How to Hack Apple ID? San Someone Hack Apple ID
Do you want to unlock the secrets of your Apple ID? Take control of your digital life by unlocking its secrets and unlocking restricting areas of content! You might not realize it but with a few simple steps, you could quickly break through any locked doors that have been keeping you from accessing certain areas or content. By following our comprehensive guide on how to hack an AppleID, you’ll discover all the methods for gaining access to previously untouchable files and services – no matter where in the world they’re located.
What to do if Apple ID is Hacked
Apple ID is also known as a kind of iCloud account that is less secure in comparison with Apple itself. It is more in danger of being hacked. Apple ID is very valuable for you because you need it when you want to have access to payments, streaming, music, etc. on your iPhone. If your Apple ID is hacked, you will encounter many problems. Because a hacker can get all of your information and will abuse you very easily. When your Apple ID has been hacked, a hacker will be able to change your password, lock your iPhone from a distance or even buy something with it. When you think that your Apple ID has been hacked, you should act immediately. Here, you will understand how your Apple ID can be hacked.
You might know something about jailbreak from the recent descriptions and hacking models. One kind of hacking is jailbreaking which is able to install custom firmware on gadgets. Malware attacks are another model of hacking iPhones that unfortunately do not have any resistance. You can find this malware in the App Store applications. We should also point to recognizing security holes that are in the Safari browser. The hackers can install spyware by utilizing these holes. In this step, Apple’s security measures will be reduced and the hackers can have access to users’ information easily. There is some software that is created by skillful hackers and is used for hacking Apple ID.
Which software helps parents to control their children in cyberspace?
One of the best software which is created is the plc spy hacking program which by using it, parents can control the activities that their children do in cyberspace. Parents can have more control of their children’s activities in cyberspace by hacking Android or iPhones. By using this program, parents can hack whole sections of their child’s phone in various versions and utilize different methods of hacking. This program does not let you hack any application or software exclusively. It lets you penetrate the phone and have access to its different sections to control the activities which your children do in messengers and social networks.
What are the applications which are used for hacking iPhones?
Another application that is used for hacking Apple ID is Spy24. By using this application, you can control calls and SMS by showing their date and time. You can also monitor the messages which are received or sent on Telegram, Instagram, WhatsApp, etc. You can check the websites which were visited and also the programs which were performed. You can hide this program and manage the phone at a distance. You can block websites, apps, and distant contacts.
Someone who is close to you can hack your Apple ID. The hacker of your Apple ID is someone who has access to your phone and is able to get hold of the information about your Apple account. There are many ways to hack Apple ID. There are hacking groups that are online that will abuse security holes. Then they will sell availability to these accounts on the places of Dark Web market. There are Phishing and Vishing attacks where a wicked party demonstrates themselves as Apple and then demands your details through email or online forms.
You should be worried about a Phishing attack because not only it will focus on Apple, but also it targets users with all of their accounts online. But fortunately, Apple could take action which is lawful against the hackers who try to retrieve passwords and iCloud Ids. Your ID can be hacked via another device that you possess. Your ID can be utilized on devices such as your iPhone, iPad, or MAC. If any of these devices get hacked or robbed, others can obtain your account details. But do not be worried. Because there are some ways that help you to keep your ID safe and secured.
What can a hacker do with your Apple ID?
If your Apple ID has been hacked, the hacker can do anything with it. For example, your personal information and contacts can be accessible to a hacker. A hacker can read your emails and notes and also can send emails without you knowing. A hacker can have access to all of your photos, videos, etc. He/she can also have access to all of the files that you have saved on the iCloud drive. Also, all of your calendar entries and appointments can be accessible to a hacker.
If your Apple ID has been hacked, a hacker will be able to restore the iCloud backup of your phone to any device which he/she wants. If the “Find My” is enabled on your iPhone, a hacker can find your real-time location. Try not to link your credit card to your account because in this case, a hacker will be able to make purchases from the iTunes Store, App Store, or Apple Books. A hacker can also delete all of your personal data which is saved on your iPhone from a distance. He/she can erase all of your contacts, messages, photos, videos, etc. The hackers are able to utilize your Apple ID and blackmail you.
If someone has obtained your account credentials, you should not utilize iCloud backups. Because in this case, you will encounter a serious problem. By utilizing iCloud Hacking, they can be informed about everything that you do on your iPhone. They will even be able to track your location. There are some signs which show you that your Apple ID has been hacked. One of these signs is the excessive utilization of the internet even when you are not utilizing your phone. When you see that the battery of your phone discharges faster than before.
How to Protect Your Apple ID from Hackers
Apple IDs are an integral part of our digital lives, and we rely on them for everything from activating our devices to making purchases in the App Store. Unfortunately, there is a risk associated with using an Apple ID, and that is the risk of being hacked. With hackers becoming more sophisticated every day, it’s important to understand how to protect your Apple ID from malicious activities.
How to Hack Apple ID on iPhone DNS Server
DNS Method to Crack Apple ID and Password:
The DNS method is the standard for breaking Apple ID passwords on iOS devices. However, you’ll get the best results from this approach on an iPhone that’s running iOS 5.1 or earlier.
Instructions for gaining access to an Apple ID via DNS are as follows:
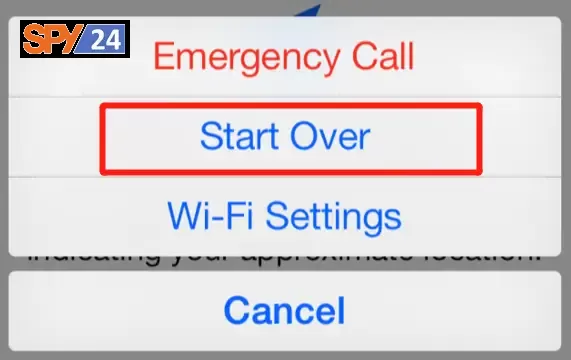
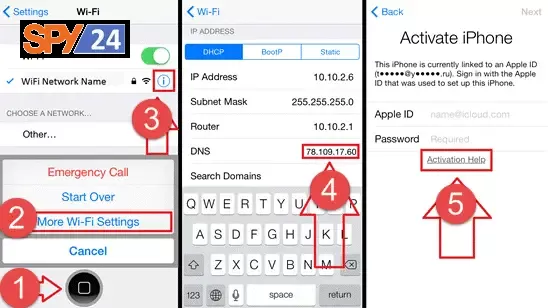
- From the Activation screen, press the Home button and choose Wi-Fi Settings. Tap the I icon
- Select the DNS server based on your location.
- Europe: 104.155.28.90
- USA & North America: 104.154.51.7
- Asia: 104.155.220.58
- Other areas: 78.109.17.60
- Tap Return and connect to the internet
- Go back to the Activation screen and tap Activation help
- You will receive a notification that you have finally connected to the DNS server
This method requires DNS server reconfiguration every time your iPhone is locked with the Apple ID.
How to Hack Apple ID using IMEI
How to Bypass Apple’s iCloud with Your Device’s IMEI Number and Delete Your iCloud Account Online:
Getting at your photos, messages, calendar, contacts, and notes—and other important information—stored in the Cloud is the primary motivation behind iCloud Password Hack techniques. To access all of that information stored in iCloud, those techniques must “find” the Apple ID and password for that account.

In this article, we’ll explain to you:
- How iCloud password Hack tools work
- What data can get iCloud Hacked
- What weakens an iPhone for an iCloud password Hack
- iPhone’s defenses against hacking iCloud password methods
- Latest iCloud Password Hack tools
- Unlock iCloud by IMEI service – Not an iCloud Password Hack
There are a number of services available to break into a user’s iCloud account and access all of their data.
Using a password-cracking tool to get into your own iCloud
The software that facilitates cracking an iCloud password was not designed for that function. Although most of these resources are spyware, some have recently begun providing services related to Apple’s iCloud.
These apps typically necessitate installation on the target device. The most up-to-date iterations of these spyware apps don’t even necessitate physical access, as they can get to the iCloud data online via the Cloud backup. It is possible to hack into iCloud from afar.
What Kinds of Information Can Be Stolen From iCloud?
When compared to the traditional hacking tools that must be installed on the victim’s iPhone, the remote iCloud hacking tools are not as effective. But they can read everything you send and receive, including your entire contact list, calendar, and any notes you make. Your location, keystrokes (to see what you type on your iPhone), or audio/video feeds are safe from prying eyes.
What makes an iPhone more vulnerable to a hack of the iCloud password?
The following conditions must be met for a hacker to gain access to your iCloud account:
A hacker can only access your data if he or she has both your iCloud ID (Apple ID) and password.
Two-factor authentication on the iPhone should be disabled.
The “Backup to iCloud” setting on the iPhone should be activated.
If any of the aforementioned conditions are not met, then the remote iCloud password-hacking tools will be unable to gain access to the contents of your iPhone.
Password-cracking techniques for iCloud accounts, and how iPhones protect you
Stopping the Hacking of iCloud Passwords
It’s nearly impossible to detect, identify, and locate remote methods of hacking iCloud passwords.
You won’t be able to trace them back to your iPhone because they aren’t there. It is even more difficult to detect malicious activity on iCloud because Apple keeps all activity logs secret.
Improve your iPhone in at least one of the areas listed above, though doing so across the board is recommended.
- Be sure to alter your iCloud password every few months.
- Don’t let anyone else use your Apple ID or password.
- Never write down or save your password anywhere on your computer (they can be hacked!)
- Avoid using simple or weak passwords by generating them randomly.
Put in motion two-factor authentication. No one else will be able to use your iPhone unless it is lost or stolen.
Switch off iCloud backup and use iTunes instead. If your iCloud is empty, even if a hacker breaks into your account, they won’t be able to access any of your data.
What a reporter did to break into her brother’s iCloud account
This article by a reporter for the Washington Post is fascinating because she hacked her brother’s iCloud account despite having no experience with computers or hacking.
She used the iCloud change password’s “Security Question” feature to her advantage. It was easy for her to guess the answers to the security questions and thus force a password reset.
Modern iCloud Password-Breaking Software
iOS vulnerabilities are heavily utilized by online hacking tools. There is a greater risk of vulnerabilities and exploits in older iOS versions.
Even so, Apple is constantly updating, patching, and otherwise bettering iOS, with a particular emphasis on making the system more secure.
The old online hacking tools for iCloud passwords that used to work are useless now.
We have already done extensive research on many iCloud password Hacking tools, the most well-known of which are iCloud lock removal US and it.
In a matter of seconds using Hollywood hacking techniques, iCloud Lock will be a thing of the past… maybe.
Secure Your Password
One of the most effective ways to protect your Apple ID is to secure your password. To do this, create a strong password that consists of at least 8 characters, including upper- and lowercase letters, numbers, and symbols. Additionally, avoid common words or phrases as they can be easily guessed by hackers. If you’re worried about forgetting your new password, consider writing it down or using a trusted password manager app like LastPass or 1Password.
Two-Factor Authentication
Another way to help keep your Apple ID safe is to enable two-factor authentication (2FA). With 2FA enabled on your account, you will be required to enter both a secure password and a one-time verification code when signing into iCloud or other services with your Apple ID. The verification code will be sent via SMS or iMessage and must be entered before you can access the service. This means that even if someone were able to guess or somehow obtain your password, they would still not be able to access your account without also having access to your phone number or device.
Be Careful What You Click On
Finally, it’s important not only to secure your password but also to be aware of what links you click on while browsing online. Be wary of suspicious emails or text messages containing links as these could lead you directly into a hacker’s trap designed specifically for stealing Apple IDs! Additionally, look out for phishing scams where hackers attempt to trick users into providing their login credentials by creating websites that appear almost identical to legitimate sites such as the App Store or iTunes Store.
Conclusion:
Your Apple ID is an essential part of accessing all things related to Apple products and services — so it’s important that you take steps toward protecting it from malicious activities like hacking attempts. Make sure you use strong passwords and enable two-factor authentication for added security; additionally, always be careful about what links you click on when browsing online as these could lead directly into a hacker’s trap! By following these simple steps and remaining vigilant about potential threats online, SPY24 users can ensure their data remains safe!
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.




