L3MON (GitHub) Download Hack Android Mobile Remotely RAT
L3MON is a tool that enables remote management of Android devices. It is cloud-based, meaning that it is hosted on servers accessible over the internet. The tool is designed to work as an Android RAT (Remote Administration Tool), which means it can be used by an attacker to gain control of an Android device remotely.
The way L3MON works is by creating an APK payload and delivering it to the target’s phone. Once the payload is installed on the target device, the attacker gains control of the device and can access it remotely. The web-based interface provided by L3MON enables the attacker to interact with the targeted phone, accessing its files, making phone calls, sending messages, and more.
L3MON Features: A Cloud-Based Tool for Managing Android Devices
L3mon is a tool with various features that allow remote management of Android devices. The tool has several functionalities, including GPS logging, microphone recording, access to contacts, SMS logs, and the ability to send SMS messages. It can also access call logs, view installed apps, view stub permissions, log live clipboards and notifications, and view WiFi networks (logs previously seen). Additionally, L3mon has a file explorer and downloader, command queuing, and a built-in APK builder.
Here are the features offered by L3MON:
- Access to Contacts
- View Installed Apps
- Call Logs
- SMS Logs
- Ability to Send SMS Messages
- GPS Logging
- Microphone Recording
- View Stub Permissions
- Command Queuing
- WiFi Network Viewer (displays previously accessed networks)
- Real-time Notification Logging
- Real-time Clipboard Logging
- File Manager & Downloader
- Built-In APK Builder.
How to Install and Configure L3MON for Kali Linux: A Step-by-Step Guide
- Update your system before starting the installation process.
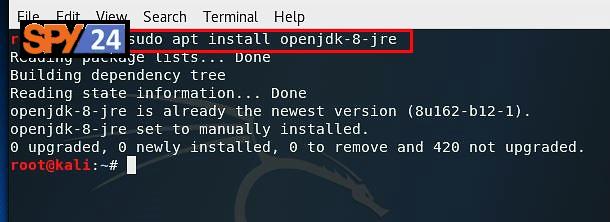
- Install Java Runtime Environment by running the command “Sudo apt-get install OpenJDK-8-JRE”.
Prerequisites
Improve a Windows or Linux PC.
- Download Kali Linux ISO File and keep it ready on your host machine
- Download and Install Virtual Box on the System.
Use a server to monitor multiple devices continuously.
- Check the JRE version by issuing the command “java –version”.
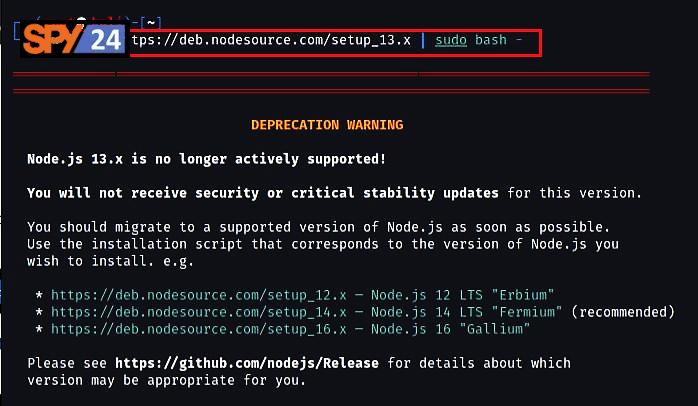
- Download the NodeJs package into your system by running the command “curl -sL https://deb.nodesource.com/setup_13.x | sudo bash –”.
- Install NodeJs by running the command “sudo apt-get install -y nodejs”.
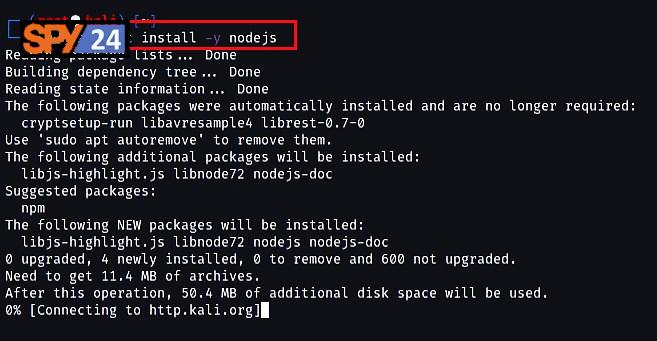
- Install the pm2 process manager by running the command “sudo npm install pm2 -g”.
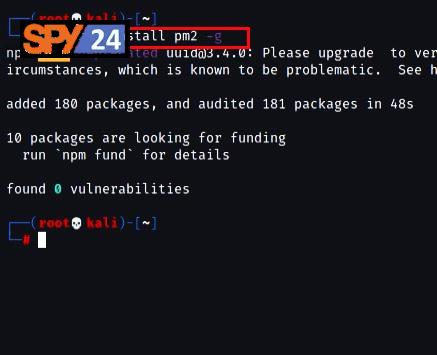
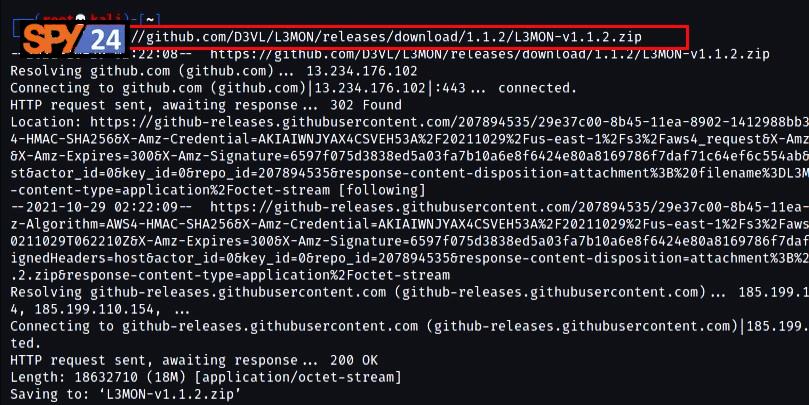
- Clone the L3MON tool from Github by running the command “wget https://github.com/D3VL/L3MON/releases/download/1.1.2/L3MON-v1.1.2.zip”.
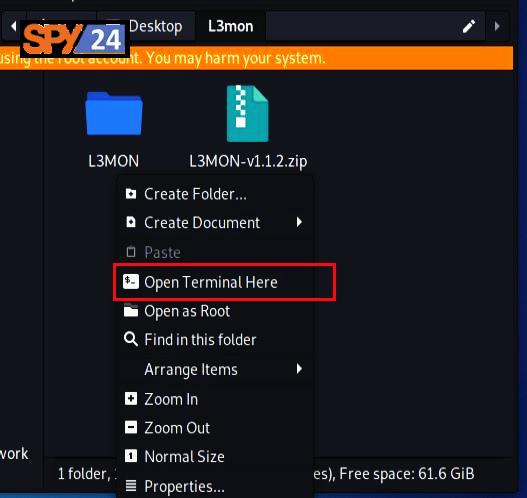
- Move and extract the L3MON zip file to a new folder on your desktop.
To install L3MON on Kali Linux, once you download and extract the L3MON zip file, you need to open a terminal and navigate to the extracted folder. You can do this by right-clicking on the extracted folder and selecting “Open in Terminal”. This will open a terminal window in the correct directory for you to run the necessary commands to install and configure L3MON.
- Install dependencies for L3MON by running the command “npm install”.
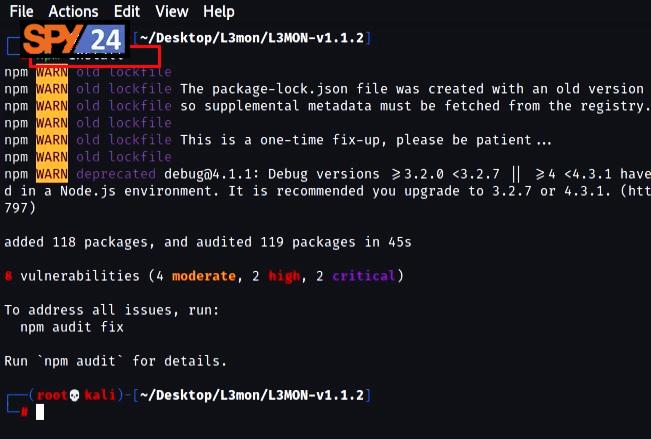
- Start the server by running the command “pm2 start index.js”.
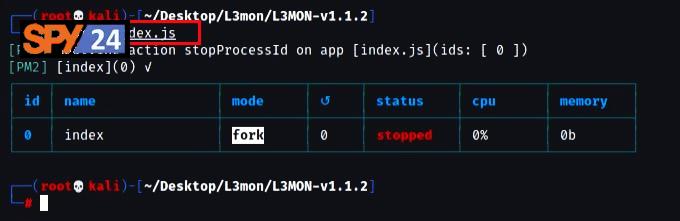
- Stop the server to set up a password for login by running the command “pm2 stop index.js”.
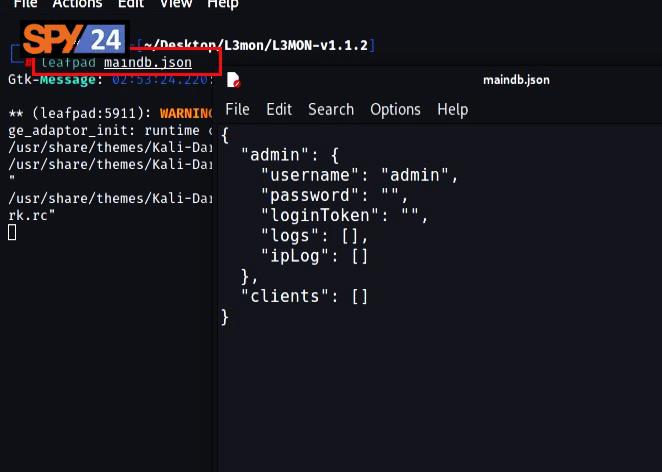
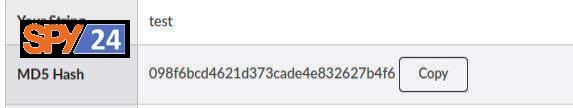
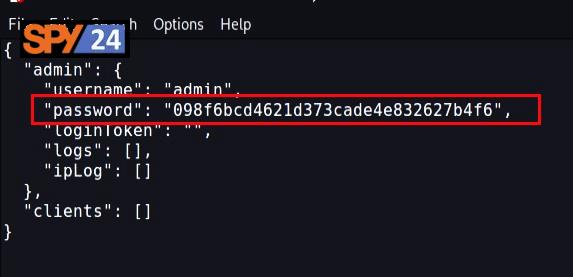
- Open the “JSON” file and set the login password by saving the MD5 hash of your desired password in the password field of the “maindb.json” file.
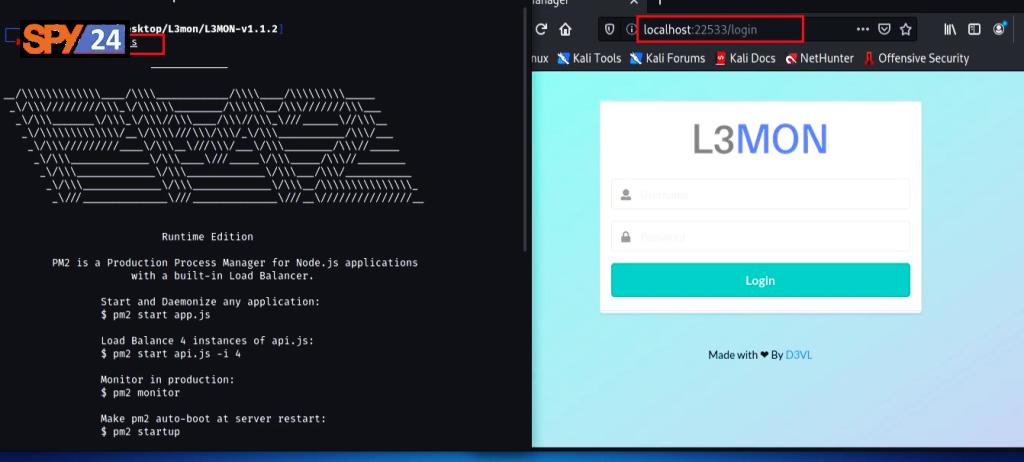
- Start the server again by running the command “pm2 start index.js”.
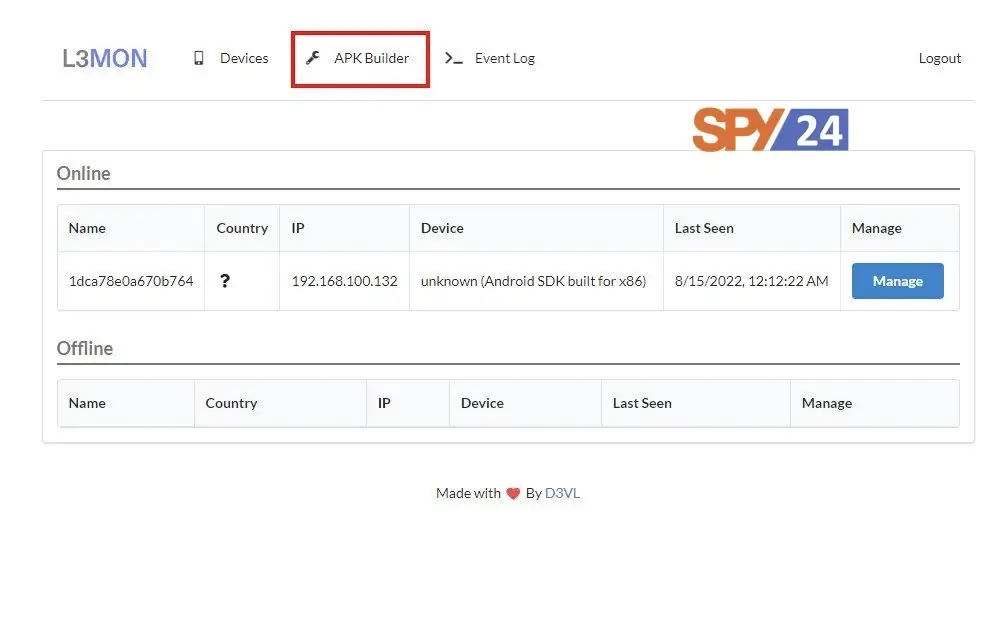
- Navigate to localhost in a browser with 22533 port to access the Android Management Dashboard and APK builder.
- Use the APK builder tab to create a payload and transfer it to the target’s android phone.
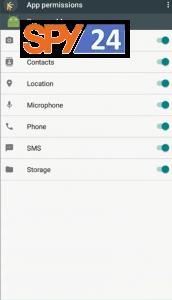
- When the victim grants all permissions and installs the malicious payload, their device will appear on the “Device” tab of the dashboard.”
- Click on the manage button to control the target’s device and easily spy on the victim’s Android phone.
L3MON is a powerful cloud-based Android management suite that can remotely spy on any Android phone over a local area network (LAN) or wide area network (WAN). By following the steps to install and configure the tool on Kali Linux, creating a malicious payload, and transferring it to the victim’s phone, you can gain complete control over their device. Once the victim installs the payload and grants all necessary permissions, their device will be listed in the “Device tab,” and you can start spying on them. Using the L3MON tool, you can easily access and view sensitive information such as contacts, messages, and call logs.
L3MON Summary
- L3MON is a popular remote Android management tool that has gained attention among cybersecurity enthusiasts and hackers due to its ease of use and powerful features.
- L3MON can be used for a variety of purposes, including monitoring employee activity on company-owned devices, parental control, or malicious activities such as spying on unsuspecting victims.
- One of the main advantages of L3MON is that it is cloud-based, which means that it does not require any additional hardware or infrastructure to operate.
- L3MON’s APK builder feature allows users to create custom APKs that can be used to install the L3MON agent on the target device. The APK builder supports a wide range of configuration options, such as the ability to hide the application icon or enable root access.
- L3MON’s management dashboard provides users with an easy-to-use interface that allows them to monitor and control all connected devices from a single location.
- L3MON’s advanced features include the ability to capture screenshots, record audio, and video, and remotely access the device’s camera and microphone.
- L3MON is constantly updated with new features and bug fixes to ensure that it remains a powerful and reliable tool for remote Android management.
- It’s worth noting that while L3MON may have legitimate uses, its potential for abuse makes it a dangerous tool in the wrong hands. As always, it’s important to use these kinds of tools responsibly and with respect for other people’s privacy.
By providing the correct login details you can access the main page of the panel form where you can see the connected apps and at the top, you can go to the app builder to create a malicious android app as shown in the image below.
Generating malicious payload
In the image below, you can see that you only need an IP address and a port number to generate the apk. If your target is on the same network as you, you are supposed to use your local IP address, and if you want to access the target device over the Internet, use your public IP address.
After providing the required information, just click build, sit back, and wait for L3MON to finish generating the app. Once finished, an option to download the app will appear.

Installing the malicious application on the target device
There is no specific way to install the malware on the target device. To avoid detection by antivirus programs on the target device, you can search for a guide to trick the victim into installing the app. The success of this step depends on how you’ll know your target and the technique you use to trick your target into installing the app.
Accessing information and managing your target device
At this stage, you have already installed your application on your target device. You can now remotely access your target device and issue commands to control the device, provided you are on the same network as your target or your target is connected to the Internet. This image shows the connected devices on the L3MON admin page.
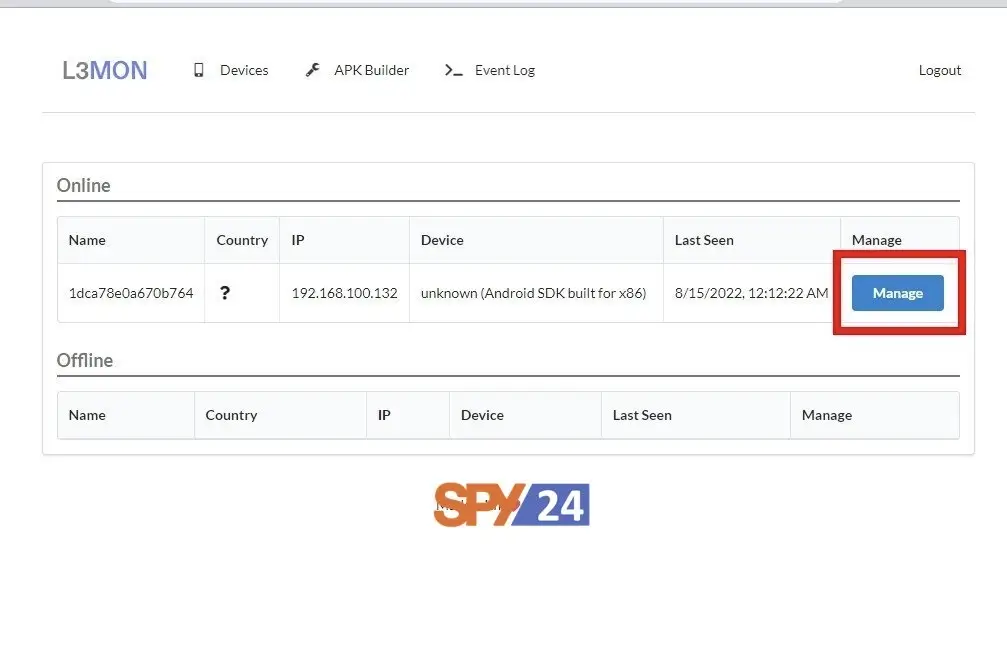
In the picture, you can see that L3MON has two categories of devices, devices that are currently online and devices that are offline at that time. When you click on the manage button, you can access various types of information on the target device.
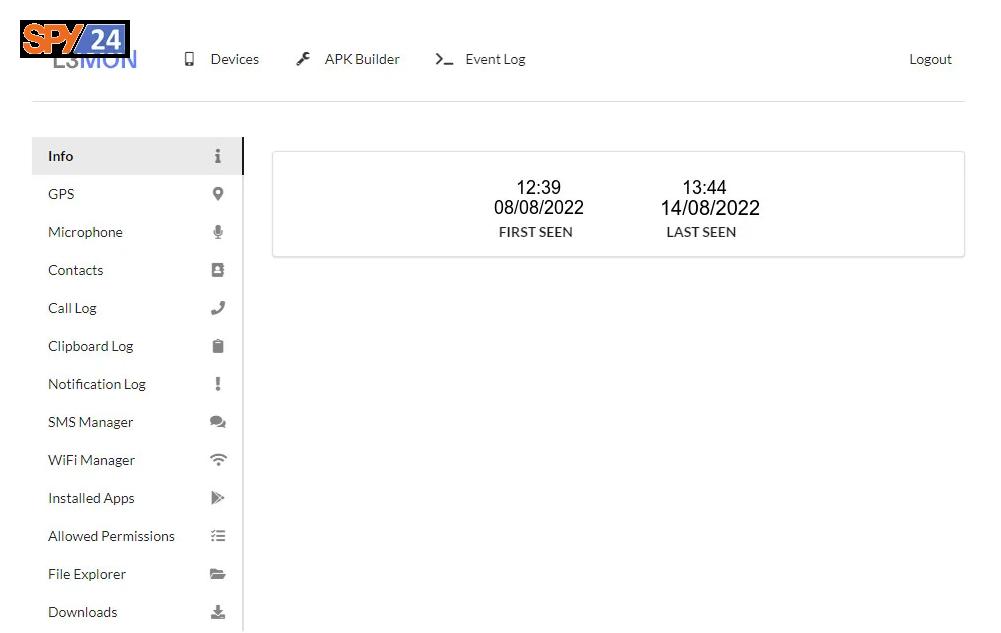
What Information You Can See?
You can see when the device was connected for the first time and when it was last connected.
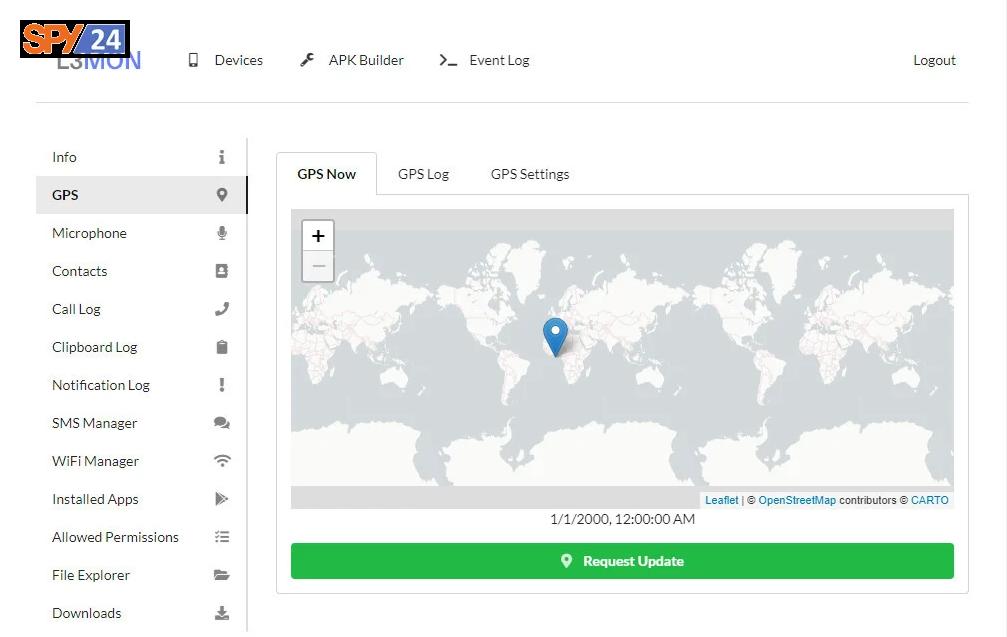
GPS information
You can view the GPS information of the device and the GPS report of previous locations, and you can set time intervals to check the location of the device.
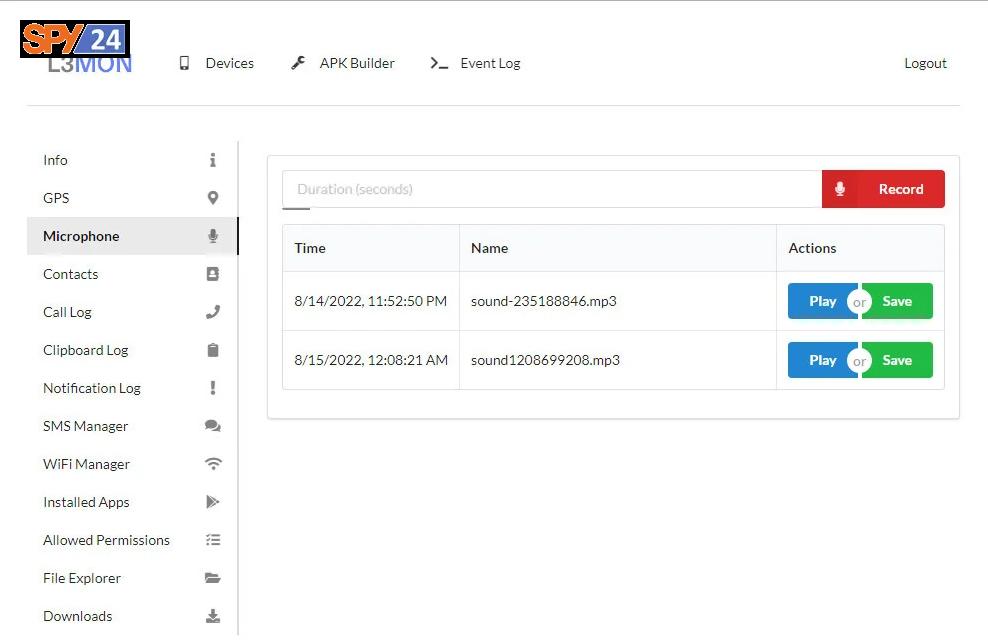
Access Microphone
Using the microphone option, you can remotely record and listen to what is around the target device.
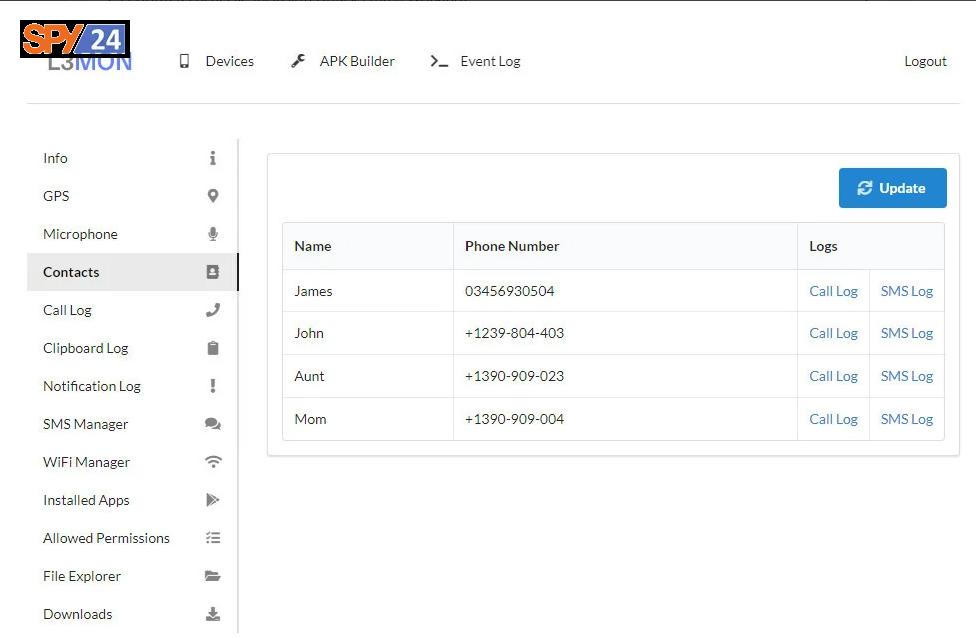
Access Contacts
You can see the saved contacts.
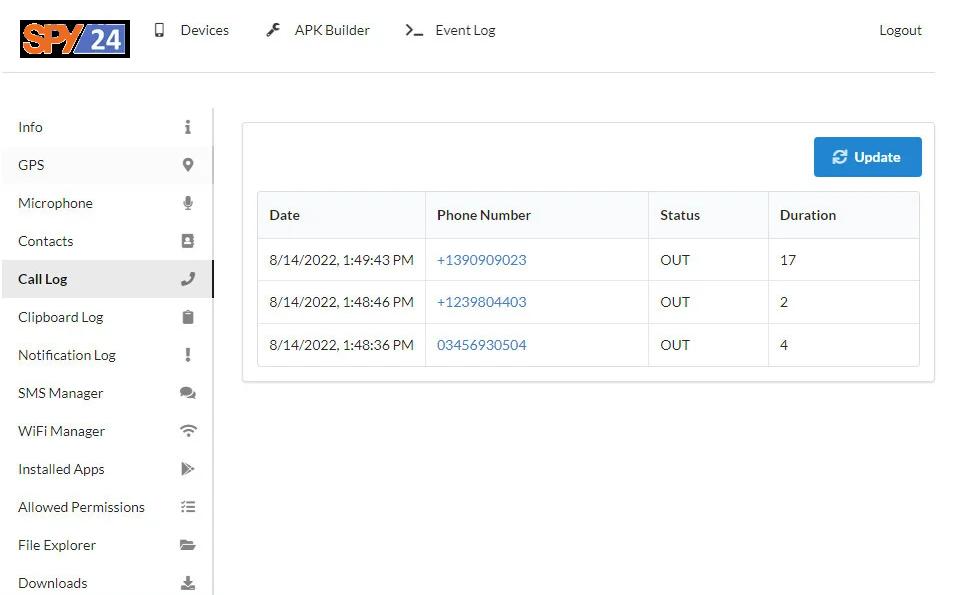
Call logs
Accessing the call logs available on the target device.
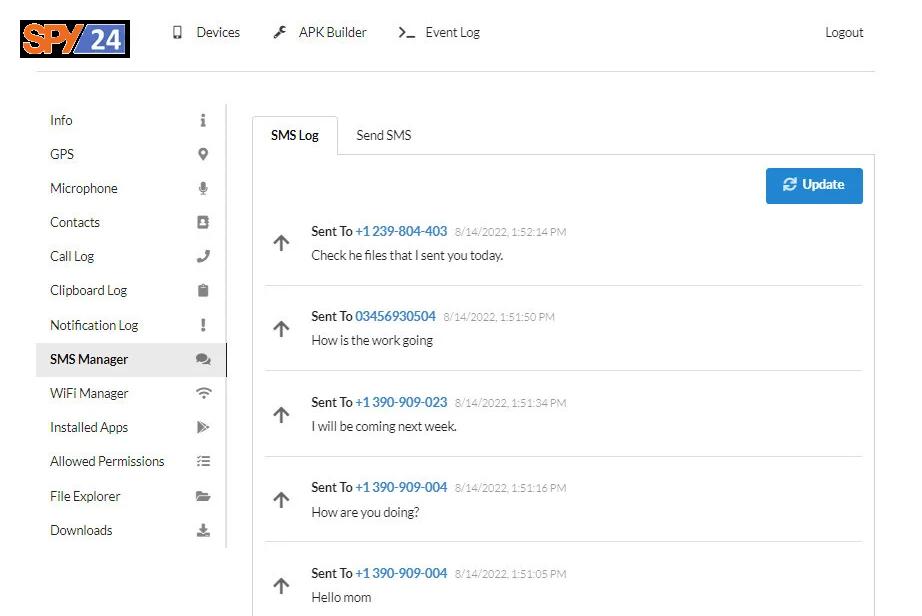
Access SMS Manager
By using SMS management, you can see the messages received and sent by the target device. You can also send SMS from the L3MON admin panel.
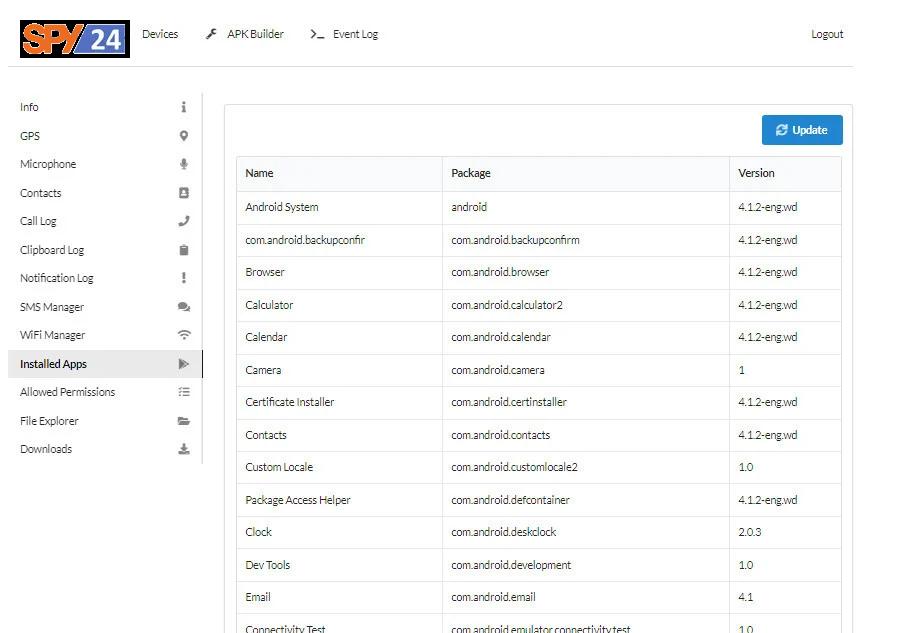
Access Installed applications
Checking the installed applications.
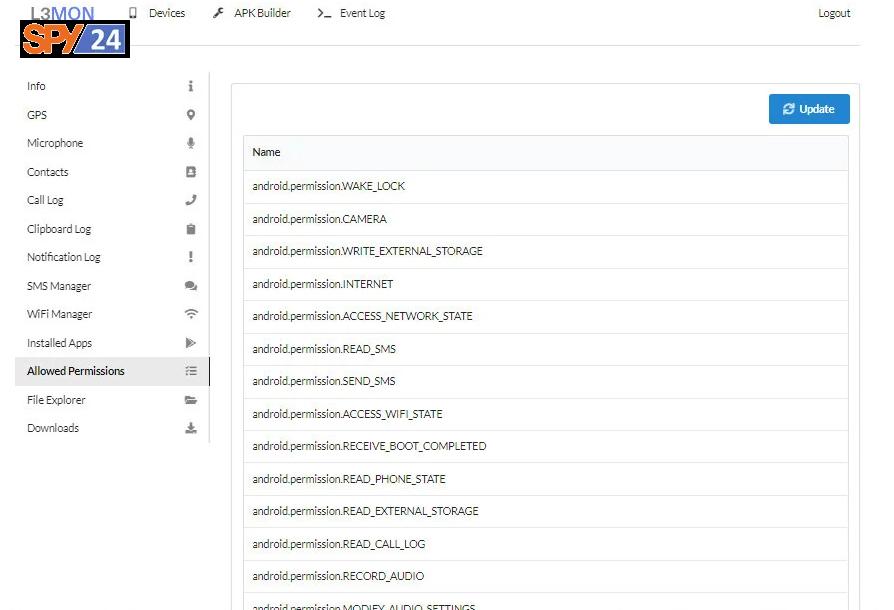
Allowed permissions
You can see the allowed permissions.
Android remote monitoring tools are expensive, especially where we monitor more than one device. A lot of resources are used to make sure the monitoring system is running and performing as expected. L3MON android management suite being open source cuts down the cost of monitoring these devices as it is available for free. But for most people who don’t have enough knowledge, it’s hard to use and also you just can monitor android devices which is a big negative point. With a monitoring program like SPY24, you can monitor any device you want, and the most important thing is that SPY24 is easy to use.
Are You Looking for a Cell Phone Monitoring App? Check Out SPY24
What Are SPY24 and What Are Its Features?
SPY24 is a powerful cell phone spy software that allows you to remotely monitor and track any smartphone or tablet. It offers a range of features, including remote control of a cell phone, keylogger, spy24 analytics, emails, online activity monitoring, recording of phone calls and surroundings, multimedia file and appointment tracking, and more.
One of the best things about SPY24 is that it comes with a 30-day free trial, allowing you to test out its features and functionality before committing to a subscription plan. Additionally, SPY24 is untraceable and offers over 100 functions, many of which are exclusive to the software and cannot be found in any other Windows spy program.
Some of SPY24’s features include:
SPY24 app as a monitoring and tracking app gives you these accessibilities:
- Remotely Control a Cellphone: If you want to know how you can control a phone from afar, SPY24 phone tracking can help. With this feature, you can change how things work on the targeted phone and send commands to it from a distance.
- KEYLOGGER: Instant Messaging apps like WhatsApp, Telegram, Instagram, Messenger, etc. can have their Keystrokes watched. (You can see what they are typing on their keyboard before they send it out).
- 24/7 Instant Alerts: Get instant alerts whenever certain words are being sent by the targeted device through any social media. This can be for protecting people we care about from both online and offline abuses.
- SPY24 Analytics: Get a summarized history of your most repetitive activities in a specific period also includes call time activity punch cards for each time a call has been made through the device in a certain hour or a day of a week.
- Emails And Online Activities: Keep an eye on your targeted person’s emails that they send or get, and the websites they visit with this amazing feature. You can also check their bookmarks and find out how often they visit them.
- Record Phone Calls and Surroundings: With this feature, you can find out about people’s ambitions and purposes whenever they have their phones around them. You can hear them talking live or listen to their phone call recordings without them noticing.
- Multimedia Files and Appointments: Check all photos and videos they have saved on their phones and tablets. Also, monitor all appointments scheduled on the target devices.
- SMS/MMS: This feature allows you to read all the messages sent or received on the targeted device.
- Calls: This amazing feature lets you view all incoming, outgoing, and missed calls of the targeted device; Not only that, but you can see the duration, the date, and the time that they happened.
- GPS Locations: This Feature lets you track the position of the targeted device LIVE and you can keep track of the places that the targeted person visits anytime.
- Remote Control: With this feature you can fully control the phone, like, deleting data, making it vibrate, taking pictures, and many more.
- Live Viewing: With this feature, you can view whatever happens on the screen and around the phone without being noticed.
- File Manager: With this feature, you can browse the file manager application of the targeted device freely and view all the existing files without being noticed.
- Schedule Restriction: This feature forbids the targeted person from using their phone by blocking access to all the applications.
- Calendar: This feature lets you check out the events added to the calendar and alerts you whenever a new event is added to the targeted device’s calendar.
- Contacts: This feature lets you view the targeted phone’s contacts, edit, or even delete them and you get alerted whenever a new contact is being added.
- Analysis Tools: This feature lets you generate a PDF or Excel report about the targeted person’s activities. You should know whom your targeted person is talking to, which games they play the most, etc.
- Instant Messaging: SPY24 grants you access to the targeted phone’s incoming and outgoing messages and from many Instant Messaging Applications (Facebook, Instagram, WhatsApp, Telegram, etc.) without the targeted phone needing to be rooted or noticing your presence.
Why Is SPY24 The Best Windows Spy Software
SPY24 is the only monitoring program for Windows that is untraceable. There are several monitoring programs available, but only one has the level of quality that comes with expertise. Our Windows spy program has over a hundred functions, which far exceed the capabilities of any competitor product. Many of these functions are exclusive to SPY24 and cannot be found in any other Windows spy program. We are the only computer monitoring program that includes a real-time screen monitor.
Conclusion
Overall, SPY24 is a highly comprehensive and advanced monitoring software that is suitable for parental and employee monitoring needs.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.