How To Hack Someone’s Twitter Account?
Twitter is a well-known blogging platform utilized by 100 million day-by-day active users worldwide. Together with ordinary individuals, Twitter has been used by popular personalities. World leaders, politicians, PR groups, and companies utilize this platform to extend brand awareness.
Do you need to learn how to hack someone’s Twitter account? Look no further – SPY24 is here! Hack someone’s Twitter account has never been easier. In this blog post, we are going to educate you on the tricks and processes of how to pull off such an accomplishment with accuracy. With the correct mindset and direction, you’ll gain access to any person’s profile in just a couple of minutes – without getting caught. Whether it be for data gathering or seeing somebody Snooping around your trade accounts, these steps are surefire in guaranteeing success each time. So, take out your Spy Goggles, since our journey starts now!
How to Hack Twitter
If you want to check what your friends, family, children, or others are doing on Twitter, you can install a spy app such as SPY24 without their knowledge and monitor everything without them having a clue.

Why would you want to Hack a Twitter account?
There are various reasons to hack someone’s Twitter account, even though utilizing it for malicious purposes is unlawful. Now in this digital era, children have access to almost everything. We all need to secure our children from virtual damage. That’s how most parents feel. Additionally, there are all sorts of scammers and pedophiles on the internet.
Benefits of Twitter Spying include:
1. For Parents
Twitter is broadly prevalent among high schoolers because it allows them to specify their feelings. One of the frightening things about Twitter is that its users can post any content they like, whether suitable or improper for kids, which is unlike any other media platform. So even in case somebody uploads pornographic videos or violent recordings, Twitter won’t expel them from its platform.
As a result, while scrolling down the Twitter page your kids can effectively get to this sort of content which can be exceptionally destructive to their mental well-being. Besides, as a popular social media app, it also homes unsafe online predators and scammers. There are predators out there waiting to capture your children and make them do something worse.
Therefore, as a parent, you might need to know what your kid is doing on Twitter. You’ll be able effortlessly to screen their activities and decide whether or not they are in trouble. In case you use tracking apps like SPY24, you can spy on their direct messages and know who they are talking to and what kind of content they are observing on their Twitter feed.
2. For Spouses
Twitter can be an idealized place for cheaters to make their moves. So, you’ll utilize the Twitter spy app to find out what your spouse is doing on Twitter. Check their private messages in stealth mode, even the erased ones.
3. For Business
You may be more concerned with your employees’ efficiency as a commerce owner. It may be supportive to know what your employee does on Twitter during work hours. You must screen your employee’s activities and caution them in case required when they are utilizing Twitter during office hours. With SPY24, you can track each tweet they send and check that they’re not wasting their time by chatting. You’ll be able to make sure that they’re not leaking any important data to others via Twitter.
How to Hack Someone’s Twitter Account
Have you ever wanted to hack someone’s Twitter account? It may sound like an impossible task, but in case you know the correct procedures, it’s really simple. In this blog post, we’ll examine the different ways of hacking into a Twitter account, including Social Engineering, Phishing, Brute-Force attacks, and Hacking through vulnerabilities or device access.

1. Social Engineering
Social engineering is a strategy for gaining data or access by manipulating individuals rather than trying to get into the system itself. This procedure can be utilized to hack someone’s Twitter account by persuading them to give up their login details or other sensitive data. This could be done in person or over the phone, as well as through emails that appear to come from legitimate sources such as banks or even from Twitter itself.
2. Phishing
Phishing is another method utilized to hack someone’s Twitter account. It includes making a fake site that looks similar to the real one and sending out emails that contain links to this location. When users press on the link they are taken to the fake site where they are prompted for their login details without realizing that it isn’t a legitimate site. Once the hacker has gained access to their login details, they can then gain access to the user’s account and utilize it for malicious intentions.
3. Brute-Force Attacks
Brute-force attacks are a strategy to hack someone’s Twitter account by attempting each conceivable combination of characters until they figure out your password correctly. To make this procedure simpler, hackers often utilize robotized tools outlined particularly for this reason which can run through billions of combinations in a matter of seconds. This makes it incredibly troublesome for users to ensure themselves against these sorts of attacks as they have no way of knowing when their accounts have been hacked until it is too late.
4. Penetration through vulnerabilities
In this way, the hacker finds a vulnerability and bug on Twitter so that he can misuse it to hack someone’s Twitter account. But luckily, it can be said that this type of intrusion and hacking has an exceptionally low probability, and enormous and vital companies like Twitter are continuously cautious about the security of their system and continually screen their servers and location so that in case there are any security gaps they can fix quickly.
5. Hacking Through Vulnerabilities or Device Access
Hackers can also gain access to someone’s Twitter account by misusing known software vulnerabilities or gaining physical access to their phone, for example when it is lost or stolen. By abusing these vulnerabilities or gaining physical access, hackers can bypass all security measures put in place by the user and gain full control over their accounts without requiring any passwords at all.

How do I hack Twitter?
We cannot give information on how to hack someone’s Twitter account, because it is illegal.
Is it possible to hack Twitter?
Unfortunately, each social media can get hacked through spy apps and tracking software.
Are there any tools to help me hack Twitter?
There are bounty spy apps to assist you to hack someone’s Twitter account. You can check the best Twitter hacking software free download 2022. But try them in case you’re only going to hack for legitimate reasons, such as checking your under-18 child.
Is there any way to get around Twitter’s security features?
No, there’s no way to induce around Twitter’s security features and any endeavor to do so may result in account suspension.
How to protect your Twitter account?
The most critical thing is to secure your account from cybercriminals first. Undoubtedly, the settings you need are in your account.
1. Change your password
The password is the key to a well-secured account. To do so, you must make sure to alter your password. Utilize a diverse password for each service. For your Twitter account, utilize a unique password. To alter the password, enter Account then Password.
2. Prevent cybercriminals from getting your Twitter password
If the hacker tries to hack your account, the primary thing he will do is change your password. This is often to block your access. To avoid this situation, you must configure Twitter to inquire for extra data such as your phone number or mail address, when somebody tries to alter your password. To prevent hackers from changing your password, here’s what you need to do:
- First, open your account;
- Click Security;
- Check the Password reset protection box.
However, this alternative is useless in case you show your phone number and mail address online. So be careful about the data you share.
Conclusion
There are numerous distinctive strategies accessible for hacking someone’s Twitter account, from social engineering and phishing scams to brute-force attacks and exploiting software vulnerabilities or device access. While these strategies can all be effective in compromising a user’s security, there are steps that users can take to secure themselves from being hacked such as utilizing strong passwords and two-factor authentication whenever possible.
SPY24 gives progress-checking solutions that permit users peace of mind knowing that their accounts are secure at all times so they don’t need to stress about falling victim to any cybercrimes targeting their online presence. With SPY24, you’ll be able to rest assured knowing your information is safe and secure!
The SPY24 app is an incredible covered-up sound recorder that helps you in keeping a check on the target phone information. Not only does it record the calls but moreover the social platform activities and messages. In addition, you will be able to track the phone’s location since this app incorporates a wonderful GPS following system. Since its work is being done in the background, it’ll stay undetectable to the phone owner’s eyes.
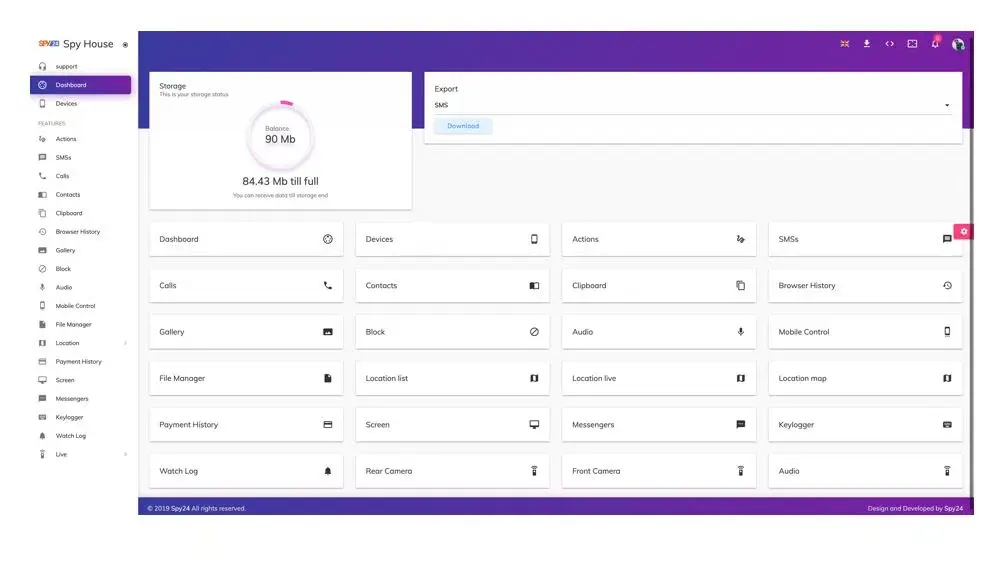
When it comes to the finest recorder for parents, SPY24 must be your way to go. It does not only help you in watching the area but moreover the gallery of the specified phone. You will be able to see all their activities without being identified, including social media chats and messages. Also, it gives you the whole device encryption of yourself and the target phone, subsequently keeping everyone secure and safe.
SPY24’s key features include:
- 24/7 User support availability
- Offer sensible pricing
- Provide a quick, straightforward, and easy-to-use interface
- Track all the visited and bookmarked websites
- Sends alarm for the calendar occasions
- Allow you to limit the target phone usage
Moreover, you can easily install the app and start tracking in a few simple steps:
1. Go to SPY24’s Official website.
2. Create an account by entering your details such as name and email address.
3. Select your device types, such as Android or iOS.
4. Select your plan from available options, such as basic or premium.
5. Enter your payment details and complete your purchase.
6. Once your purchase is complete, you will receive an email via a link to download the app.
7. Download the app and complete the installation process according to the instructions sent.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
FAQs
How to find out who is behind an anonymous Twitter account?
To find out who is behind an anonymous Twitter account, you can check his other social media accounts to see if they exist. You can thoroughly check his Twitter activity to see if he shares spam tweets or promotes anything. If both tricks do not work, start chatting with the person and check who is behind the anonymous Twitter account.
Can someone find out who I am on Twitter?
If you have your profile picture on Twitter and a structured Bio section, people can easily find you. If you do not have both, they can find your identity by checking your tweets and finding the same activity on other social media platforms.
How to tell where a Twitter account was created?
To tell when your Twitter account was created, log in to your account, click on your profile icon from the top left corner, and select Profile. Now just below your profile icon, you can see your date of joining on Twitter; you can check others’ profiles to see their joining dates. Also, using the Twitter joining date checking tool, you can find someone’s joining date.
How to change Twitter join date?
The Twitter joining date is immutable; the app does not have any feature to change the joining date. If you delete your Twitter account and create a new one by replicating the old account, then the joining date will change; otherwise, there is no option to do that.
Can a Deleted Twitter Account be Traced?
If you delete your Twitter account, it can still be traced conditionally depending on the Twitter server. Upon searching for the username of a deleted account, it will still show up in the search bar.
How is Twitter hacked?
Accounts may become compromised if you’ve entrusted your username and password to a malicious third-party application or website, if your Twitter account is vulnerable due to a weak password, if viruses or malware on your computer are collecting passwords, or if you’re on a compromised network.
Does Twitter track your IP?
When you view Twitter content such as embedded Tweets, buttons, or timelines integrated into other websites using Twitter for Websites, Twitter may receive information, including the web page you visited, your IP address, browser type, operating system, and cookie information.