ATM Hacking: Hack an ATM Machine with Blank Card

Want to hear something both exciting and chilling? An in-depth research report published last year found that most ATMs can be hacked in 20 minutes or less. Even scarier, 85% of ATMs tested for research allow attackers access to the network, and over 58% have vulnerabilities in network components or services that can be exploited to control the ATM from far away.
All of this just means that ATMs are much more vulnerable than we think. Considering that they not only hold huge amounts of money but also contain valuable user data, this can be a pretty scary thought. Especially since most of us don’t know how vulnerable ATMs are.
We scoured the dark web to see what information was available on different ATM hacking strategies. We have found rich and varied information on different strategies and have tried to summarize the basics in this article, in the hope that it helps the reader better understand what is going on and how alert they should be.
How to hack an ATM machine
There are three fundamental strategies to hack an ATM machine:
Strategy 1: ATM Malware Card
This is likely one of the foremost well-known strategies that ATM hackers utilize to exploit vulnerabilities. There are sites on the dark web that provide a complete malware pack to the client which incorporates the ATM Malware Card, PIN Descriptor, Trigger Card, and an Instruction Guide.
Strategy 2: USB ATM Malware
This is another predominant strategy for machines that support Windows XP. It empowers hackers to dispense all money from the ATM by utilizing the Malware-hosted USB drive to infect the machine.
Strategy 3: ATM Hacking Appliances
There are several ATM Skimmer Shops on the dark web that offer different ATM Hacking tools such as EMV Skimmer, GSM Receiver, ATM Skimmer, POS, Gas Pump, Deep Insert, etc. Numerous shops offer a package of these diverse devices together.
Ways To Protect Yourself
Adopt these easy habits to reduce your chances of becoming a victim of debit card fraud:
- Be careful about online money hacks. Shop and bank on secure websites with private Wi-Fi.
- Monitor your accounts. Review your reports and sign up for text or email alerts to quickly detect debit card fraud attempts.
- Don’t ignore data breach notifications. Most identity theft victims receive a warning that their accounts may have been hacked, but they do nothing. If you get one of these messages, change your PIN and ask the provider to change your debit card number. You can also ask one of the major credit card bureaus to add a fraud alert to your record.
- Check card readers and ATMs. Do not use card slots that appear dirty or show signs of tampering, such as scratches, glue, or debris. And avoid machines with strange instructions, such as “Enter PIN twice.”
- Cover your card. When using a debit card or entering a PIN at an ATM, cover your view with your other hand. Go to a completely different place if suspicious people are hanging around the ATM and if your card is stuck, notify the financial institution directly instead of getting “help” from strangers.
The tools you need to do it
- An ATM or ‘Automated Teller Machine’ skimmer
- A small camera
- A laptop or other computer

ATM Card Virus
Tyupkin is an ATM malware. This is a piece of malware that allows cybercriminals to empty ATMs through direct manipulation. This malware was detected by Kaspersky Lab as a Backdoor.MSIL. Tyupkin affects ATMs of a major ATM manufacturer running 32-bit Microsoft Windows.
ATM SKIMMER SHOP (ALL IN ONE)
There are also online stores that offer bank hacking and money transfer service. These stores sell this kind of card. One such store is the ATM Skimmer shop (all-in-one), which sells devices that can be used for ATM hacking, such as EMV Skimmers, GSM receivers, ATM Skimmers, etc.
Hacking ATM: Advanced ways to Find Security holes by Anastasis Vesileiadis
How can criminals do ATM hacking and take money? Here are four advanced methods that show how vulnerable ATMs can be.
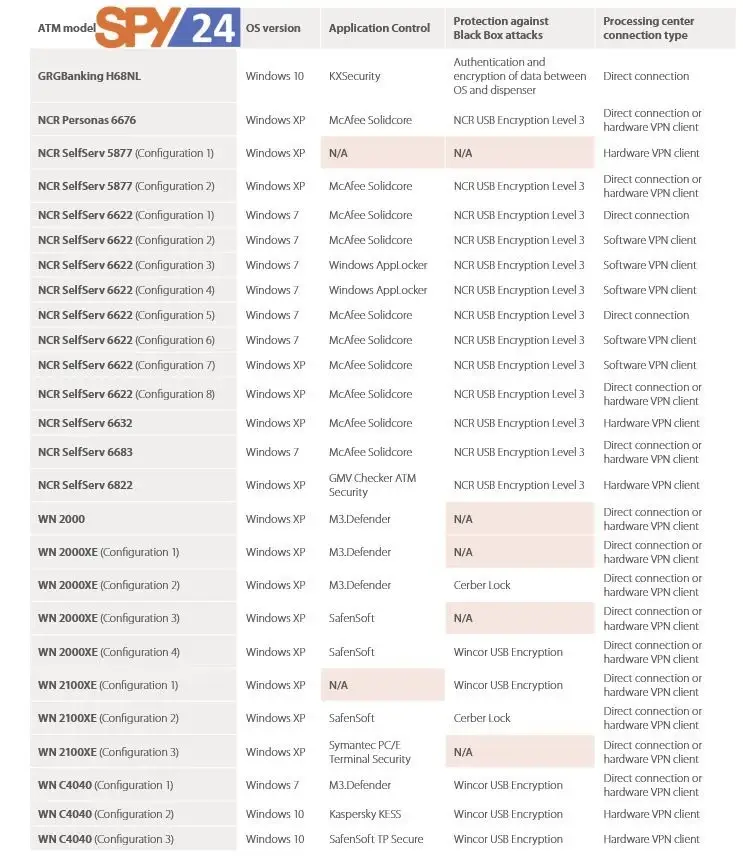
Method 1: Fake processing center
This method requires an attacker to access the cable connecting the machine to the network. Hackers disconnect the ATM from the bank’s network and then connect it to a device that acts as a fake processing center.
Method 2: Remote attack on multiple ATMs
This method involves an insider working at the target bank. Criminals buy keys from insiders to open ATM chassis. The key does not allow an attacker access to the cash trays but exposes the network cable. The hacker disconnects the ATM from the bank’s network and plugs in a special device to send all the data to its server.
Method 3: The black box attack
As described earlier, the attacker obtains the key from the ATM chassis and accesses it, but this time puts the machine into maintenance mode. Next, the hacker plugs the so-called black box into the exposed USB port. The black box in this case is a device that allows an attacker to take control of an ATM’s cash trays.

Programs to protect ATM
McAfee Solidcore and Phoenix Vista ATM are two such security solutions.
- McAfee Solidcore
McAfee Application Control prevents executables that shouldn’t be there from running in the ATM operating system.
- Phoenix Vista ATM
Diebold has purchased Phoenix Interactive Design Inc., the company that manufactures Phoenix Vista ATMs.
It is integrated into the software that ATMs use. It works by checking the integrity of the files. If an important file related to the application is modified or corrupted in any way, the system shuts down.

How ATMs are tested for security holes
As the number of ATMs increases, machines are vulnerable to hacking, theft, fraud, and more. Most ATMs still use Windows XP, making them easy targets for hackers.
We will look at the types of assessments we can perform to analyze the overall security of an ATM.
Vulnerability assessment and network penetration testing are related to operating system enhancement. Most ATMs run the Windows operating system. This operating system must be enhanced according to security best practices to reduce the attack surface for an attacker.
It can look at some of the following:
- Fixes and updates: Checks for the latest operating system and security updates.
- File system security is the rules that determine who can open important system files and folders.
- System Access and Authentication: Controls related to password and account lockout policies, user rights policies, etc.
- ATM activity control, security and application logs, control policies, event log permissions, and more are checked and recorded.
- Account configuration: user control group management, default user presence, visitor accounts, passwords, and expiration requirements.
Security check for the application:
This activity can be divided into two groups:
- Penetration testing of thick client applications
Most ATM applications are thick clients. We can perform application penetration testing on this thick client.
- App Design Review
In this activity, we can verify the security measures in the app.
A Blank atm card can be hacked
If you are wondering, “Is hacking an ATM machine with a blank card real?” then the answer is yes, of course, yes, if you know where to look.
And, of course, they won’t work if you’re wasting your time with sites or places that are just blank atm card scams.
Price list for cards that can hack ATMs (blank atm cards)
Blank ATM Cards have many variations and they also differ in cash amount. So they have different costs.
After finding a reliable source to buy these cards, you can check the card type and price list.
How do I receive my card after payments?
We use DHL to send blank cards. It takes about 7 days for standard shipping.
To send you a card, we need your full name and address.
ATM Hacking
On some machines, cellular connections to the processing server can be hacked using encryption keys found in the modem’s firmware. Default administrative credentials – username and password are both “root” – gave full Telnet access to one machine and could brute force weak administrative credentials on a web interface remote of the same model.
How to hack an atm
ATM hacking is extremely easy. Here are a few ways:
1. Opening up an ATM cabinet
Once you’ve opened the cabinet and have access to the computer’s input ports, there’s not much distance between you and the cash jackpot.
2. Installing ATM Malware
Most ATMs run security applications to prevent the installation of malware. Four of these applications, including both created by McAfee and Kaspersky Lab, have their security flaws. Another security application stored the administration password in plain text.
3. Unsafe Mode
You can simply reboot the machine in debug or safe mode, which often leads to a jackpot.
4. ATM black box connection
You don’t need to access the ATM’s computer to get money. You can quickly connect a “black box” – a Raspberry Pi or similar machine running modified ATM diagnostic software – directly to a cash machine on the safe to vomit banknotes.
Hacking an atm clone blank card
Hacking ATMs is nothing new or surprising anymore. With the improvement of ATMs like Diebold atm, DEFCON atm, and Wincor Nixdorf atm, it is not easy to cheat an ATM.
Although there are tutorials, tips, and tricks on how to hack an ATM machine online, none of them work. The people who break into the ATM won’t tell you how they do it.
So, can you hack an atm?
Yes, it is possible to hack an ATM machine and get money from it for free, but not by any of the methods above. There is no master password or hack code needed to break into an ATM.
How to hack an atm using the skimmer to hack an atm
If you ask “How do ATM skimmers steal PINs?” here’s your answer:
Some ATM skimmers are inserted into card readers, located in terminals, or located along exposed cables. Pinhole cameras installed on ATMs record a customer entering their PIN. Pinhole camera placement varies widely. In some cases, a keyboard overlay is used instead of a pinhole camera to record the PIN.
What is the dark web and how do you access it
The dark web is a part of the Internet that is only accessible by special software and it is often used for illegal activities.
Do you want to sell money?
We don’t sell money, no. If you read our article carefully you will see how it all fits together.
Does my country offer this service?
Yes, our service is available worldwide.
How do I get my card when I’ve paid for it?
We ship by DHL and normal shipping takes about 7 days. Your full name and address are all we need.

Conclusion
In this blog post, we have mentioned easy-to-implement ATM attacks and corresponding measures to prevent and detect them. Most prevention and detection measures are not that different from those needed on office networks or other digital environments.
The challenge is to apply these measures qualitatively and ensure maximum coverage. This is a recurring problem that we can only solve if we focus and set goals.
As in real life, risks must be accepted and solutions will never be perfect. It is hoped that by adopting one solution at a time and ensuring that the next solution fills the gap of the previous solution, we can bring the level of security to a level we are willing to accept.
SPY24- All in One Spy app
If you’re looking forward to an advanced tracking app and SMS hack, we offer SPY24.
SPY24 is quick and basic to install in straightforward steps:
- Download the app.
- Create your account by entering your mail address and enrolling your account.
- Select your device type; Android or iOS.
- Choose your plan from the alternatives accessible.
- Enter your payment details and affirm payment.
- Once you’ve completed your buy, full installation instructions are sent to your enrolled email address.
- Complete the installation procedure, and you’re all set!
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
FAQs
Which malware is used to hack ATMs?
Tyupkin is a piece of malware that allows cyber criminals to empty cash machines via direct manipulation. Tyupkin affects ATMs from a major ATM manufacturer running Microsoft Windows 32-bit. First, hackers gain physical access to an ATM and insert a bootable CD to install the malware code named Tyupkin.
How does ATM Jackpotting work?
ATM jackpotting occurs when a criminal gains physical access to an ATM and instructs the ATM to dispense cash until the ATM is empty.
What do most hackers use to hack?
Some of the most famous hacking tools in the market are Nmap (Network Mapper), Nessus, Nikto, Kismet, NetStumbler, Acunetix, Netsparker, Intruder, Nmap, Metasploit, Aircrack-Ng, etc.
Can you get money out of an ATM without a card?
Cardless ATMs—or contactless ATMs—allow you to access your account and withdraw money without a physical card. To use the cardless option at the ATM, you’ll typically need your financial institution’s app or your card information stored in your digital wallet.
Can ATMs be tracked?
The ATM Tracker is a fully automatic solution that silently and immediately notifies law enforcement of the attack as it occurs. ATM Tracker tracks the ATM or Cash Machine, cash inside, and criminals during their escape.
How To Become A Hacker In 2023 – Step By Step Guide For Beginners
A hacker is someone who finds vulnerabilities in a computer system or network by gaining authorized or unauthorized access to the said computer or network. There are three types of hackers namely white hat hackers, grey attackers, and black hat hackers. A great heart hacker is a hacker who employs malicious means to gain access to a computer and network in order to discover vulnerabilities. The fifth step in the process of becoming a hacker is to understand server and client-side attacks. Understanding these types of attacks will help you understand how to initiate and stop them when necessary. If you want to take hacking seriously and be very good at it then you’ll need to learn to program. These are the main steps you’ll need to follow if you plan on becoming a hacker: follow these steps and also get your hands on the popular hacking tools. The type of hacker you intend to be will depend on your own morals and principles but have in mind that the black and grey hat hacking is illegal and might get you into serious trouble when caught.
DEF CON 18 – Barnaby Jack – Jackpotting Automated Teller Machines Redux
The attraction to target ATMs is fairly obvious, but for myself, it’s kind of part of a bigger picture and a bigger plan. Next exploring systems that when compromised have direct and immediate consequences is my goal. The goal of the talk is to spark discussion on ways to remediate and fix the vulnerabilities I’m going to be demonstrating. The process of finding vulnerabilities is always more interesting, so stand-alone ATMs are easy to get ahold of, like anything on the internet. But getting atms delivered to your house on the other hand is interesting so I’m going to discuss attack methods for both standalone and hole-in-the-wall ATMs. I’ll go over walk-up style attacks, but then shift focus to the far more important vector in my opinion and that’s the remote attack. The presentation should not really be a full-blown technical tutorial, so I’m going to be following up later with a white paper that goes into more technical details. But rather than digging deep into the ins and outs of Windows CE internals, I somewhat up the sum up the security hurdles I faced with this quote: “we were concerned about protection, but not about security.”
The use of hardware, such as buggies and things that nature has nothing to do with, is used to gain access to the file system. I will be demonstrating a simple attack using a JTAG cable to access the firmware. Speaking of JTAG, I learned a valuable lesson when I accidentally wiped out a massive chunk of the firmware. Using explorer, we can copy off the files for reverse engineering. We can modify the registries or the explorer will always boot remotely. The next step is to set up or more sort of user-friendly debugging environment so as to debug Windows CE applications. I have active sync, so the goal is to execute code on the ATM machine. The tech behind the cash dispenser is housed at the very least by a safe, even if you take the cheapest option. If you spend more, you can get some fairly heavy-duty vault-style protections. The motherboard, on the other hand, is protected by one key fits all lock. This is standard practice.
Dillinger is an atm attack tool that can execute code or load software remotely. The name is derived from the bank robber, Vin diesel. Dillinger was designed for Intel and Arm, but it turns out that Conroe x86 is actually a pretty rare and basically nonexistent atm world. The code for interfacing the atm has to be customized for different atms as they all use different peripherals and nonstated protocols for communicating. Atm vulnerabilities allow for the need to replace the entire firmware in all the different executive bills. I can make these patches permanent which is far more reliable than doing it manually. It’s also a lot easier on Arm as every instruction is 32 bits long, so I place hooks at the card reader, the pin pad, and the parser that handles the remote configuration commands.
Scrooge connects to the ATM, sends authentication bypass success, initializes a software upload, and now Scrooge is actually uploading to the ATM. The show is set in a Metacafe on 80mm as I said there are two ways to pop up this remote menu–by the commuter loot cards and by a special key sequence. Let’s try it. The attack on the other ATM is to simply pop up in the compartment with your master key and set the usp that has the correct firmware. I’m not very good at this, but should hopefully be within three signals so that’s the attack essentially carried out on that one. The obvious physical countermeasure of course is to prevent the walkup. Windows CE 5 implementing the trust environment is the industry for as it should be code has to be introduced into the build and I think the option to implement a secure environment should be made a lot easier. What can do to prevent the remote attack? Disable our ms high chance you’re not using that functionality disable it.
How hackers hack ATMs remotely
Cybercriminals often target bank staff with phishing emails if they access the email. This allows the hacker to steal the worker’s digital credentials, which they then use to enter the bank’s network. This is known as lateral movement, and it commonly occurs in places where banks’ main networks and ATMs are not separate.





Getting rich in 3 days depends on how fast you can get the new
PROGRAMMED blank ATM card that is capable of hacking into any ATM machine,
anywhere in the world.
I got to know about this BLANK ATM CARD when I was searching for job online
about a month ago.
It has really changed my life for good and now I can say I’m rich and I can never
be poor again. The least money I get in a day with it is
about $50,000.(fifty thousand USD) Every now and then I keeping pumping money into
my account. Though is illegal,but there is no risk of being caught, because it has been
programmed in such a way that it is not traceable, it also has a technique that makes
it impossible for the CCTVs to detect you..
For details on how to get yours today, contact the hackers on :
spy24whatsapp no: +1 ****
Telegram: @spy24pro
signal: +1 ***
Contact them today and be happy