Best Tools to Hack Github Android – iPhone

GitHub is a code-sharing and publishing service or a social networking site for developers. Both terms are true, but why would anyone think of hacking GitHub? Gate is at the heart of GitHub, an open-source project started by Linus Torvalds, the creator of Linux. Git, like other copy control systems, manages and stores project editing. Although thin systems are mostly used for code, Git can also be used to manage any other type of file, such as Word documents or Final Cut projects.
Android Hacking Tools on GitHub
Blog Introduction: Android is the most popular mobile operating system in the world. According to Statista, Android accounted for 85.9 percent of all smartphone shipments in the second quarter of 2019. That’s over 1.6 billion Android devices in use around the world.
With such a large user base, it’s no surprise that Android is a prime target for hackers. That’s why we’ve compiled a list of the best Android hacking tools available on GitHub. With these tools, you can find vulnerabilities, crack passwords, spoof locations, and more.

dSploit
dSploit is an Android network analysis and penetration suite which aims to offer IT security experts/geeks the most complete and advanced professional toolkit to perform network security assessments on a mobile device.
drozer
drozer (formerly known as Mercury) is the leading security testing framework for Android. You can use drozer to search for security vulnerabilities in apps and devices by assuming the role of an app and interacting with the Dalvik VM, other apps’ IPC endpoints, and the underlying OS. drozer allows you to inspect packaged apps and devices running stock firmware or vendor-customized versions of Android 4.4+.
Burp Suite
Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities.
How to Hack an iPhone Using Github
Blog Introduction: In this blog post, we will show you how to hack an iPhone using Github. This method requires no jailbreak and can be done from the comfort of your own home. All you need is a computer with an internet connection and the GitHub repository for the SPY24 app.

Step 1: Download the SPY24 app from Github.
Step 2: Connect your iPhone to your computer using a USB cable.
Step 3: Launch the SPY24 app on your computer.
Step 4: Enter your iPhone’s passcode when prompted.
Step 5: Select the “Hack” option from the main menu.
Step 6: Follow the instructions on the screen to complete the hack.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
That’s all there is to it! By following these simple steps, you’ll be able to hack an iPhone using Github without any jailbreak or special knowledge required.
So consider it as a filing system for any draft document. So it’s natural for someone to find a gateway hack tutorial appealing to some. In this article, we will review the GitHub hacking tool.
To hack GitHub, it is necessary to have information about its features;
On GitHub, the user can view versions of projects in a repository without notice of any changes.
Watchers watch the GitHub repository to change the watchlist.
On GitHub, each user can star other users’ repositories in their repository.
In GitHub, asterisks are used to save or mark another user’s project so they can track it.
On GitHub, a fork can copy the project and can freely test on the copied project without damaging the original project on GitHub.
On GitHub, when you follow people. You can see their activity view in your news field.
The query above shows a lot of information from each GitHub user that can be used in the early stages of penetration testing.
Hack tool GitHub Free

Gitrecon
is a GitHub information-gathering tool. Gitrecon is a free and Open source tool available on GitHub. Gitrecon is a reconnaissance tool used for reconnaissance on GitHub accounts.
This tool is very useful when you want to get information about GitHub profiles that you normally wouldn’t be able to get from just looking at their profile.
Many developers enter their information to register on the GitHub site, such as email, username, and…, but many people do not care that this information is disclosed. This powerful get recon tool allows you to extract information by analyzing the desired user. And show it to the hacker:
Stardox
Is a data collection tool for GitHub stars that deletes Github information and displays it in the list tree view. Interestingly, it can be used to gather your own information or details about stargazers Using someone else’s tank.
What data does it receive:
- Total repositories
- Total Followers
- Total Following
- Stargazer’s Email
GateHub is very secure and it is not easy to hack it. Hacking refers to activities that seek to compromise digital devices such as computers, smartphones, tablets, and even entire networks and information associated with any of these devices.
But the point is that hacking may not always have been done for malicious purposes; They describe “entertainment”.
But that’s not the case, hacking sometimes means finding a way to persuade something to do what we want it to do. So it does not seem strange to have articles about GateHub hacking training.
Get tools from Hub Kit manually
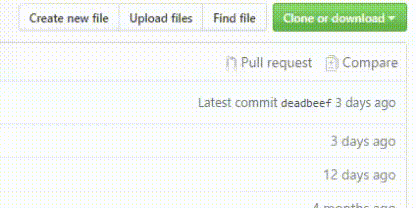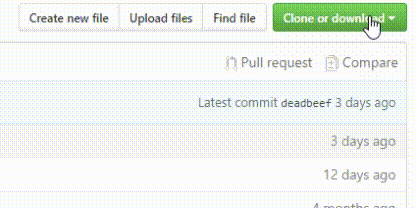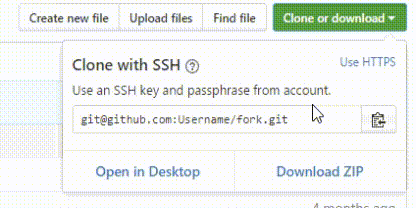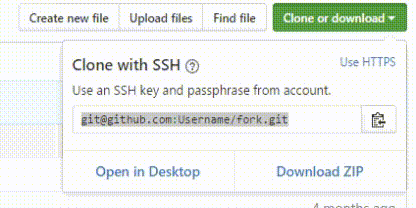
Download the tool manually from GitHub, as you can see in the image below, click Clone or download to download from the right. You will see three sections. In the first section, you can copy the tool link and use it in your Linux like the above command. In the second part, you will see the Open in Desktop option. When you open this option, you will download the required program for GateHub, and you can receive your tool directly each time you enter the GateHub site. The last part, as its name suggests, Download ZIP delivers the tool files compactly and directly
This tutorial is designed for loved ones who want to use hacking and intrusion testing tools.
GitHub Hacking Tools Introduction
Ethical hackers can use GitHub’s top hacking tools to simulate malicious attacks and evaluate any Web application, system, or database’s security. It gives a chance to fix design or code flaws before a professional hacker does.
IT security specialists utilize these tools to analyze an organization’s security readiness with their approval and a plan. GitHub has a large array of hacking tools for security testing the system during implementation and afterward.
GitHub hacking overview
Let’s discuss GitHub’s hacking tools.
- Gau
Gau gets all URLs. Gau, an open-source GitHub tool, retrieves landscape URLs. Tracking HTTP and HTTPS sites visited on websites will help investigate application subdomains.
Any abnormalities found on visited sites will be used to patch application gaps to prevent future security threats. Kali Linux runs this tool’s go code. This program requires Go and Kali Linux OS. Gau’s UI is nice.
- Dalfox
Hackers inject Cross-site scripting (XSS) into client-side code to steal sensitive data from online applications or send malicious requests to the server. This program scans for them. This DOM parser-based XSS scanner detects all three forms of XSS attacks: persistent (stored), non-persistent (reflected), and DOM.
This tool handles SQL injects, server-side template injects, and XSS attacks. Its USPs include its various testing and analytical features, great performance, and user-friendliness. This tool supports continuous integration and delivery.
- DNSx
This tool has a robust DNS kit for multiple DNS investigations. Users can use wild card filtering and other DNS checks to check system health and detect problems. It also controls and prints extracted information.
Its attributes are
- It aids in DNS tracing.
- It also probes DNS status codes.
- Operations are easy.
- Minimal requests handle wildcard queries.
If the number of subdomains searched exceeds a threshold, that system switches to wildcard and saves time.
- Ffuf
“Fuzz Faster than yoU Fool” is Ffuf. It is an open-source Web fuzzing tool that finds software hacks by randomly injecting data into the application until one combination exposes the program’s vulnerability. It eliminates several flaws that might allow hackers into apps.
Ethical hackers love this tool to find application bugs before professional hackers do. This program finds bugs and hacker-hidden subdomains, files, and directories.
This tool is the fastest web fuzzing tool and has many useful features and ways to filter responses. This modular Go-language utility integrates with the existing architecture with minimal effort. This tool can mislead if threads and filters are not properly used.
- Nuclei
Nuclei can scan many hosts for malware using a template. This tool’s strengths are fast scanning and no false positives. YAML, a data-centric markup language, is used.
YAML lets Nuclei do any security checks. It scans HTTP, DNS, File, TCP, etc. This utility scans user-provided templates for malware. IT security specialists submitted hundreds of templates to GitHub.
This tool scans websites for valid subdomains and lists them. It passively discovers subdomains using multiple online sources. This modular, speed-optimized tool matches user expectations. It’s fast, efficient, and passive.
- LastRecon
It is an open-source website malware detection program. This Python3 utility collects data from a website or system using open-source codes. It quickly gathers and displays data from many websites and social media.
This tool crawls, analyses headers check SSL certificates, and verifies identities.
Other GitHub Hacking Tools
Webscreenshot.py, Turbolist3r, Nmap Automator, DXAS, BoomER, Aquatone, Powershell-RAT, DumpsterFire, CMSeek, Sniffair, and more are on GitHub.
Conclusion:
GitHub provides many ethical hacking tools. Users can select a tool to check security vulnerabilities and fix them before going online. After implementation, they can periodically check for malcontents and fix them. If you’re looking for tools to help you hack Android devices, these Github repositories have you covered. dSploit and drozer are great for finding vulnerabilities, while Burp Suite can help you exploit them. So what are you waiting for? Get started today!