How to Hack Sim Card? Can SIM Cards Get Hacked?
Are you wondering if it’s possible to hack a SIM card? In this blog post, we’ll uncover the truth behind SIM card hacking and how it’s done, as well as the potential risks involved. We’ll also explore the advantages and disadvantages of SIM card hacking and how you can protect your SIM card from being hacked. So read on to learn more about this fascinating topic!
Is Your SIM Card Secure?
SIM cards are an essential part of mobile phones and more importantly, a way to access the internet. But can they be hacked? We’re here to answer that question, as well as give you some tips for protecting yourself from potential hacking.

What Are SIM Cards?
SIM cards are integrated circuits that hold customer data in mobile phones. They store personal information like phone numbers and contacts, as well as network authentication details, allowing the phone to access networks. When a person changes their phone number or carrier, they use a different SIM card with all the new information stored on it.
Main Reasons for Hacking SIM Cards
The most common reason why hackers target SIM cards is that they want to access someone else’s account or steal money from them. By having access to a person’s account, hackers can gain access to their private information like banking details or even personal photos and videos. They can also use stolen SIM cards to make international and premium-rate calls without the owner knowing about it until their bill arrives.
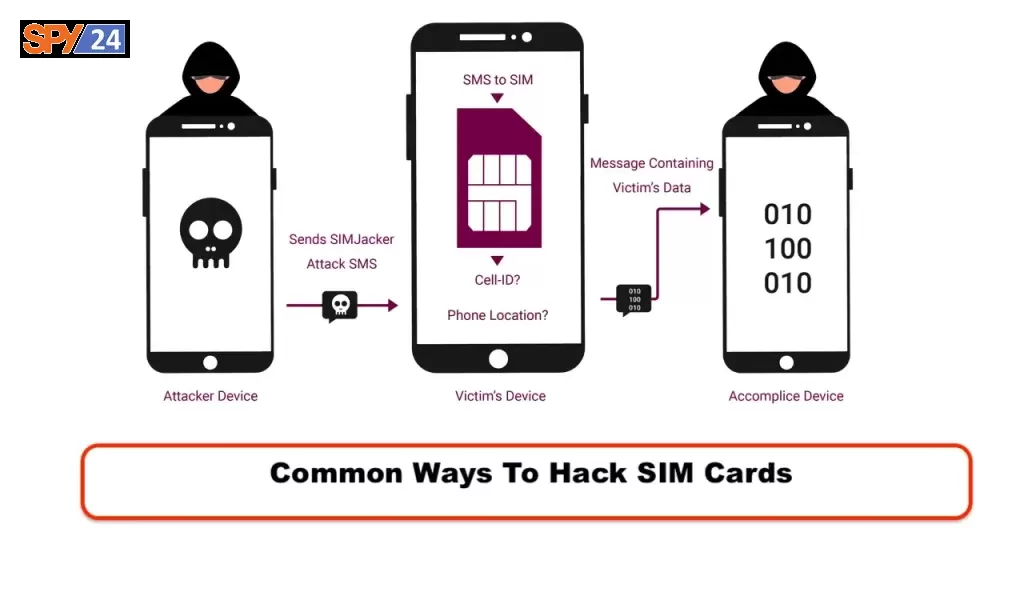
Common Ways To Hack SIM Cards
SIM cards are essential for mobile phones to access wireless networks and provide a number of services. They are also vulnerable to hacking. Hackers can gain access to your phone by exploiting weaknesses in SIM cards. Here are some of the common ways to hack SIM cards.
SIM Swapping
SIM swapping is a type of attack carried out by hackers that target mobile phones. It involves replacing the SIM card in a phone with a new one that contains malicious code. Once the hacker has access to the SIM card, they can take control of the phone and use it to gain access to personal information or to make fraudulent calls.
SIM Cloning
SIM cloning is a process in which a hacker copies the information from one SIM card to another. This can be done by using a cloning device or by using the software. Once the hacker has access to the information on the SIM card, they can use it to gain access to personal information and use it to make fraudulent calls.
Simjacker
Simjacker is a type of attack that targets SIM cards. This type of attack is possible because of the way that SIM cards are designed and the way they communicate with mobile phones. Hackers can use this exploit to gain access to personal information, make fraudulent calls, and even take control of a phone’s functions.
SS7 protocol
SS7 is a more sophisticated type of attack, utilizing the SS7 protocol. This protocol is used to transfer data between mobile networks and can be used to intercept messages and calls, as well as track a user’s location. By exploiting weak security measures, malicious actors can send commands to devices that are connected to the same network, allowing them to gain access to data and control of the device.
SPY24 Parental Control App
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
These are just some of the common ways to hack SIM cards. There are other methods as well, and it’s important to be aware of the risks associated with using SIM cards. It’s also important to protect your phone from hackers by keeping your SIM card secure and using strong passwords. By following these steps, you can help protect your phone from potential SIM card hacks.
How To Protect Yourself From Getting Hacked
The best way to protect yourself from getting your SIM card hacked is by taking extra security measures. First of all, make sure you have a strong PIN code set on your phone that only you know about – don’t share it with anyone else! Also, be aware of any suspicious emails or texts you receive, and don’t click on any links sent from unknown sources. Finally, if your phone supports two-factor authentication (2FA), make sure you enable this feature as soon as possible so that even if somebody does manage to get into your account they won’t be able to do anything without the second factor (usually an SMS code).

What To Do If Your SIM Card Was Hacked
If you think your SIM card has been hacked then there are a few steps you should take right away: contact your network provider immediately; change any passwords associated with your accounts; report the incident to the police, and monitor your bank accounts for any suspicious activity. It’s also important not to forget about physical security – make sure any devices connected to your account are locked when not in use!
How To Tell If Your SIM Card Was Hacked
Are you worried that your SIM card has been hacked? If so, you’re not alone. In this day and age, hackers are always on the lookout for new ways to access and exploit personal information. One way they do this is by hacking into SIM cards, which can lead to all sorts of problems, including identity theft and financial fraud.
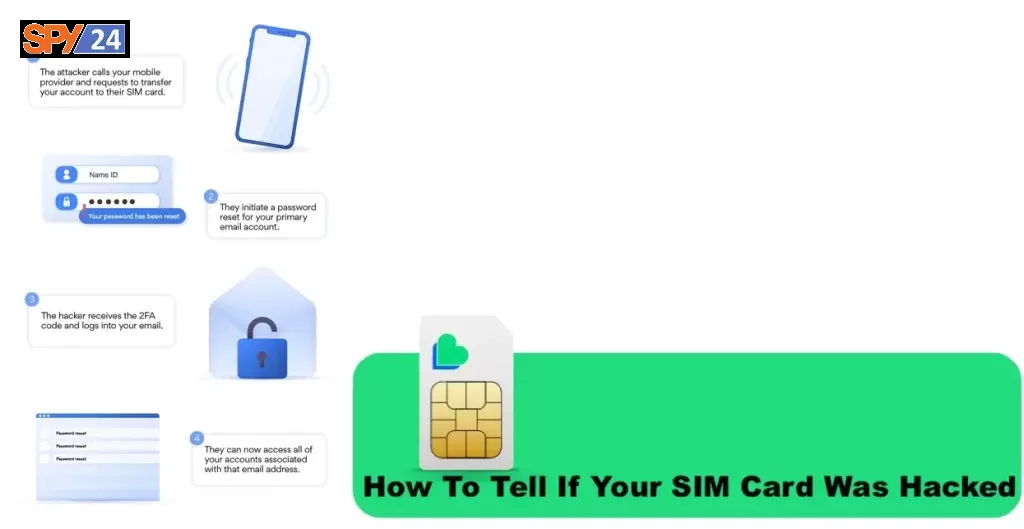
Fortunately, there are some telltale signs that can help you determine if your SIM card has been tampered with. Here are a few of the most common signs that your SIM card has been hacked:
Not Receiving Any Calls or Texts: If you’re not receiving any calls or texts from friends and family, it could be a sign that your SIM card has been hacked. This could be because your phone number has been changed or the hacker has blocked incoming messages to your device.
Request to Restart Your Phone: If you’re asked to restart your phone even if nothing is wrong with it, this could be a sign that your SIM card has been hacked. The hacker might be trying to gain access to your device’s settings or data.
Wrong Location: If your location is wrong when you look it up online, this could be a sign that your SIM card has been hacked. The hacker could be using your SIM card to track your movements or gain access to your data.
Can’t Access Accounts: If you’re having trouble logging into any of your online accounts, this could be a sign that your SIM card has been hacked. The hacker could be trying to access your accounts, or they might have changed your passwords.
Suspicious Account Activity: If there are any suspicious activities in your accounts, such as purchases or transfers that you didn’t authorize, this is a surefire sign that your SIM card has been hacked.
If any of these signs apply to you, it’s important to take steps to protect your device and your data. The first step is to contact your service provider and let them know what’s going on. They should be able to help you determine if your SIM card has been hacked and provide you with the necessary steps to take to protect your device.
It’s also a good idea to change all of your passwords, as well as the passwords for any accounts that may have been compromised. You should also keep an eye on your accounts and make sure that no further suspicious activity occurs.
Finally, it’s important to stay vigilant and monitor your device for any other signs that your SIM card has been hacked. By keeping an eye out for any suspicious behavior, you can help protect yourself and your data from hackers.
🤔What is a SIM Card Get Hacked?
A SIM Card Get Hacked is a type of fraudulent activity in which hackers gain access to a user’s SIM card information in order to make unauthorized calls, send text messages, or access the user’s personal data.
🔒How can I protect my SIM Card from getting hacked?
There are a number of precautionary measures you can take to protect your SIM card from being hacked, such as always keeping your PIN code secure, using two-factor authentication, and updating your device regularly.
💻How can hackers gain access to my SIM card?
Hackers can gain access to your SIM card by using malware, SIM Swapping, SIM Cloning, Simjacker, SS7, phishing attacks, or exploiting vulnerabilities in your device or network.
🔎 How can I tell if my SIM card has been hacked?
If you experience suspicious activity on your phones, such as strange text messages, calls, or data usage, this could be an indication that your SIM card has been hacked.
🛡️What can I do if my SIM card has been hacked?
If your SIM card has been hacked, the best course of action is to contact your wireless carrier immediately and have them investigate the issue.
What should I do if my SIM card has been hacked?🔒
If you think your SIM card has been hacked, you should report it to your provider immediately. You may also have to contact your bank to report any fraudulent activity.
Conclusion: No one wants their personal information compromised or their bank accounts emptied out by hackers. The good news is there are steps we can take before our data falls into the wrong hands – such as setting strong PIN codes, being aware of suspicious emails/texts, and enabling two-factor authentication (if available). Even if our worst fears become reality and our SIM card gets hacked, we still have time to act – by contacting our network provider and reporting it to the police straight away! With these simple precautionary steps in place, we can ensure our online safety remains intact no matter what happens.




