Hack Messages (SMS) By Phone Number
Have you ever wanted to get a text but didn’t have the phone number? Maybe you were going to a party and wanted to be able to text people without giving out your personal number. Well, there’s an app for that! Cloning a phone number is very simple and can be done in minutes using only your smartphone. Keep reading for instructions on how to do it.
How to clone a phone number
Cloning your phone number can be an extremely useful tool for a variety of reasons. First, it allows you to easily switch between multiple phone numbers without having to deal with changing your SIM card or getting a new phone entirely. In addition, cloning your phone number gives you more control over the type of content and messages that are associated with that number. For example, if you want to use a particular phone number for work-related communications but only receive texts and calls from family members on that line, cloning your number makes it easy to manage these separate communication streams.

What is the process of cloning a phone number
Another key benefit of cloning your phone number is that it allows you to take advantage of different pricing plans and promotions offered by mobile carriers. For example, if one carrier offers a lower rate for unlimited data but has more limited texting and calling options, you may want to use your cloned number with that carrier to take advantage of the discounted data plan, while still receiving texts and calls on your original phone number with a different carrier.
Why you would want to clone your phone number
Cloning your phone number can also be useful if you need to receive texts or calls during periods when your primary phone is offline or out of range. For example, if you are traveling abroad and do not have access to cell service in certain areas, cloning your phone number allows you to receive messages via SMS while still being able to receive important calls through wifi or another means of connectivity.
The benefits of cloning your phone number
Overall, there are many benefits associated with cloning your phone number, including increased flexibility, control, and convenience. If you are thinking about cloning your phone number, be sure to do your research and find a reliable service provider that can help you execute the process effectively.
How to receive texts from a cloned phone number
Want to know how to read someone else’s messages without them knowing? It’s a lot easier than you think! Yes, you can read text messages and listen in on phone calls with many powerful spyware programs. If you want to keep an eye on what your kids are doing online, you might want to hack their text messages. This might be necessary if your child doesn’t say what’s on his mind and seems worried. If talking to the child doesn’t work, keeping an eye on what they do on their phone might.
Let’s take a look at what to do. In this article, we’ll look at two of the most important spy and phone monitoring apps: SPY24 and Cocospy. Both are compatible with iOS and Android.
A spyware program is the best way to read someone else’s text messages without them knowing. There are a lot of spyware and monitoring programs, but none are as safe and well-known as SPY24. The app is made by a well-known company that has millions of customers all over the world.
A lot of different kinds of media also talk about the company. This way, you can be sure that the phone monitoring solution you’re using is very strong. With this app, you can learn how to Hack Messages By Phone Number from another phone.
Also Read
Hack Whatsapp Messages Online Free
SPY24 App SMS Hack Codes
One of the best ways to keep an eye on a phone is with SPY24. SPY24 can be used to track texts on both Android and iOS devices. This is a solution that doesn’t need to be rooted or broken out of jail. If you already have an Android device that you want to hack, you don’t have to root it first.
You don’t have to break into an iPhone’s jail to use SPY24 either. This is a very important part of the app. Many spyware apps won’t work on your device unless you root or jailbreak it, which makes it hard to use the app. With SPY24, everything is so easy!
The other great thing about SPY24 is that you don’t have to install it on an iOS device. You just need to know the iCloud password for the device. There’s nothing you need to set up. From far away, you can see everything. Tell us how to use the SPY24 app in more detail.
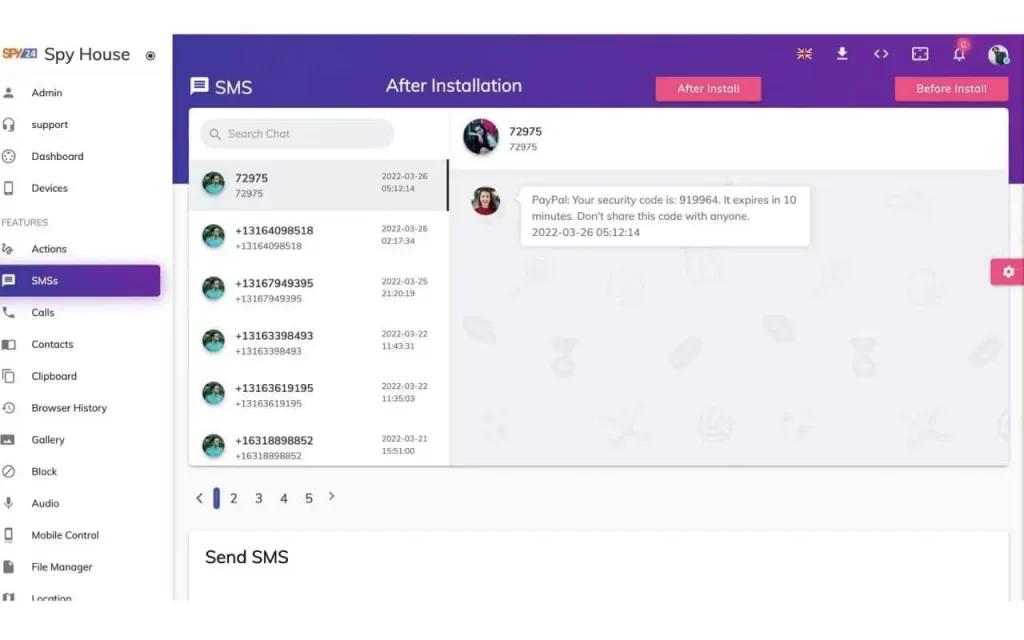
You can hack messages by phone number with the SPY24 app.
Let us show you how to use SPY24 step by step. As long as you do everything right, it’s very easy to use.
Step 1: Go to the SPY24 app’s official website and create a new account. This is important because your account will be used in all the other steps.
Step 2: Download the SPY24 app to the target device if you want to use SPY24 with an Android phone. Follow all of the instructions and give the app all of the permissions it needs to work right.
If the device you want to use is an iPhone, you don’t need to install anything. For iCloud, all you need is your Apple ID and password. With SPY24’s cloud-based monitoring solution, you can do everything from far away.
Step 3: Once the app is set up, log in to the control panel of the remote device. A screen like the one below will show up.
- SPY24 dashboard
Now, you can click on the “Messages” tab to see what text messages are being sent and received. So, not only can you see what the message says, but you can also see how to get in touch with the person who sent it. You will also be able to see all the media files that are being sent.
The steps are very clear and easy to follow, as you can see. If you want to read text messages on a device, you don’t have to root or jailbreak it. You can look at all your messages from far away. Check out this live demo of the SPY24 app to see how it works and what it looks like.
What an online spy hacker can do SMS SPY24 is able to do a lot of different things. In this part, we’ll find out more about its SMS tracking features and how to use them.
With the app, you can check all incoming and outgoing Hack Messages By Phone Number from afar. As events happen, they are all kept up to date. This means that you will be able to see new messages as soon as they are sent or received.
SPY24 also adds the time to each message so you can figure out when something happened. When you have a lot of texts to read, things can go wrong quickly. With timestamps, it’s easy to find out when a call happened.
One of the best things about the app that lets you track SMS is that you can download all the media attachments. Multimedia messages usually include pictures, music, and videos. You can get all of them with SPY24.
The right place, but not last! There are actually a few ways to do this. But we strongly recommend that you use a trusted app that you know will always work.
This will save you time and make it easy for you to track text Hack Messages By Phone Number. SPY24 is one of the most well-known spy apps, so there’s no need to explain what it does. With SPY24, you can use a different phone to read the target’s text messages.
You can also make good use of a number of the app’s other features. Like SPY24, the app can be used with both Android and iOS. There’s no need to jailbreak or root. IOS doesn’t need to be installed at all, just like SPY24!
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
How can I read someone else’s text messages without them knowing?
Many apps can hack or spy on a phone. These apps reveal a smartphone user’s text messages, call logs, contacts, social media accounts, and more. Most apps cost money. Apps cost money.
App compatibility is another highlight. Some apps are iOS-only, but many are Android-compatible. Here are the best apps to hack a phone remotely.
- Premium SPY24
SPY24 is the best Android and iOS spy app. This app works without “rooting” Android phones.
SPY24 has many parts. It allows multiple ways to access the target smartphone’s data. Call logs and personal messages are on the target phone. We’ll discuss SPY24’s capabilities next.
Can read all target phone messages. Text and video messages on the target phone can be checked and deleted quickly.
SPY24 can also access the target phone’s personal email. Email accounts require passwords.
This app can monitor social media chats, comments, and more. If the device has social media messengers, you can access them.
WhatsApp and Skype: SPY24 can access Skype and WhatsApp. Check messages, mark them unread, download multimedia, and more.
You can also message Tinder, Telegram, and Instagram users remotely.
To use this app, you don’t have to pay anything.
App configuration: Locate the target phone and install SPY24. Setup
- Sign in to SPY24 from the Cloud Portal:
SPY24.APP lets you research the target device. Look at, change, and delete target device data.
App for Cocospy ANDROID SMS HACK
Cocospy has many different parts. It lets you see almost all of the information on the phone you want to spy on. Let’s quickly look at some of the app’s most important features.
Text message spy: If you use Cocospy, you can keep track of SMS messages on the target device.
You can see all the messages that come in and go out, as well as the contact information.
Facebook messages: Facebook Messenger is also a good app for sending and receiving messages these days. You can easily see all of your Facebook messages with Cocospy.
Cocospy is a Snapchat spy that makes it easy to see photos and texts that disappear after a certain amount of time.
With Cocospy’s Instagram Spy, it’s easy to see direct messages and links shared on Instagram.
Monitoring WhatsApp: If you want to keep track of your WhatsApp text messages, Cocospy makes it easy to do so. You can also look at all of the group chats.
But there’s more! Cocospy has a number of other advanced features, like the ability to track a device’s location and set up geofencing alerts. You can learn more about Cocospy by visiting the app’s website.
How to Use Cocospy to Secretly Hack Text Messages
Want to know how to read someone else’s text messages without them knowing? Well, you can use the Cocospy feature Stealth Technology. This means that once the app is installed, the icon will be taken away by itself. The app will then run quietly in the background.
This makes sure that you can track text messages from a distance and keep it a secret from other people. The app was made to work quietly in the background without using a lot of power.
How to Use the Cocospy App on iOS and Android
Setting up Cocospy is just as easy as setting up SPY24. It is easy to use. Both Android and iOS users can get the app. You can just create an account on the website and then move forward based on the type of device you are using.
If your target device is an iOS device, you don’t need to install anything because the solution is in the cloud. This makes it very easy to use and also lets you keep an eye on the device without touching it.
Cocospy will first need to be made available on Android devices. You’ll also have to give the app all the rights it needs.
The Android app is very small and doesn’t use much data – less than 2M. It can also be uninstalled with just one click from a distance. It’s easy to set up and only takes about 5 minutes.
So, you can see that it’s easy to follow the steps. In a few minutes, you’ll be able to read all of the text messages on another phone. You can see how Cocospy works by looking at the live demo.
You don’t have to root an Android device or jailbreak an iOS device to use Cocospy.
How can I read text messages when I don’t have a phone?
Parents often have to check their kids’ cell phones to make sure they are safe. When employees and their bosses don’t trust each other, the boss may need to read their text messages. High-end security systems are built into most smartphones today. So, it’s not easy to break into someone’s phone. You need a program called spyware to read someone else’s text messages.
How can I read someone else’s text messages when I don’t have their phone?
You can spy on someone from far away if you can hack their phone with an app. You can only sign in once to the phone you want to use. Once you have the phone, you need to install and set up a spyware program on it.
Once you’re done, you can use your phone or computer to access the data on the target device from a distance. You can spy on text messages, social media posts, phone calls, and other things.
The idea of stealing text messages from a cell phone is appealing to a lot of people. People are naturally interested in what’s going on in the lives of other people and want to know about it.
Most of the time, parents want to watch the Hack Messages By Phone Number to see what their kids are doing. Business owners sometimes want to keep an eye on their staff.
Even if you don’t have access to a phone, it’s not hard to learn how to hack text messages if you know what to use.
How do I get into someone’s phone to read their text messages?
You can read someone’s texts if you know the password or code to get into their phone. The ability to get to the phone is very important. But today’s smartphones are built with strong security layers.
Most phones now have fingerprint protection built in. So, if you don’t have someone’s phone, it’s not easy to read their messages.
But you can read someone else’s text messages from a long distance. With spyware, it is easy to get into someone’s phone and read their text messages and other important information. The person who is using the phone wouldn’t even know that information on it is being looked at.
Describe how SMS works.
There are a lot of apps like this one. If you don’t know much about technology but still want to hack a phone, you need to find a simple and reliable app. Here are the top five apps for hacking someone else’s text messages in 2022.
mSpy SMS HACK CODES IPHONE
The app mSpy is used to spy on people. A lot of things come with it. So, this app on a smartphone gives you access to different kinds of information. Many parents use this app to keep track of their kids.
If you have a teen at home and you think he is acting differently, you can spy on his phone to find out why. It can keep your kid from getting into a lot of trouble.
mSpy can also be used by employers to keep an eye on their staff. If you use mSpy, you can see the following on the target smartphone:
mSpy SMS HACK CODES IPHONE
You can keep track of who calls you and who you call.
- mSpy tells you where the person with the phone is.
- Notes, IM apps, text messages, and multimedia messages are all available.
- This app can record keystrokes and delete them.
Pros:
- You don’t have to jailbreak your iPhone to use this app.
- Great controls and features for spying.
- Fair prices
- The dashboard is simple and easy to use.
Cons:
- Once you wipe the phone, you can’t use a backup to get the data back.
One license can only be bought at a time for one device. You need to buy a licence more than once if you have more than one device.
Since its release in 2013, mSpy has become a well-known hidden Android spy app very quickly. Parents, employers, and others can use this app to read a cell phone’s private messages and find out other information.
XNSPY HOW TO HACK SMS VERIFICATION CODE
You can find out if your partner is cheating on you by looking at his cell phone. You can keep an eye on your child’s phone by using this app. Both Android and iOS devices can be used with XNSPY. Here are some of the things that this app can do.
XNSPY HOW TO HACK SMS VERIFICATION CODE
- You can easily look at the phone’s phone calls, contacts, and text messages.
- With the help of this app, you can also keep track of keylogging.
- GPS tracking lets you find out where a cell phone user is physical.
- Instant messages and social media accounts can be accessed.
- You can choose to record the calls made on the phone you want to spy on with XNSpy.
Pros
- Both Android and iOS devices can use it.
- iOS doesn’t need to be jailbroken.
- Android phones don’t need to be rooted.
- Low annual fee
- A lot of ways to spy on people.
Cons
- No desktop version is available.
- If you want to cancel your subscription, you may not get your money back in full.
- For advanced features, you need to jailbreak and root your phone.
- Poor customer service
FlexiSpy
FlexiSpy is another popular Android spy app. To use this app, you have to be near the phone you want to track. You’ll need to know the phone’s unlock password to put this app on the phone you want to use. You need to look at the “settings” options after the programme is installed. Change the settings in the “Settings” menu to make the app your own. In the next section, you’ll learn about some of FlexiSpy’s most important features.
FlexiSpy SMS Hacking
- The app can be used to spy on a smartphone user’s GPS location.
- You can look at your Internet history and activities.
- This app makes it easy to get to your contacts and messages.
- You can look at pictures and other media on the target device.
- This app can be used to spy on the user’s social media accounts.
Pros:
- It comes with a lot of things.
- You can access the target device’s camera from a faraway place.
- There is a free demo account that has limited features.
- Help for customers is always available.
Cons:
- Android devices that have been “rooted” can use more advanced features.
TheTruthSpy
The TruthSpy app makes it easy and safe to spy on someone’s phone. This app works on Android-based systems. You don’t have to “root” your Android phone or tablet to use this app. The best thing about this app is that it has so many features. Here are some of the things it can do. It lets you see what the target device is doing on the internet. You can also control what people do online from far away. You can stop the target device from going to certain websites, for example. It gives you access to messages and multimedia files on the device you want to control. You can quickly look at your messages on WhatsApp, Facebook, Tinder, and other apps. Users can set up alerts that will let them know when certain things happen on the target device. It helps to watch what the target phone does in a few ways.
Pros:
- The interface is easy to use.
- An application that saves money.
- Free for 2 days
Cons:
- Not compatible with iOS, Blackberry, or Symbian.
- Only chat is available for customer service.
- Bad service to customers
- Trial versions with limited features
Is it okay to read someone else’s messages?
Everyone has the right to be left alone. A person’s right to privacy is protected by the law and constitution in many countries. So, it is against the law to follow or watch someone.
It is against the law in most countries to use apps to get into someone else’s phone. But there are some things that aren’t true. People in charge of security can use the information that smartphone users give them to find possible threats to the country.
Hacking is not a good thing to do, but sometimes it has to be done. You might think that your workers aren’t doing their jobs right if you’re the boss.
Parents need to check what’s on their kids’ phones to keep them safe. When these things happen, you can use spying apps to find out about a smartphone user. You need an advanced app to get to important information on the target phone.
How to Keep from Being Hacked?
As the number of people who use the internet to talk has grown, hacking has become a major threat to the world. People keep all kinds of private and important information on their smartphones. If the wrong people get their hands on data, it could kill people. So, here are some things you can do to keep hackers out.
- You shouldn’t click on links that you haven’t checked out and that look fishy.
- If you want to keep your phone’s data safe, you should use fingerprint and face detection locks.
- Never tell anyone your email password.
- It’s important to avoid strange popup messages.
There are a few ways to tell if someone has broken into your phone. What do these signs mean, then? In the next section, a list of the signs will be given.
A sign of phone hacking is a battery that drains quickly. Even if you’re not using the phone, you’ll notice that the battery is going down quickly.
If someone gets into your phone through a hack, it will run slower. When a spy app is running in the background, the phone slows down.
A lot of data use is another sign that your phone has been hacked. Even if you don’t use the Internet much, you will notice that a lot of data is being used.
If you have a good security app on your phone, hackers won’t be able to get in. For example, you should have a paid version of antivirus and antimalware software on your phone.
There are a few different ways to clone a phone
As more and more people rely on their smartphones for everything from making calls to checking email and browsing the internet, there has been an increased demand for tools and services that allow users to clone their phones. Cloning a phone involves creating an exact copy of all of its data and settings, which allows users to easily switch back and forth between devices without losing any of their information or preferences.

You can use special software or a hardware device
There are several different methods available for cloning a phone, including using specialized software or hardware devices. One of the most common methods is to use a phone cloning app, which can be downloaded from online marketplaces such as the Google Play Store or Apple App Store. Another option is to use a phone cloning cable or another hardware device, which may require some technical knowledge and experience in order to set up properly.
- Cloning a phone requires you to have access to the target phone for a brief period of time
Before you clone your phone, it’s important to make sure that you have access to the target phone for a brief period of time. Depending on the method that you use, this may involve physically connecting your device to the target phone or simply entering its passcode into an app on your own device. It’s also important to choose a reputable software or hardware provider that can help with the cloning process, as you’ll need to follow their instructions carefully in order to ensure that your phone data and settings are copied without any problems.
- Once you’ve cloned a phone, you’ll have an exact copy of the original phone’s data and settings
Whether you’re interested in cloning a phone for personal or business purposes, it’s important to do your research and carefully evaluate the different options available to find the solution that is right for you. There are many different providers of phone cloning software and hardware devices, so be sure to compare their features and prices before making a final decision. In the end, the key to successful phone cloning is taking the time to choose a reliable provider that can help you get the job done quickly and easily.
- Be careful when cloning phones, as it can be used for unethical purposes such as stealing someone’s identity or personal information.
- If you’re interested in cloning a phone, it’s important to choose a reputable software or hardware provider that can help you with the process.
- There are many different options for phone cloning, so do your research and find the solution that is right for you.
How to Use the USSD Code to Find Out If Your Phone Is Hacked or Tapped
Want to know the USSD code you can use to find out if your phone has been hacked or tapped? We can’t all deny that smartphones are now a must-have in the digital world we live in. We use it to talk to other people, send text messages, share and look at content on social media, and more.
But smartphones have also become a way for people to get into our private lives. Have you thought about the fact that someone could be spying on your phone while you use it?
They could be hacking or tapping your phone to get to your information, hear your private calls and conversations, and figure out where you are.
So, in this blog, you’ll find out the USSD code you can use to find out if your phone has been hacked or tapped. Use these USSD codes to check if your phone is being tapped or hacked.

How do people hack phones?
Before you worry about the code to find out if your phone has been hacked, you should know how your phone will be hacked. So, here are some ways someone can hack your phone:
- Phone’s Movement
According to a report written by cyber experts at New Castle University in the UK and released in April 2017, “Cybercriminals or hackers can steal a phone’s PIN by tracking the phone’s movement. With the information gathered by the phone’s many sensors, hackers can guess your 4-digit PIN with 70% accuracy on the first try and 100% accuracy on the fifth try.
- Sensors on a phone
Smartphones and other smart devices have features like GPS, front and back cameras, microphones, and sensors like proximity, gyroscope, NFC, accelerometer, and rotation sensors.
And some apps and websites use your phone’s features without your permission to find out a lot of private or sensitive information about you, like your phone call logs and times, your physical activities, your text messages, touch actions, PINs, and passwords.
- Phishing
Phishing is another way that hackers get into your phones. Some browsers or websites can have bad code, like spyware, that can hack your device and spy on you.
When you open these browsers or websites on your phone or tablet and then open apps that have your important information, like banking apps, hackers can see everything on your device.
Hackers can also use your device without your knowledge to put spyware on it. So, even when your phone is locked, they can spy on you by using your phone’s camera, GPS location, microphone, etc.
How to tell if someone is hacking your phone
Some ways to tell if your phone has been hacked or tapped are:
- Even when you’re not using your phone, the battery life keeps going down.
- The amount of data used is too much and more than usual.
- Even though you turned on your adblocker, you are still getting pop-ups that you don’t want.
- Your phone turns off and turns back on by itself without you telling it to.
- During calls, you hear unclear or annoying sounds in the background that aren’t coming from the other end.
What would happen if someone broke into your phone?
When someone breaks into your phone, you might have to deal with the following:
By changing your PIN or password, hackers can get to your private information and even lock you out of your device.
Not only can they read your messages, but they can also look at your photos, turn on your microphone, and put harmful codes like spyware and ransomware on your phone.
When hackers get into your phone, they can add it to a group of computers that mine cryptocurrency.
7 USSD codes to see if your phone is being hacked or tapped
Does your phone act strangely? Then you must be worried about how to check if your phone has been hacked. Here is the USSD code you can use to find out if your phone has been hacked. Just type it into your call dialer.
The cell phone, not the operating system, is what these codes are based on. This means that they work with all types of cell phones. So, these are the Android and iOS codes to check if your phone has been hacked.
- ##002#
If your voice call has been forwarded, and you enter the code ##002# on your call dialer, it will delete all of them. The data call, SMS call, or fax call will also be erased by this USSD call. Now your phone is safe and calls won’t go anywhere else.
- *#21#
*#21# is another USSD code that will tell you more about your phone. You can find out if your phone, SMS, data, or fax calls have been diverted by dialing this code. To find out if your calls have been redirected, dial the *#21# code. It will also tell you the number to which they were sent.
- *#62#
Another code that can tell you if your number is safe or not is *#62#. This code will tell you everything you need to know about whether or not your voice, data, SMS, or fax calls are being sent to another number without your permission.
- *#61#
Hackers can take over incoming calls and send them to a different phone line. If you don’t answer the call, you might not even know that it was forwarded. So, if you call someone and they don’t answer, you can use the *#61# code to find out if someone else is getting your call.
- *#67#
You can use this code when you don’t want to take a call or are already on the phone. If you dial this code, you can find out if your calls and messages are sent to other numbers when you don’t answer.
- *#004#
You can find out about your phone’s conditional forwarding by dialing the USSD code *#004#. With conditional call forwarding, you can send incoming calls to a different phone line when your wireless device is busy, unreachable (because it has lost connectivity or is turned off), unanswered, or rejected.
You will be able to see who gets your calls or messages when your phone is busy, out of range, on another line, or if you reject or don’t answer an incoming call.
- *#06#
If you dial *#06#, your device’s IMEI (International Mobile Equipment Identity) number will show up. The IMEI number is a 15-digit code that is unique to each phone. Manufacturers or phone carriers can use IMEI numbers to find phones that have been lost, stolen, or hacked.
So, these are the codes you can use to see if someone has hacked your phone. You won’t have to worry about how to find out if your phone is being hacked or tapped if you have these codes.
Conclusion
We all worry that our privacy could be invaded because of smartphones. So, you can use the USSD code to find out if your phone has been hacked. Your phone number, your calls, and your data can all be kept safe. So, you can rest easy knowing that hackers won’t be able to track your phone.
Want to know how to sneakily read someone else’s text messages? Well, you can now use the powerful spy apps SPY24 and Cocospy. They are both easy to use and safe. You’ll be surprised at how quickly you can start using these apps.
Both of these apps can be used to keep an eye on things. This means that you can check all of your text messages from any web browser on any device, no matter where you are. To read text messages from far away, you don’t need to put any app on your device.
Also, you don’t need to root or jailbreak the device you want to use. Both apps use a technology called “stealth mode” to make sure they can’t be seen on the target device. Android apps work well, and the first time you install one, you need to give it access to your phone.
To install an app on an iOS device, you don’t even have to be in the same room as the target. It is a solution that doesn’t need to be put in place. Everything happens in the cloud, which makes it easy and convenient.




SPY24 hacks on instagram helped me hack into my husband’s phone when i had a feel he was cheating. all thanks to SPY24 who helped me find the proof.