve a triumphant brute-force attack in minutes or just seconds. This is particularly easy if the password and username are predictable, such as password123 and my computer. However, passwords are not usually utilized to enter Telegram.

When you log in to Telegram, you must enter your phone number to get a confirmation code that will allow you to access your account. If you believe that this makes your Telegram safe, you are not 100% right. In 2016, hackers were able to compromise Telegram accounts in Iran by utilizing a fault in the SMS protocol. The confirmation codes sent via SMS were intercepted and provided to hackers. This gives them full access to the Telegram accounts as well as adding new devices to the same account to resume the attack.
This defect also allowed hackers to recognize 15 million unique phone numbers registered on Telegram. In circumstances like this, unless the hackers modify the password and block your access to the account, or send messages that you can notice in your chat history, you may not be conscious of the hack at all. Finally, if unsecured Telegram accounts are hacked, attackers can spy on users and collect susceptible data that can later be used to hack larger accounts and cause more damage.
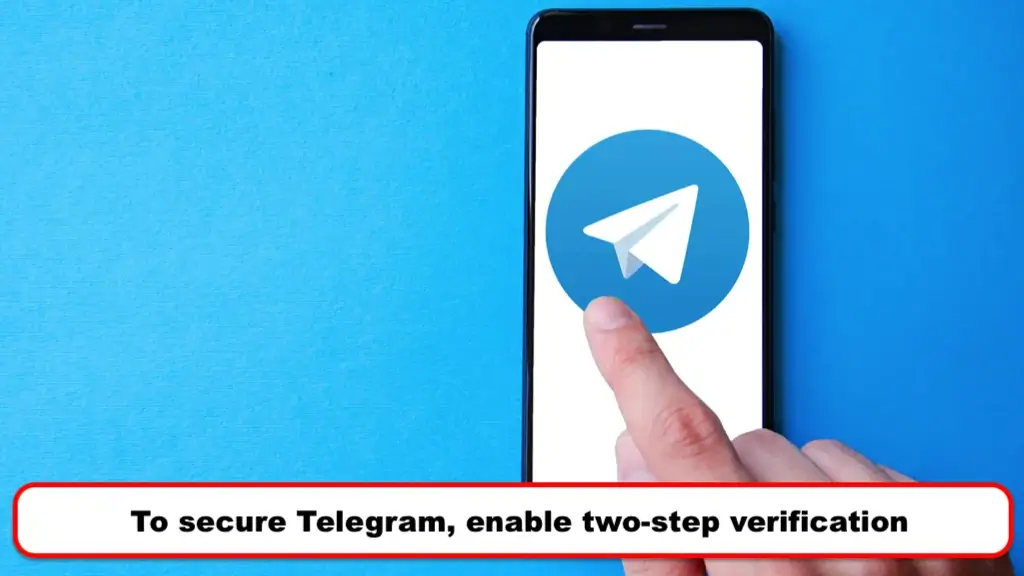
To secure Telegram, enable two-step verification
You should be aware of two-step verification, also known as 2FA or two-factor authentication. You likely have it set up on many accounts such as Gmail, Facebook, or Instagram. If you have not guaranteed Telegram utilizing the two-step verification feature, we recommend that you address this issue as soon as possible. After doing this, you will need to enter a password when logging in from a new device. Here is a guide showing how to secure Telegram by setting up two-step verification through the Telegram application.
- Open your Telegram application and log in.
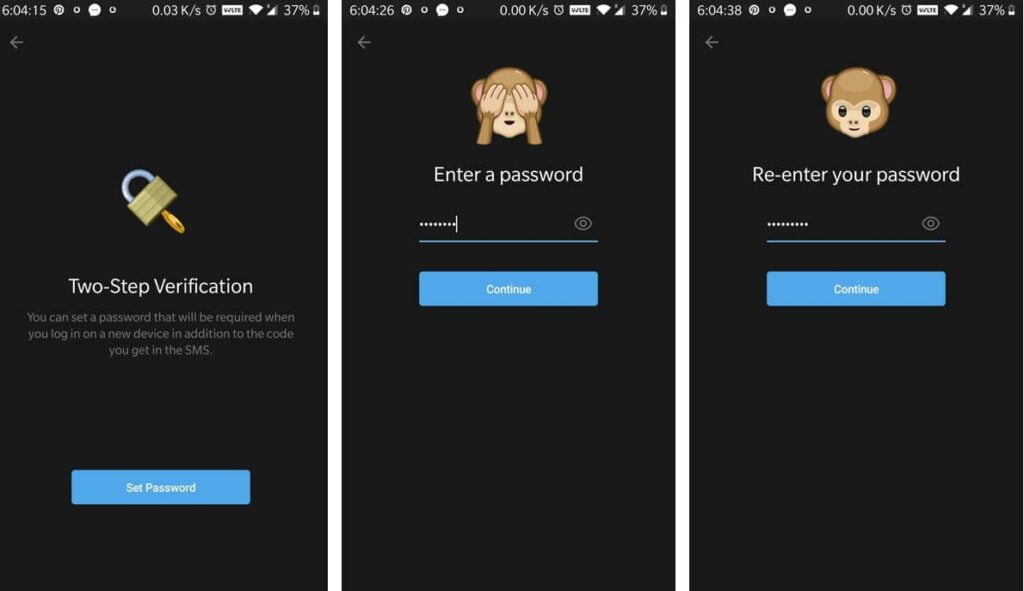
- Tap the “Menu” button in the upper right corner.
- Go to “Settings” and then tap “Privacy & Security”.
- Tap on “Two-Step Verification”.
- Make a strong password and re-enter it for verification.
- Make a hint for the password.
- Enter your email address and tap the “green check” icon.
- Go to your inbox, open your email, and click the “verify link”.
Telegram allows you to make powerful passwords, so make sure you create a long mixture of numbers, upper and lower case letters, and symbols. Of course, generating a random password guide is useless, but you can secure your Telegram confirmation password by utilizing a secure password manager. This guarantees that you can access your password if you cannot remember it. For instance, if you utilize the free Cyclonis Password Manager, you can save the password as a private note, and it will be encrypted so that no one except you can access it.
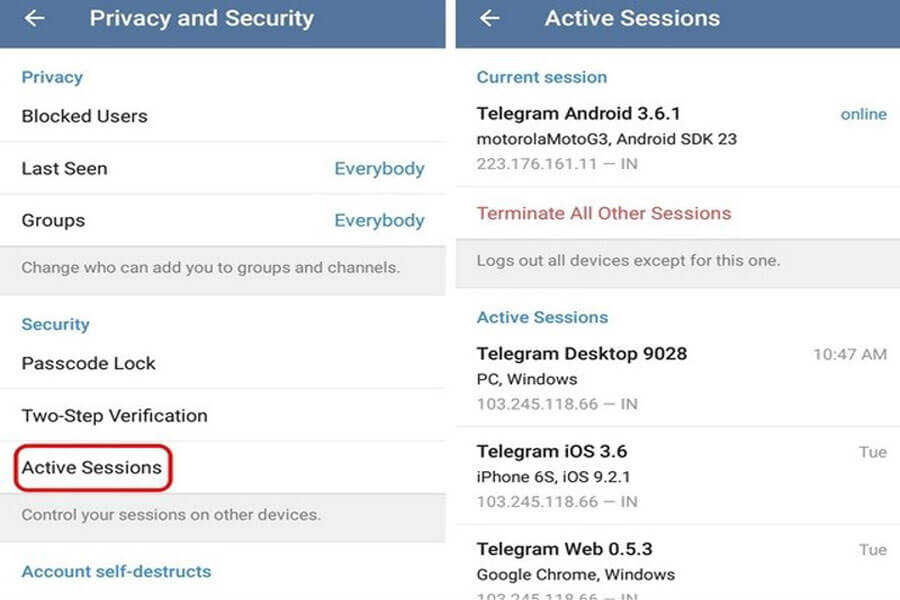
For Telegram security, terminate Active Sessions
Telegram supports multiple devices, which implies you can open the same Telegram account on different devices at the same time. Over time, you cannot remember that you are logged into some phones/laptops, and it may be abused. To make sure this doesn’t occur, scan all devices where your Telegram account is logged in.
If someone has logged into your Telegram account, you can notice it in the Active Sessions menu. This feature allows you to terminate undesirable sessions, which will hopefully help keep hackers at bay.
- Open your Telegram app and log in.
- Tap the “Menu” button in the upper right corner.
- Go to “Settings” and then to “Active Sessions”.
- Tap “Terminate All Other Sessions” or choose one session at a time and tap “OK” to terminate.
Disable P2P calls for everyone
Using default settings, Telegram voice calls are made through P2P. When employing P2P, the IP address of the user’s contact object emerges in the Telegram control log. Nevertheless, not all editions have control logs. For instance, the Windows version does not, while the Linux version does. The Telegram app offers that users can prevent IP addresses from being compromised by modifying settings. Go to Settings: Privacy – Security – Voice Call – Change Peer-to-Peer to Never or Nobody. With these settings, the user must make a voice call via the Telegram server, although the IP address is hidden, but at the cost of reducing the sound quality.
Never open executable files of other users
Instead of attacking any inherent feature of Telegram itself, some hackers simply use Telegram as a way to speak with their possible victims. For instance, some hackers have set up channels that aim to give curious users software to “crack private keys” and employ in their own hacking. Yet, after being opened by the victim, this “hacking software” infects their PC with the HackBoss malware, which substitutes all crypto wallets on that computer with their own versions of those wallets. And modified crypto wallets transmit all funding to the attacker.
Beware of impersonation
It is very typical for hackers and fraudsters to impersonate Telegram users by selecting a username that is very close to the original name, but slightly different from it. For instance, an attacker might attempt to impersonate dev0ps1 by making the username devops1. Make certain you know who you are dealing with.
How to recover your account if your mobile phone is stolen (or lost)
When we lose our phone or it is stolen, it is necessary to take a sequence of actions such as blocking it using IMEI. Yet, on the subject, we need to recover the Telegram account. After you have blocked your SIM card and have a new SIM card, insert it and install Telegram on the new device. Go through the total initial activation procedure again. Recall deleting your old phone when you have access. If you don’t, anyone who finds or steals your old phone can utilize it easily.
The time our mobile phone is stolen or lost, you can fast disable your access if we already have another paired device for the PC. In this case, go to Telegram from your PC and close your lost mobile session.
FAQs
How can I open Telegram without a confirmation code?
Telegram is a messenger application that you can be certain of its security, quickness, and expense. To open Telegram without a confirmation code, you must first separate your phone number from your account. To accomplish this, go to Settings -> Privacy and Security -> Phone Number and select “Unlink”. Then open the Telegram application and log in with your username and password.
How can I get a phone number in Telegram?
Telegram also lets you add individuals as friends just by adding their phone numbers. You can even add them by selecting a name or nickname from your contact list or by scanning a QR code.
How to protect my Telegram account from hackers?
To protect your account, you should improve the safety of your account using the ways mentioned in this article. For instance, you need to set a password lock for your Telegram, allow two-step verification, scan your active sessions, and more.
How can I enter Telegram with another phone?
To enter Telegram from another phone, you must download the Telegram application from the Google Play Store or the Apple App Store. The confirmation code will be sent to you through SMS.
Can I make another Telegram account?
Yes, you can make another Telegram account. The Telegram application lets you create numerous accounts. When you log in with your phone number, the app confirms the account by sending a code to your phone. It may take a few minutes for the account to be confirmed. If your phone is locked or forgotten, you won’t be able to log into the app utilizing that number.
How to prevent telegram hacking?
To prevent Telegram from being hacked, you must pay attention to numerous security advice and track them. You should also avoid opening unknown links, dubious messages, unknown files, etc.
Conclusion
Has someone hacked my telegram? Hopefully, they didn’t, and I wish you never have to ask this question again. If your account has been hacked, you should be very careful, particularly if you have decided to store your ID in Telegram’s virtual cloud. Terminate doubtful sessions and instantly set up two-step verification to stop unauthorized access to your account, and if your password has been compromised, modify it as soon as possible. Be sure to be careful about how you deal with others on the platform. If you desire to keep Telegram safe, make sure you don’t click on dubious links and don’t share private data with anyone. Furthermore, consider utilizing secret conversations to guarantee that all information is encrypted and cannot be intercepted by hackers.
in this article on SPY24, we talked about How to protect Telegram from hacking? And we told you some methods for preventing Telegram hacking. If you’re interested in this topic or want to know how to hack a Telegram account? you can also refer to other related articles in our magazine. Also, you can share your opinion in the comment section below.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.




