Best Twitter Hacking Software Free Download 2022
Are you ready to unlock the world of secret data and gain exclusive access to the virtual universe? Whether you’re looking for corporate espionage or just want to find out what your friends are up to, there’s no better tool on the market than Twitter hacking software. With SPY24, you can crack into Twitter accounts with ease, giving you access to view what is typically private information. Now that we’ve established why it’s advantageous for users to get their hands on some top-notch Twitter hacking software, let us show you how best to take advantage of it: by downloading free versions! We’ll provide an in-depth look at our pick of the best Twitter hacking apps available online today.
Twitter Hack and Security
Twitter is a social program that has a lot of celebrities and people using it on a daily basis, and it’s more informative. From a 15 or 16-year-old to a major foreign politician. Almost everyone uses this app and social network to publish news, so it has a lot of fans. So because its users are from all segments of society, opening an account in this app should be in a way that is safe!
But the question is whether Twitter provides enough security for its users. In general, Twitter can be introduced as a relatively secure social network and its job is to protect users’ information and privacy, but they may result in their account being hacked due to mistakes made by some users. By the way, you need to know how to hack Twitter to prevent it. Some other ways to increase Twitter’s security can also be read in the article “How to increase your Twitter security.”Below we will talk about 6 ways to hack people’s Twitter accounts.

Methods: Twitter account hacking
As we said, in this article, we are trying to talk to you about 6 reliable ways to hack Twitter, but the question arises why should we know these methods? Do we even know how to hack a Twitter account, what do we do? Knowing how to hack a Twitter account or other virtual network will help you in two situations.
The first help of knowing these methods is that you can learn how to deal with Twitter account hacking and Twitter hacking methods, increase the security of your Twitter account, and not be hacked. The second application of knowing Twitter hacking methods is that if you are in a situation where you need to infiltrate a Twitter account, you have the ability to do so.
This intrusion can be because you have forgotten your password and want to find it you can use these methods. Or you may need to sign in to your child’s or someone else’s account and control the account; Although this is illegal and not morally correct, you can hack other people’s Twitter accounts with these methods.
Beware Hackers: The Best Twitter Hacking Software Free Download
Are you a hacker looking for the best Twitter hacking software free download? If so, then this is the post for you. In this guide, we will be exploring the many different types of Twitter hacking software that are available and can help protect your accounts from malicious actors. We’ll also be discussing how to prevent twitter hacking in 2022 and beyond.
How To Hack A Twitter Account
Blog Introduction: Are you a digital security expert looking for ways to hack into a Twitter account? If so, then you’ve come to the right place. In this article, we’ll discuss several different methods of how to hack someone’s Twitter account. We’ll cover social engineering, phishing, brute force attacks, hacking through vulnerabilities, and more!
Social Engineering:

Social engineering is an attack method that involves manipulating people into providing confidential information or access to systems by using deceptive tactics. The attacker will use psychological manipulation techniques such as impersonation and flattery in order to gain the trust of the target. Once they have gained the trust of their target, they can then use this access to gain information about their target’s Twitter account or even take over the account entirely.
Phishing: Twitter Account
Phishing is another attack method that is used by attackers in order to gain access to sensitive information or accounts across various platforms. In this method, attackers will send out malicious links or emails with the intent of stealing a person’s credentials when they click on them. Once attackers have a person’s credentials, they can then use them to log into their target’s Twitter account and take control of it.
Hacking Through The Device:
Finally, attackers may attempt to hack into someone’s device in order to gain access to their Twitter account from there. This could be done by infecting a device with malware or exploiting known hardware vulnerabilities on the device itself (such as those found on older versions of iOS). Once the attacker has gained access to a device, they have free rein over any accounts associated with it – including any connected Twitter accounts!
The first way that comes to mind with hackers is to infiltrate a device that you use to log on to Twitter. This will not only access your Twitter, but your entire device will be in hacker control. This is done by client hacking methods, but for mobile devices, other methods are used. Hacking client attacks, commonly described as the quietest type of hacking, are one of the most insidious and annoying types of hacking carried out remotely.
This type of attack involves exploiting the weaknesses in the software to gain access to the system. The basis of Client Side Hacking attacks stems from the victim’s own system itself. To be a victim, contrary to the notion that the device does not have to be available to a hacker. In many cases, users, with their own mistakes and actions, put the password in front of the hacker’s eyes and this makes it easy to hack by different people. We must state that when your target is the server of a site, the server of a network, and collectively a computer called the server, the attack that is carried out is the type of client hacking. For hacking mobile devices, there are also different software that you can find with a simple look, but one of the most powerful software in this field.

Why This Twitter Hacking Tool:
In this article, you will learn about some of the best Twitter spy apps that you can use to monitor and hack someone’s Twitter account.
Track Cell Phone Activity: Call logs, Messages, E-mails, Documents, Calendar, Photo, Video, Apps, and more
Location Tracking: GPS, Geofencing, WiFi logger
Monitor WhatsApp, Skype, Facebook, Instagram, Snapchat, Line, Kik, Tinder, Hangouts, and more.
Remote Control: Schedule, App blocker
1. SPY24:
SPY24 is one of the most popular and reliable Twitter spy apps available on the internet. It is a powerful tool that can be used to monitor someone’s social media activities, including Twitter. With SPY24, you can track the activities of any Twitter user and access their direct messages, posts, likes, comments, and more.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
- Spyine:
Spyine is another powerful Twitter spy app that can help you monitor someone’s Twitter activities without getting detected. With Spyine, you can view the direct messages, posts, and likes of any Twitter user. It also provides real-time updates on the activities of the target user.
- Spyic:
Spyic is one of the best Twitter spy apps available on the internet. It is a highly advanced tool that can help you monitor someone’s Twitter activity without getting detected. With Spyic, you can track the activities of any Twitter user and access their direct messages, posts, likes, comments, and more.
- Minspy:
Minspy is a powerful Twitter spy app that can help you monitor someone’s Twitter activities without getting detected. With Minspy, you can track the activities of any Twitter user and access their direct messages, posts, likes, comments, and more.
Hacking Through Vulnerabilities:
Attackers may also attempt to exploit known software vulnerabilities in order to gain access to a person’s Twitter account. For example, if an attacker discovers that there is an unpatched vulnerability in the underlying codebase used by Twitter, they could use this vulnerability as a way into someone’s account without needing any login credentials at all.
The hacker uses special programs to randomly test many passwords to finally get the correct password. These attacks depend on the type of password and may take a very long time, sometimes up to a few months, and may not even end up. However, to increase the speed of this process, systems with stronger processing are also needed.
For this reason, it is usually recommended that you choose a strong and secure password as well as hardness on various social networks or sites where you create accounts. Many hackers collect certain information such as your name, pet name phone number, Username in a game, or any other data that they think is useful, and by various apps, Brut Force enters different passwords and hacks your Twitter account.
From the information, you know about yourself and the knowledge you have of your passwords, hack into your account password so that if you forget it, you can easily hack through you’ve been careful in articles about enhancing Twitter security or any other social network, one of the constant things you’re offered everywhere is to set up a strong and unpredictable password. That’s why one of the reasons is why. That’s because if your password is linked to certain data in your life, you’re more likely to be hacked.
Brute-Force Attacks:
In this hacking method, the hacker or hacker tries to discover the bug and vulnerability of Twitter’s own site so that it can access users’ accounts using this issue. The possibility of hacking in this way is very low because large companies like Twitter are constantly monitoring servers and sites and will quickly fix the damage if they see the damage.
Penetration testing tools are also software and scripts that help hackers and security professionals find different vulnerabilities at the application, software, server, and network level. A good variety of these tools can be found in the web world, especially many of which are open source. Some of the free hack and penetration testing tools are:
Types of Twitter Hacking Software
Brute-force attacks involve attempting to guess passwords or passphrases until a correct one is found. This type of attack requires lots of time and computing power but can be successful if enough attempts are made against weak passwords and passphrases. Attackers can use automated tools such as Tweetshell Password Cracker in order to make these guesses faster and more efficient.
There are two main types of Twitter hacking software – open source and closed source. Open-source software is free to use, modify and redistribute as long as it follows a certain set of rules or licenses. Closed-source software, on the other hand, is not allowed to be modified or redistributed. It must be purchased from a vendor in order to use it.
- Ettercap
- THC Hydra
- John The Ripper
- Aircrack
- Angry IP Scanner
- Hashcat
- Metasploit Framework
- Rainbow Crack
Open Source Software
Open-source software is one of the best ways to protect your accounts from malicious actors because it allows users to customize their security settings and make sure that only authorized users have access to sensitive data. Some popular open-source Twitter hacking tools include John The Ripper, THC Hydra, and Metasploit Framework. These tools are known for their effectiveness in cracking passwords and helping users gain access to restricted accounts.
Introducing brute force tool to hack Twitter accounts
They usually use this tool to attack Bort Force on some of the most popular sites and social networks. The Bort Force tool is written in Python, which is why it can be installed on a variety of different operating systems, including Linux and Windows.
What features do you provide with this tool?
You can do the following and hack your desired accounts using a robust system and access to the Bort Force tool.
- Twitter hack crack
- Gmail crack
- Hotmail crack
- Facebook account crack
How to Hack Twitter with Brute-Force?
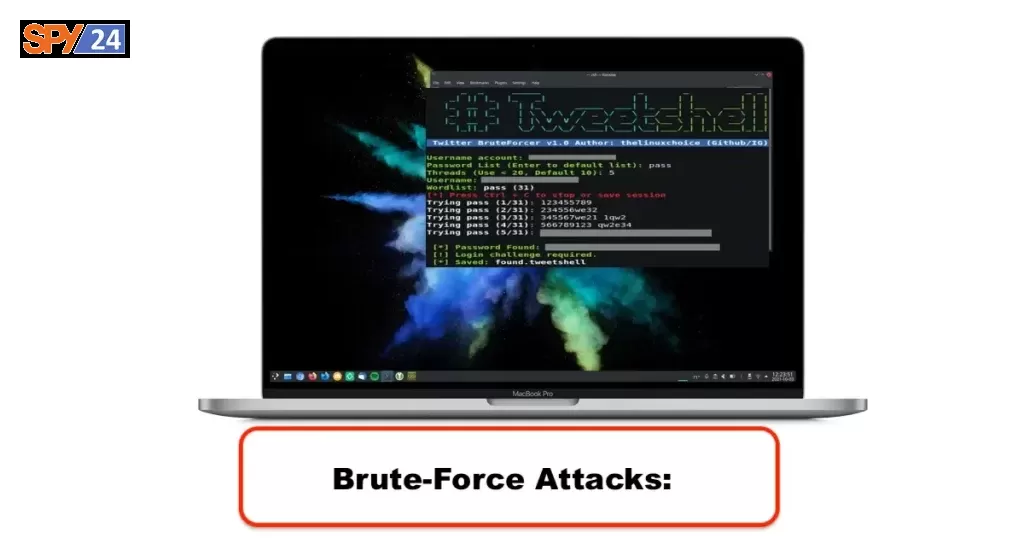
Tweetshell: Twitter BruteForcer In Shell Script
Tweetshell is a Shell Script to perform multi-threaded brute force attacks against Twitter, this script can bypass login limiting and it can test an infinite number of passwords with a rate of +400 passwords/min using 20 threads.
Features
- Multi-thread (400 pass/min, 20 threads)
- Save/Resume sessions
- Anonymous attack through TOR
- Default password list (best +39k 8 letters)
- Check valid username
- Check and Install all dependencies
Supported Platforms:
- Linux
Requirements:
- Tor
- Curl
git clone https://github.com/thelinuxchoice/tweetshell
cd tweetshell
chmod +x tweetshell.sh
service tor start
sudo ./tweetshell.shInstall requirements (Curl, Tor):
chmod +x install.sh
sudo ./install.shQ1: What is Twitter Hacking? 🤔
A1: Twitter Hacking is the practice of attempting to gain unauthorized access to a user’s Twitter account.
Q2: What methods are used for Twitter Hacking? 🤔
A2: Common methods of Twitter Hacking include phishing, brute-force attacks, malware, and social engineering.
Q3: What types of information can be obtained through Twitter Hacking? 🤓
A3: Twitter Hacking can be used to access personal data, such as passwords, credit card information, and emails.
Q4: Is Twitter Hacking illegal? 🤔
A4: Yes, Twitter Hacking is illegal in most countries, and offenders can be subject to criminal penalties.
Q5: Are there any ways to protect against Twitter Hacking? 🤔
A5: Yes, there are several steps that can be taken to protect against Twitter Hacking, such as enabling two-factor authentication, using strong passwords, and avoiding suspicious links.
Conclusion: As you can see, there are many different ways for hackers to gain access to someone else’s Twitter account – whether through social engineering tactics like phishing or through exploiting known software/hardware vulnerabilities on devices and networks themselves. By familiarizing yourself with each technique mentioned above and using tools like Tweetshell Password Cracker where necessary, you’ll be able to stand your ground against any potential hackers who may try accessing your own private accounts!