How to Hack Text Messages? Introducing the Best Spy App
In this article from SPY24, we will discuss a very interesting and important topic in hacking and security, that is, hacking text messages and SMS. If you are a beginner in this topic, don’t worry at all because we will teach you from zero to one hundred. We will learn the subject.
SMS attacks definition
Smishing is short for SMS phishing. Cybercriminals trick the user into clicking on a link or opening a file by sending text messages or sending messages through instant messaging applications. As a result, the user’s device is infected with a Trojan horse, virus, or other types of malware.
This means that your bank card information, social security number, address, and other important and private information can be vulnerable to this type of text message. Vandals usually send these messages with a link or phone number. If you call that number or click on a link, they can collect more information.
Short messages in these attacks may strongly create a sense of excitement and quick reaction in the user.
An example of this type of message may be as follows: Call this number to register and receive your card! Another example, you can register to register a basket of goods through the link below! The user may get curious and click on the link. You can easily become a victim of a smishing attack.
According to FBI reports, Americans lost $1.3 billion this way in 2016. Mobile is something that people always carry with them. If you are the type of person who reacts quickly to everything, like quickly clicking on links, etc., then you can easily fall victim to Smishing attacks.
Since you don’t know with which phone number the attacker will send you a text message, it is not possible to block it in advance. But after receiving the message, you can block it.
Also Read: Hack Messages (SMS) By Phone Number
Phishing through SMS
This method is one of the newest types of phishing, where the hacker sends a text message to the victim’s mobile phone and tries to get his sensitive and important information. In fact, mobile phones and their common use by the majority of people, It has provided a very good opportunity for hackers to take advantage of the perfect situation and technology.
Statistics show that more than half of people use smartphones, and the vast majority of them immediately consider receiving an SMS and clicking on it if there is a leak in it. In this method, a false and tempting message is sent to the user and makes him eager to open the link or enter the desired information. For example, if this message is from the bank, you win the prize. or your credit card is running out of credit, you only have until the end of today to receive your gift by visiting the link below. It is fake and by completing the desired information, you are giving your sensitive information to the hacker.
What to do to deal with a smishing attack?
Do not click on any link received in the SMS and also do not call any mentioned phone number. If a text message claims that money has been withdrawn from your bank account, or any other type of abuse, the first thing to do is to check your account directly, preferably from a device other than your mobile.
Also Read: The Simple Guide to Hacking Text Messages Without Having Access to the Phone
What is SMS malware?
Everything about SMS viruses and ways to prevent them…
Text message viruses are a type of malware, which have been widely published in cyberspace these days. Many mobile devices have been affected by viruses and have caused many people trouble. This malware, which sends messages in the ENGLISH language these days, engages the audience with its tempting offers in order to access the necessary information. Stay with SPY24 to discuss SMS viruses and ways to prevent them.
What SMS messages are suspected to be SMS viruses?
As we said in the previous section, SMS messages that contain viruses appear with texts that attract the audience. for example:
• Enter this site to get free bitcoins.
• The incredible discounts on this site are nowhere to be found.
• Become a member of this site to see information about (a famous actor).

What is an SMS virus?
It is a type of virus active on Android mobile phones that spreads through text messages or SMS. Of course, let’s also say that this type of virus also penetrates mobile phones with the IOS operating system, but due to the fact that the security of this type of operating system is more than that of Android, this penetration occurs less often.
Also Read: 10 Best Free Text Message (SMS) Hacking without Target Phone
How the SMS virus is uploaded to the phone
As soon as the virus enters the operating system of your phone, it is secretly loaded into the phone. This means that no icon or special feature will be displayed on your phone indicating that this virus has entered. At the same time, without you knowing, an SMS will be sent from your phone to your contact list, which contains a virus. In this way, the chain of spreading the virus will continue. It is interesting to know that you will never notice this unless your monthly bill includes a large amount for sending SMS.
How does an SMS attack work?
Criminals inform SMS recipients that, for example, there is a voicemail or that the smartphone is infected with malware. The message link then contains instructions on how to download the alleged security update or voice message. Only those who download these files install the scammers’ malware.

Smishing – SMS phishing
There are also text messages where recipients are tricked into thinking their private photos have been leaked because their mobile phones are allegedly infected with malware. In this way, the perpetrators apply pressure and try to convince smartphone users to install the alleged security update. In this case, downloading leads to system contamination.
In these cases please:
1. Do not click on existing links.
2. Do not download files from unknown sources.
3. Immediately delete the suspicious SMS.
Although ISPs have implemented filtering measures to prevent smishing from being sent, these cannot provide complete protection because the perpetrators are constantly taking countermeasures. Recently, it has been observed that the messages sometimes contain intentionally transposed letters, misspellings, or random character strings to bypass mobile operators’ spam filters.
What should I do if I receive such a text message?
The common feature of all these sms is that they contain a link. This link leads directly to malware or phishing sites where you are supposed to divulge sensitive information. If you haven’t clicked the link yet, SPY24 recommends:
1. Do not click on the link and delete the message immediately after receiving it. If you know the sender, call him and ask him about the authenticity of the SMS.
2. Block the sender of the message through your operating system.
3. Download apps only from reputable stores and not from external sources. On Android, disable installing apps from unknown sources. To do this, look for “Apps from unknown sources” or “Install unknown apps” in the settings and uncheck them.
4. Whether Android or iOS: update your device! iOS is currently on version 15.0.2. Android receives security updates for OS 8.1, 9, 10, and 11. You can find tips for effective basic protection on our other websites.
5. You can enable a third-party lock with your wireless service provider. In this way, it is possible to avoid accidental costs or possible costs caused by malware as much as possible. You can get information about the implementation from the information offers or portals of your mobile service provider.
Types of SMS and mobile malware attacks
Traditional phishing has plagued Internet users since the 1990s. Smishing, on the other hand, is a phenomenon of the late 2000s. The term is a combination of SMS and phishing – although it generally involves attempts to scam via messaging services (such as iMessage or WeChat) that are not based on the SMS system protocol. The lucrative attack vector for cybercriminals is collapsing, especially since smartphones have become ubiquitous.
Vishing (Voice Call Phishing) is also a type of Phishing – however, this attack method is based on voice calls.
Type of Smishing attacks
In practice, assaults can be divided into three different categories that differ in terms of criminal intent:
Different types of mobile malware
Let’s take a closer look at the different types of mobile malware, how they are distributed or installed, and the damage they can do to data on the phone itself and the network.

1. Spyware
Malware, short for mobile advertising, usually enters a mobile phone through the installation of a script or application, often without the user’s consent. The goal of most types of disruptive software is to collect data from your phone to spam you with ads. Most versions of Madware usually contain an element of spyware. Its task is to collect information about your internet usage, which it will eventually send to a third party. This data may include details about your location, your password, and your contacts.
2. Loading the drive
If you open the wrong email or visit a malicious website, you can become a victim of a type of mobile malware called a drive-by download. These types are automatically installed on your device. This type of virus can include a wide range of threats, including spyware, malware, adware, and in some cases even a bot, it can use your mobile device to do malicious things like sending viruses to other people around you.
3. Viruses and Trojans
What may appear to be a legitimate application could contain a virus ready to attack your mobile phone. These viruses may have relatively harmless effects, such as changing the phone’s wallpaper or changing the language. However, most viruses have other malicious goals in mind, such as extracting passwords and banking information.

4. Mobile phishing
Phishing abuse is nothing new. The introduction of mobile phones has caused cybercriminals to change their phishing methods to defraud users of mobile devices. Traditional phishing techniques involved sending emails to users that appeared to be from a legitimate source. The development and increased use of mobile phones has taken mobile phishing a step further by using applications to deliver mobile malware. The user, who often cannot tell the difference between a legitimate app and a fake app, is simply tricked and the fake app collects account numbers, passwords, and more.
5. Operation of the browser
When it comes to security, no mobile browser is completely safe. Because of this, a lot of browser abuse happens in the tech world. Like mobile PDF readers.
Attempts to steal user information: Smishing attacks can steal login credentials to online accounts. Online banking access is of particular interest to criminal hackers. Paradoxically, cybercriminals regularly try to capitalize on the fear of being hacked: they send SMS or text messages pretending to be from the victim’s bank.
This method is also known as “bank robbery”. These messages warn their recipients of large debts or unknown recipients and provide a phone number or link to prevent possible unauthorized access to the bank account. The link usually leads to a fake website, and a phone number directly to the cybercriminal – in both cases, the goal is to trick victims into revealing their usernames and passwords so they can then loot their accounts.
Bank raids are successful for several reasons: Some financial institutions actually send text messages or SMSes that warn of suspicious account activity. Genuine messages of this type are usually identifiable by the fact that they usually contain information known to the financial institution (eg, the last four digits of your credit card or account number). However, direct links and vague references to “your account” should make you suspicious. If you are unsure about the authenticity of a message: Sign in to your account using your browser or app – Never click on a link in an SMS or SMS.
Another reason bank hacking attacks are so successful is the tactics used by cybercriminals to obfuscate: the sender’s phone number can be hidden or spoofed using certain methods – sometimes using relatively simple means, for example by sending a Message from the computer. If such messages are automatically assigned to the legitimate sender number of the smartphone, the probability of a successful hacking attack increases many times.
Attempting to spread malware: This type of smishing is based on classic email phishing – but adapts techniques specifically designed for mobile users and end devices. For example, in the Czech Republic, there was a scam some time ago that tried to trick its victims into installing an app – apparently from the Czech Post Office. In fact, it was a Trojan to steal credit card information and compromise the credibility of other applications.
Smishing attacks aimed at spreading malware have become less common as security measures on smartphones — particularly Apple’s iOS — have made it relatively difficult to install unsigned or unverified apps. However, especially on Android devices, app sideloading is possible – here only a healthy skepticism helps if you are asked to install an app via SMS or text message.

Attempting to collect sums of money: This type of hacking attack is less for experienced cybercriminals – this is where clumsy game scammers look for more. However, such efforts are a risk – especially for the less tech-savvy. In one case, fraudsters posing as personal acquaintances contacted the victim (names most likely identified through social media) and offered a sum of money in the form of a government grant. In fact, it was a classic scam: the victim was supposed to pay a few hundred dollars in advance.
Prevent phishing through SMS
A study by Gartner concludes that 98% of all texts and SMS are read and 45% are answered. Because many
- Premium-rate SMS scams
On the Internet and on various sites, you can see software that supports this type of attack, and you have to pay for it.
For example, in the link below, you can see one of these applications that also use scams.
- How to prevent SMS attacks
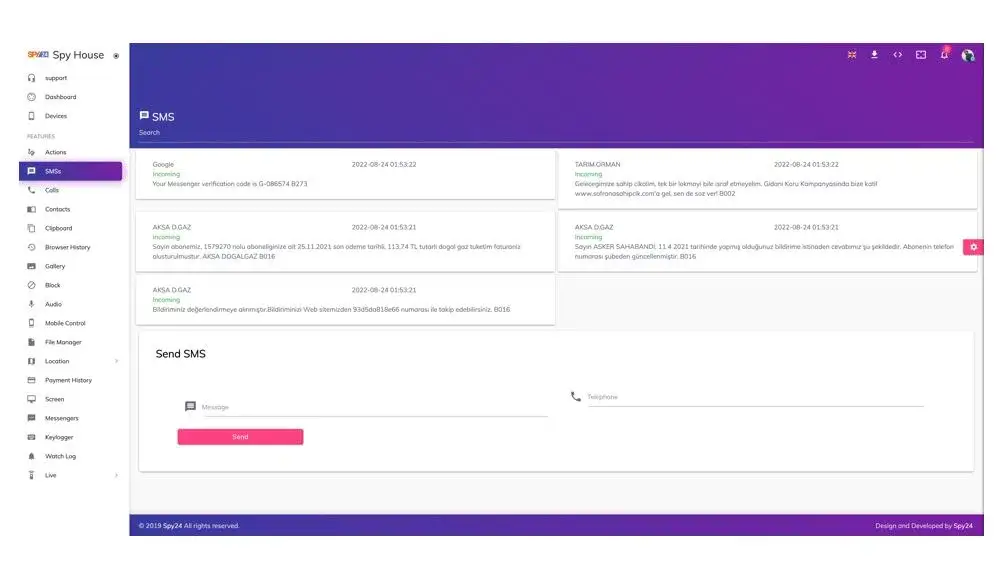
Spy text messages with the SPY24 app
Mobile text message control and tracking software allows parents to have accurate and complete control over their children’s sent and received text messages in order to be informed of their children’s complete safety…
You can learn more about the features of this program such As :
Viewing messages, limiting messages, accessing contacts, and…
After installing the mobile phone control and tracking software on the children’s mobile, the software gives this permission to (parents) so that they can have complete control and supervision of their children’s phone messages.
a spy text message with the SPY24 app
SPY24 feature
1. Parents can control their children’s text messages as follows:
2. The content of each SMS / MMS
3. Warning of suspicious and frequently used SMS messages during the day.
4. Controlling the type of message, if the message was sent or received.
5. Control and view the name of the sender or receiver with the mobile phone number.
6. View the date and time of sending or receiving text messages in descending order.
7. Insert keywords to alert a specific word in sent and received SMS.
8. Display the location and GPS coordinates of the mobile phone when sending or receiving SMS
9. No need to root the device
Are you worried about your children’s communication, calls, and SMS conversations? Do you want to know exactly what is exchanged with others in your children’s text messages?

The SPY24 application offers you these facilities along with other facilities with the careful design of security engineers. SMS is one of the ways of communication between children that never causes sensitivity! The SPY24 monitoring system mobile text message control and tracking software, it reports the list of sent and received text messages along with contact name, number, time and date, location, and full content to parents.
ios tracking
SPY24’s children’s SMS spying application is also suitable for iOS operating systems and allows you to control your children’s iOS-based phones. SPY24 is completely suitable for iOS and Apple phones and does not leave any traces of itself on the person’s phone.
So, if your child’s phone is iOS, you can easily get this program.
As an employer, do you need to monitor the performance of your employees?
If the answer is yes, with the SPY24 application, you can pay for facilities such as SMS spying and controlling and monitoring the messages exchanged by your employees.
This work is possible for you without the need for any security expert, and you can also use other features of SPY24, including interception and listening of exchanged messages in software such as WhatsApp, Telegram, and Instagram.
Suitable application for monitoring and improving the performance of school students
With the SPY24 App, can we monitor the sites where children and students go to school?
Yes, you can have strict control over the websites that your child enters under your control and supervision to prevent your child from entering violent, immoral, and inappropriate sites quickly and remotely the entire website. Block the desired ones.
Can we control the apps installed on the phone with SPY24?
Yes, you can control the programs installed on the phone of your child or family members from within the user panel, and if you come across an unethical or inappropriate program, you can completely block it remotely.
With the SPY24 program, can we view the child’s surroundings live through the phone’s camera?
Yes, you can observe the surrounding environment completely hidden and imperceptibly through the front and back camera of your child’s mobile phone and even hear the surrounding sound through the phone’s microphone.
Can the SPY24 program monitor the phone’s file management?
Yes, you can fully access all parts of the files on your child’s phone and manage them remotely. This feature is used even for files that are hidden in the phone.
Can we access the location of the phone by downloading the SPY24 program?
Yes, you can view the GPS location of your child’s phone and other family members on the map remotely and through your user panel, online and completely live, and you can view the history of places and routes that a person has taken See their traffic on Google Maps.
SPY24 Install application free The Most Powerful Hidden Spying App to Monitor Android, IOS Cell Phone & Tablet Device Remotely. Best Android Parental Control App for Kids & Teens Online Safety.
Now take the liberty to monitor Android, and IOS devices with exclusive features better than ever before Monitor all Voice & Text Messages Communication records, Listen to & Watch Surroundings in Real-time Unleash Digital Parenting with Android, IOS Spy App Spy (Surround Listing & Front/Back Camera Bugging) IM’s VoIP call recording on Android OS 13 & above With 250+ Surveillance Tools at your fingertips using Android Tracking & Parental Monitoring Software.
Conclusion
In this article from SPY24, we discussed all methods of SMS hacking through malware and different methods and explained to you how to monitor and track children, family members, employees, and students without noticing the monitoring. and become your control.
We also talked about the dangers of using various applications and malware on the Internet, which can cause many risks and problems for you and the person you want to monitor.
We at SPY24 help you to monitor and care for your children remotely with a completely safe and guaranteed idea by designing a completely safe application on different platforms.
FAQs:
Is it possible to hack or eavesdrop on other people’s text messages?
Yes, by using different methods such as smashing or using the safe application of SPY24, you can listen to the text messages of the other person.
Can a person’s SMS history and contact list be hacked and tracked?
The answer to this answer is yes, there are different ways and different software for this, using different malware or using parental control applications like SPY24.
Why are mobile SMS control and tracking software useful for parents?
So that parents can monitor the exact location of their children, the content, and messages exchanged with untrustworthy and abusive persons and prevent severe social harm to their children.




