13 Popular Wireless Hacking Tools [Updated 2023]
![13 Popular Wireless Hacking Tools [Updated 2023]](https://spy24.pro/security/wp-content/uploads/2023/02/popular-wireless-hacking-tools3.webp)
The use of the Internet is now an integral part of our daily lives, whether we are at work or at home. This has led to the fact that Wi-Fi routers and data connections have become a fundamental amenity for every user as a result.
In order to connect all devices in your home network, you can also use a wireless router. The downside of using Wi-Fi is that it could make your network visible to your neighbors, who may be interested in using it for free if they want.
As well as that, big companies that use Wi-Fi may also want to keep a close eye on how their employees are using the network to ensure that it is not misused.
In spite of the fact that wireless networks are secured with passwords, there are many Wifi hacking tools available on the market today that can be used to crack the passwords of any Wi-Fi network that has WAP, WAP2, and WPS protocols enabled.
The purpose of this article is to provide you with a list of the best Wi-Fi app hacker tools that can be used to break into networks and gain access.
What are Wireless networks and hacking?
Wireless networks are computer networks that use wireless data connections to connect devices, such as laptops, smartphones, and tablets. Wireless networks are often used to provide Internet access to these devices and to share other types of data and resources.
Hacking refers to the unauthorized access or manipulation of computer systems or networks. When it comes to wireless networks, hacking can refer to a variety of malicious activities, including breaking into a wireless network to steal sensitive information, disrupting the operation of the network, or spreading malware.

Wireless networks can be vulnerable to hacking due to several factors, including weak security protocols, poor passwords, and unpatched software vulnerabilities. As a result, it’s important to take steps to secure wireless networks and protect them from unauthorized access and malicious activity. This can include using strong encryption methods, choosing strong passwords, and regularly updating software and security systems.
Overall, in today’s interconnected world, wireless networks, and hacking are important topics that need to be addressed, and it is of utmost importance that people are aware of the potential risks and are taking precautions to avoid them in the future.
Top tools for Wi-Fi hacking
- Aircrack-ng: A popular suite of tools for wireless network security assessment and cracking.
- Wireshark: A network protocol analyzer for capturing and analyzing network traffic.
- Reaver: A tool for cracking WPA/WPA2-PSK security on wireless networks.
- Cain & Abel: A password recovery tool for Windows that can also be used for wireless network security assessments.
- Metasploit: A comprehensive platform for penetration testing, which includes tools for wireless network security assessments.
- Nmap: A network mapping and security assessment tool that can also be used for wireless network security assessments.
- Kismet: A wireless network detection and analysis tool that can be used for wireless network security assessments.
- Fern WiFi Cracker: A wireless security assessment tool that can be used for cracking WEP, WPA, and WPA2 security.
- Wifite: A tool for automating wireless network security assessments and cracking.
- John the Ripper: A password-cracking tool that can be used for wireless network security assessments.
- WPA Supplicant: A tool for connecting to wireless networks securely and for testing the security of wireless networks.
- Ghost Phisher: A tool for creating fake wireless access points for ethical hacking and security assessments.
- AirSnort: A tool for cracking WEP security on wireless networks.
It’s important to note that using these tools for illegal or unauthorized purposes is illegal and unethical, and can result in serious consequences. These tools should only be used in a controlled and ethical manner, with proper permissions, and for educational or security testing purposes.
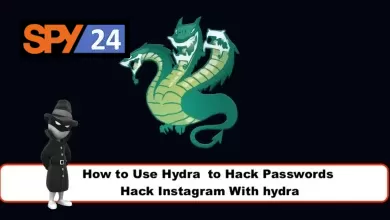
Aircrack-ng
Aircrack-ng is a popular suite of tools for wireless network security assessment and cracking. It’s widely used by security professionals and researchers for testing the security of wireless networks, finding vulnerabilities, and protecting against malicious attacks.
Aircrack-ng provides a number of tools for capturing and analyzing wireless network traffic, cracking encryption methods used in wireless networks (such as WEP and WPA/WPA2), and detecting security weaknesses in wireless networks. The suite is available for multiple operating systems, including Windows, macOS, and Linux, and is free and open-source software.
Wifite
Wifite is a tool for automating wireless network security assessments and cracking. It’s designed to be easy to use and to automate many common wireless security assessments and cracking tasks, such as scanning for wireless access points, cracking encryption methods used in wireless networks (such as WEP and WPA/WPA2), and detecting security weaknesses in wireless networks.
Wifite supports multiple operating systems, including Windows, macOS, and Linux, and is free and open-source software. The tool is popular among security professionals, researchers, and hobbyists, and is often used for testing the security of personal and corporate wireless networks.
Kismet
Kismet is a wireless network detector, sniffer, and intrusion detection system. It’s designed to be used for wireless network security assessments and to detect and prevent unauthorized access to wireless networks.

Kismet can detect and analyze wireless network traffic, and provide information about wireless access points and clients, including network names (SSID), network addresses (BSSID), encryption methods used, and other details. Kismet can also be used to detect and prevent unauthorized access to wireless networks and can alert security professionals when unusual or malicious network activity is detected.
Kismet is free and open-source software and is available for multiple operating systems, including Windows, macOS, and Linux. The tool is widely used by security professionals, researchers, and hobbyists for wireless network security assessments and to protect against malicious attacks.
Wifiphisher
Wifiphisher is a wireless security tool that performs automated phishing attacks against wireless networks. The tool automates the process of creating a fake access point that is designed to mimic a legitimate wireless network and tricking users into connecting to the fake access point and entering sensitive information.

Wifiphisher is often used by security professionals to test the security of wireless networks and to educate users about the risks of connecting to unknown wireless networks. The tool can be used to demonstrate how easily sensitive information can be obtained through phishing attacks, and to raise awareness about the importance of verifying the identity of wireless networks before connecting to them.
inSSIDer
inSSIDer is a wireless network scanner and network optimization tool. It’s designed to provide detailed information about wireless networks, including network names (SSID), network addresses (BSSID), channel utilization, signal strength, and security information.
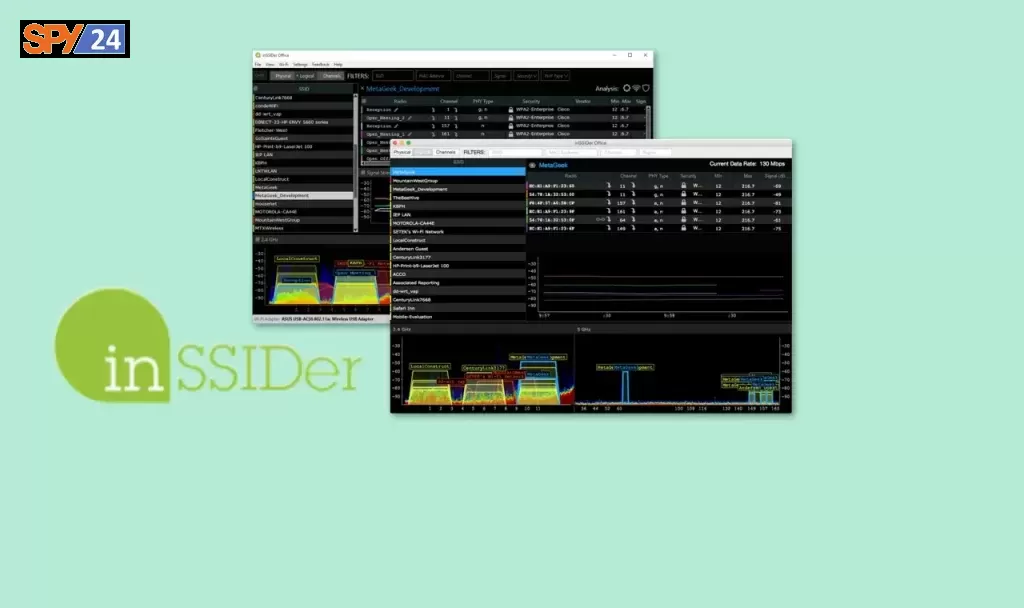
inSSIDer can be used to quickly scan for wireless networks, and to optimize wireless network performance by selecting the best channel for a wireless network based on the surrounding wireless environment. The tool also provides real-time analysis of wireless networks and can help users identify sources of interference, such as other wireless networks or electronic devices, that may be affecting network performance.
inSSIDer is available for Windows and macOS and is commercial software. The tool is widely used by network administrators, IT professionals, and hobbyists for optimizing and troubleshooting wireless networks.
Wireshark
Wireshark is a network protocol analyzer and network traffic monitoring tool. It provides a detailed view of network traffic, including the source and destination of each packet, the protocols being used, and the contents of each packet.
Wireshark is used to analyze and troubleshoot network performance issues, identify security threats, and develop and test network applications. The tool supports a wide range of protocols, including Ethernet, IP, TCP, UDP, and many others, and can be used to analyze network traffic on multiple platforms, including Windows, macOS, and Linux.

In addition to being free and open-source software, Wireshark is also an excellent tool for network administrators, IT professionals, security professionals, and researchers. Also, this tool is gaining popularity among hobbyists as a tool that can be used for learning about networking and for developing and testing network applications.
CoWPAtty
CoWPAtty is a brute-force password-cracking tool for WPA/WPA2 wireless networks. The tool uses a dictionary or wordlist to try multiple passwords until the correct one is found, allowing an attacker to gain access to a wireless network.
CoWPAtty is used for penetration testing and security assessments, to demonstrate the vulnerability of wireless networks to brute-force attacks. However, it’s important to note that using CoWPAtty for unauthorized or illegal purposes, such as cracking into someone else’s wireless network, is illegal and unethical.
CoWPAtty is available as part of the Kali Linux distribution and is a command-line tool. It is not recommended for inexperienced users as it requires knowledge of wireless network security and a good understanding of how to use command-line tools.
AirJack
In order to conduct wireless penetration tests and security assessments, the AirJack tool was developed specifically for use in wireless network attack situations. This tool can be used for injecting packets into a wireless network, interfering with network communication, and capturing data from a wireless network in order to attack a wireless network.

AirJack is capable of performing various types of attacks, including de-authentication attacks, which can disrupt network communication by disconnecting devices from a wireless network, and man-in-the-middle attacks, which can intercept and modify network data.
AirJack is not recommended for inexperienced users, as it requires a good understanding of wireless networking and the use of command-line tools. Additionally, using AirJack for illegal or unauthorized purposes is illegal and unethical.
Airgeddon
Airgeddon is a wireless network security auditing tool that can be used to perform various types of attacks on wireless networks. The tool is designed for use in penetration testing and security assessments, to demonstrate the vulnerability of wireless networks to attack.
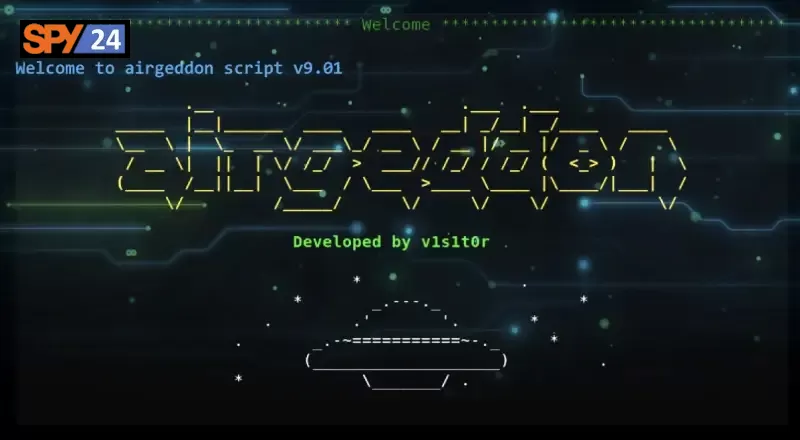
Airgeddon can perform various types of attacks, including de-authentication attacks, which can disconnect devices from a wireless network, man-in-the-middle attacks, which can intercept and modify network data, and WPA/WPA2 password cracking attacks, which can attempt to guess the password for a wireless network.
It is not recommended that inexperienced users attempt to use Airgeddon as it is a command-line tool. It is illegal and unethical to use Airgeddon for illegal or unauthorized purposes in any way.
OmniPeek
In order to monitor, analyze, and troubleshoot network traffic, OmniPeek is a network analyzer and protocol analyzer software tool that can be used. Using this tool, you will be able to capture, decode, and display data from wired and wireless networks, as well as provide detailed information about the performance and security of the network.

OmniPeek is a professional-grade tool that is used by network administrators, security professionals, and other IT experts to optimize network performance, identify security threats, and diagnose network problems. The tool provides a wealth of features, including real-time network analysis, packet decoding, packet capturing, and network visualization.
OmniPeek is a commercial software tool that requires a license to use. It is not recommended for inexperienced users, as it requires a good understanding of networking and the use of specialized software tools.
For those looking for a solution to monitor their networks and detect potential security threats, OmniPeek can be a useful tool.
CommView for WiFi
CommView for WiFi is a wireless network monitoring and analysis software tool that can be used to capture, analyze, and monitor wireless network traffic. The tool provides a graphical interface for viewing and analyzing network traffic and allows users to monitor network performance, detect security threats, and diagnose network problems.

CommView for WiFi supports a wide range of wireless network adapters and can capture and display data from 802.11 a/b/g/n/ac wireless networks. The tool provides detailed information about network activity, including data rates, signal strength, and channel utilization.
The CommView for WiFi tool is a commercial piece of software that requires a license in order to use it. There is a need for specialized software tools and a good understanding of networking, so this software is not recommended for inexperienced users.
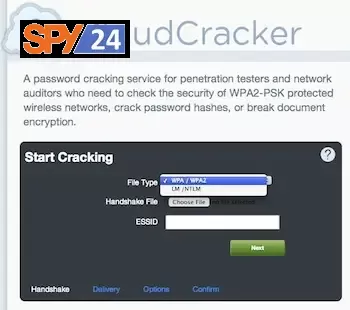
CloudCracker
CloudCracker is a cloud-based password-cracking tool that can be used to recover forgotten or lost passwords for a variety of online services, including wireless networks. The tool uses a brute-force attack method, which involves trying every possible combination of characters until the correct password is found.
CloudCracker operates on a cloud-based infrastructure, which allows users to run large-scale password-cracking jobs without the need for expensive hardware or software. The tool supports a wide range of encryption algorithms and can crack passwords for various wireless network security protocols, such as WEP, WPA, and WPA2.

While CloudCracker can be a useful tool for those who have forgotten their passwords, it is important to note that using it to crack passwords without proper authorization is illegal and unethical. Additionally, using such tools can put both the user and the network at risk, as they can leave the network open to further attacks.
In conclusion, it is recommended that users take all necessary precautions to protect their online accounts and networks, and only use tools like CloudCracker in a responsible and ethical manner.
Kali Linux NetHunter
There is an open-source penetration testing and security auditing platform called Kali Linux NetHunter which is suitable for Android devices.
Powered by Kali Linux, it provides a range of tools for penetration testing, digital forensics, and wireless network security assessments, which are all based on the Kali Linux distribution.

NetHunter supports a variety of Android devices and is designed to work on both rooted and unrooted devices. It provides a customized Android ROM that includes a custom Linux kernel, a variety of hacking tools, and an interface for managing and installing additional tools from the NetHunter store.
Final Thoughts on Best Wi-Fi App Hacker
All of the apps listed above are very good and are able to handle a variety of situations in a variety of ways, so make sure to pick the one that best suits your needs and preferences.
For those in the security industry or for ethical hacking purposes, there are a variety of Wi-Fi hacking tools available that can be used.
Some of the most popular include Aircrack-ng, Wifite, Kismet, Wifiphisher, inSSIDer, Wireshark, CoWPAtty, AirJack, Airgeddon, OmniPeek, CommView for WiFi, and CloudCracker.
It is possible to use these tools to test the security of wireless networks and identify vulnerabilities that could be exploited by malicious actors in order to identify these vulnerabilities.
We would appreciate it if you’d let us know in the comments section if you liked this post and tell us which of the best wi-fi app hacker you’ve ever used.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.