Can Someone Hack into Your Phone by Calling You
A phone is a personal device that contains your most important pieces of information. Due to rapid population growth and advanced technology, almost everyone owns a phone. Unfortunately, this gadget has the most potential to expose your most sensitive information to hackers. It is usually important to ensure that your mobile phone is protected from hackers and data thieves.
The chances of a hacker gaining access to a phone simply by call hack are slight. However, hackers often pose as authority figures and can call someone and request personal information, which they can then use to access the owner’s phone and other devices.
If your phone exhibits unusual behavior more than once, you should be on your guard. There is a good chance that you are hacked. In this post, you will learn about different ways someone can hack your phone.
Can Someone Hack My Phone by Calling Me?
It is a popular question that most people ask themselves. It’s good to understand that just like a hacker can’t hack your phone by just sending you a single text, someone can’t hack your phone by just making a phone call. Simply put, a call hack is impossible. Most hackers have more complex strategies to hack your phone. Moreover, from an official point of view, a hacker may call you and ask for your personal information. With this information, he or she will start hacking your account. Therefore, hackers cannot access your data just by a simple call hack.
Hackers, on the other hand, can do a call hack, but that depends on how likely you are to answer the phone. You can receive calls from many strangers. Answering a call doesn’t mean someone will hack your phone, but revealing important information can make you a victim of hackers.

You should also know that mobile phones are like mini-computers. It is a very sophisticated and powerful device that has undergone several years of development work. It’s good to know that a hacking expert can locate you with a single phone call. Similarly, tracking a cell phone signal takes time, but you can track where the cell phone signal is bouncing from. And hackers can’t pinpoint where exactly you live, so you don’t have to worry.
In short, the chances of someone calling you and doing a call hack are slight. Even if a call hack succeeds, it won’t give them any important data.
Can Someone Hack My Phone by Texting Me?
“Can an unknown number hack your phone by sending you a text message?” It is another question many users ask. I don’t think texting someone and hacking their smartphones is possible. But it’s also hard to say because we live in a rapidly changing world where technology makes everything possible.
You must have received many texts from an unknown source. Your phone won’t be hacked just by checking your text messages. However, be wary of messages containing questionable links or coupon codes. Before clicking any link, ask yourself: “Does it look real?” Will the link reveal my personal information?”
If you fail to identify this false information and accidentally tap a malicious link, it can install spyware on your phone that sends sensitive information to hackers. Alternatively, you may be redirected to a phishing website asking for information about your account.
So, if you receive a text about a special offer and need to click directly on that link to activate the offer, think twice before clicking. It greatly reduces the chances of someone hacking into your phone via SMS.
Though hacking your phone by simply sending a message or doing a call hack is not easy and common, you’d better be careful.
Can You Get Hacked by Replying to a Text?
The short answer is: No, you can’t get hacked by replying to a text message. It’s just another mystery like call hack. However, we do not recommend replying to messages from senders you do not know.
While you are unlikely to get hacked when replying to SMS, you may receive more unwanted SMS in the future.
In general, replying to text messages from phone numbers you don’t know is neither safe nor good. Spam text can be dangerous. Here’s why.
Spam texters send thousands of text messages at once to random groups of phone numbers. Spammers don’t know if a phone number is active.
Blindly sending mass text messages to these phone numbers will try to find an active phone number.
By replying to these seemingly random messages, spammers will know that your phone number is active and that someone is reading the texts.
When spammers find out that your phone number is active, they will send more texts to try to scam you. It’s important to never reply to random text messages from unknown phone numbers. They can send you more text messages and make you a target for scams.
Ways of hacking any smartphone
With advanced technology, it is quite possible to hack a mobile phone. But call hack isn’t that simple. You should understand that hackers use multiple methods to hack phones. For example, they can send an email saying that your account is experiencing a serious issue that needs to be addressed immediately.

It means that you must always be alert and avoid falling into traps. And as technology continues to become more sophisticated, hackers continue to improve their hacking techniques to hack and steal information from people’s phones. Below are the various methods hackers can use to access your phone.
1. Malicious apps
Mobile phones can be easily hacked by downloading malicious apps. Additionally, criminals are now hiding malicious abilities that appear legitimate, so you should know that this is a major problem for most consumers. They may also be able to process legitimate services such as mobile games. In contrast to Apple’s App Store, Google Play integrates a large number of infected apps.
2. Using free Wi-Fi
Most people find the free, unsecured Wi-Fi at their nearest local coffee shop convenient, but they don’t realize using free Wi-Fi is too convenient for hackers. Remember, hackers can easily spy on almost anything you do over Wi-Fi. So if you need to use unsecured Wi-Fi, remember to also use a virtual private network (VPN) to keep your connection secure. Assuming you don’t feel like doing this, make sure not to log in to the empty websites. You should also ensure that you are not using your email address. If you have to use email, pay attention to the address bar.
Similarly, your website address is “https://” and not “http://”. The extra S represents a secure connection, and you should understand that you can access the website securely. Similarly, you should look for the green lock icon next to the URL. Do not provide details, especially login details, if the website does not have these indicators to ensure a secure connection. Therefore, it is safe from hackers. If you proceed without a secure connection, your phone can be 100% hacked. Ideally, free and unsecured WiFi should also be avoided.
3. Leaving your phone unattended in the public
Keep an eye on your phone when you are out in public again. Many threats are found online, so be sure to pay attention to real threats as well. Leaving your phone unattended in the public can put you in great danger. It’s good to have your phone within sight or at your fingertips. If your phone has a phone visibility option, we recommend turning it off.
Additionally, this setting will allow nearby devices to exchange data through your phone. On the other hand, don’t store logins and passwords for sensitive accounts or banking apps. It prevents hackers from automatically logging you in the same way you do on your device.
If you are going to dispose of your old cell phone, you should also consider cell phone recycling tips. It helps prevent your personal information from being misused or falling into the hands of criminals. In this regard, be careful not to leave your mobile phone unattended, especially when you are in public.
4. Clicking on a weird link in the text
Clicking on a weird link in the text, also known as phishing, is an attempt to expose sensitive information. For example, a hacker can confidently send you an SMS on behalf of your parents, a trusted person, or a friend, asking you to open a photo or PDF file. If you fall into a trap, the program can destroy your entire system. Similarly, you can allow them to steal whole files.
You can only find out that your phone has been hacked by receiving a message from a stranger demanding a certain amount of money. Denying the request can threaten to release messages and photos stolen from your phone. To avoid such situations, never use suspicious links or attachments. If you are sure that it comes from a trusted source, you can use it conveniently and safely without any worries.
You may intuit or be suspicious of some links. Avoid using them. In this case, you can go ahead and remove the link and all attachments.
5. Being lazy with your password
According to Thomas Reed, Director of Mobile and Mac at Malwarebytes, many people have this problem. Once your iCloud account is hacked, the hacker can access everything on your phone and see all the data stored in iCloud. Once they have full access to your phone, one of the ways they lock it is by using the anti-theft feature.
Note that this kind of problem can occur if you reuse passwords on many websites and unfortunately one of those websites gets hacked. Likewise, all this is avoidable. Being lazy with your passwords can make the call hack easy for hackers and data thieves. You should make sure you use unique and different passwords for each site. These passwords are usually stored in a password manager. It also enables two-factor authentication for each account. Hackers usually try to annoy you, so try to avoid this simple mistake. They spare no opportunity but use it at the maximum level.
6. Using public charging station
Public charging stations can be the solution to your problem. However, using them can set you on fire as criminals gain access to your phone. It also allows them to install apps on your device. This has been confirmed by Fathom Cyber CEO James Goepel. He is also a Professor of Cybersecurity at Drexel University. Ideally, when you’re out and your phone runs out of charge, you can use the AC charging port to charge your phone instead of using the USB port. Hackers are very smart and usually hide malware and mini-computers in public charging stations.
Professional hackers can monitor all your activity as long as you use the USB port to charge. You might think you are charging your phone while it is being hacked. So don’t quickly plug your phone into any electrical outlet you come across. There are many places where you should not charge your mobile phone: Cafes, libraries, shopping malls, tourist attractions, rental cars, hotels, train stations, and airports.
So this time when you are in public and you ran out of battery, think twice about using public charging stations.
7. Bluetooth hacking
Professional hackers typically use proprietary software products to find mobile phones with working Bluetooth connectivity. Bluetooth hacking can occur if the hacker is within cell phone range. You should be alert about this kind of hacking because it’s more common than a call hack. In addition, they are usually located in densely populated environments. If a hacker is connected to Bluetooth, they may have access to all available information. You can also access the web through your Internet connection. However, hackers can only download your data if your phone is within range.
What do you do when your phone is hacked?
Suppose you suspect that your phone has been hacked. Don’t panic because you can always find a solution to your problem. Remember that some main steps must be considered to avoid serious damage. These procedures were developed by Matt Wilson, Chief of BTB, and his Information Security Advisor. They include:

1. Use antivirus software
Antivirus software isolates malware so it can’t affect the rest of your phone. It is then deleted. Leave your antivirus software on and keep it running in the background. So if you care about your data, use antivirus software all the time.
2. Restoring your device
Restoring your device will help you clean up your device and recover data from cloud storage. The steps may seem complicated, but it’s much easier than you think. Likewise, recovery varies by phone model. Additionally, Google and Apple are easy when it comes to backing up and restoring Androids and iPhones. Taking this step will minimize the damage.
3. Factory-reset your phone
Way better, however, is to perform a full factory reset on your phone to reestablish it to the settings it had once you got it. Take these steps after backing up your information to factory-reset your phone:
iPhone:
- Go to settings.
- Click “General.”
- Click “Reset.”
- Click “Erase All Content and Settings.”
- Enter your passcode or Apple ID password.
Android:
- Click “Apps.”
- Click “Settings.”
- Click “Backup and Reset.”
- Choose “Reset Device.”
- Click “Erase Everything.”
4. Allow multi-factor authentication
If you’re stressed because your phone is hacked, don’t worry since all you must do is allow multi-factor authentication. In a perfect world, this can be an idealized thought compared to holding up for an agreeable gadget to handle the issue. Other than that, numerous celebrated administrations and apps, such as major banks, Google and Facebook, usually allow this. You should know that this step acts unexpectedly on various devices as well as apps. Fortunately, you’ll select the finest commencing point by looking at framework inclination for security settings.
5. Change your essential passwords.
It is appropriate to change your essential passwords if you suspect that your phone has been hacked. Indeed it would be superior not to do it from a gadget that has been hacked. Changing the password from your hacked phone implies merely would have given the criminals your unused password. It implies you’ll not have unraveled any problems.
Apart from the steps said over and other given security conventions, you should examine your credit cards and bank accounts. In case you discover any suspicious activities, make no doubt to contact or look for assistance from your financial institution instantly. You’ll inquire them to bolt the bank account and ask about the essential steps to recover the misfortunes.
6. *2767*3855#
It is a code to hard reset your Android gadget. Use this code after you back up all of your information or in case of a supreme crisis because it will wipe your phone clean, and erase all of your information. This code will also erase and reinstall the firmware.
7. Contact businesses
If you want to limit the harm of a call hack, Contact any financial administrations or e-commerce businesses that have your credit card or bank account data. Discover which exchanges you would like to debate together with your bank and, in a few cases, report for extortion.
Ways of protecting your phone from hacking
As said prior, there are numerous ways hackers can get to your phone and steal your information. Here is an outline of tips you’ll use to ensure that your phone isn’t hacked:

1. Use security protection
If you want to ensure your phone from hackers, use security protection. It is 100% conceivable. Moreover, it can be done openly and through the portable security app on your Android and iPhone. It ensures your maximum phone security against hackers.
2. Turn off the Bluetooth and Wi-Fi
Hackers can effectively access your phone using Bluetooth or a Wi-Fi association. In this way, if they are not in use, it would be superior if you just turn them off since they don’t grant you any caution at whatever point the hacker is making his or her moves. So turn off the Bluetooth and Wi-Fi if you don’t need them; no hacker can get to your phone when it is turned off. It is typically an effective strategy for preventing hacking.
3. SIM card locking
SIM card locking is an essential way of protecting your phone from being hacked. Guarantee that you simply put the password on the SIM card, and you’d have protected it from being hacked. Setting this code is generally simple, particularly if you’ve got an iPhone. You must go to the settings, then cellular, and enter the SIM pin. To empower the look, put your existing pin. If you’re using Android, go to the settings, lock the screen, and security alongside other security settings. After that, set up your SIM card lock. So also, you’ll be able moreover to empower the choice of locking your SIM card.
4. Encrypt your device
Guarantee that your phone is encrypted. If you encrypt your device, it limits hackers and ensures your vital data, messages, and calls. To verify that your phone is encrypted, it is fitting for an iPhone client to visit the passcode and touch ID. After that, scroll to the bottom as you affirm that the information is completely empowered. Moreover, Android clients don’t get to go through any bother since they have automatic encryption, but this depends on the phone’s type.
5. Store the phone in your possession
Hackers can effortlessly take basic data when they get to your phone; consequently, it is crucial to always store the phone in your possession.
Cell phone spy app
I am presenting the foremost common way to hack a smartphone nowadays – using a cell phone spy app. Essentially by looking at how can someone hack your phone on Google, you’ll discover numerous apps available with spying capabilities.

There could be an effective app – SPY24. It is one-sided to classify it as spyware. “How can I monitor my child’s phone?” It’s a very common question among parents. SPY24 is one of the leading apps to screen child’s phones so that parents can secure their kids’ avoidance from the harmful online environment. But due to its uncommon highlights like the inaccessible following, it is broadly used to spy on someone’s cell phone.
What can SPY24 do?
You will be surprised to know that today’s spy apps can let you check fundamentally everything on the target phone. They can be set up effectively, and there’s no chance of getting detected. Indeed as a parental observing app, SPY24 comes with numerous progressed capabilities.
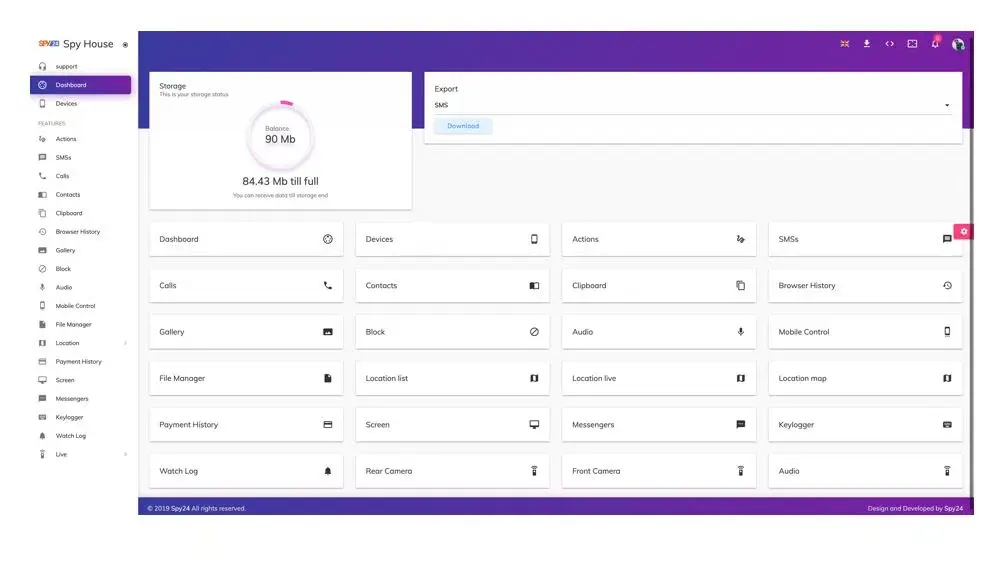
- It can screen 30+ distinctive records. The list incorporates content messages, call history, browser history, photographs, WhatsApp, Facebook, Instagram, Snapchat, Skype, and more.
- It can remotely track someone’s GPS area.
- It can record the approaching and active phone calls made on an Android phone.
- It can capture the current screen action.
- It can assist you to access the environment of the target device.
- It can record phone calls and the phone screen of the target phone.
- It can check video apps like YouTube and Tik Tok.
with all these unique features, SPY24 is a great monitoring app for android smartphones.
Conclusion
According to this article, getting access to your data by simply a call hack is more than incomprehensible for hackers. You must know that hacking can be challenging, but reacting to the call can make it simple for criminals to get to your phone. Subsequently, it is nice to guarantee that you just take safety measures all the time.
So, what can somebody do along with your phone number? Well, there’s a distinction in alternatives on the matter. It is no big deal if you get calls or texts from an unknown number. The core of the matter is that you just do not accept the given data effortlessly. It is additionally imperative to know the conceivable ways to hack one’s phone. We have talked about each strategy in detail. Trust it helps.
FAQs
1. How do hackers call?
Professional hackers can use dedicated technologies that search for vulnerable mobile devices with an open Bluetooth connection. Hackers can pull off these attacks when they are within range of your phone, up to 30 feet away, usually in a populated area.
2. Can someone hack my phone without my phone?
Yes, unfortunately, people can access and even control your phone remotely. There are plenty of spyware apps and bugs that let people hack into your phone without you even knowing about it. It’s usually through certain links or credentials that hackers do this.
3. What does #002# do to your phone?
Code ##002#: To Fix Redirection and Diversion
It is another valuable code you can use to check if your phone has been hacked. It switches off any shape of covered-up redirection from your smartphone.
4. Can someone see my camera?
Yes, your phone camera can be simply hacked. Hackers can use your smartphone’s camera to hack your gadget, spy on you, and get to your phone without your information!
5. What can hackers hack?
- Hijack your usernames and passwords.
- Steal your cash and open credit card and bank accounts in your name.
- Ruin your credit.
- Request unused account Individual Distinguishing proof Numbers (PINs) or extra credit cards.
- Make purchases
- Use and maltreat your social security number.
- Sell your data to other parties who will use it for criminal or illegitimate purposes.




