Hacking Email Password Free Software
Have you ever wondered how to hack email? It’s not as difficult as you might think. In this blog post, I will show you how to do it and provide a few tips to help keep your email account safe. Keep reading for more information!
Can Easy V3.3 hack Yahoo email passwords for free? Free Software Hack Yahoo Email Password Easy V3.3 This is the only free and easy way to hack account passwords at home. Hack Yahoo Email Password Easy V3.3 Free Software can hack Facebook and other passwords in minutes, even if you don’t know how. This is the main reason Account Hacker is so popular. Hacking Facebook passwords is easy.
How to Hack a Yahoo Account
In this blog post, we will show you how to hack a Yahoo account. This is a simple process that can be done by anyone with basic computer skills. We will show you step-by-step how to do it so that you can hack into any Yahoo account you want.
Step 1: Go to the Yahoo login page and enter the victim’s email address in the “Username” field.
Step 2: In the “Password” field, enter the victim’s password.
Step 3: Click on the “Sign In” button.
Step 4: Once you are logged in, click on the “Mail” tab at the top of the page.
Step 5: On the left side of the page, under the “Folders” heading, click on the “Inbox” folder.
Step 6: On the right side of the page, under the “Messages” heading, you will see a list of all of the victim’s emails. To read one of these emails, simply click on it.
That’s all there is to it! With just a few simple steps, you can easily hack into any Yahoo account. Just remember to use this information responsibly and only hack into accounts that you have permission to do so. Happy hacking!
Our hacking software is so simple that a 5-year-old can hack Facebook. It is the easiest Facebook hacking tool available. Yahoo Email Password Hack Easy V3.3 Free Software. Our Twitter and Hotmail password-hacking software have been downloaded thousands of times.
Free Yahoo Account Hack
Below are some randomly selected testimonials from people who used our Password hacking software to hack Instagram, Twitter, and other passwords.
Your Facebook hacking software revealed my husband’s password. “Great software.” Chicagoan Samantha James
The SPY24 homepage reads “Can I Hack Yahoo Email Password Easy V3.3 Free Software.”
Hack Facebook Inbox before the price rises!
How to Change Your Yahoo Mail Password
Blog Introduction: In light of the recent Yahoo Mail password hack, it’s more important than ever to make sure your Yahoo account is as secure as possible. The good news is that changing your password is a quick and easy process. Here’s how to do it.
Step 1: Sign in to your Yahoo account.
Step 2: Click on the gear icon in the upper right-hand corner of the page and select “Settings.”
Step 3: Under the “Account Security” heading, click on “Change password.”
Step 4: Enter your new password in the “New password” field and click “Save.”
That’s all there is to it! By following these simple steps, you can change your Yahoo Mail password and help keep your account safe from hackers.
How to Avoid Email Hacking
Email hacking is a serious problem that can have devastating consequences for both individuals and businesses. Although there are no guaranteed ways to prevent email hacking, there are some steps you can take to reduce the risk of your email being hacked.
Use a strong password. A strong password is at least eight characters long and contains a mix of upper and lowercase letters, numbers, and symbols. Avoid using easily guessed words like your name or birthdate.
Don’t use the same password for all of your accounts. If a hacker manages to guess your password, they will have access to all of your accounts. By using different passwords for each account, you can minimize the damage if one of your passwords is compromised.
Enable two-factor authentication. Two-factor authentication adds an extra layer of security by requiring you to enter a code from your phone in addition to your password when logging into your account. This makes it much harder for hackers to gain access to your account even if they know your password.
Keep your software up to date. Outdated software often has security vulnerabilities that can be exploited by hackers. By keeping your software up to date, you can help close these security holes and make it more difficult for hackers to gain access to your system.
Also Read
How to Understand If Your Yahoo Account Has Been Hacked?
Be careful what you click on. Hackers often use malicious links or attachments in emails to infect your computer with malware or steal sensitive information. Avoid clicking on links or opening attachments from unknown senders, and be cautious even with emails from people you know. If an email looks suspicious, it’s better to err on the side of caution and delete it without opening it.

How to prevent email hacking
The first step in preventing email hacking is to take proactive measures to secure your account. This can include using strong passwords that are unique and difficult to guess, as well as enabling any available security features or two-factor authentication options. It’s also important to be vigilant about suspicious emails or attachments, and always update your software when prompted so that you have the latest security patches and updates.
How to know if your email has been hacked
If you suspect that your email account has been hacked, there are a few steps you can take to try to regain control of it. One option is to change your password immediately, either through your email provider or by resetting it directly from the compromised account. You should also report the incident to your email service provider, as they may be able to help you recover your account.
What to do if your email has been hacked
In order to protect your email account from being hacked in the future, it’s important to take steps to stay informed about the latest security threats and best practices. This might involve signing up for security alerts from reputable organizations or following security-focused blogs and websites. Additionally, you should avoid using public Wi-Fi networks whenever possible, and never click on suspicious links or open attachments in unsolicited emails. With these precautions, you can help ensure that your email account remains secure and protected against hackers.
Email hacking is a serious problem that can have devastating consequences, but there are some steps you can take to reduce the risk of your email being hacked. By using a strong password, enabling two-factor authentication, and being careful what you click on, you can help protect yourself from email hacking attempts.
How to Hack an Email Address
Blog Introduction: In this day and age, it’s more important than ever to keep your information safe and secure. With hacking becoming more and more common, it’s important to know how to protect yourself. One of the best ways to protect yourself is by learning how to hack. That way, if someone tries to hack you, you’ll be one step ahead of them. In this blog post, we’ll show you how to hack an email address.
- Go to the website of the email service provider. For example, if the email address is a Gmail address, go to www.gmail.com.
- Enter the email address that you want to hack into the “Username” field on the login page.
- Leave the “Password” field blank and click on the “Login” button.
- If you see a message saying that the email address does not exist, then you know that you’ve successfully hacked into the account!
Hacking can be a useful skill to have in today’s world. By learning how to hack, you can better protect yourself from being hacked. In this blog post, we showed you how to hack into an email account. Try it out for yourself and see how easy it is!

How to hack someone’s email
Hacking an email account can seem like a daunting task, but with the right tools and knowledge, it is actually quite simple. To get started, you will need to collect some basic information about the email account that you want to hack. This might include the username and password for the account or other details such as IP addresses or login locations.
The steps you need to take in order to hack an email account
Once you have gathered this information, you can begin using specialized hacking tools to try and crack into the email account. These tools are designed to perform a variety of different attacks on your target’s account, including dictionary attacks that use lists of common passwords and brute-force attacks that automatically try millions of different combinations until they find a match.
Why you would want to hack an email account
If you are successful in hacking an email account, there are a number of things that you can do with that information. For example, you could use the account to monitor someone’s online activities or communications or even spy on their personal messages and private conversations.
What you can do once you have hacked an email account
To prevent your own email account from being hacked, it is important to take steps to keep your passwords and other login details secure. This might include using strong passwords with a combination of letters, numbers, and symbols and never sharing these credentials with anyone else. Additionally, you should avoid clicking on suspicious links or opening unexpected attachments in emails, as this can put your account at risk of being compromised by hackers.
How to prevent someone from hacking your own email account
Whether you are trying to hack someone else’s email account or protect your own from being hacked, the key is to stay informed and take proactive steps to keep your information safe online. With a little knowledge and determination, you can be successful in hacking almost any email account that you encounter.
TOP 10 to keep from getting hack
Here are 10 easy things you can do to stay safe online. They can also help protect your family and friends and keep hackers from getting into your email:
- Whenever you can, use a password manager and two-factor authentication.
Use a trusted password manager to change all of your online passwords to strong, unique ones for each login. This can’t be said enough. Hackers use a method called “credential stuffing,” in which they use stolen usernames and passwords to sign up for as many online services as they can. Why? Because many usernames and passwords are the same for more than one account.

It can take some time to make a unique password for each online service you use, but it’s worth it to avoid the risk. Set up two-factor authentication (2FA) as an extra layer of security for the accounts that offer it when you set up your passwords. This is especially important to stop people from changing your password without your permission. Do the same thing when you set up IoT devices at home, and look for IoT devices that support two-factor authentication when you buy them!
- Check to see if a new email service supports 2FA before signing up.
Not all email providers provide 2FA. So, when you sign up for an email service, check to see what security layers are available, such as two-factor authentication (2FA), which can be done via SMS (less secure) or an app like Google Authenticator or Authy.
The main benefit of 2FA is that it adds a second layer of security, like sending a one-time password via text message to a smartphone. A new login should only be possible for the person who has your device. It can also let you know when someone tries to log into your email account.
- Don’t click on links in emails or texts that look sketchy.
Phishers often send email or text messages with links that look real, but when you click on them, they steal your information. Malware-filled email attachments are also a common way to cause trouble online. You can avoid these scams most easily by not clicking on the links or attachments.
Instead, open a new tab and go to the company’s website through the link or email to see if the information matches the official source. As a general rule, you should never click on links or download files from people you don’t know. The bad news is also emails from people you know that have links or attachments with no context.
This will also help you catch one of the most common types of phishing emails: the fake password reset (for example, “Your account has been compromised! To change your login and password, click here.”) Do you remember when emails from the 2016 Democratic National Convention got out? It started with a fake request to reset the password.
- Use a VPN on your phone and computer
Use a VPN to encrypt your internet connections and keep your identity secret. If you want to keep your personal information safe, there’s no reason not to. While you’re at it, the VPN will make your browsing experience even better, with fewer ads, less tracking, and, of course, more peace of mind knowing you’re safe.
- If you can help it, don’t use public Wi-Fi or public computers.
When you’re not at home or traveling, try to only use the internet on your own computer or phone, with your VPN turned on, of course. People can put keyloggers or other harmful software on public computers, like those in hotels, which can come back to hurt you. If you can wait until you’re on your safe home network to do online banking or access other highly personal accounts.
- Get a good antivirus program.
When it comes to keeping your information safe, a good antivirus raises the bar by protecting you in real time from phishing attacks and other threats like malware, ransomware, and more. Your PC, Mac, Android phone, and other devices should all have antivirus software installed.
- Protect your Wi-Fi and router.
Whether you are a home user or the owner of a small business, it is more important than ever to know who and what is on your network. Unauthorized users could be trying to hack into your system. Make sure you change your router’s admin password and set your Wi-Fi password to something a hacker couldn’t figure out.
- Keep the OS on your computer and phone up to date.
When a security update for your operating system comes out, you should update it right away. This is an important part of information security.
Keep all of the programs on your computer and phone up-to-date.
Updates usually improve security, so if one is available, you should get it right away.
- Think about putting a freeze on your credit.
If your email has been hacked, you can put a credit freeze on your account as a last resort. It’s easy to do and gives you more control over who can use your accounts. If someone needs to look at your credit report when you buy something (like a car), you can easily turn the account back on and then turn the freeze back on afterward.
Even if you have taken steps to protect your email, you should assume it is not safe. What does this mean? Simply, you shouldn’t send sensitive information like payment or credit card information, Social Security numbers, and other information that could be used to find out who you are, if at all possible, through email.
If hackers get into your email, they can find ways to find this information, but don’t make it easy for them. Two-factor authentication (2FA) and good old-fashioned vigilance should be enough to alert you to suspicious activity so you can take steps to fix it right away.
Follow the easy tips above to avoid becoming a target. Taking these few extra steps won’t stop spam from getting into your inbox, but it will help keep hacking attempts out of your inbox.
How to Read Email Without Password?
How to read others’ emails without a password? Spy apps keyloggers let you read others’ emails.
Have you asked, “How can someone read your email without the password?” This blog discusses reading emails without passwords. Discover.
Many people ask if someone can access their emails without their knowledge. Even people want to read emails without a password.
Why are your emails read without a password?
Smartphones and computers now dominate our daily lives. Some people obsess over others. They may read emails and texts to get personal information. Reading emails may be beneficial.
Parental controls allow parents to monitor their children’s email behavior. Reading your loved one’s mail is positive.
As internet crimes rise, you may need to defend your family. Spy and monitoring software allows company owners to check employee emails for performance and activity.
Is reading an email without a password illegal?
Reading an adult’s emails or texts without permission is illegal. Tell the target about the phone’s keylogger or monitoring software. Otherwise, you may violate privacy.
Because their phones, tablets, and laptops are yours, you can legally check your kids’ and employees’ email and text messages without a password using parental control or company-owned devices. Only in this case can you read someone’s email without their consent.
ways to read email without a password
As mentioned in this blog, monitoring someone’s email could be for child supervision, employee monitoring, or other reasons. Three methods work.
Three ways to read an email without them knowing are:
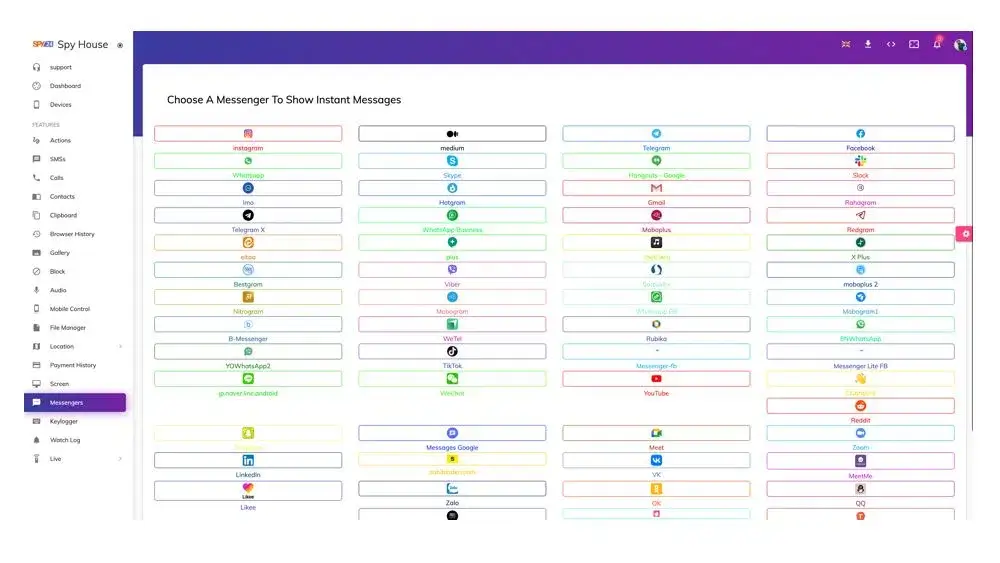
Email spying with apps
Today, children, spouses, and employees don’t want to share personal information with loved ones. To access others’ emails, people use spy apps or email tracking software like Hubspot, Yesware, Streak, Mobistealth, SPY24, mSpy app, and others.
Email tracking software allows access to a target’s email without passwords or notifications. It could monitor Android and iPhones. After installing the software on their phone, you may not need it.
Spying on others’ mail for legitimate reasons may not be illegal. Notify employees that you will be using email tracking systems to monitor their emails so they can focus on their work.
After monitoring, you may not want to tell your kids or partner about the spy app. We suggest secretly monitoring their emails.
SPY24, the best email spying software without passwords, has many great features. Sign up for SPY24 to secretly monitor your target’s emails.
Want to know how to get into someone’s email?
If you are a parent, you might want to keep an eye on who your kids are emailing. You might also want to check the email of your partner.
The hard part is figuring out how to get into these email accounts. It looks like a very complicated process, but it’s not that hard. You just need the right apps or software to spy on someone.
In this article, you’ll learn about the different ways you can easily and quickly hack into someone’s email account. Don’t move and keep reading.
How to Use Software to Hack an Email Account?
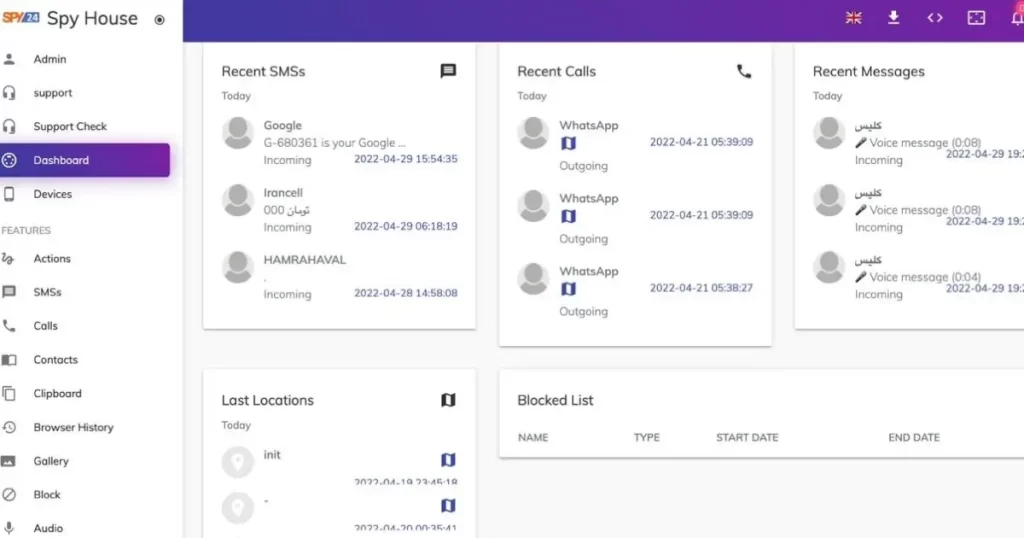
SPY24 is one of the best apps for hacking email. You can hack into someone’s email account and listen in on their conversations with it. This way, you can make sure that your kids or employees don’t give out personal information to strangers or people who want to hurt them.
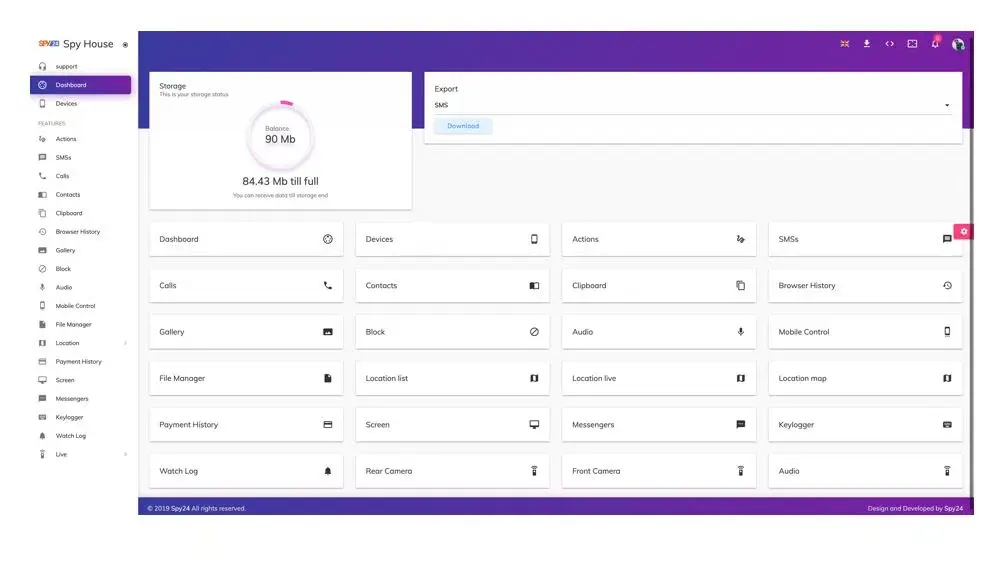
With SPY24 email hacking, you can quickly and easily look at all the information gathered from email monitoring from your SPY24 online control panel. The app has a lot of useful features in addition to being able to track email. Even if you deleted some emails, SPY24 lets you get them back so you can read them. You can also look at any audio, images, or videos that were shared in the conversations. It also lets you record what you type on the keyboard. With this feature, you can find out what your target has been sending to other people. You can get information like passwords and other login information from the keystroke feature.
Website monitoring and blocking is another important part of SPY24. Especially for kids, the Internet is a dangerous place. With this feature, parents can keep an eye on the websites their children go to. They can choose to stop their kids from going to websites that are dangerous or not good for them. With the “View Call Log” feature, you can also keep track of their calls. You can listen in on their phone calls and find out who called, how long the call went on for, and when it ended, among other things.
If you’re a worried parent who wants more information than what’s in the email, you can use the GPS tracking feature. Since kids are often glued to their phones, using SPY24 is one way to find out exactly where your child is. In this way, the app does a few things. It keeps track of your GPS location and shows it to you on a map. Every few minutes, it sends you an update.
How to Use SPY24 to Hack Email
Buy the SPY24 app and install it.
Enter the activation key you get when you set up the program.
Sign in to your online portal and use the dashboard to turn on email spying.
Click “Email” on the menu to download the emails that have been saved.
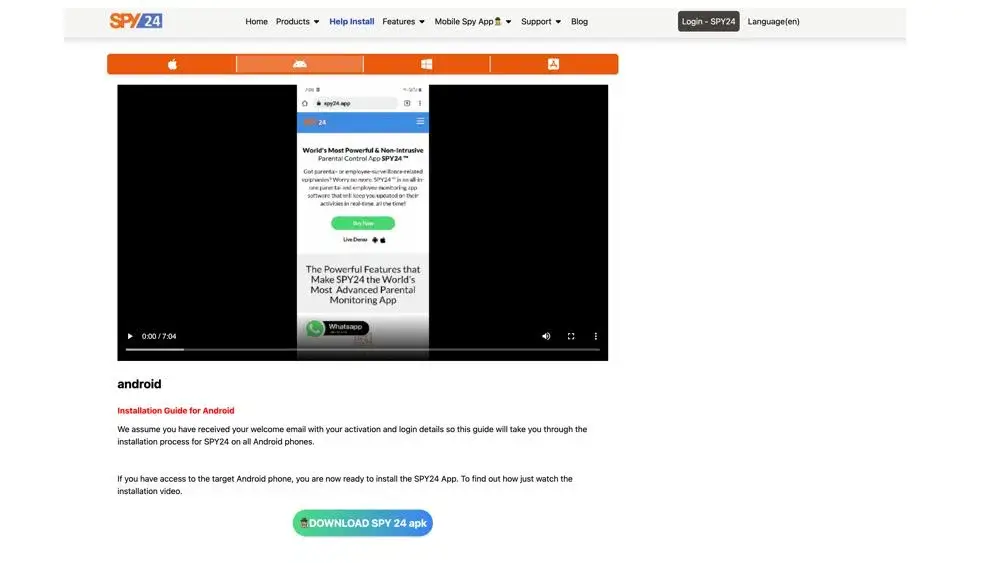
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
Phishing email hack
Scammers use complex email hacking techniques like phishing to steal personal data. Hackers can steal your email login credentials and use them to steal your inbox data.
Attackers send Google or Microsoft-looking emails. Scam emails contain links to fake login sites. Entering your login details allows scammers to steal them.
Phishing is illegal in most countries because it allows people to read and spy on others’ emails.
Keylogging someone’s mail
Parents often use keylogging to monitor their kids‘ internet use. Keyloggers record all keystrokes on target devices.
This software records employee and user emails in the background without their consent. Thus, you could read your child, employee, and user emails.
Installing a keylogger on a device is enough. Avoid free keyloggers and use trusted software.
How to prevent email reading?
Here are some email security tips.
- Multi-factor authentication with multiple security questions.
- Sign out of all other email devices.
- Email on your own devices.
- Avoid public WiFi for confidential data.
- Email access requires a VPN.
- Clear browser cookies regularly.
- Remove keyloggers with reliable antivirus software.
Work with Gmail? If so, check out these productivity-boosting Gmail add-ons.
Leaks:
Data breaches may have compromised your email account. Hackers can access all your accounts if you use the same password. Hackers buy dark web passwords from cybercriminals after data breaches.
Not logging out:
If you check your email on a public PC and don’t log out, someone else can steal your password and hack your account. Always log out of public computers. Beware of malware and spyware on public PCs.
Unsecured public Wi-Fi:
Coffee shop and airport Wi-Fi is often unsecured. Hackers can easily spy on traffic, including email. Avoid this by using trusted, password-protected networks. VPNs secure and encrypt your connection.
Simple passwords:
Hackers can guess weak or obvious passwords. Strong passwords have at least 12 characters and include upper- and lowercase letters, characters, and numbers. Password managers help manage multiple passwords.
An updated antivirus software:
Protecting your devices from password-stealing malware requires a good antivirus and regular updates. Downloaded or attached malware can infect your computer.
Is my email hacked?
Signs of email hacking include:
- Password not working.
Email inaccessibility is a sign of a hack. If your usual email password doesn’t work, someone may have changed it. Hackers change your email password to keep you from logging in.
- You have unknown emails.
Hackers don’t always change your password, so you can still access your email. You may find unsent messages in your sent folder. Hackers may be trying to change your password on other sites by sending you password reset emails from websites you didn’t request. Unrecognizable messages indicate a hacker has access to your account.
- Friends say you send strange or spam messages.
If your contacts report receiving spam from your email address, your data may have been hacked.
Log IP addresses vary.
Some email providers have a tool that records your IP address every time you log in. Gmail’s right-hand corner says “Details” if you scroll down. This shows your account’s IP addresses. If you only log in from home or work, the IP address will show these addresses. Different IP addresses indicate unauthorized email access.
How can hackers use your email?
If your email is hacked, you may wonder, “Can someone hack my bank account with my email address?”
Hackers want your email because it contains valuable information. Email hackers can use your contact list for phishing and other fraud. They will also know which financial and banking websites you use from your emails. They can reset passwords, access credit information, and delete accounts using your email. They can use the information to steal money or sell personal data on the dark web.
Our email addresses are often the main login identifier. Hackers can use your email address to access your online accounts.

Email hacking: what to do
What to do if a scammer hacks your email account? Take these precautions:
- Run antivirus.
If your email account is hacked, the FTC recommends running a full antivirus scan. Avoid the “quick scan” setting and use a deep scan to find and remove all malware (including Trojans, spyware, and keyloggers that may still be tracking your keystrokes after the hack) and potentially unwanted applications.
Hackers want to steal money or commit credit card fraud, not embarrass their friends. Hackers target businesses that wire funds frequently. A compromised email account can send unauthorized transfers. BEC cost $2.4 billion in 2021, up from $1.8 billion in 2020, according to the FBI’s Internet Crime Center.
Run an antivirus scan ASAP. To avoid restarting the cycle, clean your system before changing sensitive information.
- Change passwords.
Password change after malware removal. You may need to contact your email provider to prove your identity and reset your password if you’ve lost access.
Choose a unique password without repeated characters or numbers. Avoid passwords with your name, birthday, or other personal information. Hackers use this information to brute force your account.
Each account should have a unique, complex password with at least 12 characters (ideally more). Use a password manager to create and store complex passwords.
Email password change:
Gmail
- My account.google.com
- Sign into Google under Sign-in & security.
- Click Password & sign-in method.
- Sign into Google.
- Re-enter a new password and click. Change password
Outlook/Hotmail
- Access Hotmail at outlook.com.
- Click your name at the top right.
- View Profile.
- Click Email password change
- Microsoft verifies your password change request: enter your email and click Send code
- Enter the code from your inbox and click Submit.
- Enter your current and new passwords
- (at least eight characters and case-sensitive), then re-enter them.
Save Yahoo Mail
- Yahoo Mail login: login.yahoo.com
- Click your name at the top right.
- Account Info
- Account Security tab
- Change password
- Enter a new password, confirm it twice, and click Continue.
- Contact other online services
Changing passwords for other online accounts is crucial. Amazon, Netflix, credit card companies, and libraries need resets. Update your passwords to prevent hackers from accessing other accounts.
Secondary accounts are more valuable targets in these security breaches, so secure them. If the scammer found your password, your bank account could be next.
Use different passwords for each site. Using the same password for multiple sites increases the risk of subsequent breaches. Avoid streamlined email or social media logins to reduce risk. If your email account links to online vendors, even multiple passwords may not be enough.
- Tell others
Protect your contacts too. Tell your friends, family, and coworkers you’ve been hacked.
Attackers could have sent dozens or hundreds of malware-laden emails to everyone you know while they controlled your account. This phishing attack gives them new victims.
Notify other platforms’ contact lists. Attackers may bait contacts via email. They could send fake messages from your social media and messaging apps. Notifying contacts lets them clean and protect their devices.
- Change security questions
Hackers may have hacked your account by answering your security questions.
False security questions can prevent hackers from breaking in again. Keep them private but memorable. Google found that many users answer security questions the same way. Nearly 20% of Americans answered “pizza” to “What is your favorite food?”
Multi-factor authentication protects logins and password resets. This authentication secures email with secondary email addresses or text messages.
- Report the hack
Report the hack to your email provider if you haven’t. Even if your hacked email didn’t prevent access, this is crucial. Hacks help providers track scams. Reporting a hack helps the provider improve security, protecting you and others.
Your email provider may also know the attack’s origin. The breach may affect more services.
- Create an email account.
Restarting can be easier. Is this email hacked? Is your provider not reducing spam? Change may be needed.
Look for email encryption by default. Data encryption protects private emails from provider breaches. Hackers need a security key to access this data.
Email change:
Changing email addresses is difficult. Most email services don’t let you change your email address, so you have to create a new account and migrate your data. Forwarding and notifying people can simplify the process. Some services let you import old emails. Keep your old account active after making a new one. Use it for a while to avoid missing important messages and getting locked out of your online accounts.
- Contact creditors
Hackers’ reach extends beyond email hacks. Ask credit reporting agencies to monitor your accounts in the months after being hacked.
Note any suspicious-named emails you’ve received recently. Before defrauding your accounts and using your credit card, fraudsters are more likely to contact you and get your personal information. Scammers know that personalization often bypasses spam filters.
- Consider ID protection.
After being hacked, consider ID protection. These services monitor email and retail accounts in real-time. They also report credit scores and provide identity theft assistance.
Since this protection is expensive, look for reputable companies. Use a legitimate service, not a hacker scam to steal your data.
Use account monitoring and cyber security software. Expanded internet security suites monitor online accounts for data breaches. They’ll help you after a leak or hack.
- Securely
Scan your phone, tablet, and laptop for viruses. Protect your personal data in the cloud. Change your passwords, notify your providers, and scan your cloud data and backups for viruses. These steps can reassure you.
If you haven’t, upgrade your basic antivirus to full-time internet security. Find a service that prevents unknown threats and protects your online activity.
Fixing hacked emails makes self-defense easier. If your email is hacked, follow these steps to regain control and avoid future issues.
- Conclusion
Even without your password, someone may be reading your emails. Every email access should be cautious. Since sensitive career or personal information is there.
Reading emails without permission may violate privacy rights. Be mindful of privacy when making requests. However, parents or business owners can legally access children’s and employees’ emails without their knowledge.