How to Hack Someone’s WhatsApp Account Using a Mac Address Spoofing Attack Example
WhatsApp is one of the most popular messaging apps in the world, but it also has its fair share of vulnerabilities. Hackers can use MAC address spoofing to break into someone’s WhatsApp account. They can also use other methods, like the WhatsApp Spy App, to remotely hack into someone’s account.
With either method, a hacker can steal all of the target person’s WhatsApp data. This includes their messages, contact list, and more. So, if you want to keep your WhatsApp account secure, be sure to learn about WhatsApp hacking methods and how to protect yourself against them in this article on SPY24.
How To Hack Someone’s WhatsApp Account Using A Mac Address
The MAC address spoofing attack is a hacking technique that is used by hackers to gain access to someone’s WhatsApp account. This attack can be used on both iOS and Android phones. Once the attack is completed, the hacker can access all the content in the target’s WhatsApp account. This includes all of the messages and contacts. The attack can be performed through a Wi-Fi network using the Mac address of the target’s phone. This address can be found in the phone’s Wi-Fi settings. Once the MAC address is known, the hacker can use it to gain access to the target’s WhatsApp account.
when the hacker has access to the target’s WhatsApp account, they can do a number of things. They can read all the messages that the target has sent and received, as well as see all the contacts in their WhatsApp address book. They can also send messages to the target’s contacts from their phone, or read any messages that their contacts have sent them. This attack is a highly dangerous one, as it gives the hacker access to all of the target’s personal information. They can use this information to stalk, blackmail, or harass the target, which can cause serious harm to them.

This is a very easy method to hack someone’s WhatsApp account. First, you need to find out your target’s MAC address. There are many ways to do this, such as by looking in their Wi-Fi settings or using a Wi-Fi analysis tool. Once you have the MAC address, you can enter it into a MAC address spoofing tool. The MAC address spoofing tool will then send out a signal that looks like a Wi-Fi signal. If your target’s phone picks up the signal, it will connect to the fake Wi-Fi connection and then give you access to their WhatsApp account.
How To Hack Someone’s WhatsApp Without An App or Software
The most common method of hacking someone’s WhatsApp without using an app is by performing a “spoofing” attack. This attack involves creating a fake WhatsApp account with the same phone number as the target’s own, and then sending a message to the target from the fake WhatsApp account.
This message will contain a request to “join” the fake WhatsApp account, and if the target accepts this request, the hacker will gain access to his or her WhatsApp account and be able to monitor all phone calls and messages made from it.
In order to perform a WhatsApp spoofing attack, the hacker will first need to get the target’s phone number. This can be done by either finding the number on a website or by having the target provide it to them directly. Once the hacker has the target’s phone number, they can then go through the process of creating a fake WhatsApp account with the same phone number. This is where the actual hacking takes place, as the hacker will now be able to access all of the target’s personal information. This includes their call logs, text messages, photos, and much more.
There are a number of different methods that can be used to hack someone’s WhatsApp account, each with its own benefits and drawbacks.
One of the simplest and most effective methods is to use a MAC spoofing attack. In this attack, the hacker sends out a signal that looks like a legitimate Wi-Fi connection. The target’s phone then connects to this fake connection and gives the hacker access to their WhatsApp account.
This method is easy to perform and is very effective at gaining access to a target’s WhatsApp account. However, if the target is aware of this method, they can take steps to prevent it from happening.
How to Hack WhatsApp with Chrome
The first step is to go to the Chrome Web Store and type in “WhatsApp Spy” or “WhatsApp Monitor” in the search bar. You will find many apps that will help you to hack someone’s phone. These apps allow you to access a person’s WhatsApp messages and view their phone calls with just a few clicks.
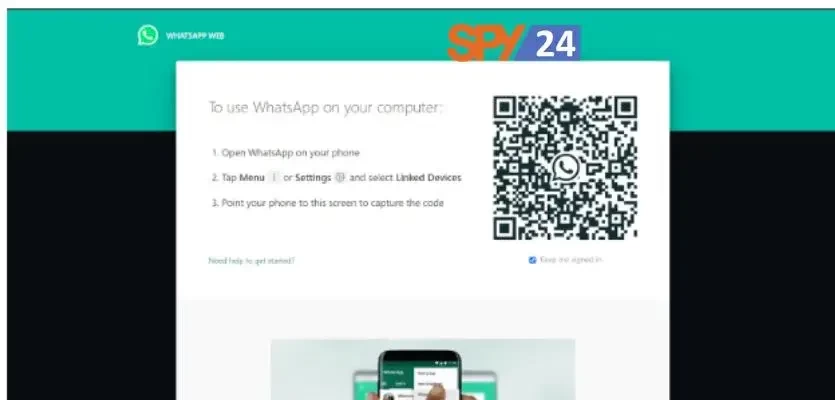
Step 1: Search for WhatsApp Spy or WhatsApp Monitor on the Chrome Web Store.
Step 2: Download and install the app.
Step 3: Open the app and enter the target’s phone number.
Step 4: Start hacking their WhatsApp account.
Step 5: Monitor their WhatsApp account and read all of their conversations in real-time
The Method of Spoofing With a Mac Device
When you’re hacking someone’s WhatsApp account with a Mac device, you’ll use MAC Spoofing. This is when you use the MAC address of the phone that you’re hacking to gain access to their WhatsApp account.
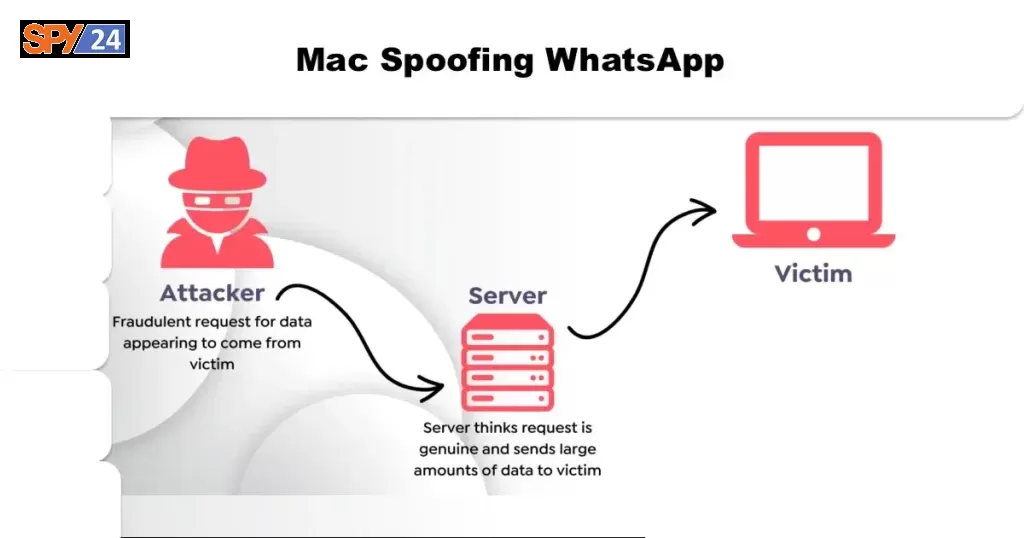
MAC Spoofing is an extremely effective way to hack someone’s Whatsapp account because the phone doesn’t detect the MAC spoof. So, it’ll always give the hacker access to their account.
The drawback to this method is that you must have the person’s MAC address. This isn’t always easy to get, but if you have access to their phone, you can usually get it.
Mac Spoofing WhatsApp
If you’re looking for a specific method to hack someone’s WhatsApp account, MAC spoofing is a good choice. This is an attack in which the hacker uses the victim’s MAC address to gain access to their account. This is a very powerful method because it gives the hacker access to all of the information in the victim’s account.
The most common method used to execute this attack is to use a MAC address spoofing tool to mask the victim’s real MAC address. This tool then sends the MAC address to the victim’s phone via a WhatsApp message.
Mac spoofing is a method that uses the phone’s MAC address to access its WhatsApp account. This method is extremely powerful because it gives the hacker access to all of the information in the victim’s WhatsApp account.
This information can include:
- Messages
- Photos
- Videos
- Call Logs
- Contacts
- Geotagging (if the victim uses it)
The hacker can then use this information to track the victim, blackmail or harass them, or steal their personal data.
How does MAC Spoofing Attack work?
In a MAC spoofing attack, the hacker uses the target’s MAC address to gain access to their WhatsApp account. This can be done by either performing a MitM (Man-in-the-middle) attack or by having the target provide the hacker with their MAC address directly.
Once the hacker has gained access to the target’s WhatsApp account, they can then use it to monitor all of their messages, calls, and location. They can also send messages to their contacts or use their account information for other purposes. One of the easiest ways to hack someone’s WhatsApp account is to use a MAC spoofing attack. This attack involves using the target’s MAC address to gain access to their WhatsApp account.

The main advantage of using this method is that it is easy to perform and doesn’t require any special equipment or software. The main drawback is that it relies on the target’s phone having an open network connection.
WhatsApp Spy App—Remotely Spy on WhatsApp Messenger
WhatsApp is one of the most popular messaging apps in the world. It is used by millions of people every day to communicate with family, friends, and coworkers.
A WhatsApp Spy app is an application that allows you to remotely spy on another person’s WhatsApp messages without them knowing. This app is very similar to a keylogger program, but instead of recording every keystroke on the user’s phone, it records all of their conversations instead.
There are a number of different WhatsApp Spy apps available on the market, but not all of them work the same way. Some WhatsApp Spy apps can be used for good or for bad purposes. For example, it can be used to keep an eye on your teenage children or to spy on your partner. On the other hand, it can also be used by criminals to stalk or harass their victims.
If you’re considering using a WhatsApp Spy app to spy on someone else, you should be cautious about the way you use it. It’s important to remember that this type of software can be a powerful tool, but it can also be used for nefarious purposes.
If you’re in the market for a WhatsApp Spy app, then you’ll probably want to choose one that is both easy to use and effective in its operation. The best WhatsApp Spy app in our opinion is SPY24.
This app lets you spy on any type of target from anywhere in the world. You can even remotely activate your phone camera and microphone without detection.
SPY24 has the best performance score on our market and is rated 4.8 stars by users on Play Store.
WhatsApp Spy Cross-Platform Messaging
WhatsApp Spy apps are designed to work on Android and iOS platforms. They can work on any device that has WhatsApp installed on it.
This means that you can spy on both iPhone and Android users.
WhatsApp Spy apps are extremely useful in many different scenarios. For example, you can use WhatsApp Spy apps to monitor your children’s social media accounts. You can also use them to spy on your partner or spouse if you think they are being unfaithful.
How To Use SPY24 App for WhatsApp Spying
SPY24 is a WhatsApp Spying app that can be used to track a person’s WhatsApp messages in real-time.
The app works by connecting to the target’s WhatsApp account and sending a MAC spoofed message to their phone. This message installs a Trojan virus onto the phone, which then collects all of the WhatsApp messages and sends them to an online server for monitoring.
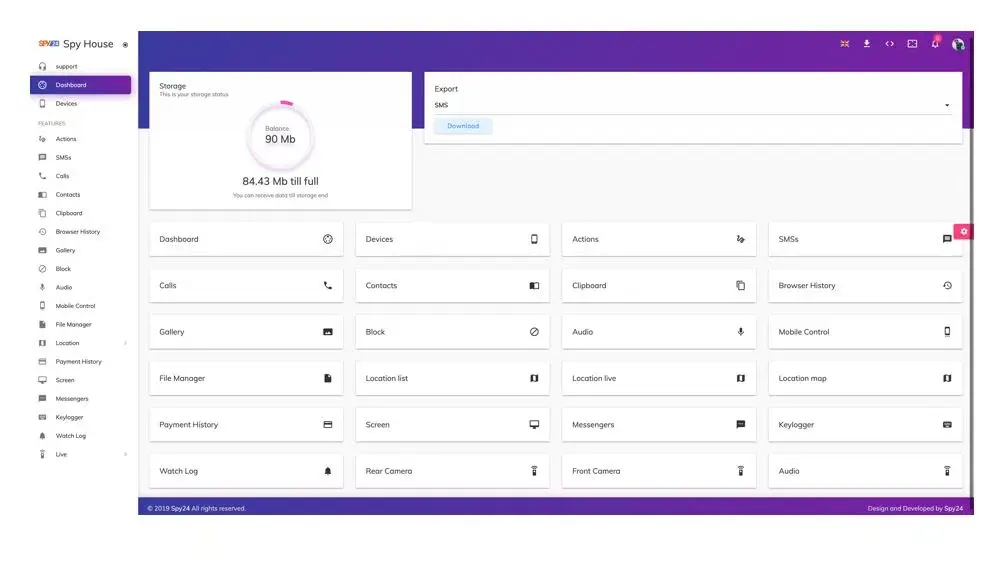
To use the SPY24 app, you simply need to download and install it on your phone. Then, you follow the simple instructions provided by the app to set up your WhatsApp account.
1. Download and install the SPY24 app on your phone or Computer.
2. Launch the app and create an account.
3. Select the WhatsApp account that you want to spy on from the list of accounts in the app.
4. Send a MAC spoofing message to the target’s phone.
5. Wait for the response from the target’s phone.
6. Once you have the target’s phone, you can start monitoring their WhatsApp messages immediately.
7. Continue monitoring the account for as long as you like.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
Conclusion:
WhatsApp hacking has many uses, both good and bad, but the most important thing to remember is to use caution when using this type of software. It can be powerful, but it can also be used for nefarious purposes. If you’re considering using a WhatsApp Spy app, you should do some research and make sure that you’re using a trusted and verified app. It’s also important to remember that using a WhatsApp Spy app can be illegal in some parts of the world. Be aware of the laws in your region before deciding to use a WhatsApp Spy app.
SPY24 is a WhatsApp Spy app that works across platforms; so it works on both Android and iOS devices. This app has a great performance rating on the Google Play Store, and it lets you spy on both iPhone and Android users. So, if you’re looking for a WhatsApp Spy app that works effectively on both platforms, then Spy 24 is one of the best options in our market. We highly recommend it for both personal and professional use.
FAQs:
(1) Can I use SPY24 to spy on my friend’s WhatsApp messages?
Yes, you can use SPY24 to spy on your friend’s WhatsApp messages.
All you need to do is get the friend’s WhatsApp number and enter it into the SPY24 app. Then, you can monitor all of their messages and calls from a remote location.
(2) Can WhatsApp Spy be used to spy on my child?
Yes, WhatsApp Spy can be used to spy on your child in order to know what they’re up to.
You can monitor their social media accounts, call logs, text messages, and location. You can also block specific applications from sending them messages.
Furthermore, you can set time limits on how long they can use their phone each day.
(3) Can WhatsApp Spy be used to monitor my spouse?
Yes, WhatsApp Spy can be used to monitor your spouse.
It works just like any other monitoring software, so you can use it to keep an eye on your spouse’s behavior online and their social media accounts.
You can also use it to track where they go and to listen in to their phone calls and text messages.
(4) Can WhatsApp Spy be used to spy on someone who lives overseas?
Yes, you can use WhatsApp Spy to spy on someone who lives overseas, as long as they use WhatsApp to communicate.
Just enter their WhatsApp number into the SPY24 app, and then you’ll be able to monitor all of their activities in real-time.
This is a great way to stay connected with friends and family members who live in different countries.
(5) Can WhatsApp Spy be used to spy on private group messages?
Yes, you can use WhatsApp Spy to spy on private group messages. In fact, this is one of the best and most popular ways to use WhatsApp Spy.
This is because private group messages are often where people share confidential or sensitive information.
For example, a private WhatsApp group for work colleagues might contain salary information or other proprietary information.